Make User Management in Crowd Less Manual, More Manageable
As your teams scale and more user directories get added, these tasks don’t just grow, they compound. A few missed deactivations can lead to serious compliance issues. Inactive accounts may continue consuming costly licenses. During audit season, you might spend days piecing together fragmented logs to prove access controls are in place.
In this article, we will explore five most common, everyday user management challenges admins face in Atlassian Crowd. We will also explore how automation can solve each challenge in a scalable manner.
Challenge 1: Inactive Users Occupy Licenses and Create Risk
The problem
Every admin has seen this situation: users haven’t logged into Crowd for months, yet their accounts remain active and licensed. These dormant users quietly inflate your Atlassian bill and create a real security risk.
How dormant accounts create risk
Consider this, a mid-size software company discovered over 120 dormant users across three departments. These users hadn’t logged in for 90+ days but still had access to internal project spaces and received email notifications. Many of them had already left the company but hadn’t been fully offboarded from Crowd.
Why these risks happen
Teams often prioritize onboarding and provisioning but overlook the cleanup. Most deactivation processes rely on manual audits, emails from HR, or support tickets. And when nobody owns the cleanup process, these accounts slip through the cracks.
How to address these risks with automation
You can mitigate these risks by:
- Setting an inactivity threshold, such as 60 or 90 days.
- Create a rule against this threshold to automatically deactivate users who haven’t logged in within that window.
- Add conditions to exclude service accounts or long-term absentees.
