In early 2024, Ticketmaster confirmed that hackers had stolen data from over 560 million accounts - names, emails, and passwords were among the biggest targets.[1] Incidents like this remind us that a single weak password can open the door to massive data leaks and reputational damage.
Think about it, how many times have you reused the same password across work accounts, social media, and maybe even your banking app? It feels convenient at the moment, but it’s exactly what attackers count on. Once one system is breached, those credentials often get sold and tested across dozens of others.
This is why password security best practices are more than IT hygiene; they’re a frontline defense for both individuals and enterprises. From creating strong passwords to avoiding common mistakes, adopting MFA, and preparing for a passwordless future, here’s what you need to know and prepare for security.
Why Password Security Matters the Most Today?
Passwords are far from obsolete. Even with biometrics, MFA, and passkeys gaining ground, passwords remain the first line of defense for most accounts. Here’s why they still matter:
- Breaches are still password-driven
- The majority of breaches in 2024 can be linked back to stolen passwords and human error.[2]
- Attackers actively target passwords because they are often the easiest way into systems.
- Enterprises depend on them
- Businesses rely on passwords for access to cloud apps, collaboration tools, and financial systems.
- A weak password can enable account compromise long before other security layers (like MFA) stop the attack. Recently, a weak password allowed hackers to end a 158-year-old company.[3]
- Individuals are at risk, too
- A single leaked password from a shopping site can be reused to break into email, social media, or even banking apps.
- Password reuse multiplies the damage across multiple accounts.
Bottom line: Passwords may feel old-school, but in 2025, they remain one of the most targeted points of attack, and securing them is still essential.
How to Create Strong Passwords?
The foundation of password security is knowing how to create a strong one. Short, simple, or predictable passwords are easy for attackers to crack with brute force or credential stuffing. A strong password reduces that risk significantly.
- Focus on length over complexity
- Aim for at least 12–16 characters.
- Longer passwords are exponentially harder to crack.
- Use passphrases instead of single words
- Example: Coffee!Train!Window!Rain
- Easier to remember than P@55w0rD! but far more secure.
- Mix character types wisely
- Combine uppercase, lowercase, numbers, and special characters.
- Avoid predictable patterns like Password123!.
- Avoid personal details
- Do not use birthdays, names, pet names, or phone numbers.
- Attackers often mine this data from social media.
- Keep it unique per account
- Each account should have its own password.
- Reusing one password across multiple sites creates a domino effect if breached.
Pro Tip for IT Teams:
Creating strong passwords is just the first step. Enforcing them across your organization is where the real challenge lies. With miniOrange’s “Create and Manage Password Policies”, admins can:
- Define minimum length, complexity, and history rules.
- Enforce unique password standards across Active Directory users.
- Prevent common weak patterns and dictionary words.
- Automate compliance with HIPAA, PCI, and GDPR requirements. This ensures every user follows the same strong password rules — without leaving it up to guesswork.
Common Password Mistakes to Avoid
Even the best security policies can fail if users fall into bad password habits. Attackers often rely on these mistakes because they’re predictable and easy to exploit.
- Reusing passwords across accounts
- If one site is breached, attackers test the same password across banking, email, and work accounts.
- This is how a small leak can snowball into a major compromise.
- Choosing weak or common passwords
- Variations like Password123 or Qwerty! still rank among the most used globally.
- These can be cracked in seconds with automated tools.
- Storing passwords in unsafe places
- Writing them on sticky notes or saving them in browser autofill exposes them to anyone with local access.
- Malware and phishing kits are designed to grab these quickly.
- Skipping password updates after a breach
- If your credentials appear in a data leak and you keep using them, attackers will eventually get in.
Pro Tip for Admins:
Mistakes like these are often human, not intentional. With miniOrange’s Password Expiry Notification and Password Alert features, IT teams can:
- Remind users before passwords expire.
- Alert them if they are using weak or compromised credentials.
- Reduce the IT workload of constant password resets. By catching weak or reused passwords early, you lower the chance of a breach caused by simple mistakes.
Best Practices for Managing Passwords
Creating strong passwords is one thing. Managing them across dozens of accounts is another. Most breaches happen not because people don’t know the rules, but because managing multiple unique passwords becomes overwhelming.
- Use a secure password manager
- Password managers generate and store strong, unique passwords.
- This eliminates the need to memorize or write them down.
- Store credentials in an encrypted vault
- Unlike browser autofill, dedicated password vaults encrypt data and protect it with a master key.
