An IT helpdesk handling access requests all day is not unusual. A Finance hire waits for folder access because it has to be added manually. A contractor’s permissions stay active weeks after their project ends because no one tracks every group they were added to. These small gaps turn into bigger security risks when the environment grows.
This happens when Active Directory permissions depend on individual updates and scattered delegation. Access becomes inconsistent. Permission sets grow without structure. Users collect more access than they need, and admins end up fixing the same problems again and again.
Role-Based Access Control, or RBAC, changes this pattern. Instead of managing access user by user, RBAC assigns permissions through roles that match how teams actually work. It simplifies delegation, prevents clutter, and builds a predictable security baseline across the directory.
In this blog, we will break down how RBAC streamlines AD operations, reduces risks, and helps IT teams run access management with more clarity.
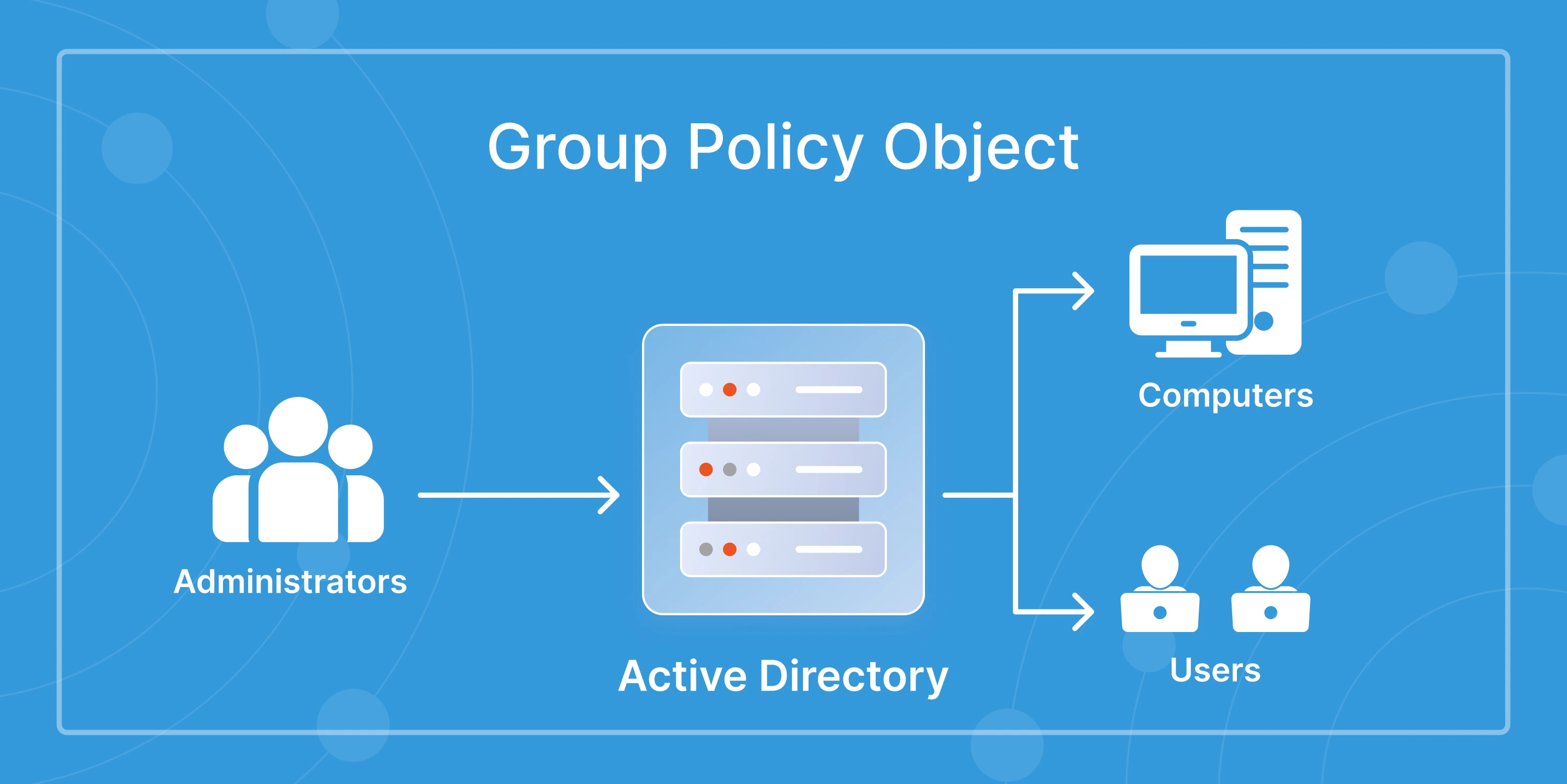
What Is RBAC in Active Directory?
