If you've ever logged into your work computer or accessed a company resource using your employee credentials, you've likely interacted with Active Directory. It's the system many organizations use to manage users, devices, and access permissions across their networks.
In fact, according to Frost & Sullivan, approximately 90% of Global Fortune 1000 companies utilize Active Directory as their primary method for seamless authentication and authorization.
In this blog, we'll explore what Active Directory is, how it functions, and why it's integral to modern IT infrastructure. Whether you're an IT professional or simply curious about enterprise network management, this guide provides clear insights into the role and significance of Active Directory.
What is Active Directory?
Now that we know how widely Active Directory is used, let’s look at what it actually is.
Active Directory, often shortened to AD, is a directory service developed by Microsoft. It helps organizations keep track of users, computers, printers, groups, and other resources on a network — all in one place. Instead of managing access manually for each device or user, AD allows IT teams to organize everything centrally.
Think of it as a digital phonebook combined with an ID verification system. It doesn’t just store names and passwords — it also enforces rules about who can do what. When you log into your work PC, try to access a shared folder or connect to a printer, Active Directory checks if you’re allowed to do that.
It’s been around since Windows 2000 Server and remains a key part of many IT environments today, especially for businesses using Windows-based systems.
How Does Active Directory Work?
Understanding what Active Directory is sets the stage, but it’s just as important to know how it functions in real-world environments.
At its core, Active Directory acts like a gatekeeper. When a user tries to log into a computer or access a company resource, AD checks their identity and decides whether they’re allowed in — and what they can do once they’re in.
Here’s a simple breakdown of how it works:
Authentication: When you enter your username and password, AD verifies your identity using stored credentials.
Authorization: Once you're authenticated, AD checks your permissions — for example, whether you're allowed to access a shared folder or install software.
Directory Structure: Everything in AD — users, devices, and resources — is organized in a structured way, like folders within folders. These are called Organizational Units (OUs) and help admins apply specific rules to different departments or teams.
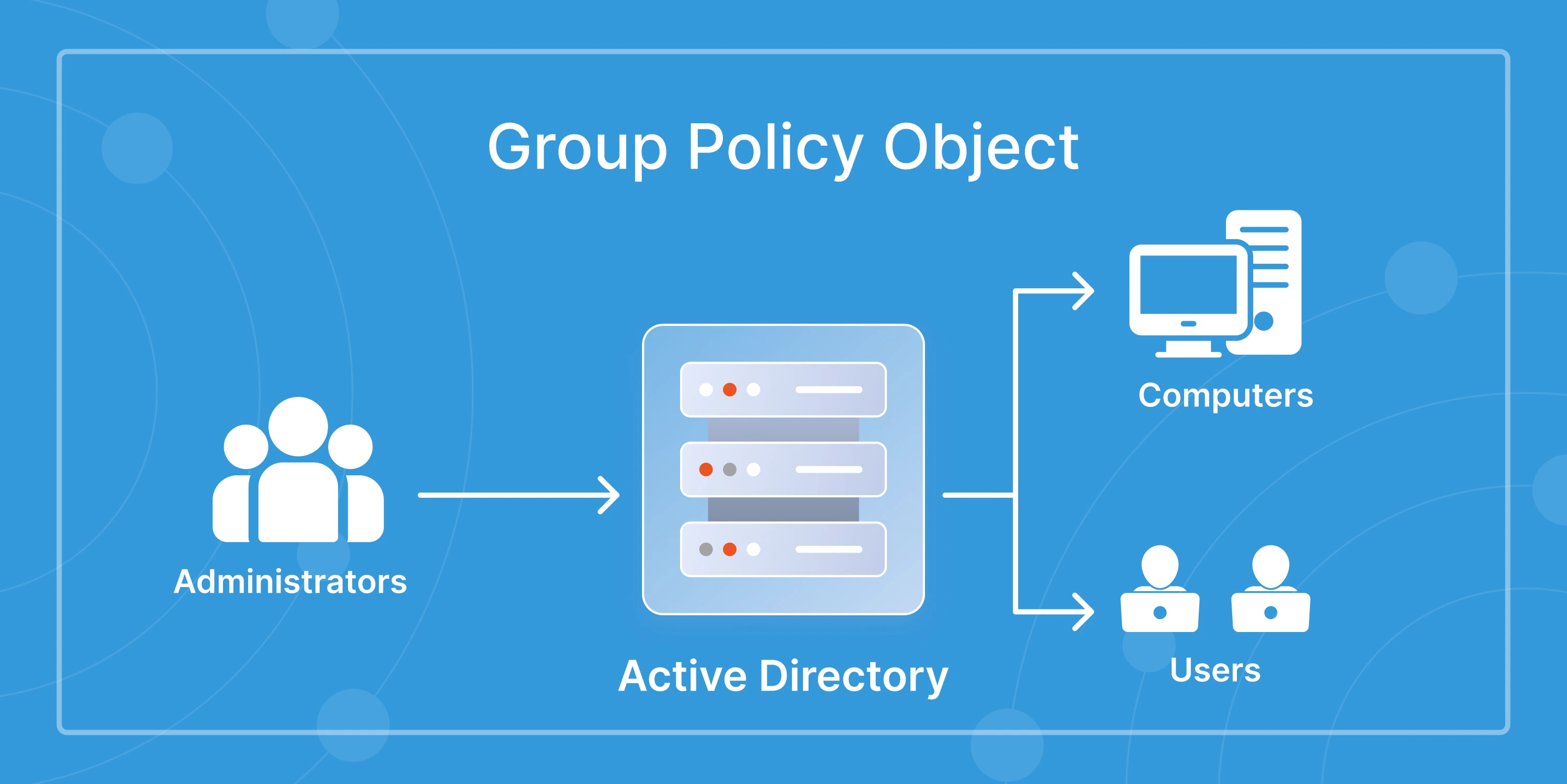
Group Policies: Admins can define security rules (like password policies or Restrict/Allow Apps, Network Settings, Startup/Shutdown Scripts) and apply them to groups of users through something called Group Policy Objects (GPOs).