- Avoid sharing credentials
- Never send passwords over email, chat, or shared documents.
- Shared accounts without accountability are a huge security blind spot.
- Rotate high-risk passwords when needed
- For privileged accounts or systems handling sensitive data, rotate passwords if a compromise is suspected.
Pro Tip for IT Teams:
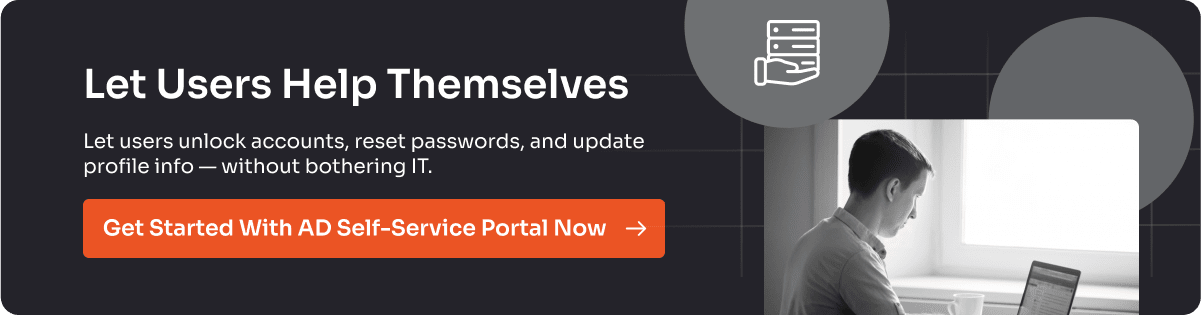
Managing password hygiene at scale is tough without automation. With the miniOrange AD Self-Service Portal, you can:
- Let users reset or update their passwords securely without IT help.
- Enforce strong password policies across all accounts.
- Keep credentials synced between Active Directory and connected applications. This gives users control over their credentials while reducing IT overhead — a win on both sides.
MFA and Password Security
Even the strongest password can be stolen through phishing, keyloggers, or database breaches. That’s why relying on passwords alone is risky. Multi-Factor Authentication (MFA) adds an extra step that makes it much harder for attackers to get in.
- Why MFA matters?
- If a password is compromised, MFA acts as a second lock on the door.
- Methods like OTPs, authenticator apps, push notifications, or biometrics stop attackers even if they know the password.
- Common MFA options
- SMS-based OTPs (better than nothing, but vulnerable to SIM swaps).
- Authenticator apps like Google Authenticator or Authy.
- Hardware keys (YubiKey, FIDO2 devices).
- Biometric verification, such as fingerprints or facial scans.
- Pairing MFA with strong passwords
- MFA doesn’t replace strong passwords - it complements them.
- Together, they reduce the risk of credential-based attacks like phishing or credential stuffing.
Conclusion
Passwords remain one of the most common entry points for attackers, but they don’t have to be your weakest link. Strong creation habits, better management, MFA, and modern practices like passkeys all help reduce the risks of stolen credentials. The real challenge is applying these best practices consistently across users and systems.
That’s where the right tools make the difference. With miniOrange AD Tools, you can:
- Create and enforce password policies across Active Directory.
- Remind users with Password Expiry Notifications and block weak or reused credentials.
- Enable Self-Service Password Resets to cut down on IT tickets.
- Add MFA or passwordless authentication to critical apps for an extra layer of security.
By combining smart user practices with automated enforcement, you close the gaps that attackers exploit while making logins smoother for employees. Passwords may evolve, but with the right approach, they can still be a secure and reliable part of your defense in 2025.
