Managing user access, security settings, and system configurations across a network can quickly get out of hand, especially in growing organizations. That’s why most Windows-based environments rely on Group Policy in Active Directory to maintain consistency and control.
Group Policy enables IT administrators to define rules and settings that apply uniformly across users and devices — from password policies to desktop configurations — without requiring individual configuration of each machine. It’s not just about saving time; it’s about reducing mistakes and improving security.
In this blog, we’ll break down:
- What is Group Policy?
- Why it matters for security and management
- How to set up and manage policies in Active Directory
- Common use cases and challenges
Let’s get into how Active Directory GPOs work and why they’re still essential in 2025.
The Benefits of Group Policy in Active Directory
Group Policy is one of the core features that make Active Directory a powerful tool for enterprise IT management. It gives administrators a way to enforce rules, configure system behavior, and apply consistent settings across all users and computers within a domain, without having to touch each machine individually.
Here’s why Group Policy is beneficial for organizations of all sizes:
1. Centralized Control
With Group Policy, you can manage everything from desktop backgrounds to software installation policies from a single console. This centralized control reduces manual work and lowers the risk of configuration errors.
2. Security Enforcement
A 2024 ESG survey found that 80% of IT professionals consider misconfigurations the top security risk in AD, often stemming from outdated or unmanaged GPOs.
Policies like password complexity, user permissions, and account lockouts help reduce attack surfaces and enforce regulatory compliance.
3. Standardized Configuration
Group Policy ensures that all users and systems follow a consistent configuration, making it easier to onboard new employees, troubleshoot issues, and maintain IT standards across departments or locations.
4. Simplified Administration
Instead of configuring settings on each endpoint, IT admins can apply changes at the domain, site, or organizational unit (OU) level, and those changes take effect automatically across all affected systems.
5. Scalable for All Organizations
Whether it’s a 50-person team or a 5,000-user enterprise, Group Policy scales efficiently. Smaller businesses benefit from the time savings, while larger organizations gain more control and consistency.
What Is Group Policy in Active Directory?
Group Policy is a feature built into Microsoft Windows that allows administrators to define rules and settings for users and computers within an Active Directory (AD) environment. It helps standardize configurations, enforce security measures, and automate system management — all from a centralized location.
Core Functionalities of Group Policy
At its core, Group Policy enables:
- Control over user environment settings like desktop layout, Start menu options, and drive mappings
- Enforcement of security rules, such as account lockout thresholds or restricted software use
- Automation of tasks like software deployment and script execution during logon/logoff
How Group Policy Works with Active Directory
Group Policy is tightly integrated with Active Directory. When a user logs in or a computer starts up, the system checks Active Directory for applicable Group Policy Objects (GPOs) linked to that domain, site, or organizational unit (OU). These GPOs are then applied in a specific order to determine how the system behaves.
This connection between Group Policy and Active Directory ensures that rules are applied consistently across the organization, even when users switch devices or log in from different locations.
Key Components of Group Policy
- Group Policy Object (GPO): A container that holds policy settings. Each GPO can contain hundreds of individual rules for both users and computers.
- Policies: Settings defined within a GPO, such as password policies, desktop restrictions, or software rules.
- Scope of Management: GPOs can be linked to domains, OUs, or sites, determining which users or computers receive the policy.
- Group Policy Management Console (GPMC): A tool used to create, modify, and manage GPOs.
Together, these components allow IT teams to efficiently manage large networks while ensuring policy compliance and reducing manual errors.
Purpose and Uses of Group Policy
Group Policy isn’t just a convenience feature — it’s a foundational part of system management in Windows-based networks. It helps organizations enforce security, control user environments, manage software, and streamline administrative tasks.
Here are some of the key uses of Group Policy in Active Directory environments:
1. Security Enforcement
- Enforce password policies, such as minimum length, complexity, and expiration
- Set account lockout policies to prevent brute-force attacks
- Restrict user access to Control Panel, Task Manager, USB ports, etc.
2. User and Computer Configuration
- Control desktop backgrounds, Start menu layouts, and screen savers
- Define environment variables and power settings
- Hide or disable system drives for specific user groups
3. Software Deployment and Patch Management
- Deploy applications silently to user devices
- Roll out updates or patches without manual intervention
4. Drive Mapping and Printer Management
- Automatically map network drives and assign default printers based on user roles or departments
5. Folder Redirection
- Redirect folders like Documents or Desktop to a network location for easier backup and accessibility
6. Remote Desktop Services Configuration
- Manage RDS user settings, timeouts, session limits, and redirection policies
7. Auditing and Compliance
- Enable auditing for logon/logoff, file access, and administrative actions to support compliance with standards like HIPAA, GDPR, or SOX
8. Customization and Branding
- Customize the login screen, system messages, or desktop branding based on organizational identity
9. Power Management
- Apply energy-saving settings across the network to reduce electricity usage on idle machines
10. Security and WMI Filtering
- Apply policies only to specific users or systems using security groups
- Use WMI filters to target machines based on properties like OS version or hardware configuration
Types of Group Policy in Active Directory
Group Policy Objects (GPOs) in Active Directory can be categorized not just by their scope (domain, site, OU, etc.), but also by their origin and purpose. Microsoft officially classifies them into two key types: built-in GPOs (provided by the system) and custom GPOs (created by administrators).
Built-in GPOs (Microsoft-Provided)
In Microsoft Entra Domain Services (formerly Azure AD DS), two default GPOs are automatically created to provide baseline configurations for users and computers:
AADDC Users GPO
This GPO is pre-linked to the AADDC Users container and is intended for configuring user-related policies, such as login scripts, desktop settings, and user environment controls.
AADDC Computers GPO
This GPO is pre-linked to the AADDC Computers container and is used to configure policies for computers, including security settings, system behavior, and update preferences.
These built-in GPOs act as starting templates and can be customized to meet organizational needs. Only users who are part of the AAD DC Administrators group have the necessary privileges to manage these policies.
