Why Use SAML SSO in Decoupled .NET Applications?
Centralized Authentication
Eliminate multiple logins—authenticate once and access all connected apps securely without additional credentials.
Cross-Platform Compatibility
Seamless integration with ASP.NET, ASP.NET Core, and microservices-based .NET applications.
Tailored for Decoupled Apps
Use our plugins to integrate SAML SSO into your decoupled .NET apps effortlessly.
Compliance & Security
Built on SAML 2.0 standards, ensuring encrypted communication and enterprise-grade security.
How SAML SSO Works for Decoupled .NET Applications (Frontend + Backend)
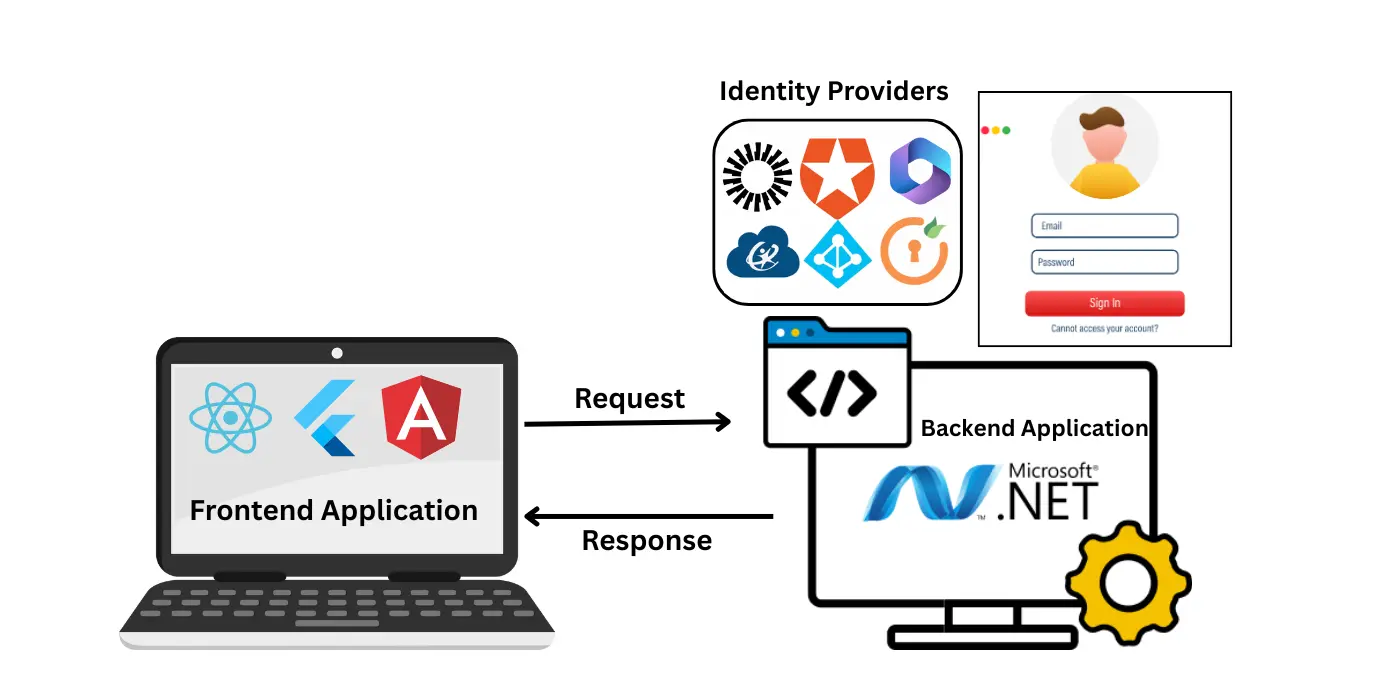
A decoupled .NET application consists of independent apps (API, front-end, back-end) that need a unified authentication mechanism. Here’s how miniOrange makes it work:
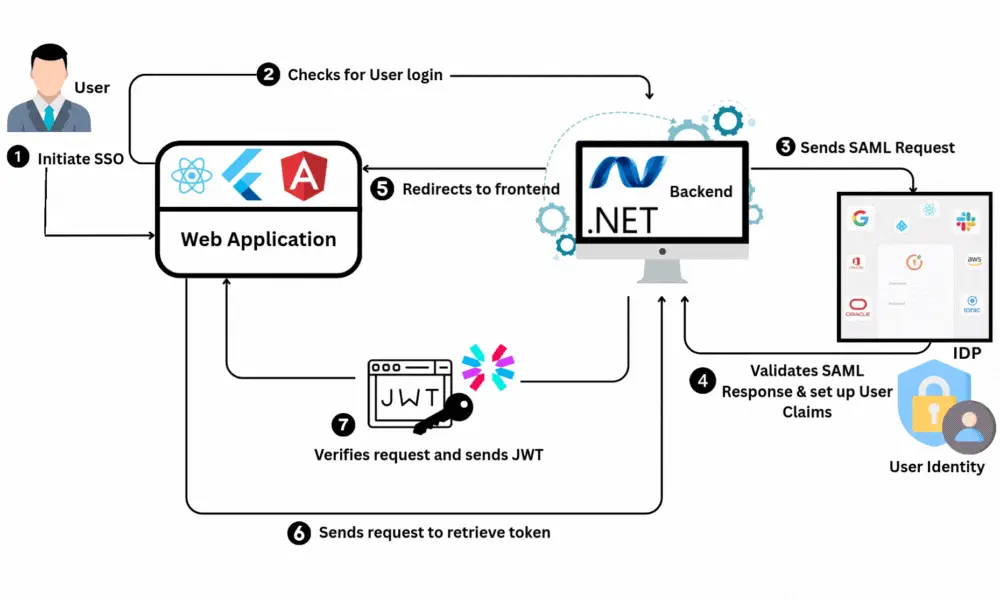
1. User Starts Login
When User A visits your frontend app, the app checks if the user is already logged in. If not, it starts the SSO process.