Domain Controllers: These are the servers that run AD DS (Active Directory Directory Services). When you log in or request access, you’re talking to one of these servers.
Put simply, Active Directory creates a centralized system where user identities and permissions are stored and managed, helping organizations stay organized, secure, and in control.
Features of Active Directory
Active Directory is more than just a directory — it’s a framework that gives IT teams the tools to manage users, systems, and access across an organization. Its features are designed to support everything from small business networks to large enterprise environments.
Here are some of the core features and roles:
1. Centralized Management: Admins can manage user accounts, computers, security groups, and permissions from one central location — saving time and reducing errors.
2. Authentication and Authorization: AD verifies user identities (authentication) and determines what resources they can access (authorization), ensuring secure access to company assets.
3. Organizational Units (OUs): OUs allow for logical grouping of users and devices, often by department or location, making it easier to apply specific rules or policies.
4. Group Policy Management: Through Group Policy Objects (GPOs), admins can control settings for users and computers across the network, such as password policies, software restrictions, and security configurations.
5. Single Sign-On (SSO): With SSO support, users can log in once and access multiple systems or applications without re-entering credentials, improving both security and convenience.
6. Replication and Redundancy: Changes made on one Domain Controller are automatically replicated to others in the network, ensuring consistency and high availability.
Why Is Active Directory Used?
The main purpose of Active Directory is simple: to help organizations manage users and resources in a secure and organized way. Whether you're a small business or a global enterprise, AD gives you a reliable system to control who can access what, and under what conditions.
Here’s why Active Directory is used in most business environments:
- Centralized Control Over Users and Devices: Instead of managing each user or system individually, AD lets IT teams handle everything from a single point — from adding users to setting security rules.
- Improved Security and Access Management: AD enforces identity checks and access policies, helping ensure that only authorized users can access sensitive systems, files, or applications.
- Streamlined Onboarding and Offboarding: New employee? IT can quickly assign them the right permissions. Someone leaving the company? Access can be revoked instantly.
- Consistent Policy Enforcement: Group policies in AD help apply security and operational rules across all users or systems, such as password requirements or screen lock timeouts.
- Support for Scalability and Growth: As companies grow, so do their IT needs. AD is built to scale — whether you're managing 50 users or 50,000. This dominance highlights why AD remains the go-to solution for most IT departments — Microsoft Active Directory holds over 95% of the on-premises directory services market.
In short, Active Directory provides the structure, security, and flexibility modern organizations need to keep their digital environments under control.
Benefits & Advantages of Using Active Directory
For IT teams juggling dozens—or even thousands—of users, devices, and systems, Active Directory offers more than just structure. It brings a set of practical, day-to-day benefits that help keep everything secure, efficient, and under control.
Here’s how organizations benefit from using Active Directory:
- Enhanced Security: By enforcing strong authentication policies, AD helps reduce the risk of unauthorized access and internal threats. It also supports integrations with MFA (Multi-Factor Authentication) and conditional access.
- Simplified User and Device Management: Admins can manage thousands of user accounts, computers, and permissions without needing to configure each one manually. This saves time and ensures consistency.
- Seamless Integration with Other Systems: AD integrates smoothly with Microsoft services like Exchange, SharePoint, and Teams, and also supports third-party apps and services through LDAP or SSO.
- Automated Policy Enforcement: Using Group Policies, IT teams can apply security settings and usage restrictions across the organization, without touching every device.
- Support for Hybrid and Cloud Environments: Modern AD deployments can work alongside cloud services like Microsoft Entra ID, allowing organizations to manage users across both on-premises and cloud platforms.
