In 2025, the US saw over 18.4 billion data records exposed, 2.28 billion of which were directly tied to password leaks. (Source: Demandsage) That’s not just a stat, it’s a reality check for every IT team managing identities and access across large user bases.
Most organizations already have a password policy in place. But here’s the thing: having a policy and enforcing it effectively are two very different challenges. Users reuse passwords. They forget them. They pick the easiest option just to get past the login screen. Meanwhile, IT teams spend hours resetting accounts, troubleshooting lockouts, and firefighting access issues that could’ve been prevented with better password governance.
In hybrid or remote work setups, the problem gets worse. Users expect quick fixes. Admins juggle password expiry, help desk overload, and compliance standards like NIST or GDPR. And when attackers know password hygiene is lax, it becomes their favorite entry point.
This blog breaks down the best practices for managing password policies in Active Directory, not just what to set, but how to actually enforce them without annoying users or piling more work on IT. We’ll also show you where self-service password reset (SSPR) tools come in, especially if you’re trying to reduce support tickets, stay compliant, and make password management user-friendly.
Why Password Policies Matter?
Passwords are still the first line of defense in most enterprise environments. Yet, they remain one of the weakest links in the security chain. Without strong password management practices, it’s only a matter of time before misused or stolen credentials lead to a breach.
In enterprise IT, password policy management isn’t just about setting rules. It’s about shaping behavior, how users create, use, and reset their passwords. A well-defined policy protects against brute-force attacks, prevents unauthorized access, and reduces the risk of insider threats. But for it to work, it has to be enforced consistently across departments, devices, and user roles.
Many organizations follow compliance standards like NIST SP 800-63B, GDPR, or ISO 27001, which now emphasize usability and automation over strict complexity alone. These frameworks push for password compliance requirements like:
- Minimum length of 8–12 characters
- Blocking commonly used or breached passwords
- Limiting password reuse
- Mandatory Password resets periodically
The goal is to reduce friction without compromising security. However, maintaining this balance is challenging if enforcement relies solely on manual processes, scripts, or native AD tools.
By aligning your policy with modern standards and automating its enforcement, you take a big step toward both compliance and operational efficiency.
Common Password Policy Challenges
On paper, password policies appear simple: enforce length, complexity, expiration, and perhaps add some reuse restrictions. But in practice, enforcing these rules, especially in Active Directory environments, comes with real challenges.
1. Users find workarounds
When password rules get too complex or disruptive, users start gaming the system. They add “123” or “!” to the same password they’ve used before. Some even write it down or save it in plaintext files. This completely defeats the point of strong password management practices.
2. Admins rely on inconsistent tools
If you're using Group Policy or PowerShell scripts to enforce password rules, you’ve probably hit limitations already. While native AD supports Fine-Grained Password Policies, managing them across groups is complex and lacks centralized visibility. Native tools also provide little reporting or alerting, making it hard to monitor compliance in real time.
3. Forgotten passwords overload helpdesks
Without self-service reset options, forgotten passwords or lockouts quickly escalate into support tickets. It slows down users and eats into IT’s time, something no team can afford when juggling compliance audits and real work.
4. Compliance isn’t enforced properly
You may have a password policy on paper, but how do you know it’s being followed? Most teams struggle to meet password compliance requirements across multiple user roles, departments, and locations. There’s no audit trail, no reports, and no easy way to prove compliance.
5. No way to prevent weak or breached passwords
One of the most overlooked issues is how to prevent weak passwords in Active Directory. Unless you actively block dictionary words, breached credentials, or common patterns, users can easily create passwords that look “valid” but are trivially guessable.
Best Practices for Managing Password Policies
There’s no universal password policy that fits every organization, but there are clear, research-backed practices that work across industries. These best practices help strike the right balance between security, compliance, and user experience.