2. Frontend Redirects to Backend
The frontend passes the login request to the .NET backend to handle authentication.
3. Backend Sends SAML Request to Identity Provider (IdP)
The backend sends a SAML request to the Identity Provider (IdP) (like Azure AD, Okta, etc.) to ask for user authentication.
4. IdP Authenticates the User
The IdP checks the user's credentials. If everything is valid, it sends back a SAML response confirming the user's identity.
5. Backend Logs the User In
The backend reads the SAML response, logs in the user, and sets a claims cookie. Then it redirects the user back to the frontend.
6. Frontend Asks for a Token
After being redirected, the frontend sends a request to the backend to get a JWT token (a secure login token).
7. Backend Sends the JWT Token
The backend checks the request and sends a signed JWT token back to the frontend. The frontend now uses this token to make secure API calls.
Use Case: SAML SSO for Angular, Vue.js & React Frontends with .NET Backend
Scenario:
Organizations are increasingly adopting decoupled apps, using modern frontends like Angular, Vue.js, or React that communicate with a centralized ASP.NET (.NET Core/Web API) backend. While this setup offers flexibility and scalability, it presents a challenge when implementing SAML Single Sign-On (SSO).
Challenge:
SAML Incompatibility with Modern Frontends:
SAML depends on browser-based redirects, which don’t play well with frontend frameworks like React, Angular, or Vue.
Disjointed Authentication Experience:
The absence of a centralized login system leads to inconsistent user experiences and adds complexity and time to the development process.
Unauthorized API Access:
Unable to allow only authenticated users to access your .NET APIs. Implementing JWT could help prevent unauthorized data exposure.
Lack of Role-Based Access:
User roles (e.g., admin, viewer) needed to be enforced at the backend, keeping them hidden from the frontend and reducing security risks.
No Frontend Code Modifications:
The organization prefers not to alter frontend code—whether due to the risk of introducing bugs or the complexity of deployment pipelines.
Solution:
Backend-Handled SAML Authentication:
By introducing a .NET-based SAML Identity Broker, all SAML requests and responses are handled at the backend.
Multi-IdP Support:
With support for multiple Identity Providers like Azure AD, Okta, ADFS, and Google Workspace, organizations can centralize authentication across different systems.
Secure Token Exchange + API Access:
After successful SAML authentication, the backend issues a JWT or session token. Frontend apps use this token to make secure API calls, ensuring only authenticated users can access your .NET APIs.
Role & Attribute Mapping:
The backend fetches user roles and attributes (like email, department, and permissions) from the IdP and applies RBAC policies. This keeps role enforcement off the frontend, improving security.
Outcome:
By implementing the miniOrange SAML SSO solution for decoupled frontend-backend apps, organizations benefit in the following key ways:
Centralized & Secure Authentication:
Centralized SAML authentication ensures secure login, better control, and prevents token mishandling on the client side.
Better User Experience Across Frontends:
Users on Angular, Vue.js, or React apps experience smooth, SSO-based login flows without redirects breaking the UI or interrupting sessions.
Efficient Token-Based API Communication:
Post-authentication, JWT tokens are issued by the backend, enabling frontend apps to securely call APIs.
Granular Access Control with RBAC:
Fine-grained authorization logic that can enforce access restrictions at both the API and feature levels—without exposing role logic in the frontend.
Support for Multiple Identity Providers:
miniOrange SAML SSO integrates with any SAML-compliant IdP—allowing organizations to manage multiple login sources from a single backend integration point.
Why Choose miniOrange for SAML SSO in Decoupled .NET Apps?
Seamless Integration with .NET Backend
Works with ASP.NET Core, Web API, and microservices. Ensure smooth and secure communication between .NET apps.
Secure Token-Based Authentication
Ensures safe API access using industry-standard JWTs. Prevent unauthorized access and maintain data integrity.
Supports Multiple IdPs
Authenticate your users using a variety of Identity Providers (IdPs) such as Okta, Azure AD, ADFS, Google Workspace, and more.
Flexible Role & Attribute Mapping
Go beyond basic authentication with custom role and attribute mapping.


Leave a Comment