This ensures licenses are recycled and reduces exposure from idle accounts.
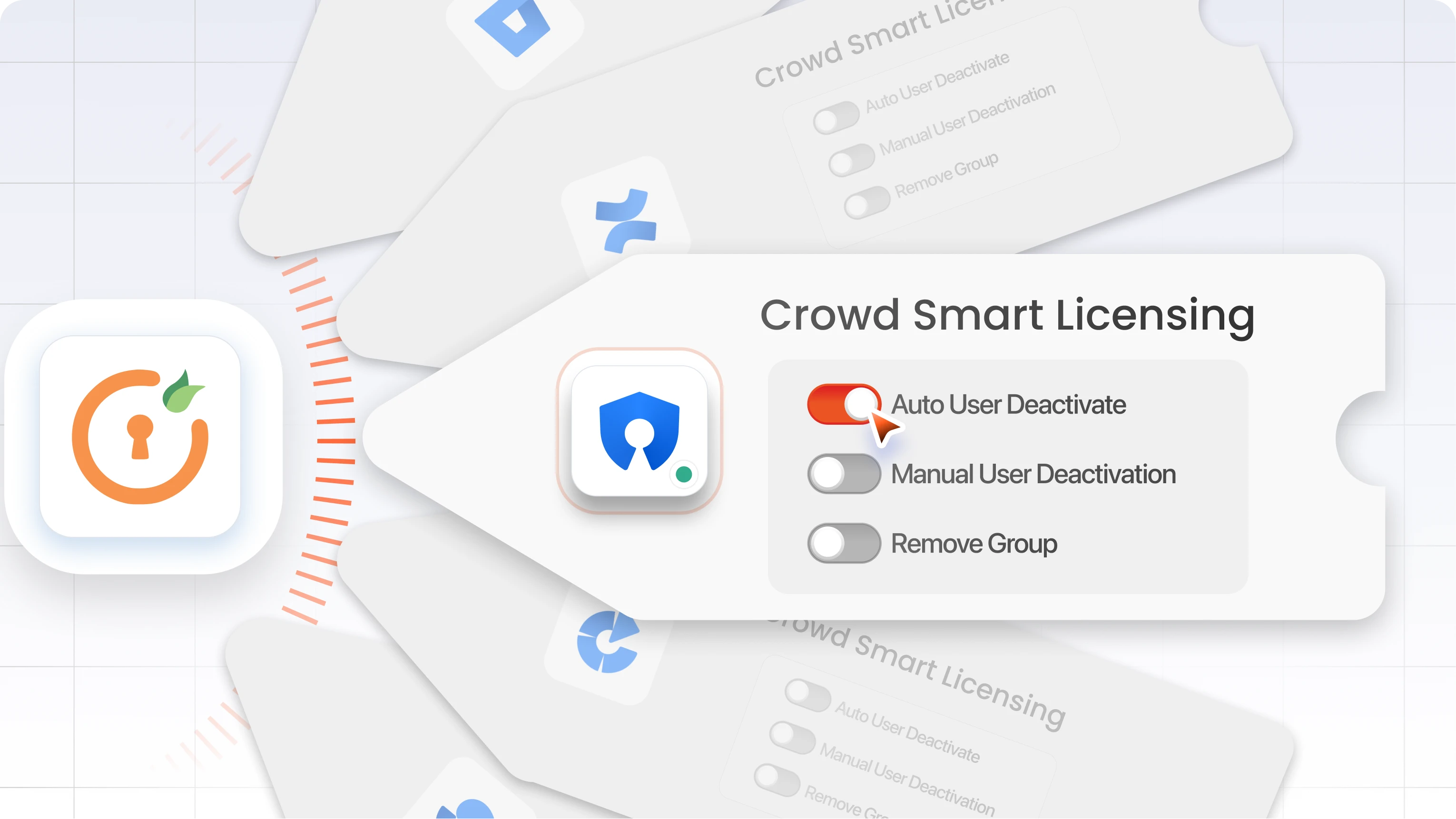
Where can you get this automation
The miniOrange Automated User Management app for Crowd includes an auto-deactivate feature that helps streamline user cleanup on a recurring schedule. You can also trigger it manually with a single click. Inactive users are flagged and removed from Crowd, with optional notifications sent to designated team/account owners.
Challenge 2: Returning Users Still Need Manual Reactivation
The problem
Contractors, interns, seasonal employees, and even full-timers on sabbatical all have one thing in common: they leave temporarily only to return after some time. But when they do, they often find their accounts deactivated. Reactivating these users is usually a manual process that involves Jira tickets, admin intervention, and delays, not ideal when users need access urgently.
Why it becomes a bottleneck
For many Crowd environments, user status is binary: either active or inactive. Once a user is deactivated, either due to inactivity or an intentional offboarding, they’re essentially locked out. The only way back in is through an admin.
This means someone from HR or the returning user themselves
- must raise a request
- Wait for it to be assigned
- Then wait on IT to restore access.
That adds unnecessary turnaround time and pulls admins away from more strategic work.
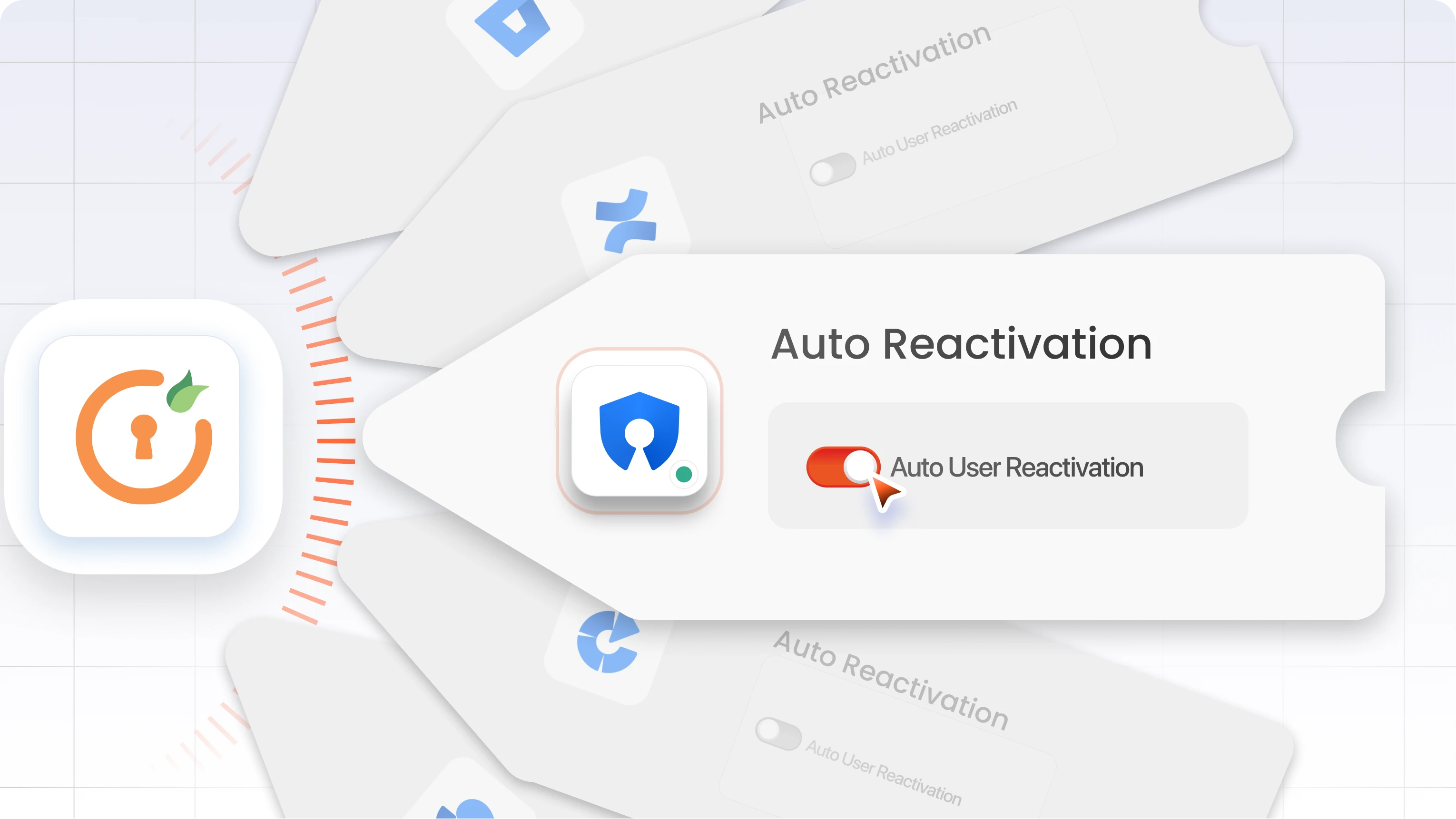
How to fix this bottleneck with automation
You can configure automatic reactivation for previously deactivated users. With miniOrange, the system monitors login attempts from deactivated accounts. If the user passes identity verification and matches existing directory records, the account is reactivated instantly, without admin involvement.
