Need Help? We are right here!
Search Results:
×Two-Factor Authentication (2FA) also called 2-Step Verification, is a security process in which a user has to pass two different authentication methods to gain access to an account, device, or computer system. The first factor is the basic thing you know: username and password, and the second factor is what you might have as unique (Smartphone, security tokens, biometrics) to approve authentication requests. By enabling 2FA, you'll add an additional layer of security, making it harder for attackers to access the data through a person’s device or an online account. Two-Factor Authentication (2FA) security helps you and your users to protect against phishing, social engineering, and password brute-force attacks and secures your logins.
miniOrange provides users, employees & organizations an option to enable Two-Factor Authentication (2FA) for their Cloud, Mobile, in-house apps & Websites accounts. miniOrange also provides a seamless 2FA solution for all VPNs, which does not necessitate the installation of an external proxy on top of your VPN servers. On top of it, the miniOrange provides 2FA security on Windows & RDP login. In business, this also means that by using 2FA, employees can access all their work without having to enter usernames & passwords repeatedly and it still maintains total control across every login.
Knowledge factors include multiple passwords, PIN codes, and answers to security questions. Anything you can remember, type, say, do, execute, or otherwise recall when needed is considered as a knowledge based authentication factor.
This factor suggests that you possess a certain object since it is improbable that a hacker would acquire your password and take anything physical. This category includes smartcards,mobile phones, hardware tokens, software tokens, and keychains.
This feature is often verified by a fingerprint test on a device, but it also includes anything that may be a wholly unique identification of your physical person, such as a retinal test, voice or facial recognition, or any other sort of biometrics.

per user per month
*Please contact us to get volume discounts for higher user tiers.

Zero Trust approach within 2FA helps to create an effective environment, policies, and infrastructure to minimize data breaches.
2FA login for users using just Username and OTP/TOTP thus, preventing the need to enter Password.
Allow users to log in even if there is no internet available by using Offline 2FA method such as soft token and security questions.
Admin can enable or disable 2FA for a specific user role and for any particular application.
Provides Two-Factor Authentication (2FA) solutions for OpenVPN, Palo Alto, Cisco Pulse, Windows, RDP & etc.
It offers inline registration of users so you'll simply activate and setup 2FA and you're ready.
2-Factor Authentication (2FA) decreases the chance of a hacker gaining access to corporate accounts/devices or other sensitive information.
Employees may securely access business apps and resources from practically any device/account and location, without jeopardising the company's network.
2-Factor Authentication creates a situation where any successful account breach or fraudulent transaction requires additional efforts and resources.
When you use a 2-Factor Authentication (2FA) process, you’ll have less suspicious activity on customer accounts, which means you’ll spend less money on security management.
We provide customization on our products which are platform independent and they can be easily accessed by an end user.
You can use our 2 Factor Authentication APIs to integrate additional security into your applications on any device that supports a web-Browser.
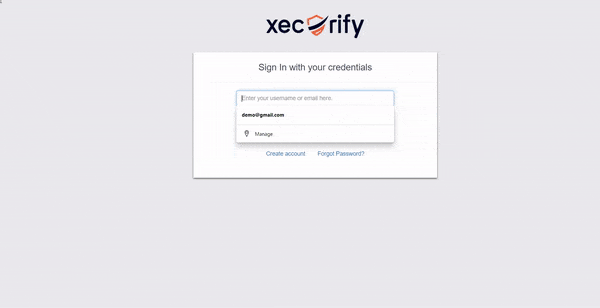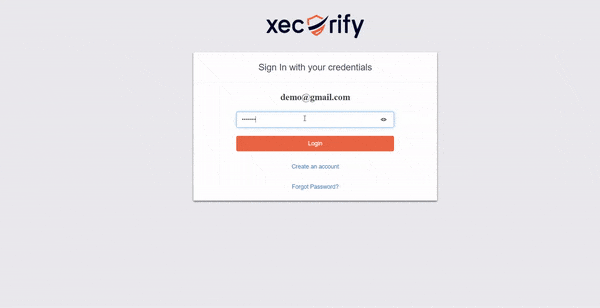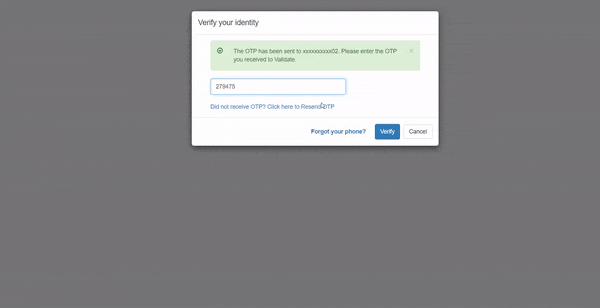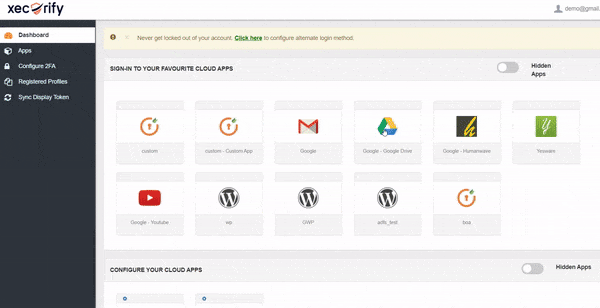
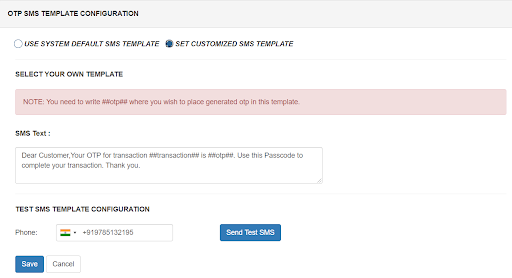
miniOrange 2FA solution provides the service of OTP over SMS/Email by using the default gateway which can be used by users as well. However, if you have a custom SMS/SMTP gateway, you can modify your connection to use that instead. miniOrange provides an option to use your custom SMS/EMAIL gateway. Also, the templates for SMS and email which are sent to users containing OTP for authentication are also completely customizable.
