IT admins and security teams often find themselves stuck with repetitive, high-risk privileged tasks such as resetting passwords, provisioning accounts, and executing scripts, all of which demand elevated access. Manually handling these tasks not only consumes valuable time but also increases the chances of security lapses, human errors, and compliance violations.
This is where Privileged Task Automation aka PTA comes in. PTA streamlines and secures privileged operations by automating workflows. By reducing manual intervention, organizations can enhance operational efficiency while strengthening security.
As an integral part of Privileged Access Management (PAM), Privileged Task Automation ensures that privileged tasks are executed securely and consistently, minimizing the attack surface and mitigating insider threats.
This blog will explore how Privileged Access Management and Automation work together to safeguard critical IT operations, improve governance, and reduce administrative burdens.
What is Privileged Task Automation?
Privileged Task Automation (PTA) enhances cybersecurity by providing a sophisticated feature within Privileged Access Management (PAM) systems. PTA cleverly allows for the elevation of user privileges during task execution while keeping the actual privileged credentials concealed from the user. This capability empowers administrators to assign critical tasks to non-privileged users, enabling them to perform actions that typically require elevated access. This not only streamlines operations but also maintains strict security protocols by restricting direct access to sensitive credentials.
Unlike manual operations that are prone to errors and security risks, Privileged Task Automation Tools securely handles operations that involve elevated permissions. By doing so, it not only strengthens security but also enhances operational efficiency. Automation through PTA means that tasks that could take hours or even days are now completed in a fraction of the time, with significantly reduced chances of human error. This is particularly important in today’s digital landscape where data breaches and insider threats are major concerns.
Furthermore, PTA differs significantly from Robotic Process Automation (RPA). While both automate routine tasks, PTA is specifically designed for tasks that require elevated access and focuses on security and compliance aspects of these operations. RPA, on the other hand, automates general, repetitive tasks across various business functions without necessarily involving privileged access. Therefore, while RPA improves general business efficiency, PTA provides a secure framework for handling sensitive operations, thus protecting organizations from cyber threats and reducing operational costs associated with manual oversight and errors. Privileged Task Automation thus not only complements PAM by enhancing security protocols but also ensures that critical operations are executed without interruption, paving the way for a secure digital transformation in modern business models.
Why is Privileged Task Automation (PTA) Important?
Following are the benefits of Privileged Task Automation (PTA), let us take a look one by one.
Security: Reducing Human Intervention and Risk of Credential Misuse
Privileged Task Automation (PTA) boosts security by limiting direct user access to sensitive credentials, using predefined task sets with securely stored privileges and role-based access controls to mitigate credential misuse and enhance operational integrity.
Efficiency: Saving Time by Automating Repetitive Tasks
One of the key benefits of PTA is its ability to save time and increase productivity by automating repetitive and routine tasks. Advanced systems like Robotic Process Automation (RPA) take this further by automating tasks that are triggered frequently, using software 'robots' to perform activities faster and more accurately than human operators.
This not only speeds up operations but also frees up skilled employees to focus on more strategic tasks that add greater value to the organization. By automating these tasks, companies can operate more efficiently and respond more quickly to changing needs.
Compliance: Ensuring Audit Logs for All Privileged Activities
PTA also plays a crucial role in compliance by ensuring that all privileged activities are logged and auditable. This is vital for meeting regulatory requirements and for maintaining a transparent and traceable security environment. Automated systems provide comprehensive logs that track the use of each credential, differentiating legitimate from malicious use, and documenting every action taken under privileged access. This level of detail is essential for audits and for identifying potential security breaches, helping organizations maintain compliance with industry standards and regulations.
How Does Privileged Task Automation Work?