1. Set clear rules for length and complexity
Start with a minimum of 12 characters. Include a mix of uppercase, lowercase, numbers, and symbols, but don’t force it blindly. Let users create passphrases if they prefer, as long as they meet entropy requirements. Short passwords, no matter how complex, aren’t enough today.
2. Follow NIST’s 2025 password policy guidelines
NIST recommends avoiding frequent forced resets and focusing on password strength and breach checks. Eliminate outdated practices like changing passwords every 30 days or banning reused characters; those just create frustration without improving security.
3. Block weak, breached, and common passwords
Use dynamic blocklists to stop users from choosing “Password@123” or anything in known breach databases. Tools like miniOrange's SSPR support integration with breached password APIs to enforce this automatically.
4. Limit password reuse and history
Users often rotate between the same 2–3 passwords. Enforce history policies that prevent reuse of at least the last 5–10 passwords, especially for privileged accounts.
5. Enable secure self-service password reset
Users forget passwords; it’s inevitable. A self-service password reset tool cuts downtime and reduces helpdesk load. Make sure the reset process includes identity verification steps like OTP, backup email, or MFA.
6. Apply group-based password policies
Different roles need different levels of security. Apply stricter rules for admins, finance, and HR teams. Use tools that allow group-based password policy enforcement, not just one blanket GPO for the whole domain.
7. Audit, report, and improve
Compliance isn’t a one-time task. Use tools that give you real-time reports on policy violations, password strength trends, and reset behavior. This helps you fine-tune policies and prove compliance during audits.
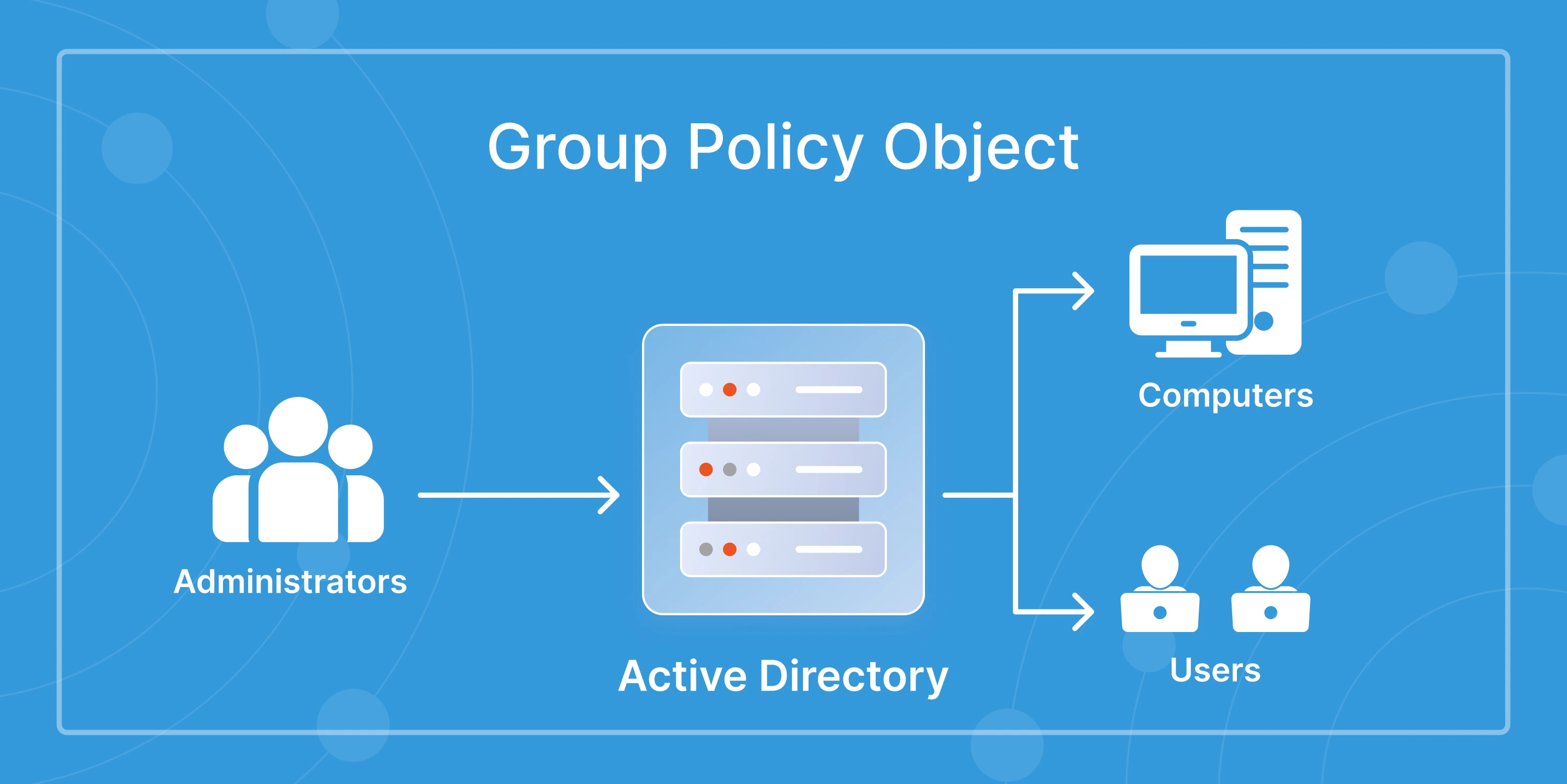
How Active Directory Handles Password Policies
Active Directory has built-in options to manage password policies, but they’re not always flexible enough for modern enterprise needs.
By default, AD lets you configure password settings like minimum length, complexity requirements, lockout thresholds, and expiry periods using Group Policy Objects (GPOs). These apply at the domain level and affect all users equally, unless you use Fine-Grained Password Policies (FGPP), a feature that lets you create different rules for different user groups.
Sounds good in theory, but here’s where it gets tricky.