Passwordless authentication is a convenient and secure way to log in without having to remember a password. With Two-factor authentication, users can simply enter their username and receive a one-time password or push notification to log into the application. This eliminates the hassle of remembering passwords and the risk of losing credentials.
Learn More about Passwordless
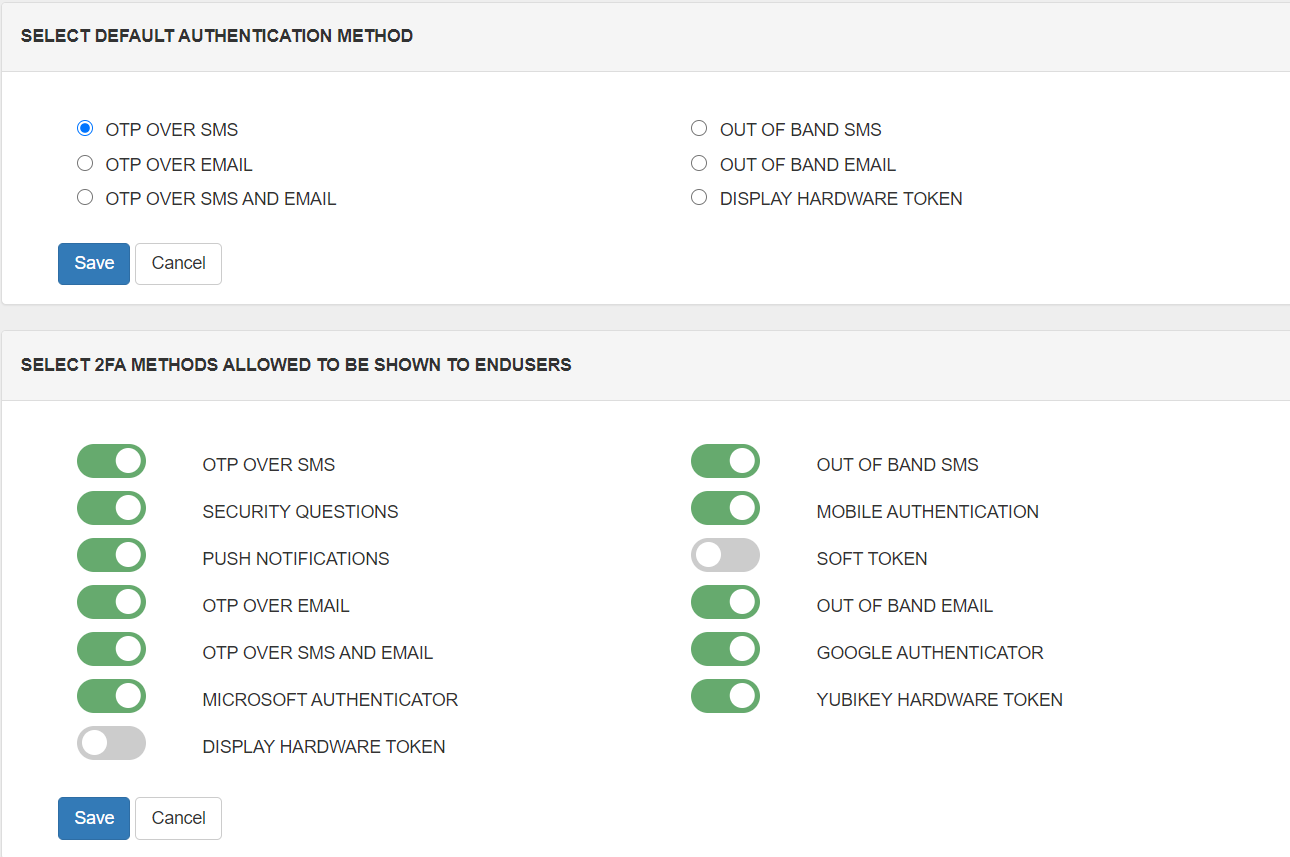
Admin can set the default two-factor authentication methods for users to avoid the extra step where each user can set their own 2FA method.