Custom GPOs (Administrator-Defined)
Custom GPOs are created manually by IT administrators to address specific operational or security requirements within the organization. Instead of relying solely on the default GPOs, custom policies enable granular control and better organization of settings.
Key characteristics:
- Created using the Group Policy Management Console (GPMC)
- Typically linked to custom Organizational Units (OUs) for targeted application
- Designed to group similar policy settings logically, reducing complexity and avoiding monolithic configurations
This modular approach helps administrators maintain a cleaner GPO structure, simplifies troubleshooting, and allows different departments or user groups to receive tailored policy sets based on their roles or responsibilities.
However, Group Policy in Active Directory isn’t one-size-fits-all. Depending on the structure and needs of your organization, various types of Group Policies can be applied at different levels, offering flexibility and control over how settings are distributed and enforced.
Below is a list of the types of Group Policy in Active Directory, along with what they are used for:
1. Local Group Policy
- Applies to a single computer (standalone or domain-joined)
- Managed directly on the machine using gpedit.msc
- Useful in small environments or for custom local rules
2. Site Group Policy
- Applied at the Active Directory site level
- Useful when managing configurations for physical locations (e.g., branch offices with separate subnets)
3. Domain Group Policy
- Managed centrally through the Group Policy Management Console (GPMC)
- Applies to all users and computers within the Active Directory domain
- Typically used for organization-wide security and configuration settings