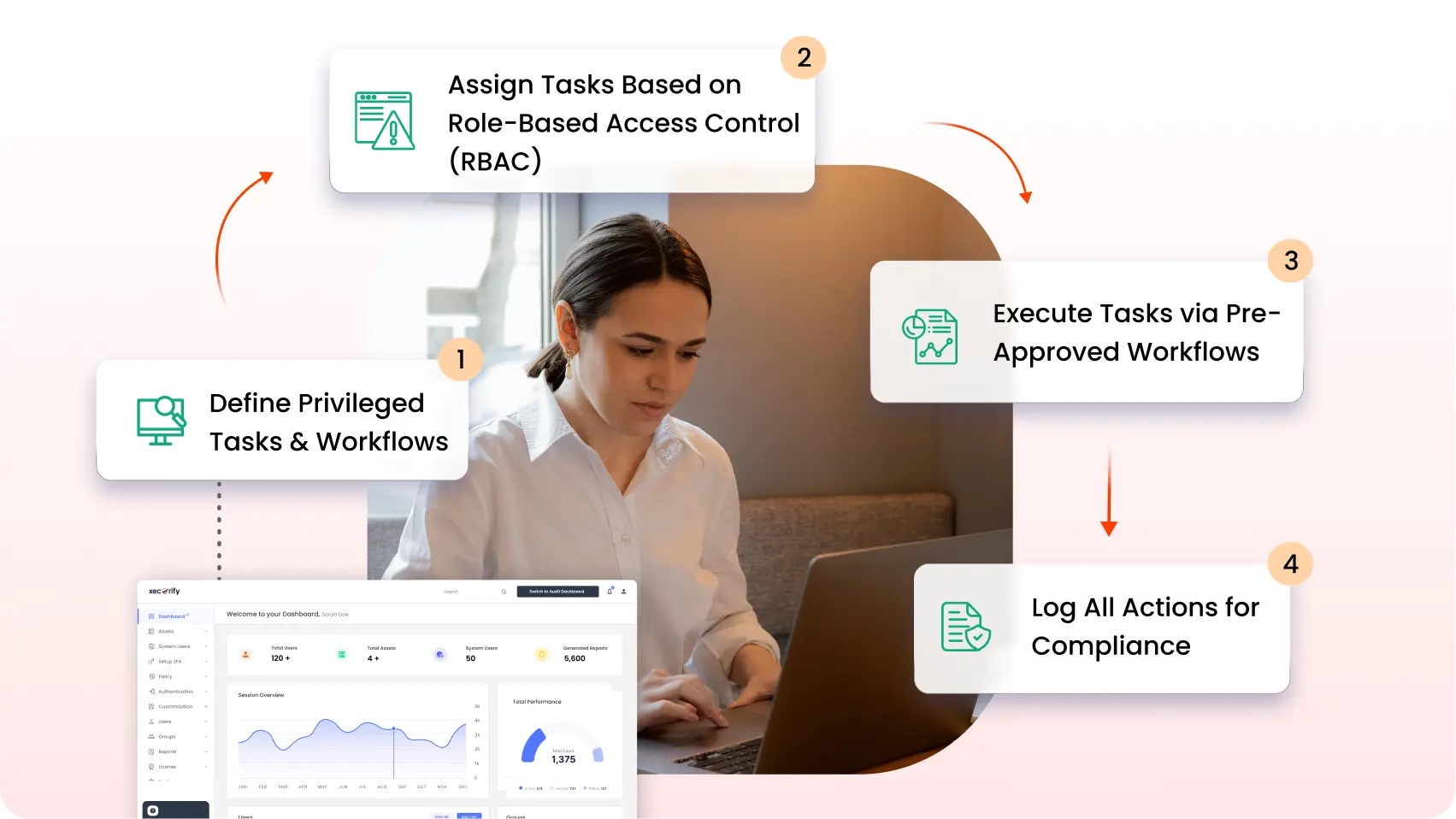
Its simplifies and secures the execution of critical tasks within an organization's IT infrastructure. Here's a step-by-step breakdown of how PTA operates:
Step 1: Define Privileged Tasks & Workflows
The process begins in the PTA system where privileged tasks are clearly defined using the Designer and Player modules. An authorized user creates workflows in the visual design tab of the PTA module, outlining the sequence of tasks. This setup includes crucial components such as pre-checks to verify conditions before execution, execution of the task itself, post-checks to ensure the task was completed successfully, and rollback mechanisms to revert changes if necessary. These workflows are designed to be dynamic and extensible, allowing for modifications as required by the organization's needs.
Step 2: Assign Tasks Based on Role-Based Access Control (RBAC)
Once the workflows are defined, tasks are assigned to users based on their roles within the organization. This is managed through RBAC, ensuring that users can only access tasks that are pertinent to their specific responsibilities. This not only enhances security by restricting access to sensitive functions but also helps in maintaining operational integrity by assigning tasks to the most appropriate personnel.