Role-Based Access Control, or RBAC, is a simple idea. Instead of assigning permissions to individual users, you assign them to a role. Users inherit access from the role they belong to. This cuts down the work needed to manage permissions and keeps access consistent across teams.
Active Directory supports RBAC through groups, OUs, and predefined permission sets. A Finance role can have a fixed set of folder permissions. A Helpdesk role can have password reset rights. Anyone who belongs to these roles gets the same level of access without manual updates.
This model is popular because it reduces errors, simplifies delegation, and prevents users from collecting random permissions over time. It also gives IT teams a cleaner, more predictable way to manage access in complex environments.
Why AD Delegation Becomes Complex Without RBAC
Active Directory starts simple when there are only a few users. The trouble begins when teams expand, roles shift, and permissions start getting added on a case-by-case basis. Over time, access becomes inconsistent and difficult to track.
- Permissions pile up on individual accounts
When every request is handled manually, users end up with a long list of permissions that no one reviews. This creates overprivileged accounts and increases the risk of internal misuse or accidental exposure. - Nested groups make it harder to understand who has what
Group nesting looks convenient at first, but it becomes confusing when you try to audit access. A single user might inherit permissions from multiple group paths, and admins often lose visibility into the full chain. - Delegation depends on who remembers to update it
When responsibilities change, admins must remove old access, add new ones, and verify everything manually. These steps are often missed, leaving users with leftover permissions they no longer need. - Access updates rely on individual judgment
Without a structured role model, every admin handles access differently. Two users in the same department may end up with completely different permission sets.
Pro Tip: Role templates in miniOrange AD Tools reduce this complexity by assigning access based on roles instead of individual updates. This gives your directory a cleaner baseline and lowers the chance of permission clutter.
Benefits of RBAC in Active Directory
RBAC solves most of the permission problems that show up in a growing AD environment. It replaces individual decisions with structured access models that match how teams actually work.
- Faster onboarding for new hires
Every new employee gets the right access on day one because the role already knows what they need. This reduces access tickets and saves time for both IT and the new hire. - Consistent access across departments
Users in the same role follow the same access pattern. No more guessing who should have which permissions or group membership. - Lower risk of overprivileged accounts
RBAC enforces least privilege by default. Users get only the access required for their job, not whatever was added over months of manual updates. - Cleaner's role changes when teams shift
Switching departments is simple. Move a user to a new role, and their access updates automatically. No need to hunt down old permissions.
Pro Tip: miniOrange updates AD permissions automatically during role changes, which prevents leftover access rights from staying active.
- Easier compliance and auditing
Auditors can check role definitions instead of reviewing hundreds of individual accounts. This shortens audit cycles and reduces back and forth. - Less permission clutter to clean up
RBAC reduces random permissions, outdated access, and one-off exceptions. This creates a cleaner AD environment with fewer blind spots. - Scales smoothly with team growth
Whether you have 50 users or 5,000, RBAC keeps access predictable and easier to manage at every stage of growth.
How RBAC Simplifies AD Delegation
Once roles are defined, delegation becomes easier and more predictable. You no longer chase individual accounts or update permissions every time someone changes a team or responsibility.