FAQs
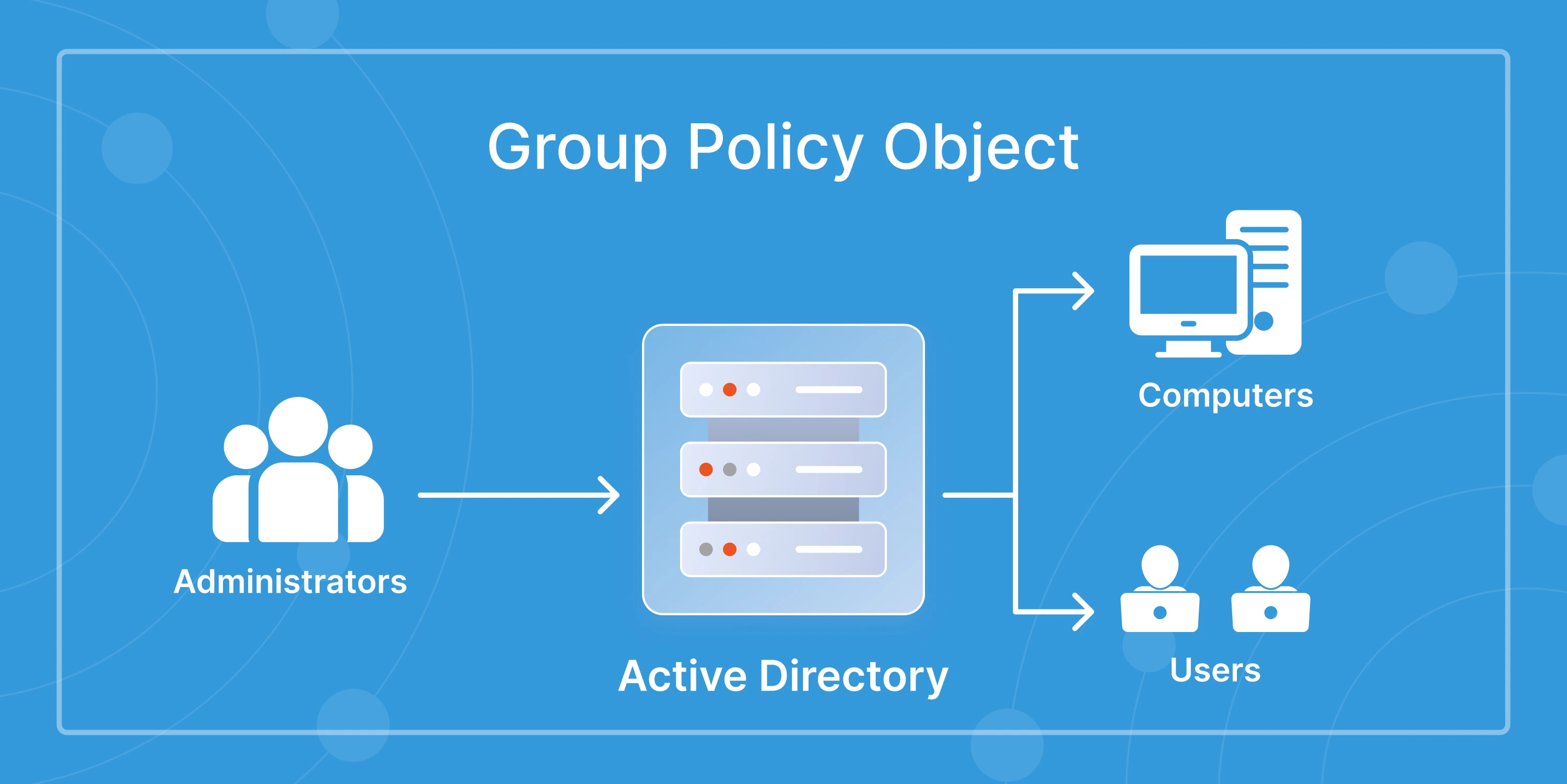
1. How do I enforce strong password policies across Active Directory?
You can configure Group Policy Objects (GPOs) in Active Directory to set minimum length, complexity, and history rules. For more granular control, tools like miniOrange Password Policy Enforcement allow you to block dictionary words, prevent password reuse, and align policies with compliance standards.
2. What are the compliance requirements for password security (HIPAA, PCI-DSS, GDPR)?
- HIPAA requires secure authentication mechanisms to protect ePHI, often involving strong passwords plus MFA.
- PCI-DSS mandates minimum password length, complexity, and periodic resets for accounts handling payment data.
- GDPR expects organizations to take “appropriate security measures,” which includes password protection aligned with industry best practices.
3. How can enterprises reduce password-related helpdesk tickets?
Most IT teams spend a large share of time on password resets and lockouts. Deploying a Self-Service Password Reset (SSPR) solution allows users to reset or unlock accounts securely, reducing IT workload and downtime.
4. Should enterprises still enforce password rotation policies?
Modern guidance (like NIST) suggests avoiding forced frequent changes unless there’s evidence of compromise. Instead, enterprises should combine strong password creation, breach monitoring, and MFA to secure accounts without frustrating users.

Leave a Comment