- Improved Operational Efficiency: From automating routine tasks to reducing helpdesk tickets, AD streamlines IT operations and reduces the risk of human error.
Core Components of Active Directory
Behind the scenes, Active Directory is made up of several moving parts — each serving a specific function to keep the system organized, secure, and reliable.
Let’s break down the five core components of Active Directory you’ll come across in any standard deployment:
1. Logical Components:
These define how data is organized within AD. Think of them as the digital structure used to manage and group users, devices, and policies. Key logical components include:
- Domains – A logical grouping of users and resources.
- Organizational Units (OUs) – Containers used to organize users or computers within a domain.
- Trees and Forests – Larger structures that allow multiple domains to work together securely.
2. Physical Components:
These refer to the actual servers and their network locations. The most important one is the Domain Controller (DC) — the server that stores the AD database and responds to authentication requests.
Other physical components include:
- Sites – Represent physical locations in a network.
- Replication – Keeps domain data consistent across all DCs.
3. FSMO Roles (Flexible Single Master Operations):
These are specialized roles assigned to domain controllers to ensure certain tasks are handled by only one server at a time, preventing conflicts or duplication. There are five FSMO roles:
- Schema Master
- Domain Naming Master
- RID Master
- PDC Emulator
- Infrastructure Master
Each plays a unique part in keeping Active Directory running smoothly.
4. Protocols & Services:
Active Directory uses several protocols to function, the most important being:
- LDAP (Lightweight Directory Access Protocol) – Used to read and edit directory information.
- Kerberos – The primary protocol for secure authentication.
- DNS (Domain Name System) – Critical for locating domain controllers and resources on the network.
These services ensure users can log in, locate resources, and connect securely.
5. Active Directory Services:
Within the AD environment, certain server roles are responsible for key operations:
- Domain Services (AD DS): The main role of store directory data is to handle authentication and authorization across the network.
- Certificate Services (AD CS): Used to create and manage digital certificates for securing data and establishing trust.
- Federation Services (AD FS): Supports identity federation, enabling users to access systems across organizational boundaries (e.g., SSO between partners).
- Lightweight Directory Services (AD LDS): A lighter version of AD DS for applications that need directory services but not the full functionality of a domain controller.
- Rights Management Services (AD RMS): Protects sensitive information through encryption and sets usage restrictions on files and emails.
6. Active Directory Database:
All the information in AD — users, passwords, permissions, and computers — is stored in a central database called NTDS.dit. This file lives on the domain controller and is replicated to other DCs to maintain consistency.
Together, these components make up the foundation of Active Directory, enabling it to manage users and systems effectively across networks of any size.
How is Active Directory Structured?
Active Directory’s structure is what allows it to scale from small organizations to global enterprises, all while keeping everything organized and under control. It’s built like a hierarchy, both logically and physically, to reflect how businesses operate in the real world.
Here’s how the structure breaks down:
1. Forest – The Top of the Hierarchy:
A forest is the highest level in AD’s structure. It contains one or more domain trees and acts as a boundary for security and trust. Forests can support separate organizations while allowing selective collaboration between them.
2. Trees – Connecting Domains:
Multiple domains can be linked together in a tree structure. These domains share a common namespace and trust each other, making it easier to manage across business units or regions.
3. Domains – The Core Unit:
A domain is the basic unit of structure in Active Directory. It contains users, computers, and resources that share the same directory database and security policies. Each domain has a unique name, like yourcompany. local.
4. Organizational Units (OUs) – Grouping Within a Domain:
Organizational Units (OUs) help you group users or devices within a domain — often based on department, location, or function. IT teams use OUs to apply specific policies to specific groups without affecting the entire domain.
5. Sites – Reflecting the Physical Network:
While OUs and domains represent the logical structure, sites are used to represent physical locations, like branch offices or data centers. This helps optimize network traffic and authentication requests based on geographic location.
Putting It All Together
So, a typical AD structure might look like this:
Forest → Tree → Domain → Organizational Units → Users/Groups/Devices, with Sites managing traffic across physical locations.
This layered structure keeps directory data organized, scalable, and aligned with how your organization actually operates.
Conclusion
Active Directory plays a critical role in how organizations manage users, devices, and access across their networks. From verifying identities and enforcing policies to organizing resources and supporting secure collaboration, AD provides the backbone for IT operations in countless businesses worldwide.
Whether you're managing a small environment or a large, distributed workforce, understanding how AD works — and how to extend its capabilities — is key to building a secure and efficient IT setup.
If you're looking to simplify day-to-day Active Directory tasks like user management, password policies, account monitoring, or automated provisioning, tools like our [AD Tools solution] can help streamline operations while maintaining full control over your AD environment.
This guide is just the starting point — stay tuned for deeper insights on specific AD features and best practices for managing them effectively.

Leave a Comment