Admin also has the privilege to restrict a few of the 2FA methods for end-users, so that users are only allowed to use a particular set of two-factor methods. Users can only see the allowed two-factor authentication methods on the user dashboard.
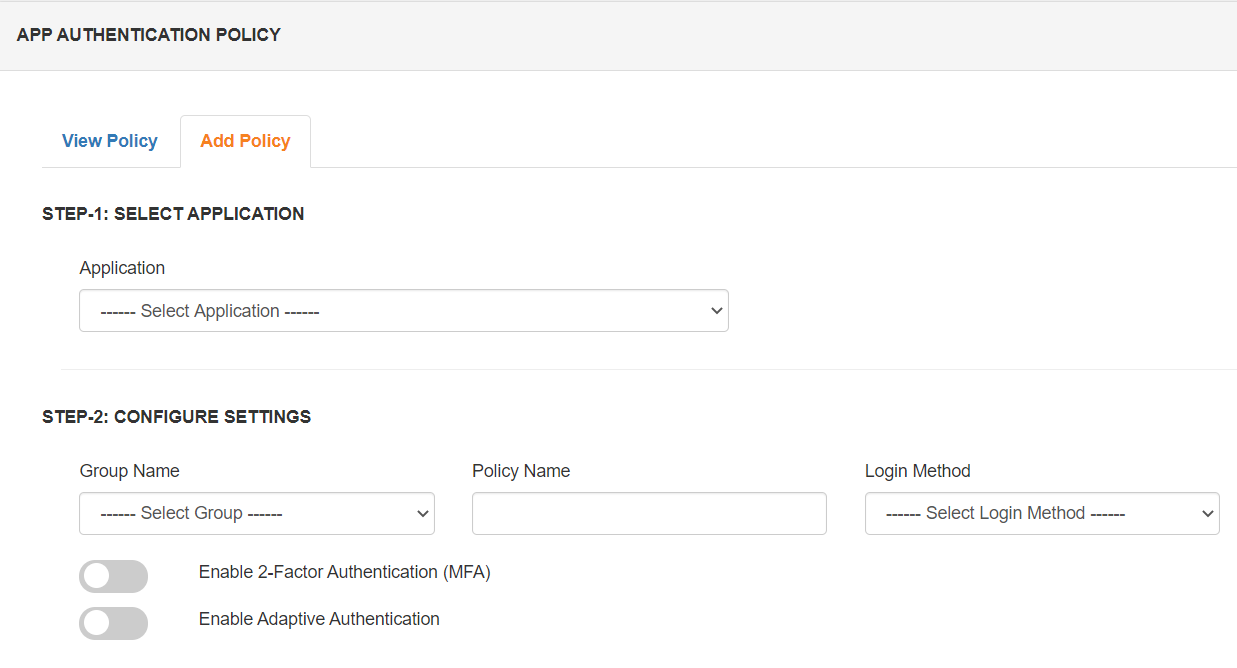
Role-based 2FA authentication is an approach of restricting system access to authorized users. With hundreds or thousands of employees, security is more easily maintained by limiting access to sensitive information based on each user's established role within the organization. We provide an option to manage users and user groups according to their roles and providing them with the necessary access. Admin can enable/disable 2FA for a particular role and application.

Two-factor Authentication (2FA) might seem daunting to you, after all, you need to apply an additional step in order to access your accounts and devices. However, in this fast-paced digital world, traditional authentication no longer works, as cyber attackers target sensitive customer information. Cybercriminals can steal your data services and gain access to your personal information if you don't use 2FA. Two-Factor Authentication (2FA) protects your devices, accounts, and data from security breaches, phishing, and brute-force password attacks. Knowing your password alone won't allow cyber attackers to pass security checks if you've enabled 2FA security. As concerns about digital security increase, more and more individuals are choosing 2FA (Two-Factor Authentication) solutions.
Usernames and passwords can be vulnerable to keyloggers, which can copy all data entered. Hackers can use spyware to monitor users' behavior and steal passwords or personal details.
Ransomware is a type of malware that an attacker installs on a user's system, stealthily encrypting the user's files or data. The attacker demands a ransom from the victim to decrypt the locked files and restore access. 2FA is effective at preventing ransomware attacks by keeping attackers out of the system.
MFA and 2FA are almost similar and often used interchangeably. 2FA is basically a subset of MFA since as the name suggests 2FA restricts the number of authentication factors to two, while MFA can be two or more.
In this case, call or email your administrator and he can give you access through his admin console. He can enable Forgot my phone option temporarily. If you already have another phone, then you can ask the administrator to reset your phone number and easily login via 2FA.
Almost every industry requires 2FA, but healthcare, retail, Banking, Media, Travel, and energy are the industries that use 2FA at a vast level.
In this Cyber World cyber threats are very common hampering organizational Security. But 2FA is one of the major security solutions which addresses threats like Stolen Passwords, Social Engineering, Key Logging, Phishing Attempts, and Brute-Force Attacks.
