Active Directory (AD) will still run the show for identity and access management across most enterprise networks. Thousands of companies worldwide depend on it to manage users, control access, and keep systems running. But here’s the twist in the story - attacks on AD environments are up by 42% this year alone (source: Cayosoft), with various new vulnerabilities.
That’s where LDAP authentication comes in.
This blog breaks down how LDAP authentication works with Active Directory, why it matters, and how to set it up on platforms like WordPress using the miniOrange LDAP plugin. Whether you're looking to streamline logins or tighten security, understanding this integration is key.
Why Active Directory Remains Relevant?
Every organization has its own internal structure, some flat, some deeply nested, and both Active Directory and LDAP servers are designed to accommodate that variety. These directory services allow you to model your organization digitally, creating a structure that mirrors departments, teams, and roles.
Resources are arranged in a logical, hierarchical format, whether you're using AD or an LDAP-based directory. This makes it easy for users to locate systems or services by name, without needing to know where they’re physically hosted. That logical abstraction not only simplifies access but also makes administration and scaling much more efficient.
What is Active Directory?
Active Directory, often known as AD, is a Microsoft-developed proprietary directory service that operates on its own Windows Servers. Active Directory (AD) is a database and set of services that provides centralized management of users, computers, and other objects within the network. Active Directory connects different users with the network resources they need to get their work done. It also simplifies user management as it acts as a single repository for all user and computer-related information.
How does Active Directory Work?
When a user logs into a system, AD checks their username and password against its stored records. If the credentials match, the user is authenticated. AD then determines what that user is allowed to access, enforcing access control based on their roles, group memberships, or assigned policies.
Active Directory Structure and Elements: The Core Building Blocks