4. Organizational Unit (OU) Group Policy
- Applied to specific OUs containing users or computers
- Ideal for assigning policies to departments, teams, or business units
Each type of Group Policy serves a unique purpose and can be layered strategically to enforce consistent behavior across your network, without overcomplicating management.
Understanding Group Policy Processing and Precedence
Effective Group Policy management hinges on a thorough understanding of how GPOs are processed and how conflicts between various policy settings are resolved.
The LSDOU Processing Order
Group Policy Objects are applied in a deterministic and hierarchical order known as LSDOU:
- Local: The Local GPO on the individual computer is processed first.3 This provides a baseline configuration for the machine.
- Site: GPOs linked to Active Directory Sites are applied next. These apply to all computers and users within that specific site.
- Domain: Following Site GPOs, policies linked to the Active Directory domain are processed.3 These apply to all objects across the entire domain.
- Organizational Unit (OU): Finally, GPOs linked to Organizational Units are applied. For nested OUs, GPOs linked to parent OUs are processed before those linked to child OUs.
This hierarchical order dictates that settings applied later in the sequence (e.g., OU policies) can override conflicting settings applied earlier (e.g., Local, Site, or Domain policies).4 It is important to note that cloud-based policy management tools like Microsoft Intune apply policies to users and groups without this hierarchical structure, which contrasts significantly with traditional on-premises Group Policy.
How to Create a Group Policy in Active Directory
