Iam
iam
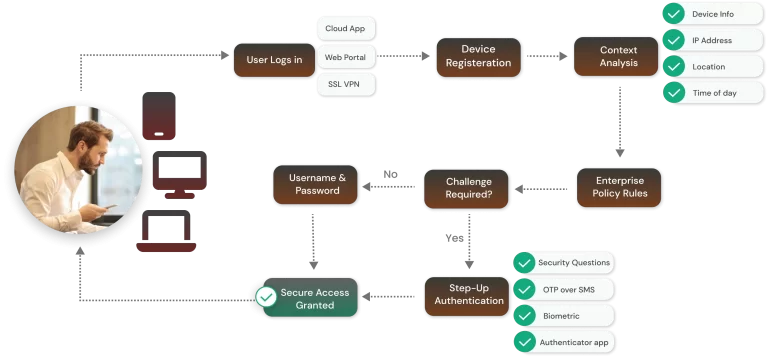
5 Reasons to Deploy Context-Based Authentication
Thu May 12 2022
iam
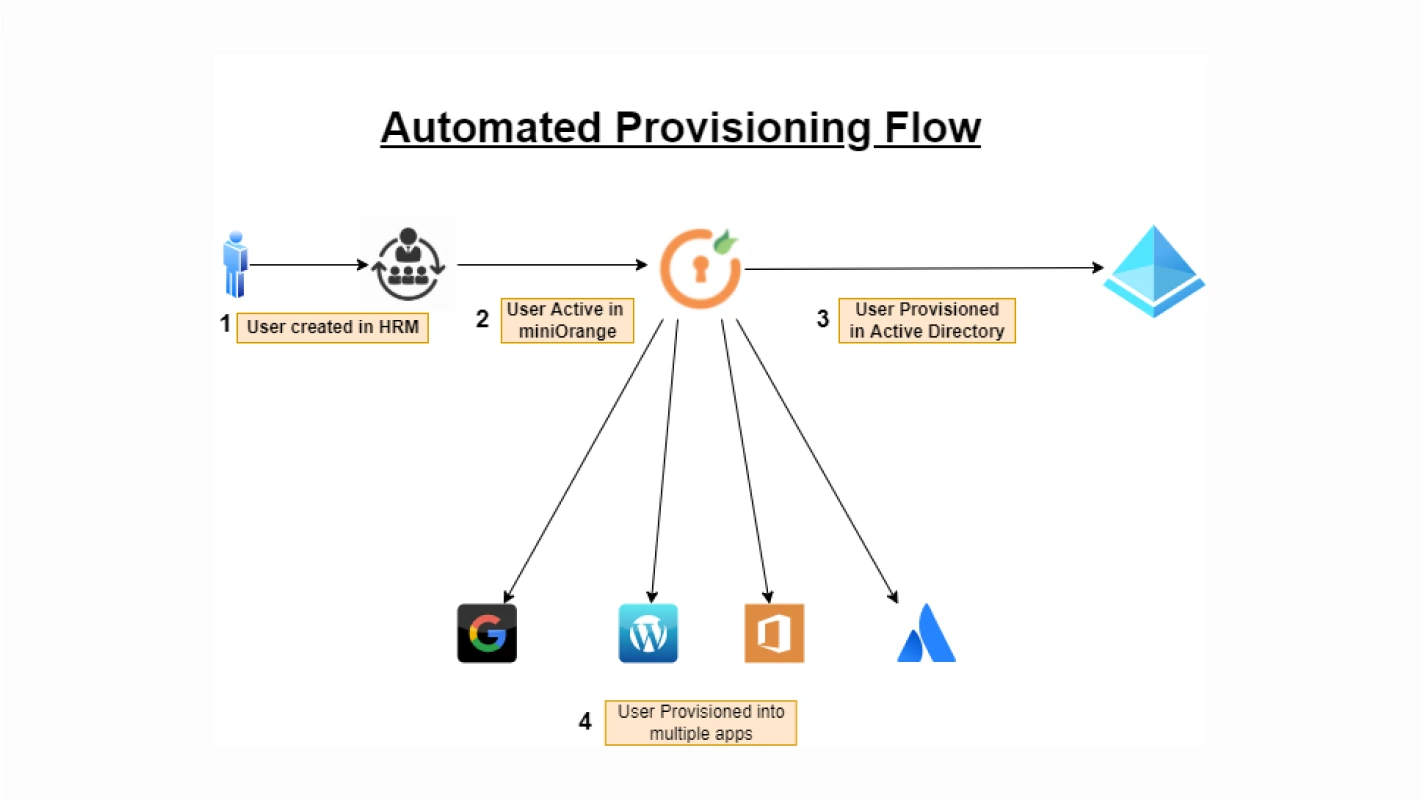
Automated Provisioning | 4 main benefits of Automated User Provisioning
Thu May 12 2022
concepts
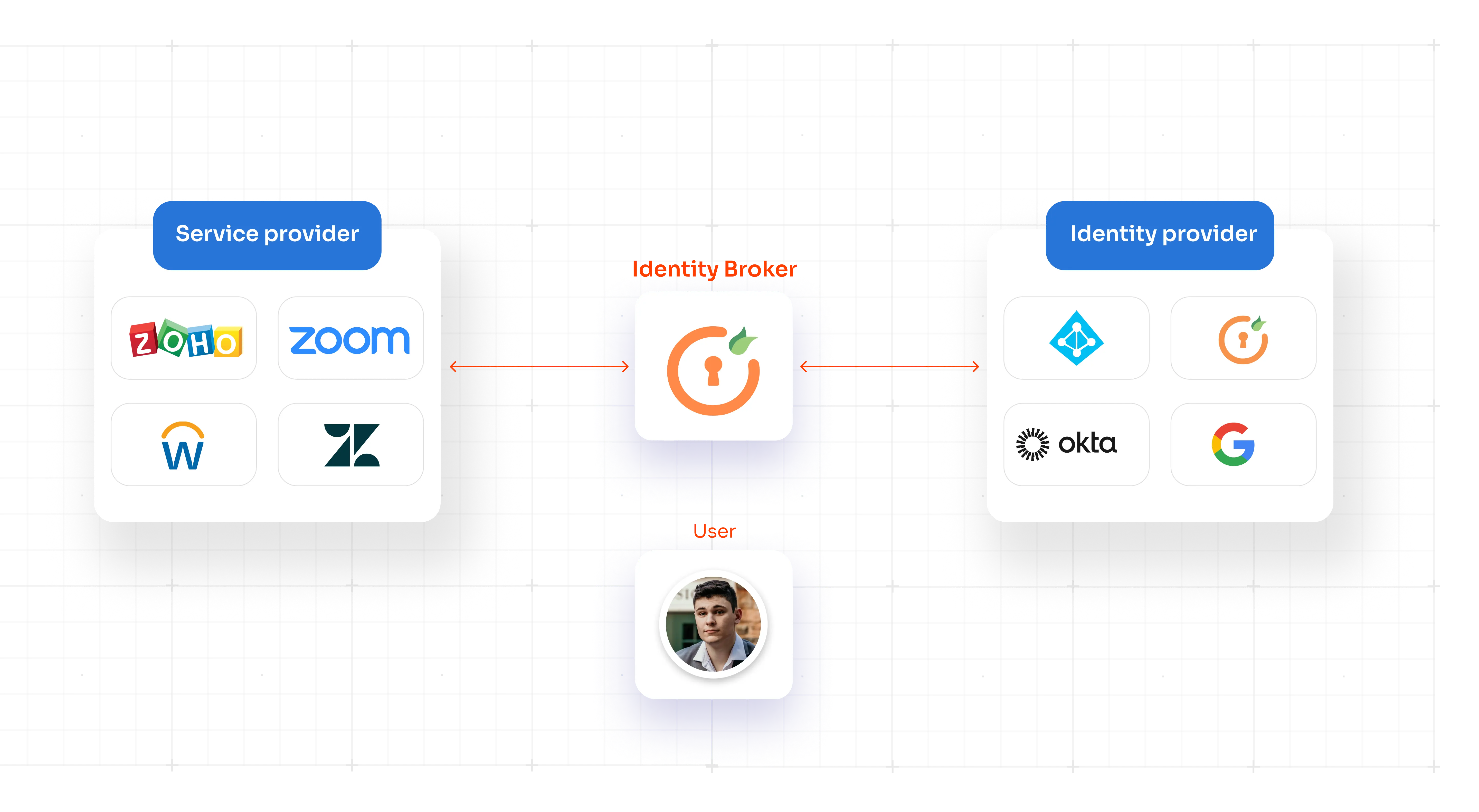
Azure Active Directory SSO for Enterpises | Azure AD Integration
Thu Feb 17 2022

concepts
Custom Database Connection
Thu May 12 2022
iam
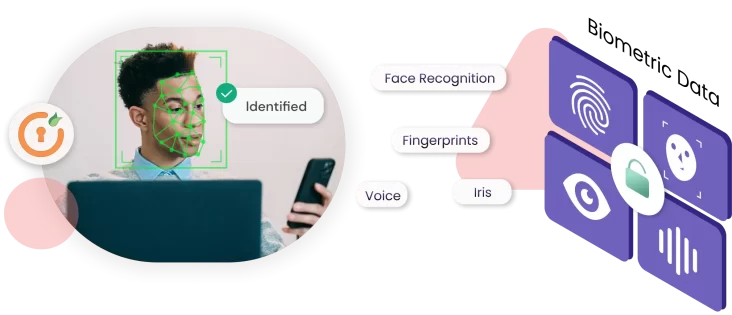
Know Everything About Biometric Authentication
Thu May 12 2022

iam
IAM vs. PAM: What’s the difference?