This works especially well when paired with inactivity-based deactivation. Users who were removed due to dormancy can log back in and regain access, without compromising security.
Where the automatic reactivation feature has the most impact
Organizations with flexible workforces, such as consulting firms, universities, or companies that operate seasonal shifts, benefit most.
For example:
- A returning adjunct professor logs into Crowd and is reactivated on the spot.
- A freelance developer picks up a second engagement and doesn’t need to raise an access request.
- An employee on sabbatical returns without needing HR to coordinate with IT.
Safeguards to keep in mind
Reactivation doesn’t mean free-for-all access. You can pair this with conditional rules: only users from certain domains, roles, or directories may be auto-reactivated. You can also exclude high-privilege accounts to ensure critical access is still reviewed manually.
miniOrange regularly works with customers to tailor solutions to their specific access control requirements. If your use case calls for more granular reactivation logic, our team can help customize the app to meet your security and compliance needs.
Challenge 3: Missed Offboarding Leaves Security Gaps
The problem
When an employee leaves the organization, their access to internal tools should end immediately. But in many Crowd setups, there’s a delay between someone’s exit and the deactivation of their account. This opens up an unnecessary window of risk, sometimes for days or even weeks.
Why this is more than an oversight
Every lingering account is a potential entry point. If a former employee still has access to your Crowd instance, they can view sensitive issues, clone repositories, or access internal documentation they no longer have any business seeing. From a compliance standpoint, this is a red flag during SOC 2 or ISO 27001 audits.