AD uses a hierarchical model to organize information. This structure makes it easy to manage large numbers of users and devices.
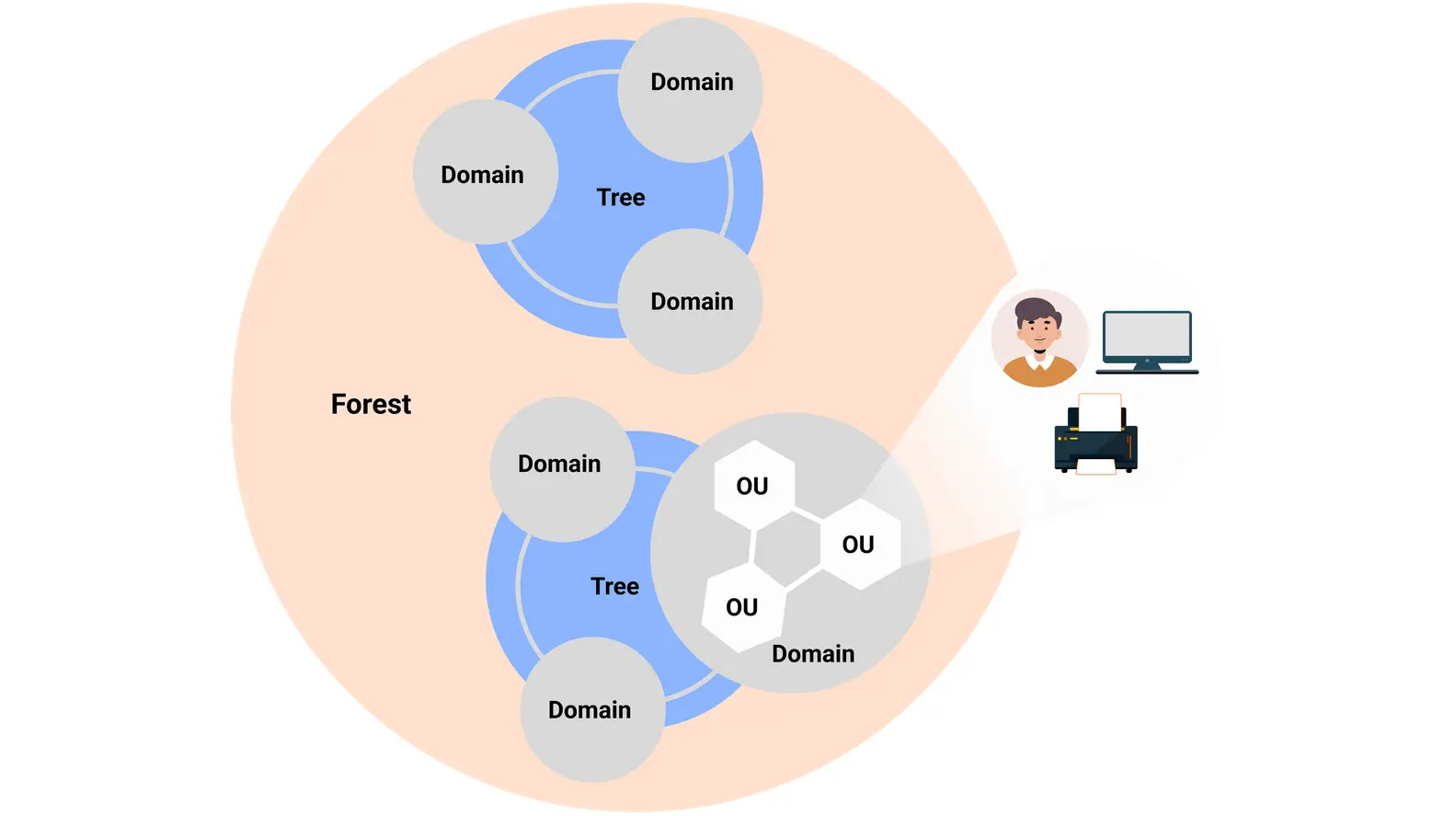
- Objects: Represent users, computers, printers, or any network resource. Each object has unique attributes.
- Organizational Units (OUs): Logical groupings of objects—used for applying policies and delegating control.
- Domains: Collections of objects and OUs under a common database and security boundary.
- Trees: A set of related domains connected by trust relationships.
- Forest: The topmost layer, containing one or more domain trees that share a common schema and configuration.
This model allows AD to reflect the real-world structure of an organization, departments, teams, and locations, while keeping user management and policy enforcement consistent.
What is LDAP Authentication?
LDAP (Lightweight Directory Access Protocol) is a protocol used to access and authenticate users against directory services like Active Directory, OpenLDAP, or FreeIPA. It works by verifying a user’s credentials (username and password) before granting access to systems or applications.
When a user attempts to log in, the system sends their credentials to an LDAP server. The server checks if the credentials match what’s stored in its directory. If they do, access is granted. If not, the request is denied.
LDAP is Not a Directory. It’s the Protocol
It's important to understand that LDAP is not a directory itself, it's the protocol used to talk to one. Think of it as the bridge that allows your application or website to securely communicate with your identity system. That system could be:
- Microsoft Active Directory
- OpenLDAP
- Azure Active Directory
- FreeIPA
- Other LDAP-compliant directories
LDAP supports both authentication (verifying who the user is) and authorization (defining what the user is allowed to do), making it a reliable and widely used standard in enterprise security setups.
How LDAP Authentication with Active Directory Works Using the miniOrange Plugin
If your website is built on a CMS like WordPress, Drupal, or Joomla, and you want users to log in using their existing Active Directory (AD) credentials, the miniOrange LDAP/AD Login for Intranet Plugin makes it possible, without syncing user data or duplicating accounts.