Mon Sep 25 2023

Solutions
IDAM for Banking and Finance Sector to ensure regulatory compliance
Fri Mar 17 2023

iam
Identity and Access Management (IAM) Market After Economic Turndown
Thu May 12 2022

iam
What is Identity Federation Services? How To Secure Applications with SAML and OpenID Connect
Mon Sep 25 2023
concepts
LDAP Authentication with Active Directory
Tue Aug 30 2022

iam
How to enable secure Mobile App authentication - SSO for Mobile apps
Wed Jul 19 2023
concepts
Multi-Factor Authentication (MFA) for Active Directory (AD)
Mon Aug 29 2022

iam
The necessity of Banking Cybersecurity
Wed Mar 01 2023
announcements
Salesforce Multi-factor Authentication | Salesforce MFA
Thu May 12 2022
concepts
Secure VPN with Multi-Factor Authentication
Sun Feb 26 2023

concepts
Implementing SSO Support For Enterprise Apps
Mon Jul 01 2024
concepts
Migrating from RSA Access Manager to miniOrange Identity Platform
Sat Mar 05 2022

concepts
What is a Directory service and Why do you need one?
Thu May 12 2022

iam
Adaptive Authentication
Wed Jun 19 2024
concepts
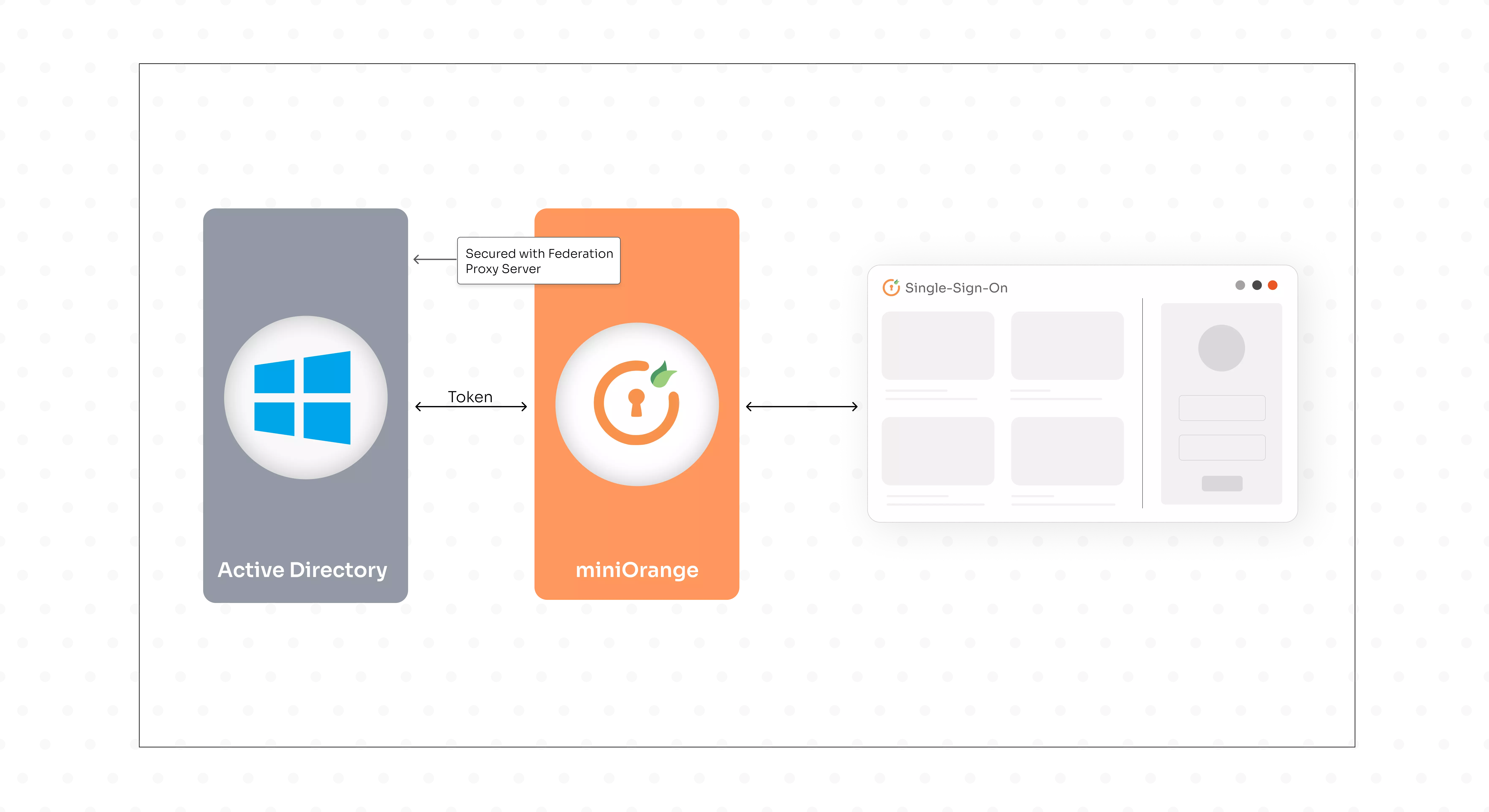
What is ADFS?