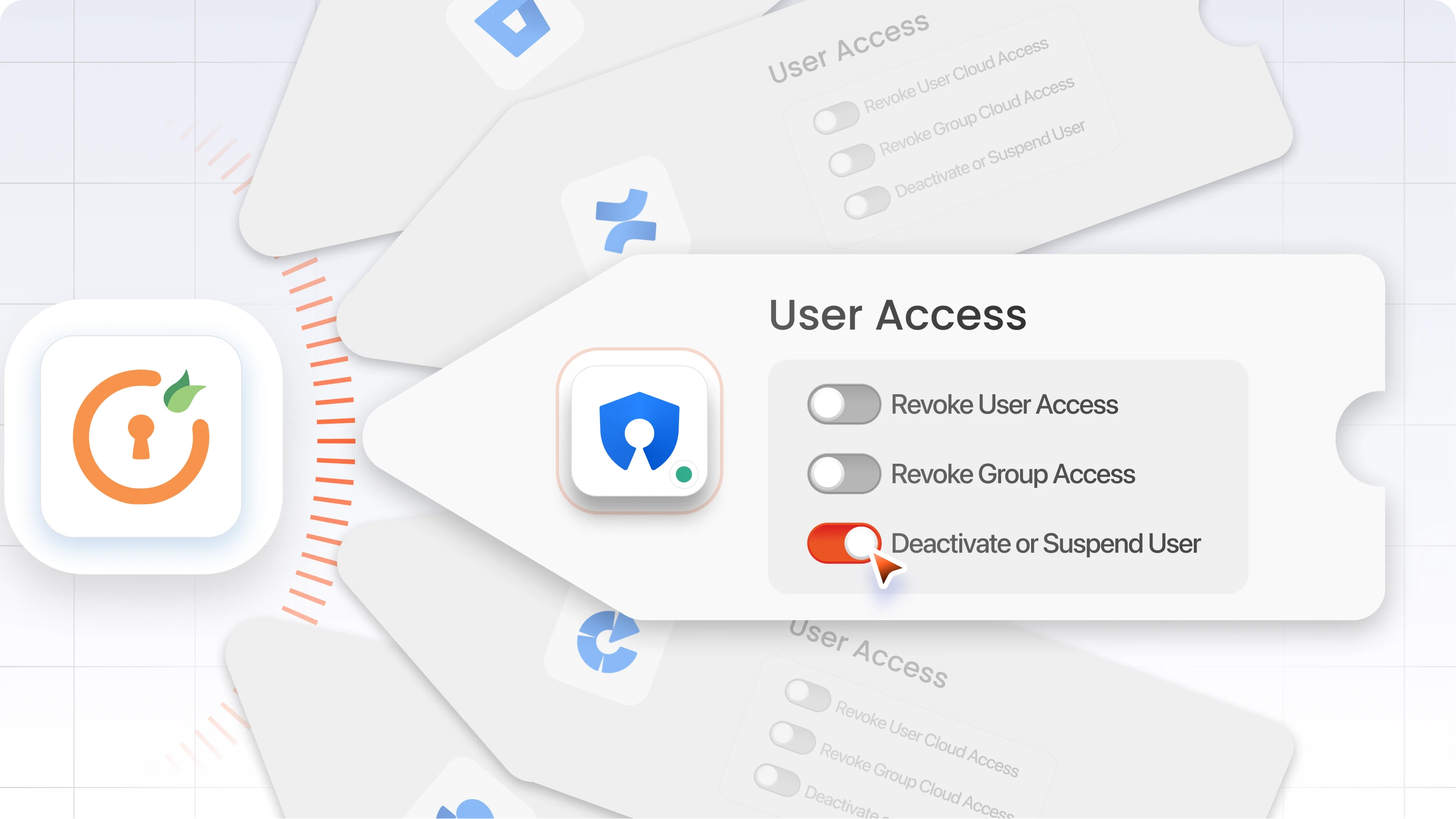
How to fix it with automation
With the miniOrange Automated User Management app for Crowd, you can sync user status from your source of truth, typically an HR platform or a central identity provider like Azure AD, Okta, or LDAP.