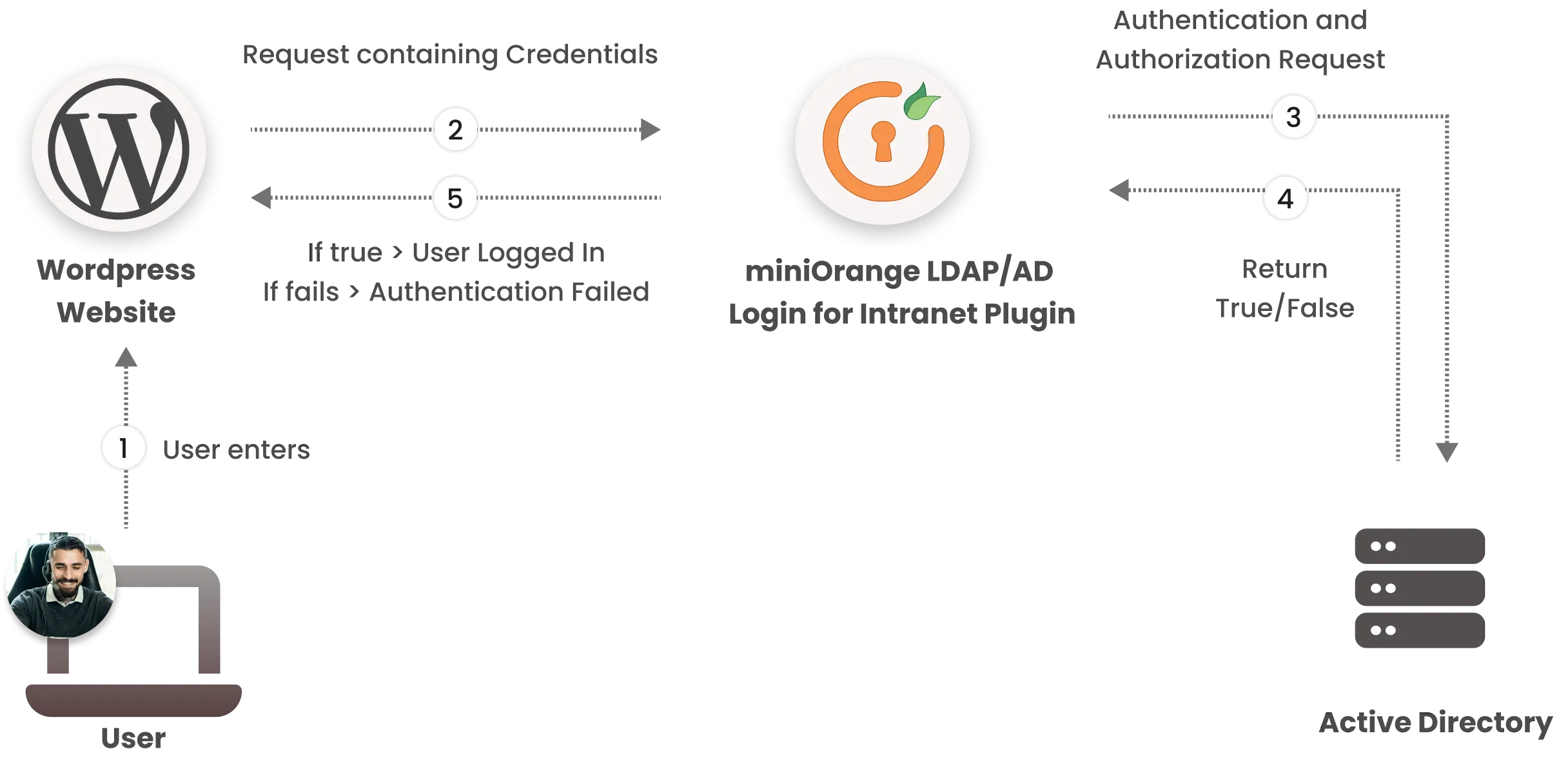
Step-by-Step Login Flow:
1. User Attempts Login
A user enters their AD username and password on the website login page.
2. Plugin Captures Credentials
The miniOrange LDAP/AD Intranet Plugin captures these login credentials and prepares an LDAP request.
3. LDAP Request Sent to Active Directory
The plugin sends an LDAP Authentication and Authorization request to your Active Directory server.
4. Directory Lookup and Validation
Active Directory checks:
- If the user exists under the configured search base (this includes all targeted Organizational Units or OUs).
- Whether the username and password match.
5. Response from AD
Active Directory responds with a result:
- Successful Bind: If the username and password are correct, AD returns a successful bind response, indicating valid credentials.