- Most organizations struggle with how to enforce password policy in Active Directory effectively because:
- FGPP is hard to manage at scale. It requires careful use of Password Settings Objects (PSOs) and doesn’t integrate well with reporting or automation.
- There’s no built-in way to check password strength against breach databases.
- User experience is poor. When passwords expire or are rejected, users get generic error messages. That usually means a call to IT.
- Audit and compliance tracking is missing. You can’t easily generate reports on password quality, reset attempts, or policy violations.
So while AD supports basic enforcement, it falls short of meeting Active Directory password policy best practices for 2025, especially when it comes to automation, visibility, and user-centric controls.
This is where third-party tools like miniOrange's SSPR step in to bridge the gaps and give you more control over policy enforcement and user behavior.
Why You Need a Self-Service Password Reset Tool (SSPR)
Let’s face it, users forget passwords all the time. And when they do, they expect instant fixes. But in most AD environments, that means creating a helpdesk ticket, waiting for IT to respond, and dealing with productivity loss.
Multiply that by hundreds or thousands of users, and you’ve got a never-ending queue of password reset requests eating up your IT team’s time.
This is exactly why more IT admins are turning to an Active Directory self-service password reset tool.
An SSPR solution gives users the ability to reset their passwords or unlock their accounts without raising a support ticket. But more importantly, it does this in a secure, policy-compliant way.
Here’s what a good enterprise self-service password reset solution should do:
- Enforce password policies at the reset screen: Users can’t bypass complexity or reuse rules, even during reset.
- Verify user identity before resetting: OTP via email or phone, security questions, or MFA can be added for verification.
- Support AD-integrated password changes: Changes reflect instantly in Active Directory and follow domain rules.
- Log and audit all reset activity: Every action is tracked for compliance reporting.
- Reduce IT workload: Admins can focus on actual problems instead of unlocking accounts all day.
With a tool like miniOrange SSPR, users can reset their own passwords in Active Directory while still maintaining control, enforcing your password policy, and improving the overall user experience.