Creating and configuring Group Policy in Active Directory is a core task for IT administrators. With the right structure, GPOs help enforce consistent rules while giving flexibility to adapt settings for different departments, sites, or roles.
Here's a step-by-step guide on creating and configuring Group Policy in Active Directory:
Step 1: Open the Group Policy Management Console (GPMC)
- On a domain controller or admin workstation, go to Start → Administrative Tools → Group Policy Management.
- Or run gpmc.msc from the Run dialog (WIN + R)
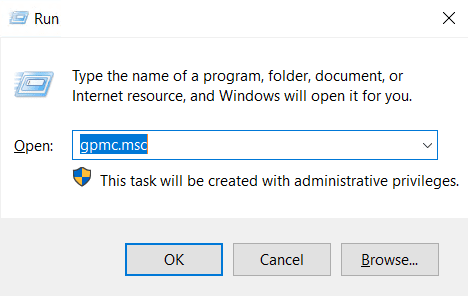
Step 2: Create a New Group Policy Object (GPO)
-
In the left panel, expand the domain node.
-
Right-click on the Group Policy Objects folder → click New.
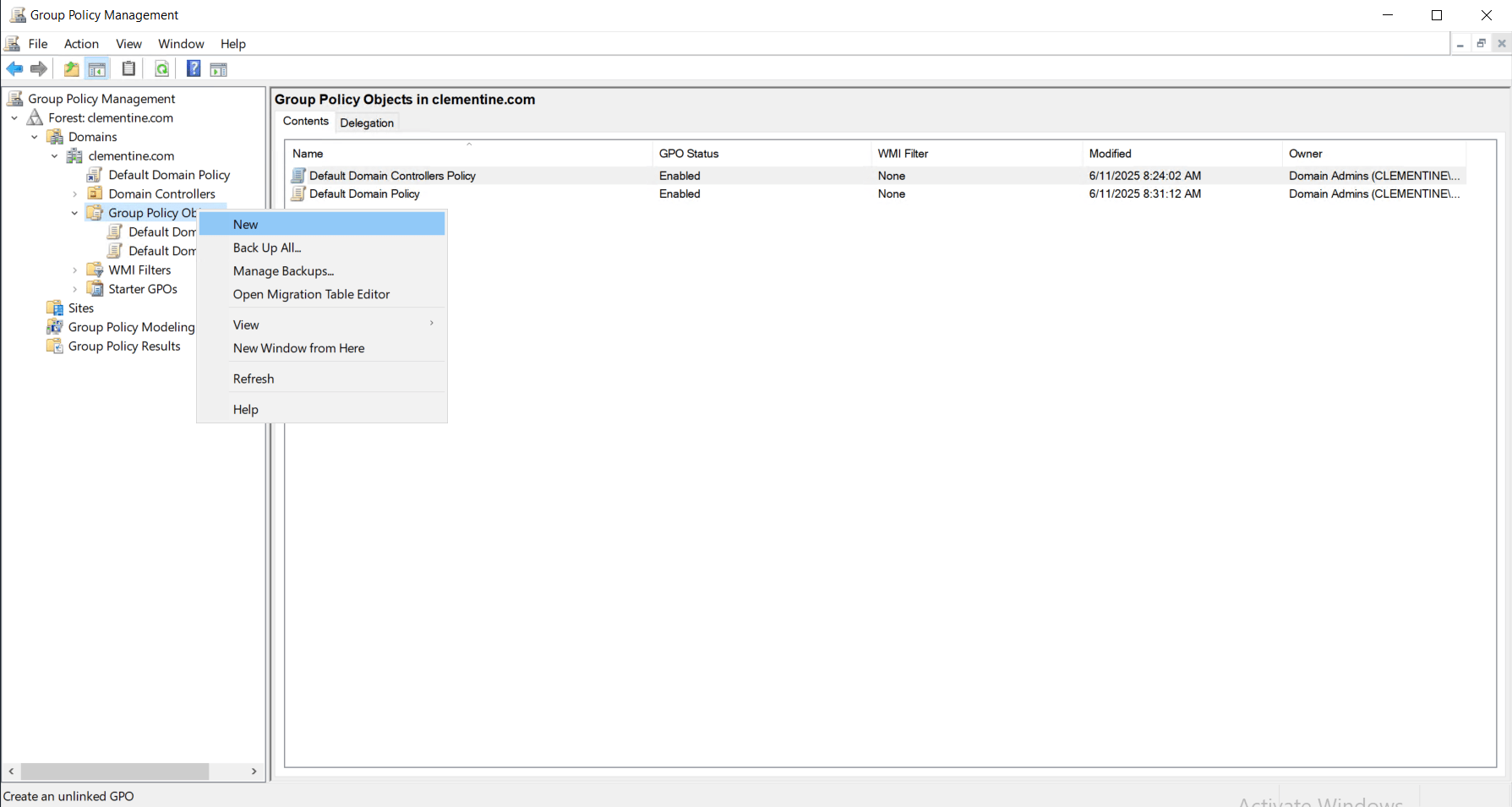
-
Name your GPO (e.g., “Password Policy - HR Dept”)
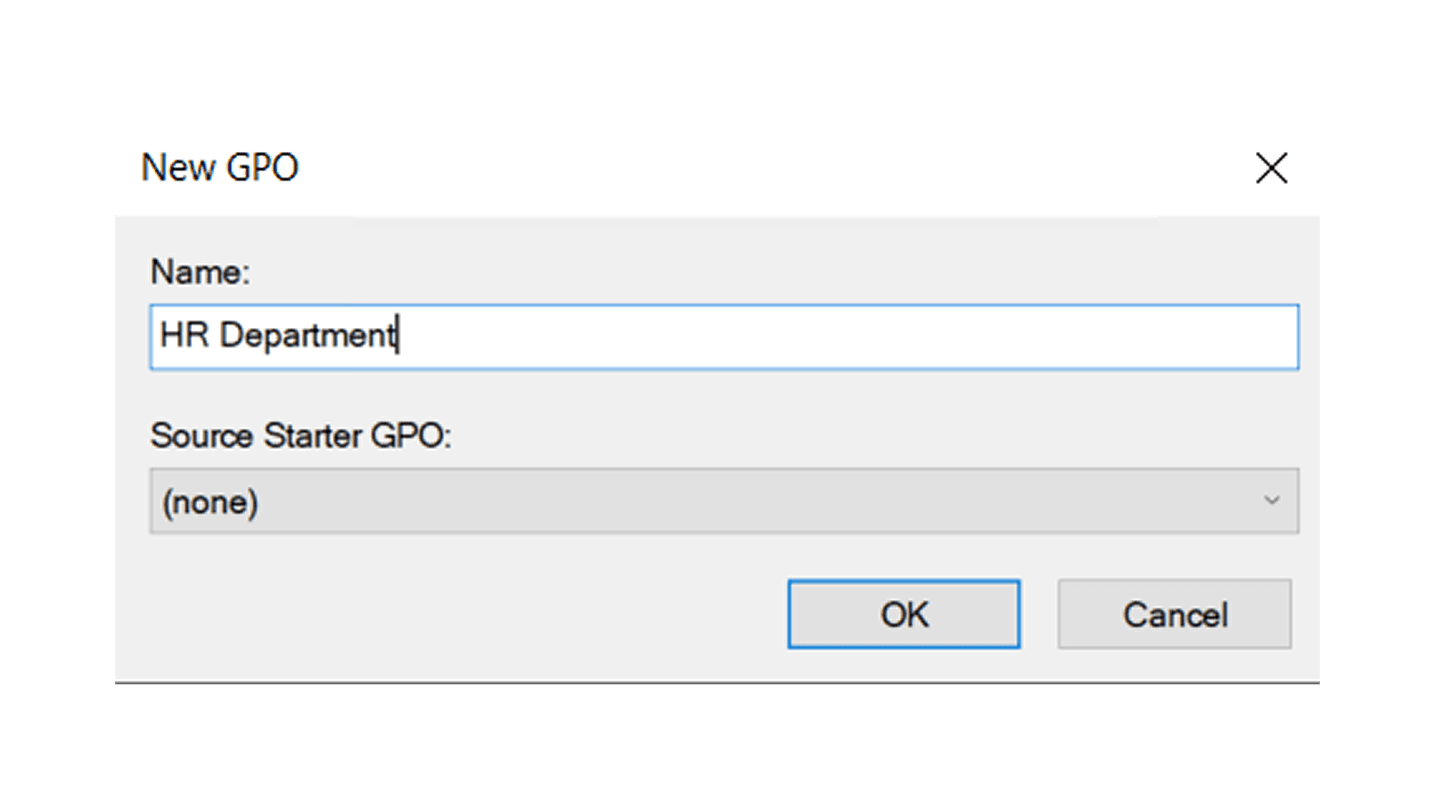
Step 3: Edit and Configure the GPO