- One role assigns multiple permissions at once
Instead of adding permissions one by one, you assign a user to a role, and the entire permission set applies instantly. This keeps access consistent and reduces manual work. - Departments follow a fixed access pattern
A Helpdesk role can reset passwords. A Finance role can access specific folders. A Sales role can view shared CRM resources. These rules stay the same for everyone in that role, which removes guesswork. - Offboarding becomes clean and straightforward
Removing a user from a role automatically removes all connected permissions. You do not need a checklist or a separate follow-up to ensure access was fully revoked.
Pro Tip: miniOrange triggers provisioning and deprovisioning tasks automatically when users move between roles, so access updates never depend on manual steps.
- Delegation can be assigned to non-admin teams confidently
Managers or team leads can assign users to roles without touching sensitive AD permissions. This keeps AD secure while reducing IT load. - Reduces repetitive access tickets
Since roles handle most of the common access needs, the helpdesk receives far fewer permission requests.
How RBAC Strengthens AD Security
RBAC does more than simplify access assignments. It strengthens your security posture by controlling how permissions spread across the directory and how users interact with sensitive resources.
- Enforces least privilege without extra effort
Users get only the access they need based on their role. Nothing more. This reduces accidental exposure and limits how far an attacker can move if an account is compromised. - Blocks common privilege escalation paths
When access is assigned manually, users often collect permissions over months or years. RBAC keeps access tied to the role, which prevents stacked privileges that attackers can exploit. - Removes permission sprawl in large teams
Access tends to grow when no one tracks it. RBAC keeps a clean structure where permissions are attached to roles, not individuals. This reduces hidden risks inside large AD environments. - Makes audits and reviews faster
Instead of checking every user, auditors can review role definitions and confirm that access controls follow your internal policies. This speeds up compliance reviews and reduces audit fatigue.
Pro Tip: miniOrange adds workflow approvals for sensitive actions. This ensures risky operations like privilege changes or access to high-value systems are reviewed before they take effect.
- Reduces lateral movement inside AD
Attackers rely on overprivileged accounts to move through systems. When roles are tightly defined, the blast radius of any compromised account becomes smaller. - Supports a stronger identity hygiene practice
Clear roles make it easier to enforce naming standards, lifecycle rules, and periodic access reviews. Consistent identity hygiene leads to fewer blind spots in day-to-day operations.
Implementing RBAC in Active Directory
Moving to RBAC does not require a redesign of your entire AD setup. It simply replaces individual access decisions with a structured model that scales better. A phased approach works best, especially in environments with existing permission clutter.
- Identify the core job roles in your organization
Start with functional teams like HR, Finance, IT, Sales, and Operations. List the tasks they perform daily so you can map the right permissions later. - Map each task to the permissions it needs
If HR updates employee attributes, map the exact AD permissions required. If Helpdesk resets passwords, list the groups or rights needed. This creates a clear link between real work and the access behind it. - Build permission sets for each role
Translate these tasks into AD groups. Each role gets its own group or set of groups, which becomes the permission source for every user in that role. - Test with a small pilot team
Pick a single department and assign roles to a limited group of users. This helps validate that each role gives the right access without excess permissions. - Roll out roles across the directory in phases
Move department by department. This avoids confusion and lets you adjust roles as new needs appear. - Schedule quarterly access reviews
RBAC is easier to maintain when you revisit roles regularly. This prevents role drift and keeps permissions aligned with your current workflows.
5 Common RBAC Mistakes and How to Avoid Them
RBAC delivers long-term value only when the structure stays disciplined. These are the mistakes most teams make and the exact steps to avoid them.
- Creating too many roles
Mistake: Teams sometimes build a new role for every small difference in access. This creates role clutter and makes the model harder to manage.
How to avoid it: Keep roles tied to job functions, not individual requests. Use broad roles like HR, Finance, and Helpdesk, and handle small variations with approval-based temporary access instead of new roles. - Mixing user-specific permissions with role-based access
Mistake: Admins assign direct permissions to individual accounts when they want a quick fix. This breaks the RBAC model and creates hidden access paths.