Fri Feb 18 2022
concepts
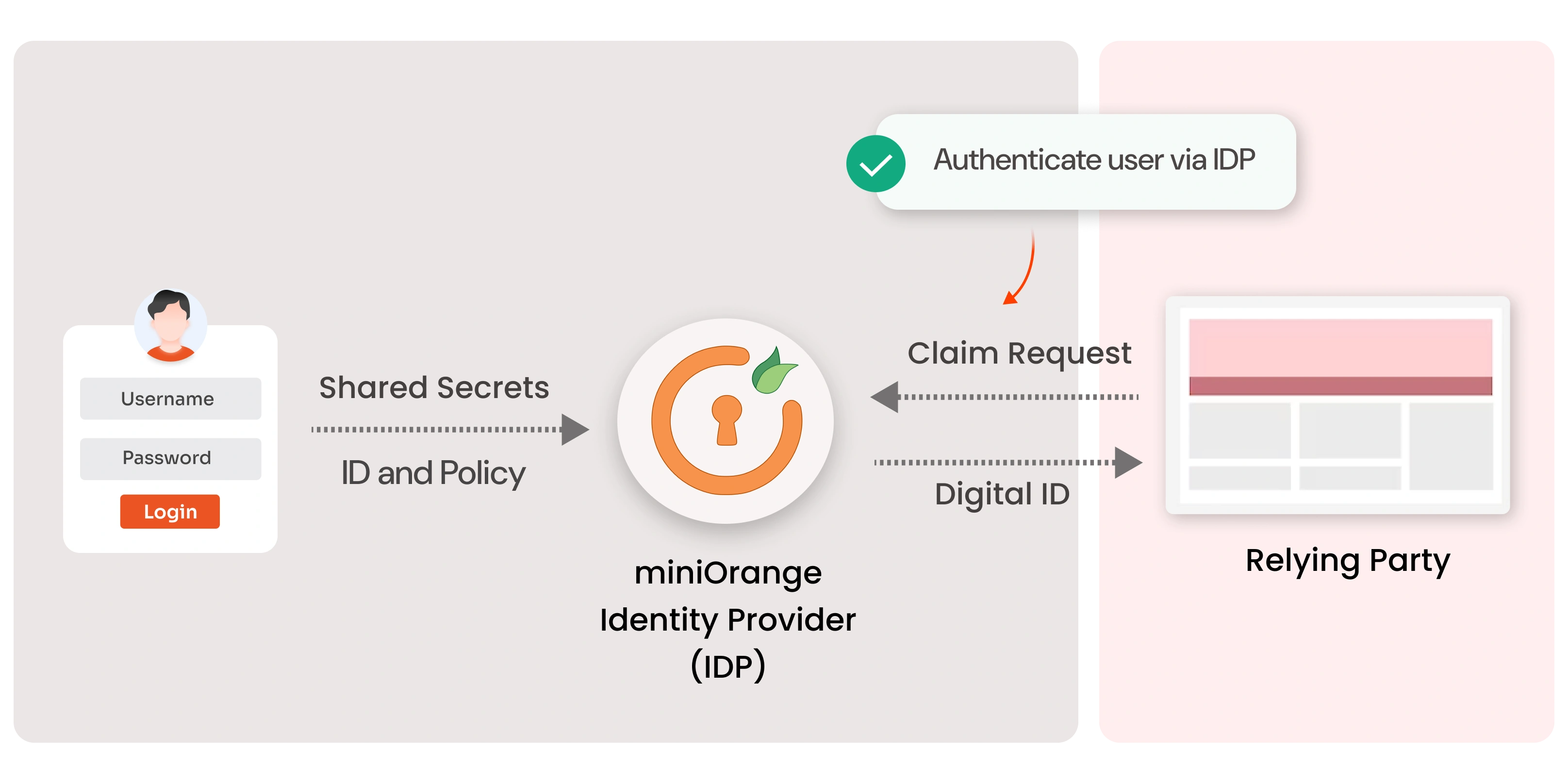
What is an Identity Provider (IDP)?
