Single Sign-On sounds simple in theory.
Add SAML, connect an identity provider, and users log in seamlessly.
So why does SSO often become one of the most stressful parts of a production system once it goes live?
And why do so many .NET and Umbraco teams that start with Sustainsys.Saml2 eventually regret the decision?
Let’s break it down—how Sustainsys actually works in real-world environments, why issues begin to surface, and where the hidden costs truly come from.
Why Sustainsys.Saml2 Looks Like the Perfect Choice at First?
If you’re building a .NET or Umbraco application, Sustainsys.Saml2 is usually the first name you hear.
On paper, it checks all the right boxes:
- It’s open source
- It’s widely referenced
- There’s no license fee
So the obvious question becomes:
Why pay for SAML when a free option already exists?
The answer only becomes clear after implementation begins.
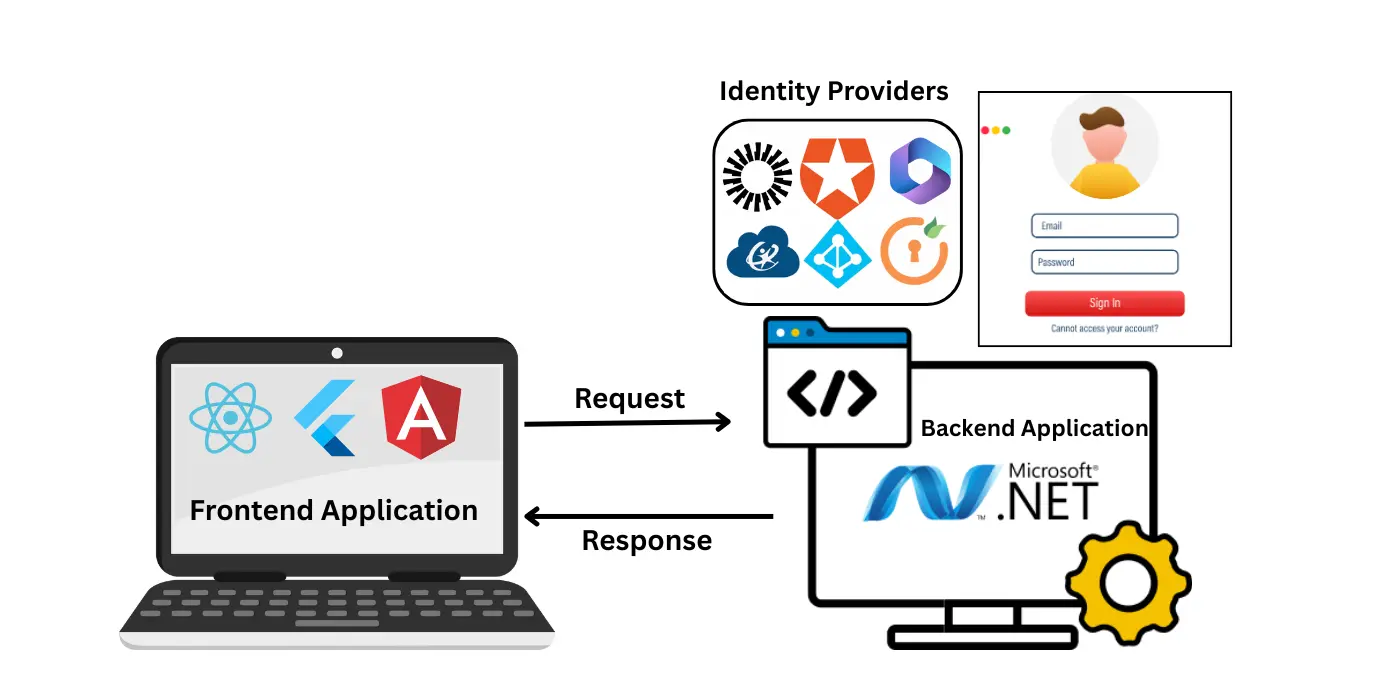
How Sustainsys.Saml2 Actually Works in Real Projects?
Sustainsys.Saml2 is not a full SSO product. It’s a developer-focused SAML library, and that distinction matters.