- Right-click on your new GPO → click Edit
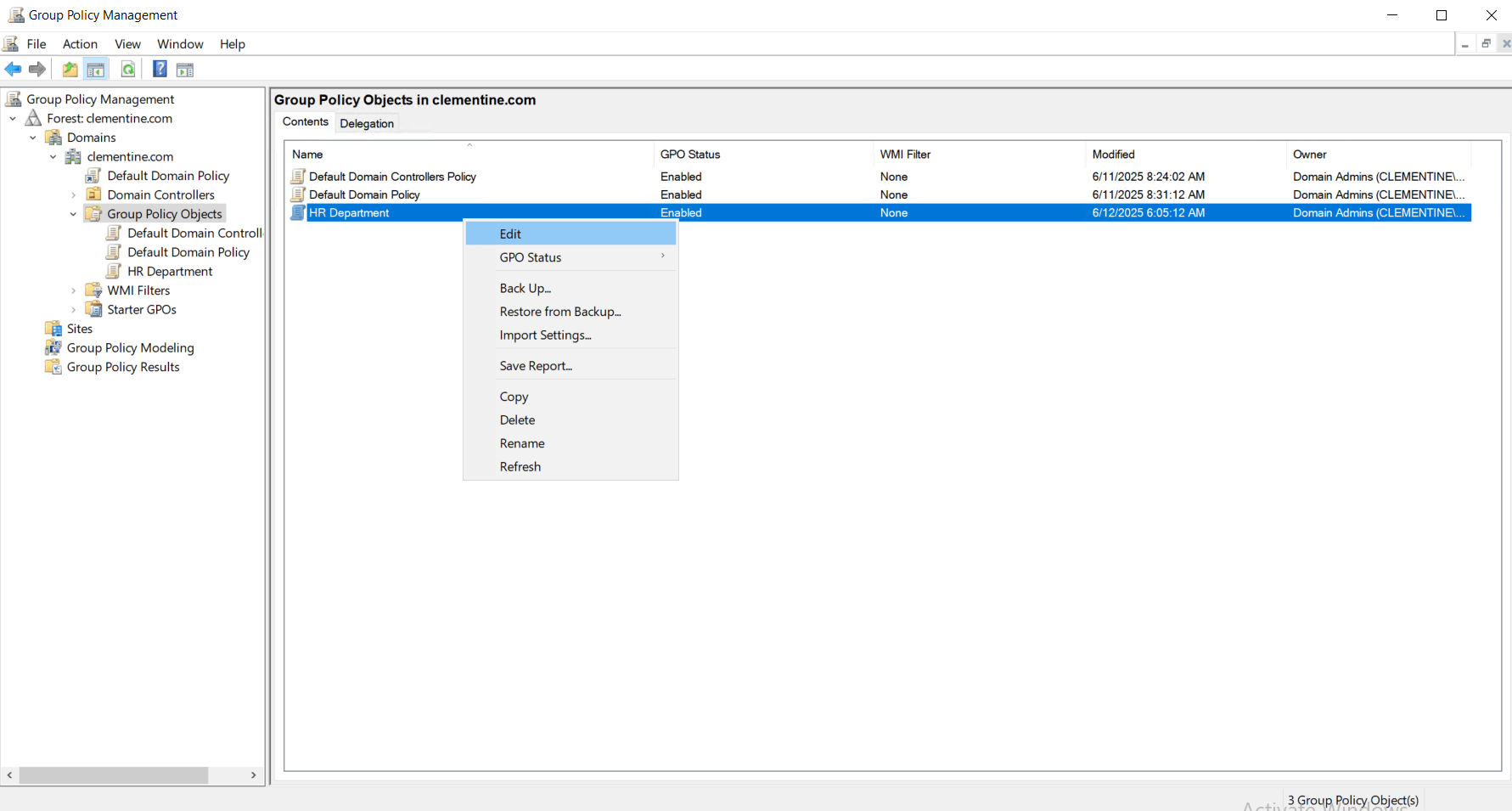
- The Group Policy Management Editor will open
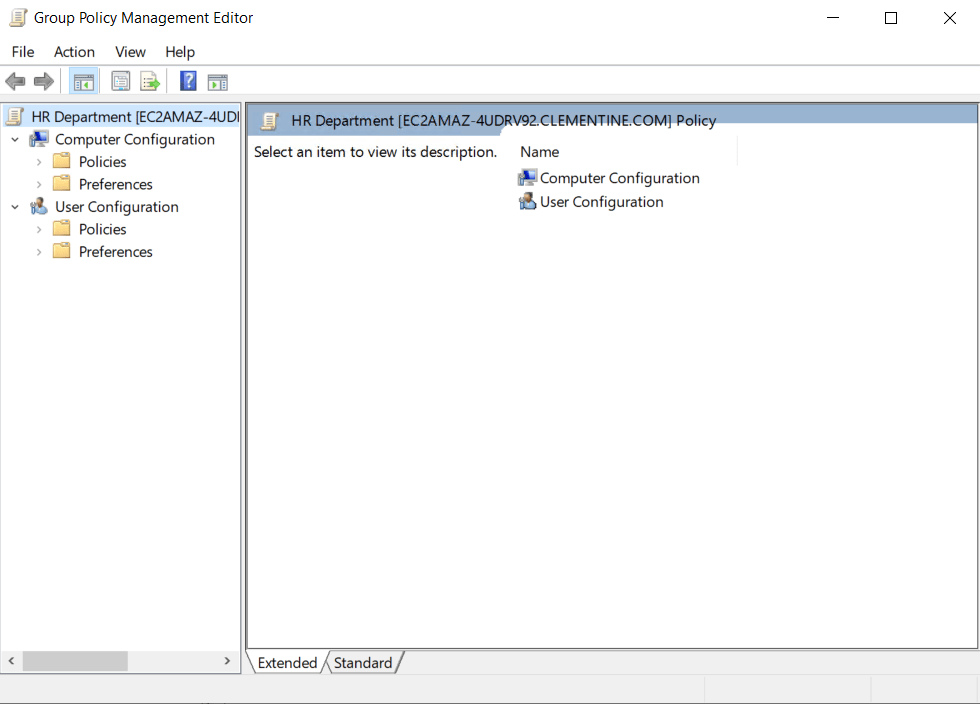
- Configure user or computer settings under:
- Computer Configuration → Policies
- User Configuration → Policies
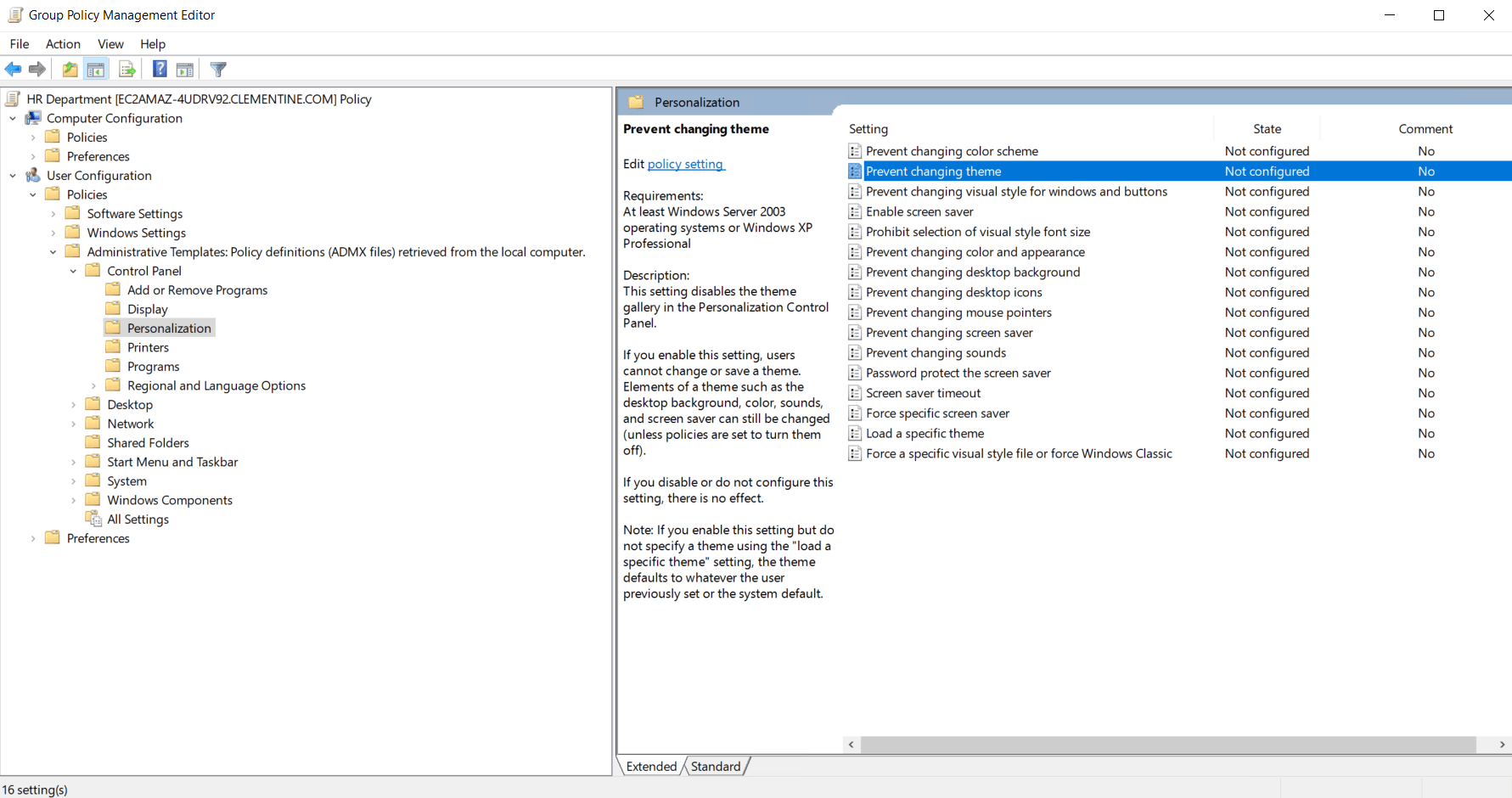
Step 4: Link the GPO to a Domain, Site, or OU
- In the GPMC, right-click the domain, site, or OU where you want the policy to apply.
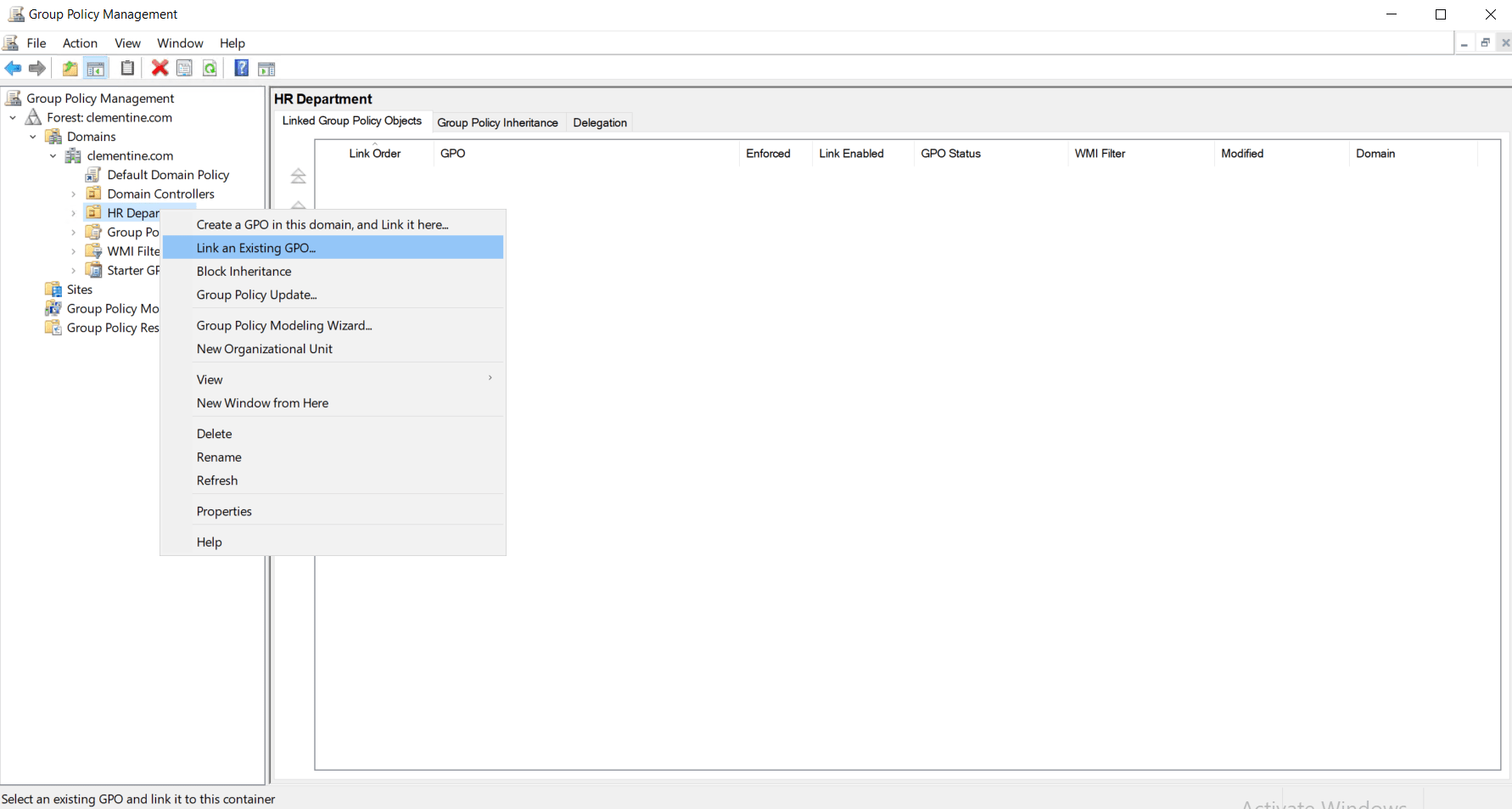
- Choose Link an Existing GPO, then select your newly created GPO
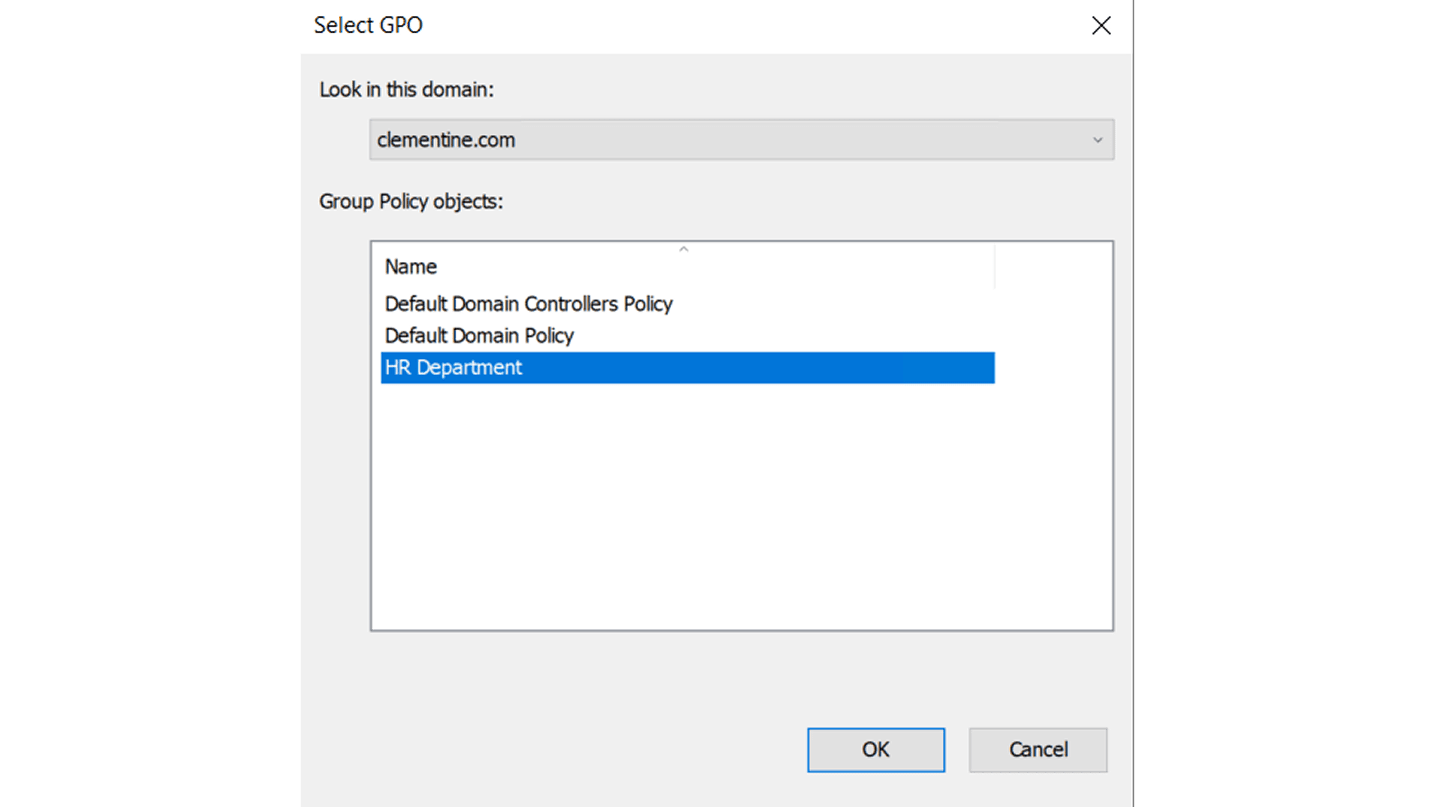
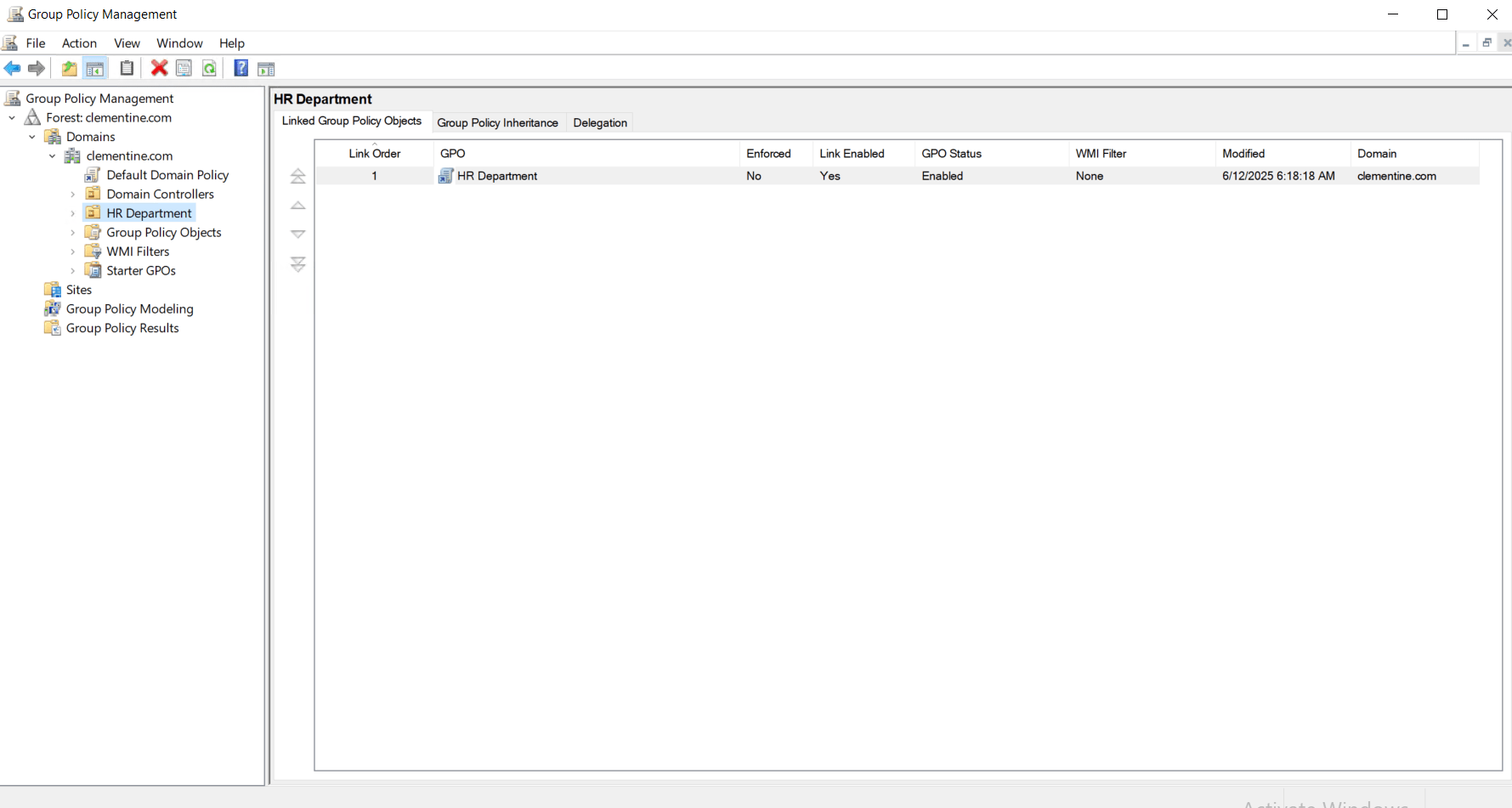
Step 5: Test and Validate the GPO
- Use tools like gpresult /r or rsop.msc to verify that the policy is applied correctly.
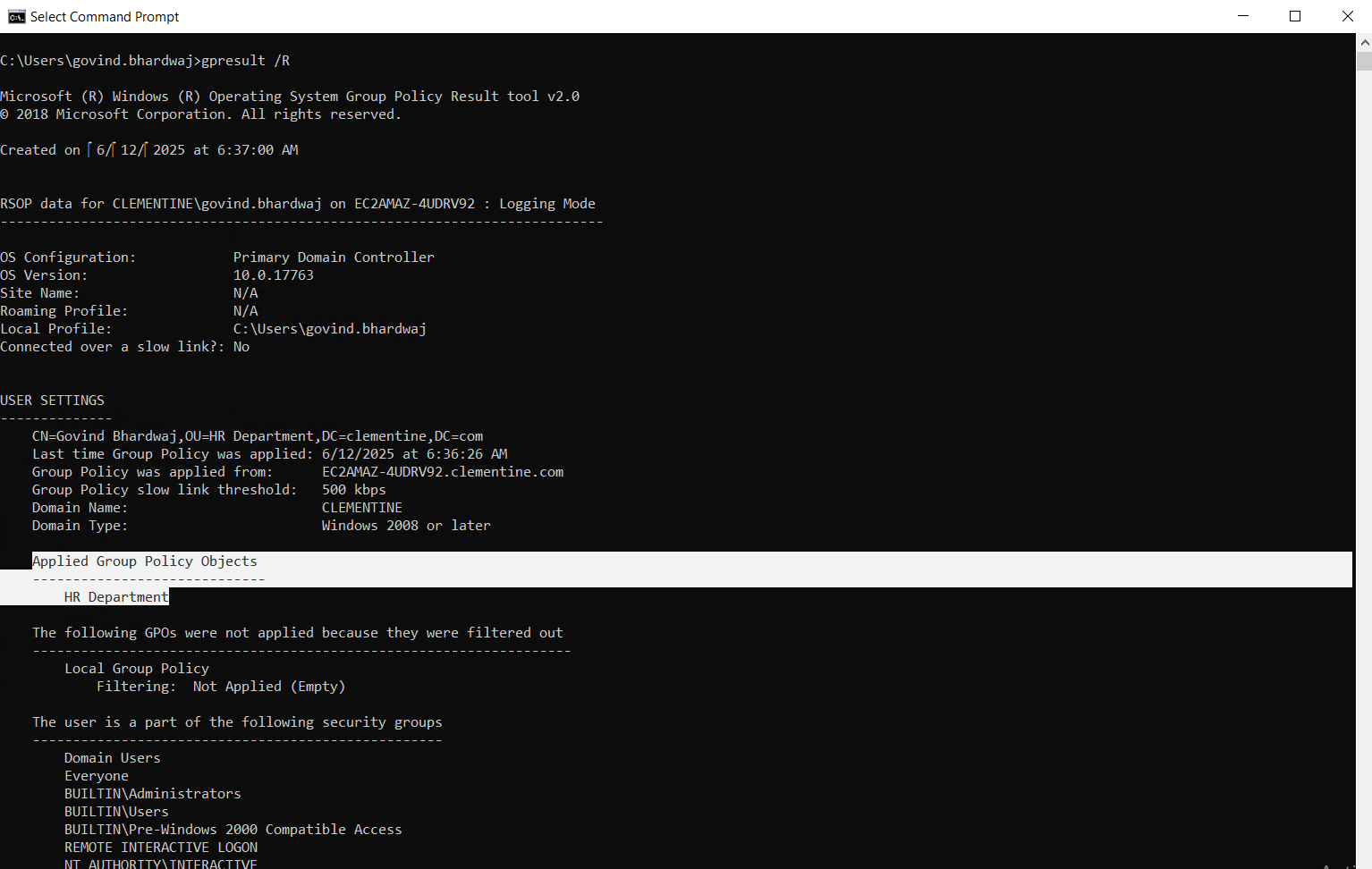
- Test on a non-production machine before deploying to wider groups.