When a user is marked as "terminated" or "inactive" in the upstream system, their access in Crowd is revoked immediately.
You can also define workflows based on scheduled cleanups. For example, run a daily or weekly schedular that scans for users that no longer exist in your core directory or whose accounts are flagged for removal.
What else can be automated
- Removal from project-specific groups or roles
- Email notifications to team leads or security reviewers
- Conditional deactivation: e.g., only if the user hasn’t logged in for X days after HR deactivation
Security advantage
By automating offboarding, you reduce the gap between user exit and access removal. This not only strengthens your security posture but also makes access governance more reliable and consistent across teams.
Challenge 4: Group Management Chaos Creates Permission Creep
The problem
Group-based access is a powerful mechanism in Crowd. It allows you to define roles, control project-level permissions, and manage access to Atlassian apps like Jira, Confluence, and Bitbucket.
But as teams shift, projects close, and employees move between roles, group memberships rarely get updated. Over time, users end up with more access than they need—or should have.
Why this becomes dangerous over time
This phenomenon, known as permission creep, is one of the most common causes of internal security lapses. A user might move from engineering to product but still retain access to repositories, admin panels, or private documentation from their previous role. It’s not necessarily malicious, but it’s still a risk.
Why it happens
Group access is often granted with good intent but forgotten later. There's no expiry logic or ownership tracking by default. Once a user is added to a group, they typically stay there unless someone notices and manually removes them.
