What is the CLOP Malware Attack?
CLOP Malware attack was recently launched against several companies stealing their data and blackmailing them for a ransom, or else the data will be leaked on the Dark Web. It was created by a group of Russian hackers It has managed to beat the top cybersecurity guidelines set by the institutions of IT Security. It can be shared through third-party applications which have been whitelisted by the SOC team for daily operations and then once in the “playing field”, they can disable all types of firewalls and security measures placed by the company’s IT security teams.
How does the CLOP Malware work?
- In 2023, hackers found a vulnerability in the popular file-sharing app called MOVEit, where employees stored their files and shared them across teams.
- A group of hackers found a vulnerability within MOVEit and managed to pass legitimate executable files over the MOVEit servers, spreading the CLOP malware across the users.
- With these CLOP malware files in place, they managed to remove all the essential security policies set by their SOC teams and stole all the company data.
- Now with this business-critical data, the hackers threatened the heads of enterprises of leaking all their data over the dark web and have started asking for ransom before the deadline.
The CLOP leaks malware attack has targeted the top industry-leading companies and stolen their data. The hackers have sent an open message to all to contact them via email and give a payout in exchange for deleting their data before its released to the public on the dark web.
How does CASB secure against CLOP Malware?
With the CASB solution, and its active threat detection rules it continuously monitors for malware attacks and potential attack surface areas in the infrastructure. It also monitors the actions of the users and third-party apps interacting with the business data and makes sure they stay in check with the security rules set by the SOC team.
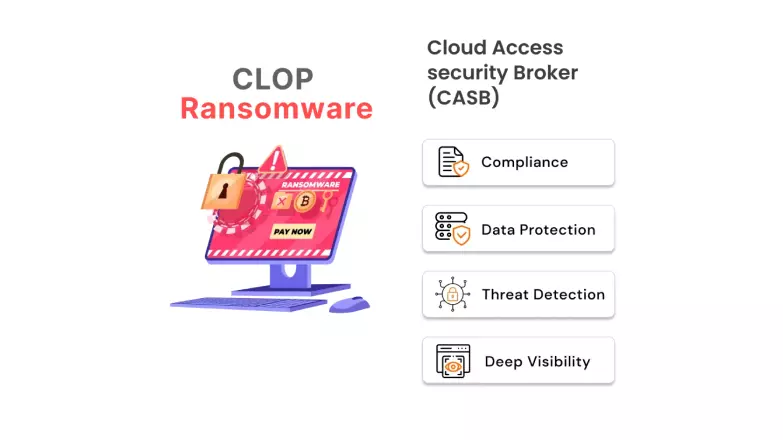
The major features of using CASB security solution include,
Compliance: Compliance ensures that the security standards are met for the relevant industry in which the organization operates to find sources of data breaches and mitigate all targeted threat vectors. This makes it a highly reliable and trustworthy CASB security feature.
Data Protection: Data Protection is a fundamental requirement for the rapidly pacing IT industry. The volume of data being generated and transferred is doubling every day. To secure these data items, your business needs a scalable solution that guarantees minimal downtimes, and most importantly, provides the best data protection solution to safeguard all your data.
Threat Detection: Threat Detection is a feature where once a threat is identified, it needs to be isolated and discreetly mitigated without disturbing the efficient working of other processes. CASB provides deep insights and sets risk scores for identifying such potential threats.
Deep Visibility: CASBs provide users with deep visibility to generate insights for threat reports and risk assessment to control an app’s access controls and monitor user working remotely and/or using BYOD (Bring Your Own Device) for accessing company documents.
What benefits of using CASB for Enterprise Security?
Malware Detection: CASBs actively search for malware and are updated with the latest malware policies. They are designed to provide complete malware mitigation procedures and isolate it in one place to prevent it from spreading further.
App Risk Score Assessment: CASBs actively monitor each application’s moves and what it interacts with. If an application is observed to repetitively access the company data, it gives it a risk score. Once this risk score crosses a threshold, this third-party application’s access permissions are revoked to prevent it from accessing any more company data.
Security Report Generation: CASBs also provide security reports and threat activities that it mitigated, so that the SOC team to gather deep insights and observe which section of their infrastructure is being targeted and then take measures to safeguard them better over time.
Role-Based Access Control: CASBs make sure that no user or third-party application interacts with a data item, out of their scope of access by using strict role-based access control policies to control access over data and prevent it from falling into the wrong hands.
In Summary
In this blog, we saw how CASB cloud security solution can secure your business from ransomware attacks such as Clop Malware. This ransomware managed to steal confidential data of government institutions and attacked universities stealing 45,000 student data which includes their social security numbers as well. The miniOrange CASB is the top solution to prevent again such attacks and will be the first line of defense against any threat that the ransomware attacks pose.
So if you are looking for a CASB solution for your business and team, miniOrange is the best solution on the market with a globally recognized support team and the most affordable pricing you’ll find anywhere else
So what are you waiting for? Shoot us a query at info@xecurify.com we will get right back to you and address all CASB security needs!
Additional Resources
Check out more CASB resources by miniOrange,





Leave a Comment