Thu May 12 2022
concepts
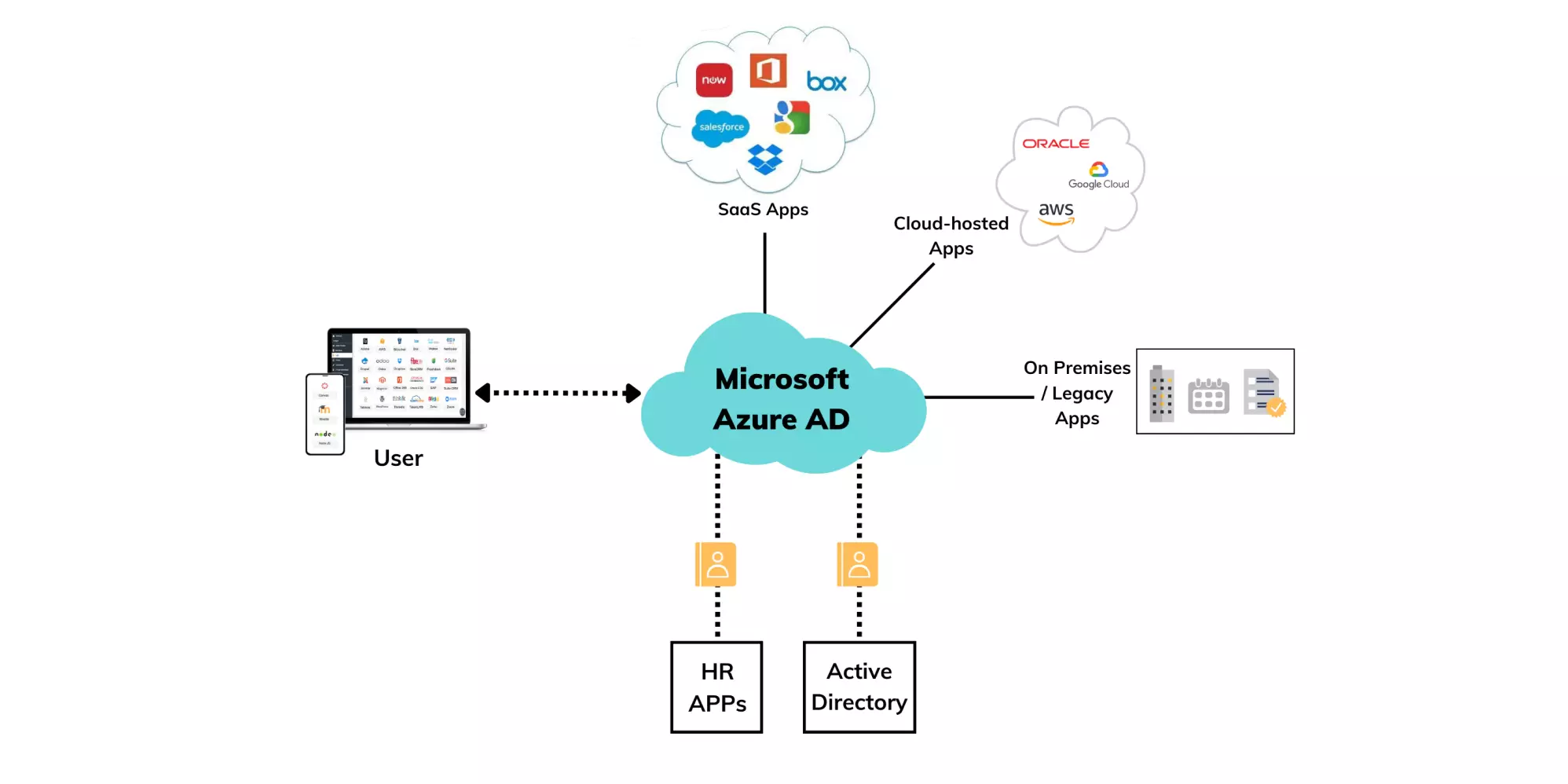
What is Azure Active Directory? | Microsoft Azure AD
Thu Feb 17 2022
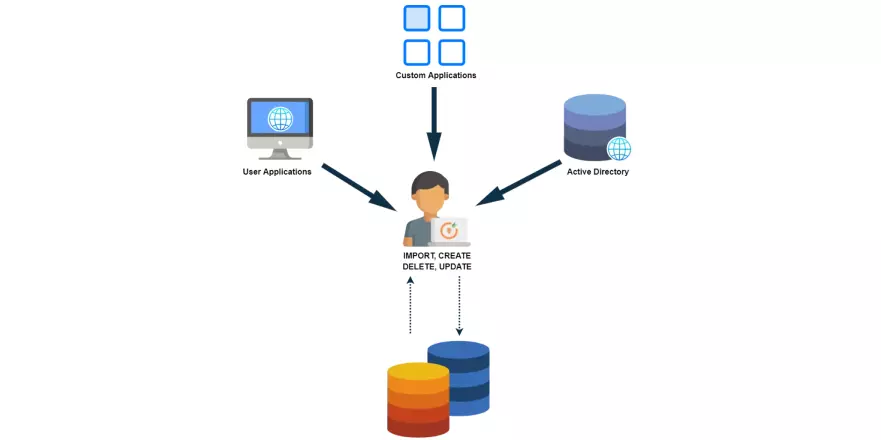
concepts
What is Deprovisioning & why is it important?
