Need Help? We are right here!
Search Results:
×Designed to support every team involved in managing user access and identity security across the organization.
Automate user provisioning and deprovisioning across all systems to reduce manual work and eliminate access-related tickets.
Enforce least-privilege access, prevent insider threats, and reduce breach risks with real-time lifecycle controls.
Maintain continuous compliance with full visibility, audit trails, and automated access certifications.
Enable faster onboarding, seamless role transitions, and secure offboarding without depending on IT for every change.
Scale lifecycle automation securely across departments, applications, and cloud environments as your organization grows.
| Lifecycle Stage | Manual User Provisioning (Problems) | User Lifecycle Management (Solution) |
|---|---|---|
| New Hire Onboarding | New hires wait days to get productive | Automated provisioning enables day-one access for new users |
| Role Change Management | Role changes leave excessive permissions behind | Dynamic access updates remove outdated privileges automatically |
| Employee Offboarding | Former employees retain active accounts | Real-time deprovisioning revokes all access instantly |
| Audit & Compliance | Audit preparation becomes time-consuming and risky | Built-in governance and audit-ready reporting |
| IT Operations Efficiency | IT teams are overwhelmed with access tickets | HR-driven automation reduces manual IT workload |
Automatically provision user accounts across directories and applications the moment a new hire joins, create corporate email IDs, assign birthright access, and trigger approval workflows for role-based access. This ensures secure, compliant, and productive day-one onboarding with zero manual effort.
Dynamically update roles, group memberships, and permissions when users change teams, departments, or responsibilities. Remove outdated access automatically to prevent privilege creep and reduce security risk.
Automatically disable user accounts and revoke access across connected systems at exit via single-click or scheduled workflows ensuring real-time, compliant offboarding and preventing orphaned accounts.
Design flexible, policy-driven approval workflows for managers, application owners, and high-risk access requests. Maintain controlled access governance using multi-level, multi-stage approval mechanisms for all access requests.
Generate detailed lifecycle activity reports and immutable audit logs for every provisioning, update, and deprovisioning event. Simplify audits, investigations, and compliance reporting with full visibility.
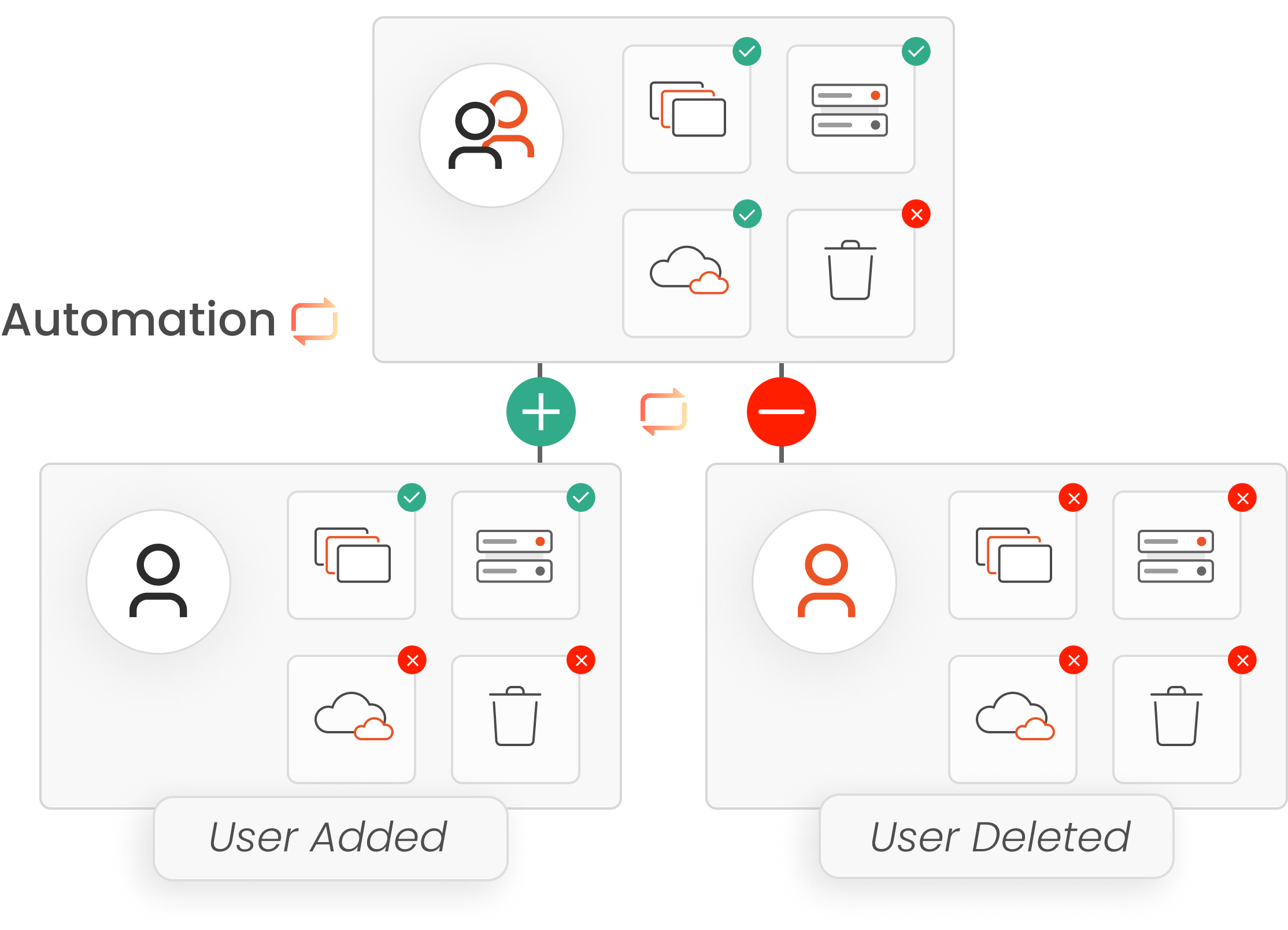
Automatically provision user accounts and role-based access across systems to ensure secure, productive day-one onboarding.
Update roles and permissions automatically when users change teams or responsibilities, preventing privilege creep and access gaps.
Disable accounts and revoke access across all applications instantly to eliminate orphaned accounts and protect sensitive data.
Grant time-bound, policy-controlled access to external users with approvals and automatic expiration.
Automate identity onboarding and access alignment across organizations to ensure secure, seamless transitions.