Best Practices for Group Policy Deployment
- Use descriptive names for GPOs (e.g., “Screen Timeout – Finance Dept”)
- Avoid too many GPOs linked to the same OU to reduce complexity and delays
- Use security filtering or WMI filters for targeted applications
- Document GPO settings and changes for auditing and rollback purposes
By following these steps, you can ensure your Active Directory GPOs are deployed efficiently, with minimal disruption and clear control over what’s being enforced.
Common Challenges and Troubleshooting Tips
While Group Policy is a powerful tool, it’s not without its challenges. Misconfigurations, conflicts, or delays in policy application can impact system performance and user experience. Here are some of the most common issues and how to address them.
1. Policy Conflicts and Precedence Issues
Problem: Conflicting GPOs applied at different levels (e.g., domain vs OU) may lead to unexpected behavior. In fact, one of the reports found that over 50% of organizations don’t have clear visibility into Group Policy changes, leading to policy conflicts, misapplied settings, or undetected errors.
Solution: Understand the GPO processing order — Local → Site → Domain → OU. Policies applied later override earlier ones unless explicitly blocked. Use the Group Policy Modeling Wizard in GPMC to simulate results.
2. GPO Not Applying to Targeted Users or Computers
Problem: A GPO doesn’t seem to take effect for certain users or systems.
Solution: Check security filtering and WMI filters. Ensure the object has Read and Apply Group Policy permissions. Also, confirm the device is in the correct OU.
3. Delayed or Inconsistent Policy Updates
Problem: Changes in GPOs are not reflected immediately across endpoints.
Solution: Run gpupdate /force to manually refresh policies, or reboot the system. By default, policies refresh every 90 minutes (with a random offset).
4. Difficulty Diagnosing GPO Behavior
Problem: It’s unclear which GPO settings are being applied or blocked.
Solution: Use built-in tools like:
gpresult /h report.html: Generates a detailed HTML report
rsop.msc: Shows Resultant Set of Policy for the system/user
5. Unintended Side Effects After GPO Deployment
Problem: A new policy breaks a critical feature or application.
Solution: Test GPOs in a staging OU before rolling them out widely. Use version control if available through AGPM (Advanced Group Policy Management).
These troubleshooting practices can help you proactively resolve issues and ensure policies behave as expected across your Active Directory environment.
Conclusion
Group Policy is a fundamental part of managing any Windows-based network through Active Directory. Whether it’s enforcing security settings, streamlining user configurations, or automating software deployments, Active Directory Group Policies provide IT teams with the tools they need to maintain consistency, control, and compliance at scale.
When implemented correctly, GPOs reduce manual workload, prevent misconfigurations, and improve both user experience and system security. For any organization, small or large, mastering Group Policy means taking a proactive step toward better IT governance.
To make Group Policy even more effective, tools like miniOrange AD Tools can help administrators manage policies, monitor configurations, and automate user access with greater control and visibility. If you're looking to enhance your Active Directory environment, it's worth exploring solutions that extend beyond the default capabilities.
FAQs
1. What are Group Policy Objects (GPOs)?
Group Policy Objects (GPOs) are containers that hold configuration settings for both users and computers within an Active Directory environment. These settings control everything from password policies to desktop restrictions. When linked to domains, OUs, or sites, GPOs ensure consistent policy enforcement across targeted users and systems.
2. What is Active Directory Group Policy Management?
Group Policy Management in Active Directory involves creating, editing, linking, and managing GPOs across an AD domain. This is typically done through the Group Policy Management Console (GPMC), which provides a centralized interface for organizing and troubleshooting group policies at different levels — domain, site, and OU.
3. How are Active Directory and Group Policy related?
Group Policy is a core feature of Active Directory that enables centralized management of configurations across domain-joined machines. Active Directory provides the structure (domains, OUs, users), while Group Policy defines the rules applied to those structures. Together, they allow for scalable, consistent, and secure system administration.
4. What is Group Policy in Windows Server?
In Windows Server, Group Policy is a built-in administrative tool used to manage settings across multiple computers in a domain. From Windows Server 2008 onwards, Group Policy features are accessed via GPMC and can control everything from startup scripts to network security configurations. It's an essential part of Windows Server infrastructure for enterprise IT environments.



Leave a Comment