Step 3: Execute Tasks via Pre-Approved Workflows
With roles and workflows established, tasks are executed according to the pre-approved processes. Users interact with the system through a single interface that supports dynamic instruction sets, making the execution process efficient and effective. The system's design ensures that all tasks are carried out in the correct sequence and that all necessary checks are performed before, during, and after task execution.
Step 4: Log All Actions for Compliance
Every action taken within the PTA system is logged for compliance purposes. This comprehensive logging covers everything from initial task definition to final execution and post-execution analysis. These logs are vital for audits and reviews, providing a clear and accountable record of all privileged activities. This step is crucial for organizations needing to adhere to various regulatory standards and to ensure transparency and accountability within their IT environments.
Key Use Cases of Privileged Task Automation (PTA)
1. Privileged Task Delegation
PTA allows IT teams to perform sensitive tasks without direct access to critical credentials. By automating the delegation process, PTA ensures that general IT staff can execute necessary operations—such as managing user accounts or updating configurations—without ever seeing or handling the actual privileged passwords or keys. This reduces the risk of accidental exposure or malicious misuse of credentials, enhancing overall security.
2. Automated Patch Management
One of the routine yet critical IT tasks is keeping software and systems up to date with the latest patches. PTA automates this process by scheduling and applying updates across servers and databases. This not only maintains security by addressing vulnerabilities quickly but also ensures that patches are applied consistently and without human error, leading to better system stability and reduced downtime.
3. Password Rotation & Expiry
Secure management of privileged passwords is a cornerstone of IT security. PTA automates the process of changing these passwords regularly and ensuring they expire at predefined intervals. This automation helps comply with security policies that require frequent updates to passwords, reducing the window of opportunity for attackers to exploit older credentials and thereby enhancing the security posture.
4. Server Reboots & Configuration Changes
Regular maintenance tasks like server reboots and configuration adjustments are crucial for the smooth operation of IT systems. Automating these tasks through PTA helps maintain them without manual intervention, ensuring they are executed accurately and timely. This not only minimizes the risk of human error but also allows IT personnel to focus on more strategic activities rather than routine maintenance.
Benefits of Using Privileged Task Automation in a Modern PAM Strategy
Till now we know what pta is, how its work, importance and everything about it now lets look at how its going to benefit your pam strategy, lets have a quick look:
1. Eliminates Manual Execution Risks
Privileged Task Automation (PTA) significantly reduces the risks associated with manual execution of sensitive tasks. By automating the execution of privileged tasks, PTA minimizes human errors and potential security breaches that can occur when tasks are performed manually. This automation ensures that each task is executed consistently and securely, adhering to predefined protocols and reducing the likelihood of accidental misconfigurations or unauthorized access.
2. Enforces Least Privilege & Just-In-Time (JIT) Access
PTA is a crucial component in enforcing the principle of least privilege and Just-In-Time (JIT) Access with in a PAM strategy. By automating task execution and access control, PTA ensures that users are granted only the necessary privileges for the shortest duration required to complete a task. This minimizes the exposure of sensitive credentials and reduces the attack surface, thereby enhancing the overall security posture of the organization.
3. Reduces Downtime and Operational Costs
Automating privileged tasks through PTA not only speeds up operations but also significantly reduces downtime associated with manual interventions and errors. This increased efficiency translates into lower operational costs as tasks are completed faster and with fewer resources. Additionally, by minimizing downtime, PTA helps maintain business continuity and enhances productivity, providing a direct economic benefit to the organization.
4. Enhances Visibility and Compliance Tracking
PTA improves visibility into the execution of privileged tasks by logging all actions and changes made during task execution. This comprehensive tracking is invaluable for compliance and audit purposes, ensuring that all privileged activities are documented and traceable. By providing detailed logs and reports, PTA enables organizations to demonstrate compliance with regulatory requirements and to quickly address any potential issues or anomalies that are detected.
Conclusion
In today’s rapidly evolving cybersecurity landscape, Privileged Task Automation (PTA) is no longer a luxury, it’s a necessity. By automating high-risk privileged operations, PTA enhances security, minimizes human errors, and ensures compliance with industry regulations. It streamlines workflows, enforces least privilege principles, and eliminates manual execution risks, making IT operations more efficient and secure. For organizations looking to reduce security vulnerabilities, optimize IT efficiency, and strengthen governance, implementing Privileged Task Automation within a Privileged Access Management (PAM) strategy is a game-changer. Interested in enhancing your IT security with miniOrange PAM through Privileged Task Automation?






Leave a Comment