How to avoid it: Route every permission through a role. If a user needs extra access, create a temporary role with an expiry date rather than modifying their account directly. - Forgetting to retire old or unused roles
Mistake: Roles created for temporary projects often remain active long after the project ends, granting permissions no one tracks anymore.
How to avoid it: Review roles quarterly. Remove or merge any role that no longer maps to a current job function. - Poor naming standards
Mistake: Roles like Group 4 or Custom Access tell you nothing about the permissions they grant. This slows down audits and leads to confusion.
How to avoid it: Use clear and descriptive names like HR Basic Access, Finance Read Access or Helpdesk Tier 1. Name roles so any admin can understand their purpose instantly. - Not separating temporary access from permanent access
Mistake: Contractors or project-based users are assigned permanent roles. This leaves long-term access behind after their work is complete.
How to avoid it: Create time-bound roles for contractors and short-term projects. Assign an expiry date so permissions drop automatically at the end of their engagement.
Best Practices for RBAC in Active Directory
A well-designed RBAC model keeps your directory predictable, secure, and easier to maintain over time. These practices help you get long-term value from your roles without adding clutter.
- Keep your role list simple
Start with broad functional roles like HR, Finance, Sales, and IT Helpdesk. Avoid creating new roles for minor access differences. Simplicity keeps access predictable. - Use a clear naming standard
Names like HR Basic Access or Finance Restricted Access make the purpose obvious. Good naming standards speed up audits and reduce confusion when multiple admins manage AD. - Align roles with business functions
Tie each role to real responsibilities. A role should represent what a team actually does, not what one user asked for in a one-off request. - Automate provisioning where possible
Automation ensures consistent access assignments and reduces manual errors. When a user moves or leaves, access updates happen on time. - Review access on a quarterly cycle
Roles evolve as teams grow. Quarterly reviews help identify outdated roles, unused permissions, and access that no longer match current job functions. - Create time-bound roles for temporary access
Short-term projects and contractors should have their own roles with expiry dates. This ensures temporary access does not become permanent. - Avoid mixing technical and business roles
Keep system-level roles separate from business roles. This prevents technical permissions from leaking into functional roles.
Conclusion
RBAC brings clarity to an area of AD that usually becomes chaotic with time. When access flows through well-defined roles instead of individual updates, delegation gets easier, security improves, and permission clutter stays under control. IT teams spend less time fixing inconsistencies and more time focusing on real operational work. Users get the access they need faster, and audits run with fewer surprises.
As environments grow and responsibilities shift, a role-based model gives AD a stable structure to work with. It replaces guesswork with predictable rules and keeps your security posture steady. This is also where the miniOrange AD Management Tool adds value. It supports role-based delegation, automates provisioning tasks, and helps you maintain clean access hygiene as your directory scales.
With the right roles, clear standards, and regular reviews, RBAC becomes a practical way to keep AD secure, consistent, and aligned with how your business operates.
FAQs
1. Why should I use RBAC for AD delegation?
RBAC removes the guesswork from delegation. When permissions are tied to roles, IT teams no longer update access one user at a time. Delegation becomes predictable, faster, and less prone to errors.
2. How does RBAC improve AD security?
RBAC enforces least privilege by default. Users get only the access they need for their job. This reduces permission sprawl, blocks privilege escalation paths, and lowers the impact of compromised accounts.
3. Does RBAC replace all AD groups?
No. RBAC works with AD groups. Each role is usually backed by one or more groups. You may still keep technical or system-specific groups, but access should be routed through roles whenever possible.
4. How do I handle temporary or project-based access with RBAC?
Create time-bound roles for contractors or project work. Assign an expiry date so access drops automatically when the work ends. This keeps your long-term roles clean.
5. How can I automate RBAC in Active Directory?
Automation helps keep role changes consistent. Tools like the miniOrange AD Management Tool update permissions automatically when users join, exit or switch roles. This reduces errors and avoids leftover access.



Leave a Comment