It provides the core SAML building blocks, but everything else is your responsibility:
- Configuration management
- Security hardening
- Certificate handling
- Error handling
- Logging and monitoring
- Ongoing maintenance
At the start, this feels manageable. But production environments rarely stay simple for long.
Why Do Problems Start Appearing After Go-Live?
Ask any team running Sustainsys in production and the same questions keep coming up:
- What happens when an IdP sends claims in an unexpected format?
- What happens when a certificate expires without warning?
- What happens when a customer wants a non-standard SAML configuration?
With Sustainsys, there is:
- No personalized support
- No guaranteed response time
- No dedicated engineer to analyze logs
- No accountability when authentication breaks
Teams often end up:
- Digging through GitHub issues
- Searching community forums
- Manually decoding SAML assertions
At this point, “free” starts costing days, or even weeks, of engineering time.
How Does Configuration Become a Bottleneck?
Sustainsys relies heavily on:
- Manual configuration files.
- XML metadata handling.
- Code-level changes.
Every new identity provider, certificate rotation, or environment change usually requires developer involvement—and often a redeploy.
Why does this matter?
Because in modern organizations, SSO is rarely managed only by developers.
- IT teams
- Security teams
- Operations teams
All need to interact with authentication settings. Sustainsys simply isn’t built for that audience.
Why Does Admin-First SSO Matter Today?
This is where commercial solutions like miniOrange .NET SAML SSO and Umbraco SAML SSO change the experience completely.
Instead of editing config files or touching code:
- Identity providers are configured through a dashboard
- Metadata is uploaded visually
- Attributes and roles are mapped via UI
- SSO flows are tested in real time
What takes hours—or days—with Sustainsys can often be done in minutes.
How Does Scaling Turn SAML into Technical Debt?
As applications grow, SSO requirements almost always expand:
- Multiple identity providers
- Role mapping and attribute transformations
- Detailed authentication logs and reports
- Stronger security visibility
With Sustainsys, these aren’t configurations—they’re custom code.
And custom SAML code comes with a cost:
- It must be maintained
- It must be tested
- It must be revalidated with every .NET or Umbraco upgrade
Over time, SSO becomes one of the most fragile parts of the system—something teams hesitate to touch because a small change can break authentication entirely.
Why Is Maintenance the Real Long-Term Cost?
Open-source projects move at the pace of community momentum—not enterprise timelines. That often means:
- No guaranteed fixes
- No planned security updates
- No assured compatibility with newer frameworks
With a commercial SAML solution like miniOrange:
- Security is actively monitored
- Updates are planned and supported
- Compatibility with newer .NET and Umbraco versions is part of the product, not an afterthought
For organizations that treat authentication as a critical security layer, this difference is huge.
How Do Non-Developers Get Locked Out with Sustainsys?
Here’s a hidden issue many teams overlook.
Not everyone responsible for SSO is a developer.
IT admins, support engineers, and system integrators often need to:
- Configure identity providers
- Troubleshoot login failures
- Rotate certificates
Sustainsys assumes deep technical expertise, creating dependency on a small group of engineers—and turning simple changes into delays.
miniOrange solves this with an admin-first design, enabling non-technical teams to manage SSO confidently and independently.
What Is the Biggest Cost Nobody Budgets For?
The real hidden cost of Sustainsys.Saml2 isn’t money. It’s opportunity cost.
Every hour spent:
- Debugging SAML flows
- Managing certificates manually
- Maintaining fragile custom logic
Is an hour not spent improving your product or serving your customers.
So, When Does Sustainsys Make Sense, and When Doesn’t It?
Sustainsys.Saml2 is a solid open-source library.
It can work well for:
- Small, internal projects
- Teams with deep SAML expertise
But for production-grade, customer-facing, or enterprise .NET and Umbraco applications, the trade-offs become hard to ignore.
Why Do Teams Choose miniOrange Instead?
miniOrange .NET SAML SSO and Umbraco SAML SSO don’t just offer SAML compliance.
They deliver real-world value:
- Faster implementation
- Lower operational overhead
- Better security visibility
- Easier administration
- Real support when things go wrong
In real-world software delivery, those benefits are often worth far more than a “free” license.

Leave a Comment