Fri Aug 19 2022

concepts
What is G Suite IP Restriction? Enable IP Restriction for G Suite
Thu May 12 2022
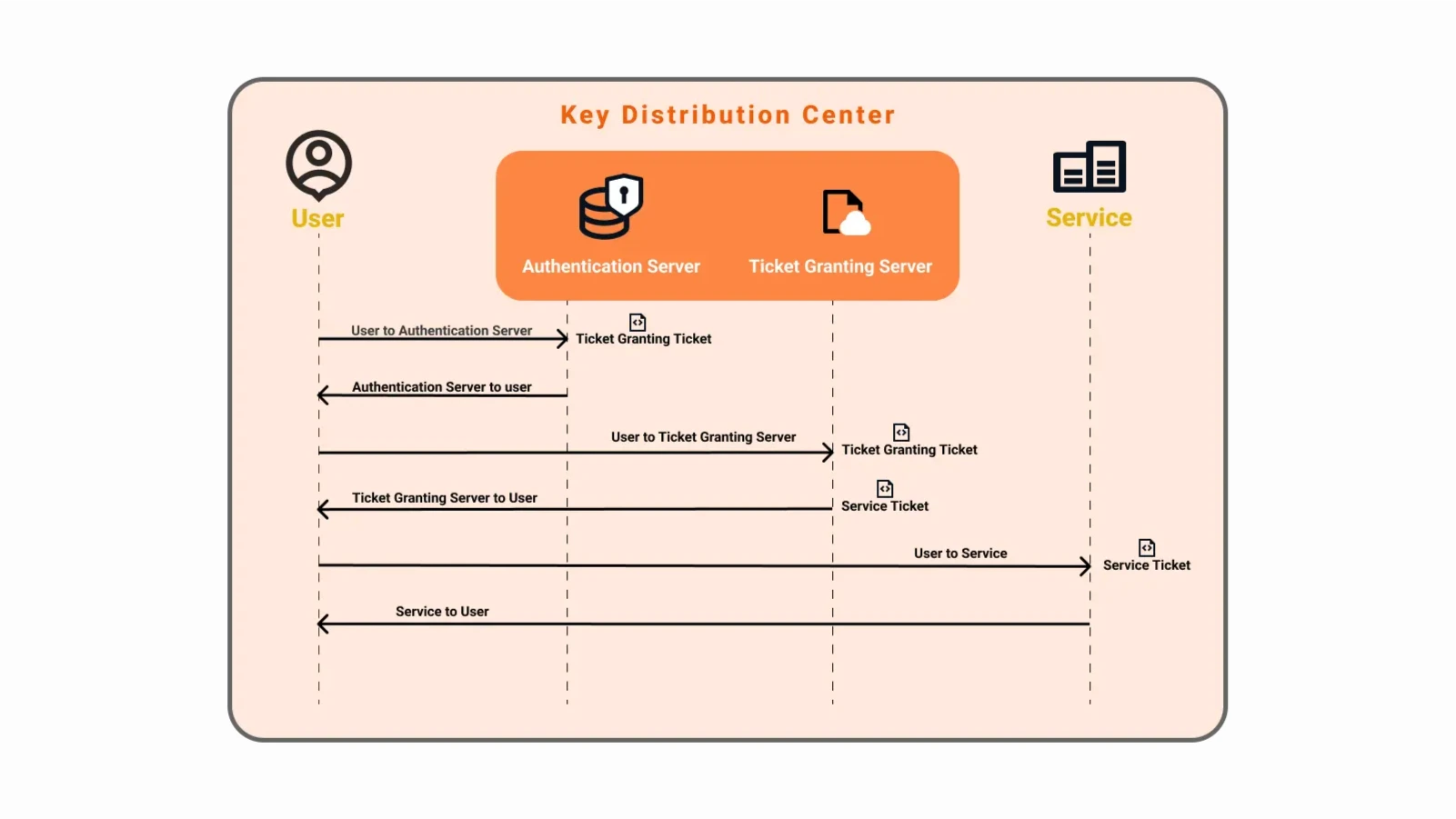
concepts
Kerberos NTLM Windows SSO
Thu May 12 2022