- Bind Failure: If the credentials are incorrect or the user does not exist under the configured search base, AD returns an error, such as "Invalid Credentials" or "User Not Found."
6. User Access Granted or Denied
Based on the response, the plugin either logs the user in or displays an appropriate error message.
This entire process happens in real time. The plugin doesn’t store credentials; authentication is always handled directly by your AD.
Want to Dive Deeper?
If you're looking for a detailed breakdown of real-world use cases, integration workflows, and how LDAP login can reduce operational overhead, check out our white paper: Enhancing Business Efficiency with WP LDAP/AD Login for Intranet Sites Plugin
How LDAP Helps Secure Internal WordPress Sites?
Internal WordPress sites often hold sensitive data, HR tools, employee portals, or intranet dashboards. Using LDAP authentication adds a critical layer of security by ensuring only authorized users from your internal directory can access these resources. Here’s how LDAP tightens security for internal sites:
- No Public Registration: Users can't sign up or bypass login; access is restricted to verified users in your Active Directory or LDAP directory.
- Credential Validation at the Source: Logins are verified directly against your directory, reducing the risk of password leaks or stored credentials in WordPress.
- Access Based on Role or Department: You can control access using AD groups, ensuring that only specific users or departments can view or manage certain parts of the site.
- Account Disablement Is Instant: Once a user is disabled or removed from your directory, their access to the site is automatically revoked, no manual cleanup required.
- Audit-Ready Setup: LDAP authentication aligns with most internal compliance requirements, making it easier to audit and report on user access.
Key Benefits of LDAP Authentication with Active Directory
Using LDAP authentication with Active Directory doesn’t just streamline login, it simplifies identity management across your WordPress site. Here’s how it helps:
1. Centralized Access Control
All user logins are authenticated directly against your AD or LDAP server. That means no duplicate accounts, no manual provisioning, and no syncing delays, just one source of truth for user identity.
2. Better Security, Fewer Password Risks
Since passwords are never stored in WordPress, the risk of credential leakage is drastically reduced. Combine this with Active Directory’s existing password policies, account lockouts, and group restrictions, and you strengthen your overall access control.
3. Easy Role-Based Access
You can define who can access what based on existing AD groups. Whether it’s giving managers admin-level access or restricting certain content to specific departments, role-based login becomes effortless.
4. Reduced IT Workload
No more repetitive account creation or password resets. With users logging in via LDAP, your IT team can spend less time on admin tasks and more time on what matters.
5. Scalable for Any Setup
Whether you have 50 users or 5,000, the LDAP login flow stays fast and consistent. It works across multiple Organizational Units (OUs), supports complex search filters, and integrates with hybrid or multi-domain environments.
Conclusion
LDAP authentication with Active Directory gives you the best of both worlds, centralized control from AD, and flexible access for your WordPress site. Whether you're running an internal portal, an employee dashboard, or a secure content hub, the miniOrange LDAP/AD Login for Intranet Plugin connects your WordPress users to your directory without extra effort or risk. It simplifies user management, improves login security, and ensures that only the right people get access to the right content, all while keeping your AD as the single source of truth.
FAQs
What is the difference between LDAP and Active Directory?
LDAP is a protocol used to access directory services. Active Directory is Microsoft’s directory service that supports LDAP (among other protocols) and stores user, group, and device information in a structured format.
Can I use LDAP authentication with WordPress?
Yes. You can use the miniOrange LDAP/AD Login plugin to authenticate users on your WordPress site using credentials stored in Active Directory, OpenLDAP, or other LDAP-compliant directories.
Does the plugin store any passwords?
No. The plugin only sends credentials to your LDAP server for validation and does not store or cache them locally.
Can it support multiple OUs or nested groups in AD?
Yes. The plugin supports custom search filters, multiple OUs, and nested group structures to match complex AD hierarchies.
Will it work with non-Windows LDAP directories?
Yes. Besides Microsoft AD, the plugin also supports OpenLDAP, FreeIPA, JumpCloud, and other LDAP-compatible systems.



Leave a Comment