Benefits of miniOrange AD SSPR Tool
If you’re looking to enforce password policies without frustrating your users or overloading IT, the miniOrange SSPR tool for Active Directory gives you exactly that, and more.
It’s more than just a reset tool. It’s a complete AD password policy enforcement software that plugs into your existing environment and starts reducing password-related issues from day one.
Here’s how it helps:
- Enforces Password Policy at Reset: Users can’t bypass your password length, complexity, history, or breach check rules. Whatever policy you define in AD is fully enforced during self-service resets.
- Group-Based Policy Support: Apply different password reset rules and methods based on user groups or departments. Finance, HR, and Admins can have stricter reset flows.
- Multiple Verification Methods: Secure reset flows with OTP (email/SMS), push notifications, security questions, authenticator apps or even MFA. You control the authentication methods per group or policy.
- Instant AD Sync: Any password change or reset is immediately updated in Active Directory. No sync delays, no gaps.
- 24x7 Availability: Users can reset passwords or unlock accounts at any time, with no dependency on IT office hours.
- Full Audit Trail: Every reset and unlock is logged, so you’re covered for audits and security reviews. Easily export reports when needed.
- Reduced Helpdesk Volume: By automating resets, you cut down tickets and free up IT for high-priority tasks.
- Compliance-Friendly: Supports modern standards like NIST, ISO, and GDPR. Helps you maintain enterprise password management and compliance without manual enforcement.
Whether you’re a growing business or managing multiple domains, miniOrange helps you shift from firefighting to proactive password governance.
Conclusion
Managing password policies isn’t just a checkbox for compliance; it’s a real opportunity to cut security risks, reduce IT workload, and improve the user experience.
But policies alone don’t protect your environment. What matters is how consistently they’re enforced and how easy it is for users to follow them.
If your team still resets passwords manually, struggles with lockouts, or lacks visibility into policy violations, it’s time to move beyond native AD features and patchwork scripts.
The miniOrange AD Tools platform brings everything you need into one place: password policy enforcement, user self-service, account unlocks, audits, alerts, and more. With the miniOrange Self-Service Password Reset (SSPR) solution, you can empower users to reset their passwords securely, apply group-based rules, and enforce policies during every login and reset.
It’s purpose-built for Active Directory environments and designed for teams who want to do more than just “manage” passwords; they want to take control.
Ready to simplify password policy enforcement and reduce password-related tickets?
Explore the full suite of miniOrange AD Tools and see how SSPR fits into your IT strategy.
FAQs
What are the best practices for managing password policies?
Best practices include setting a minimum password length of 12 characters, using complexity rules, blocking reused and breached passwords, and enabling self-service resets. These help enforce strong password management practices across the organization.
How to enforce password policy in Active Directory?
You can enforce password policy in Active Directory using Group Policy Objects (GPOs) or Fine-Grained Password Policies (FGPP). For better control and reporting, use tools like miniOrange SSPR to automate resets and apply group-based rules.
What is the best self-service password reset tool for AD?
The best self-service password reset (SSPR) tool for Active Directory should include:
- Policy enforcement at reset
- Multi-factor verification (OTP, email, questions, etc.)
- Group-based access control
- Real-time sync with AD
- Audit logs and reporting for compliance
- 24/7 availability from any device or location The miniOrange Self-Service Password Reset tool checks all of these boxes. It’s built specifically for Active Directory environments and helps you reduce helpdesk tickets while staying compliant.
What are the NIST password policy guidelines 2025?
NIST 2025 guidelines recommend using long passwords or passphrases, avoiding periodic resets, blocking breached passwords, and simplifying user experience with secure self-service reset options and MFA.
How do enterprises manage password compliance?
Enterprises manage password compliance using a mix of policy enforcement, self-service tools, identity verification, and regular audits. Solutions like miniOrange AD Tools automate enforcement and simplify compliance reporting.


Leave a Comment