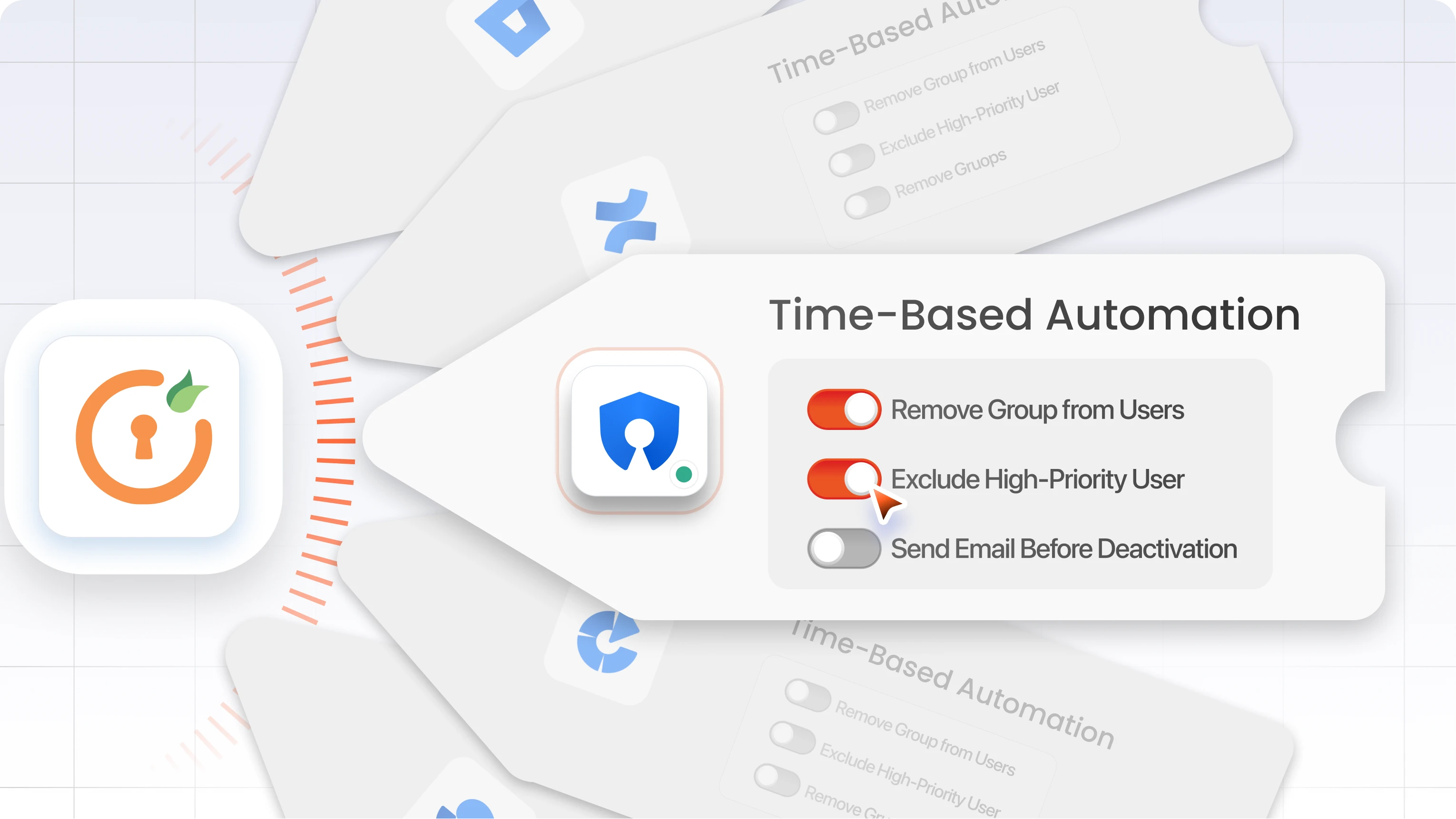
How to manage groups with automation
You can define time-based rules to automatically remove users from certain groups after a specific period. For example, if someone is added to a temporary “Project-X-Access” group, you can configure it to expire after 30 days unless explicitly extended.
Alternatively, use event-based triggers: if a user’s role or department changes in your upstream directory, update their group memberships in Crowd automatically to reflect the new structure.
What visibility looks like with miniOrange
The miniOrange app maintains group membership audit logs, so you always know:
- When a user was added to or removed from a group
- What triggered the change (manual, scheduled, or event-based)
- Who approved or initiated it (if workflows require sign-off)
Compliance and governance benefit
These logs are not just helpful for debugging, they’re essential during access reviews, audits, or compliance checks. You can export group history reports to demonstrate adherence to the principle of least privilege.
Challenge 5: Audit Season Becomes a Last-Minute Rush
The problem
When it’s time for an internal audit or compliance check, admins often scramble to gather logs, access histories, and change records. The data is either incomplete or scattered across systems.
Why it happens
Manual user management rarely includes centralized, searchable activity tracking. Without proper audit logging, it’s hard to prove access compliance after the fact.
How to fix it with automation
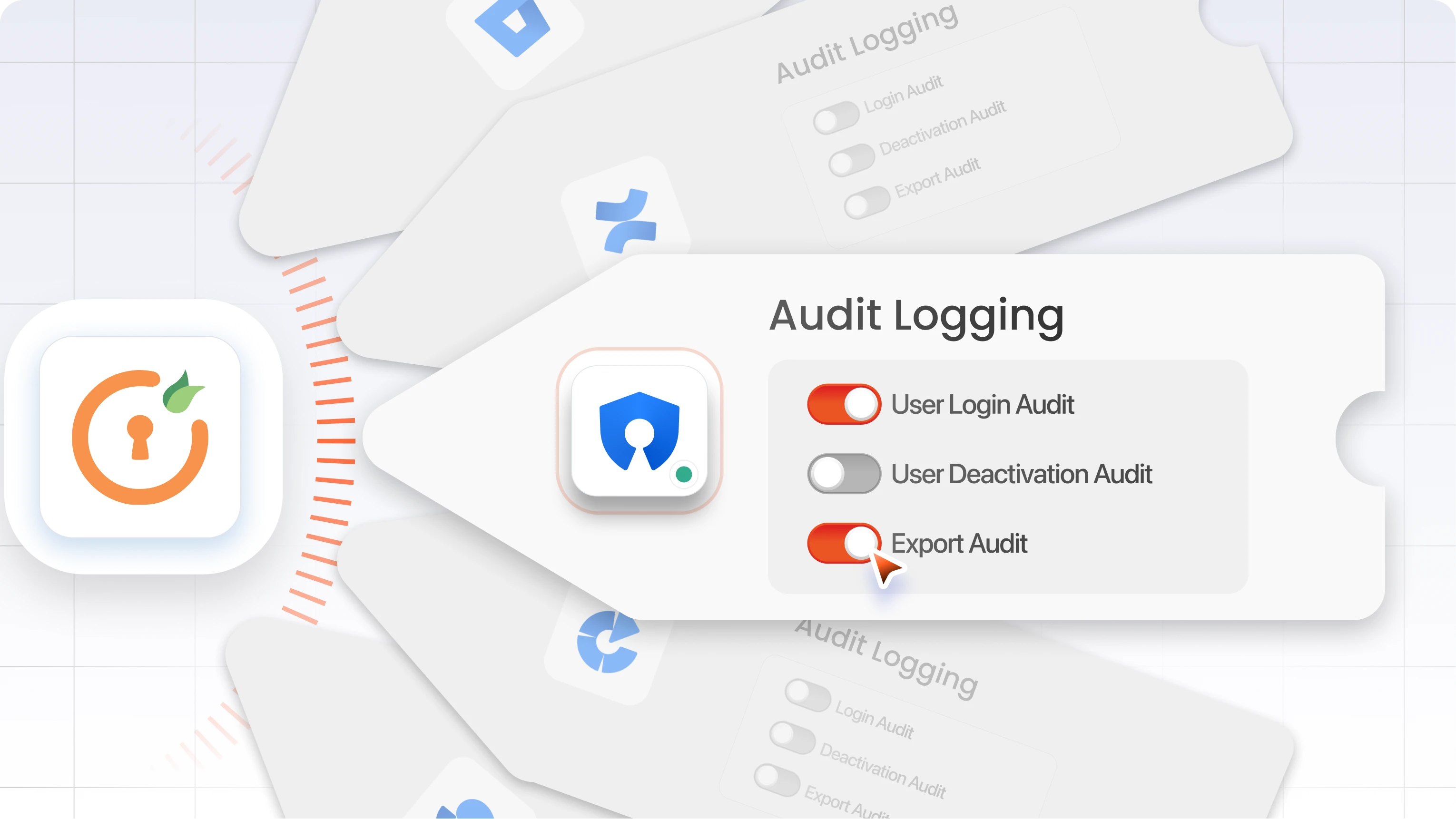
The miniOrange app’s extensive audit logging feature ensures all account activity is captured, whether it's a login, deactivation, or group change. This information can be exported easily for audits, reducing preparation time and increasing accuracy.
