Need Help? We are right here!
Search Results:
×Average Cost of Data Breaches
Data Breaches caused by Insiders
GDPR, HIPAA & more
Available for you
PAM software and PAM tool from miniOrange secure elevated accounts with centralized control, monitoring, and
least privilege enforcement across hybrid environments.
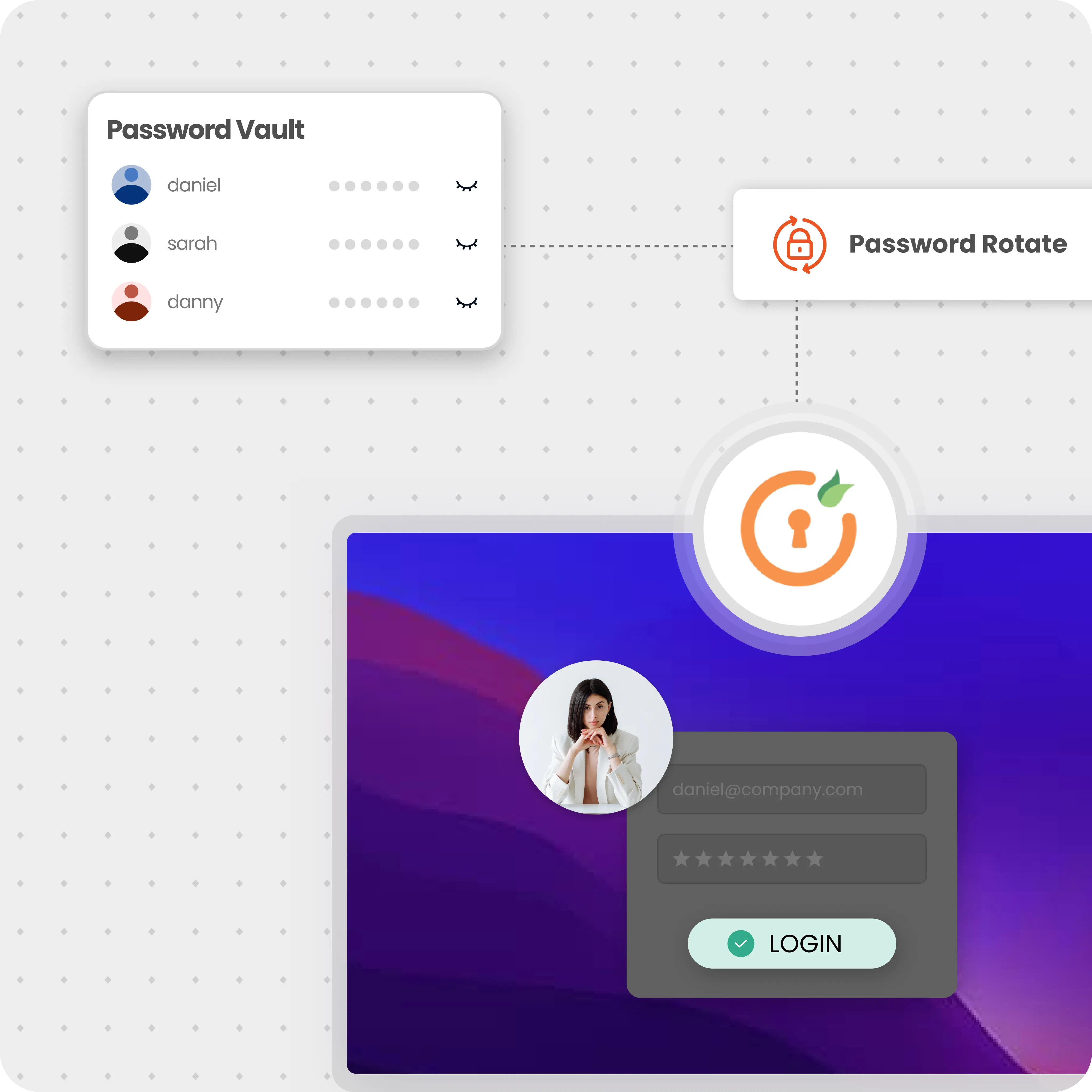
Protect privileged accounts using a centralized password vault that enforces strong passwords, MFA, and automated credential rotation for SSH, RDP, VNC, Active Directory, and databases, with AES-256 encryption.
Enable privileged session monitoring with real-time live streaming, recording, playback, instant session termination, and alerts through an intuitive dashboard for rapid threat response and compliance audits.
miniOrange PASM centralizes account discovery, securely stores credentials, enforces granular RBAC, enables temporary access workflows, and manages the full lifecycle of human and service accounts.
With PEDM, assign time-limited access to restricted resources tailored to user privilege levels, ensuring precise administrative control without standing privileges.
Provide Just-in-Time access to dynamically provision temporary access rights exactly when needed, eliminating standing privileges and minimizing security risks across sessions.
Hassle-free deployment without endpoint agents, enabling quick setup across servers, cloud, and hybrid infrastructure with zero disruption
Agentless endpoint control prevents malware, enforces least privilege on workstations/devices, aligns access with roles, and blocks unauthorized elevations.
No endpoint agents required, deploy quickly across servers, cloud, and hybrid setups without infrastructure changes or disruptions.
Round-the-clock technical assistance ensures rapid issue resolution, custom integrations, training, and ongoing optimization worldwide.
Affordable pricing delivers enterprise PAM capabilities without high licensing fees or complex maintenance overheads.
Intuitive dashboard simplifies policy setup, role management, and integrations with existing IAM, SIEM, and directories.
As a leading PAM solution provider, miniOrange delivers privileged access security tailored to
the unique risk, compliance, and access requirements of organizations across multiple industries.

Safeguard sensitive financial data and meet regulatory compliance requirements, including PCI DSS, SOX, and RBI guidelines. Control privileged access to core banking systems, payment gateways, and customer databases with comprehensive audit trails.
Learn More about Finance and Banking in PAM
Protect critical OT systems and industrial controls from unauthorized access. Secure production environments, manufacturing execution systems, and supply chain networks with automated privileged access controls and continuous monitoring.
Learn More about Manufacturing in PAM
Ensure HIPAA compliance while securing electronic health records and medical devices. Manage privileged access to patient data systems, diagnostic equipment, and healthcare applications with role-based controls and real-time session monitoring.
Learn More about Healthcare in PAMEnterprises face escalating risks from unmanaged privileged accounts, creating a need for
privileged access management solution.
Vault and rotate passwords automatically to block attackers exploiting stolen admin credentials during breaches.
Monitor sessions in real-time to detect anomalous behavior from privileged users before damage spreads.
Generate detailed logs and reports for SOX, PCI DSS, and HIPAA to simplify regulatory audits and avoid fines.
Start a free trial with us - the next step is all yours
Fully hosted in the cloud, no servers needed, with auto-updates and instant scaling for growing needs.
Install on your servers to keep sensitive data in-house for strict security and compliance rules.
Combine cloud and on-premises setups with minimal downtime and complete customization flexibility.