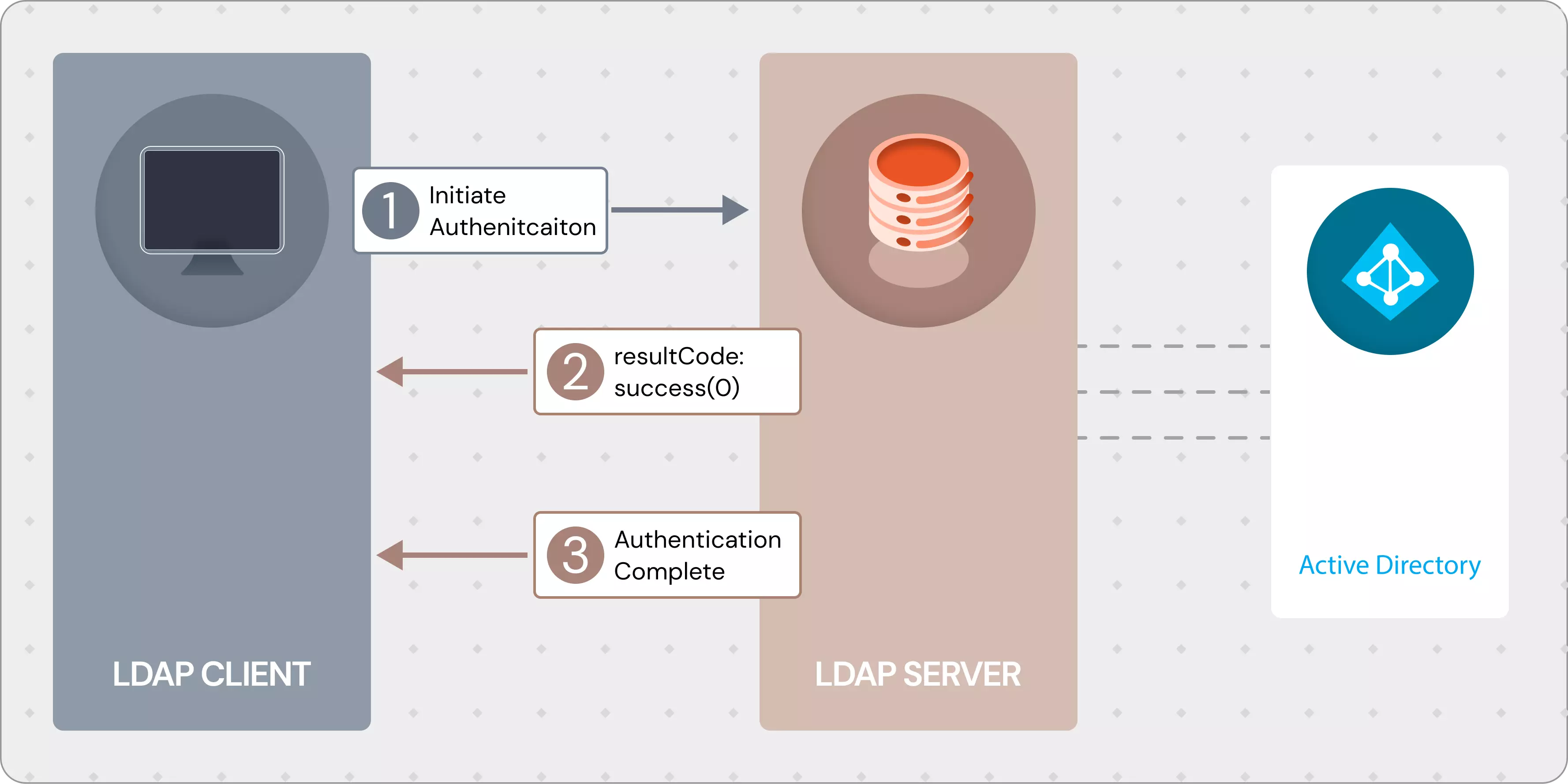
concepts
What is LDAP (Lightweight Directory Access Protocol)?
Sat Feb 19 2022
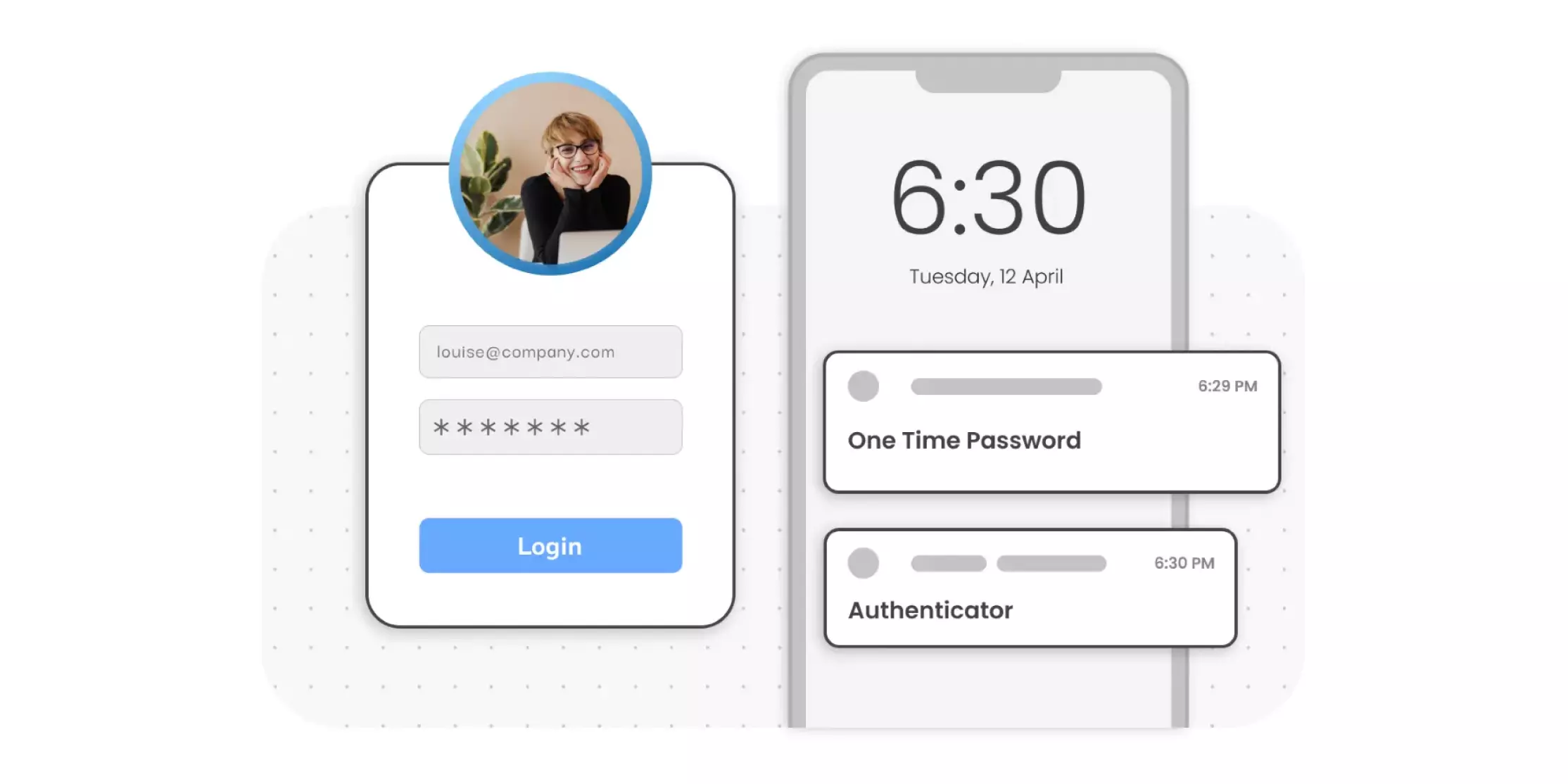
concepts
What is Multi-Factor Authentication (MFA) in Cybersecurity?