Compliance advantage
This approach supports audit-readiness as a continuous state, not just a year-end panic.
How miniOrange Brings It All Together
The miniOrange Automated User Management app for Crowd is built for admins who want greater control without the repetitive overhead. It addresses the full spectrum of Crowd user lifecycle challenges—from onboarding to deactivation, through targeted, no-code automation.
With this app, you can:
- Automatically deactivate inactive users based on login thresholds
- Instantly reactivate users upon valid login attempts
- Trigger offboarding based on HR events or directory sync
- Manage group memberships with conditions and expiry timers
- Maintain proper logs for every user and group action
The goal isn’t just automation. It’s safe, scalable, and compliant user management that adapts to your organization’s workflow.
Whether you're managing a lean engineering team or a growing enterprise setup with multiple directories, the app helps you reduce manual interventions and security risks, without losing visibility.
Final Thoughts
Managing users in Atlassian Crowd doesn’t need to be a reactive, ticket-driven process. With the right automation in place, it becomes predictable, secure, and surprisingly hands-off. The five challenges we covered aren’t edge cases, they're recurring friction points that add up over time.
By proactively automating user management, you not only save time but also reduce risk, improve compliance, and increase team efficiency.
If you’re ready to move beyond spreadsheets and reactive workflows, explore how miniOrange can help you make Crowd administration smarter and simpler.



Leave a Comment