Sun Feb 26 2023

concepts
What is Single Sign-On (SSO) and How does SSO Work?
Sun Feb 26 2023
Concepts
What is the difference between SAML and OAuth?
Fri Apr 07 2023
iam
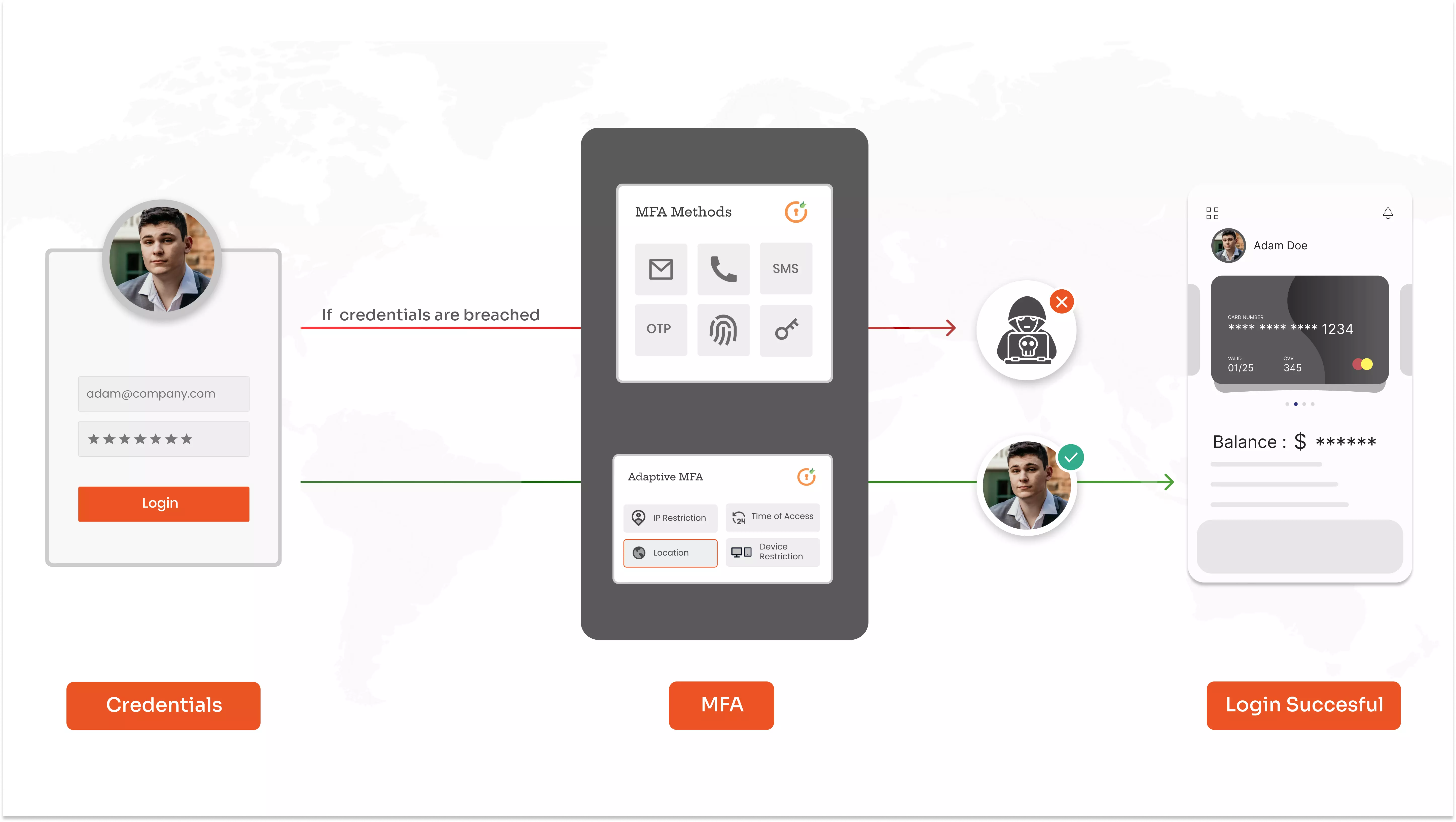
Why is Multi-factor Authentication (MFA) necessary for Banks and Financial Institutions?
Sat Jul 22 2023

iam
5 Reasons Why Your Business Needs Multifactor Authentication
Thu May 12 2022

concepts
What is Zero Trust Security & How does it work?
Thu May 12 2022

