What is Zero Trust Security & How does it work ?
Zero Trust is an approach to perimeter-less security that helps create an effective environment, policies, and infrastructure to minimize data breaches. Although many enterprises were moving towards the Zero-Trust model, Remote working (Work From Home) accelerated it by ten folds.
Zero Trust assumes that no conventional network exists; networks maybe local, cloud-based, or a combination or hybrid with resources anywhere as well as workers in any location. Although a lot of sellers have tried to create their own definitions of Zero Trust, there are a number of recognized organization standards that can help you bring Zero Trust into alignment with your organization.
Remote Work increased demand for a zero trust model, because of its potential to remedy the Remote working challenges to security
What is Zero Trust ?
Zero Trust is a model that recognizes trust as a vulnerability and aims at eliminating trust from the Network while ensuring a simplified user experience. It assumes all users, devices, and endpoints are compromised and verify all requests based on their identity and before giving any access to resources.
It reduces the risk of successful data breach and contains severity of breach by eliminating trust and preventing lateral movement.

Why is there a need for Zero Trust ?
In the legacy system, security is defined by protecting organization resources from external threats. In legacy systems, a VPN or Firewall is used to create a perimeter around the organization’s network. All users/devices within the organization network, are considered as trusted users/devices, have unrestricted access to all company resources.
The recent rise in the popularity of remote working brought forth new challenges to the existing security system. With the majority of users working remotely (using remote networks), relying on this approach is less effective, less efficient, and more dangerous.
What is a Zero Trust Architecture?
Zero Trust model encourages micro-segmentation – it involves identifying Protect surface, a collection of networks most critical assets, data, and applications, and creating a perimeter around it. These perimeters act like a firewall for the protected surfaces and ensure that known, allowed and legitimate traffic can access the protected surface.
Organizations can strengthen security by using granular policies, thus reducing the chances of a breach and improving containment of breach if any takes place.
How does the Zero Trust security model work?
In a Zero Trust system all users, within the organization network perimeter and outside the organization network perimeter are treated as untrusted. All the users requesting resources are verified and RBA sessions are used to grant user access to resources.
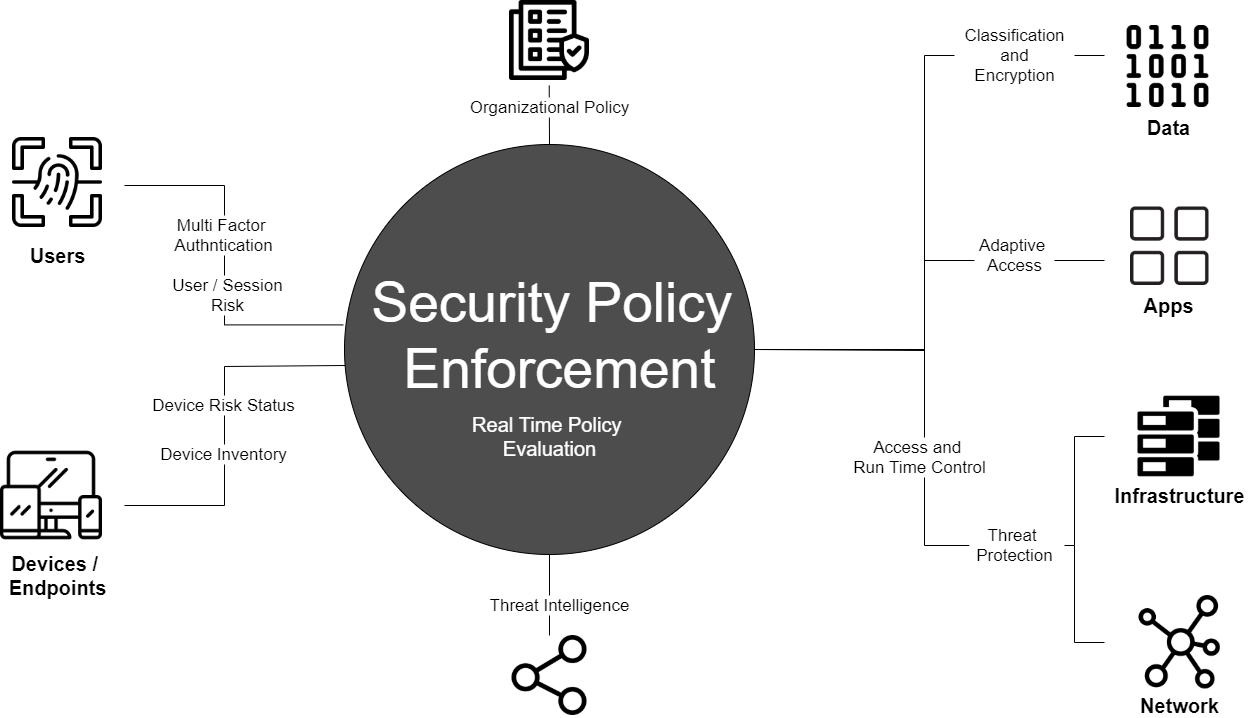
All the user requests and data pass through the security policy enforcement engine. This Security engine ensures protection by verifying device and identity before granting access to the data or applications, and further by monitoring session activities and implementing policies and threat assessment/intelligence.
Zero Trust Pillars
The philosophy behind zero-trust assumes that no user/device can be trusted and must be verified for authentication and authorization. The 4 pillars of the zero-trust approach are:
- Assumption of all environments being hostile and breached.
- Verifying user, user device.
- Focusing on data protection and not the breach attack.
- Least privilege access to all users.
- Real-time monitoring of traffic for Malicious activities.
Users and devices are always verified and given the least privileges and access to requested resources. Users need to request access to other resources and are verified again for them. This way, the zero trust approach offers unrealistic security.
Challenges to Zero Trust
As Zero trust is a security methodology, it requires organizations to evaluate their security strategies and parameters for their system and make consistent efforts to evaluate and improve existing strategies. Some of the major challenges are:
- Support for Zero trust system from management and users
- The rapid increase in devices leading to increased chances of unsecured end-point.
- The exponential growth of applications increases the need for tracking and monitoring.
Zero trust Maturity Curve
Zero trust is the Implementation of the zero tesut model that can be classified into various stages on the basis of adoption and protection.
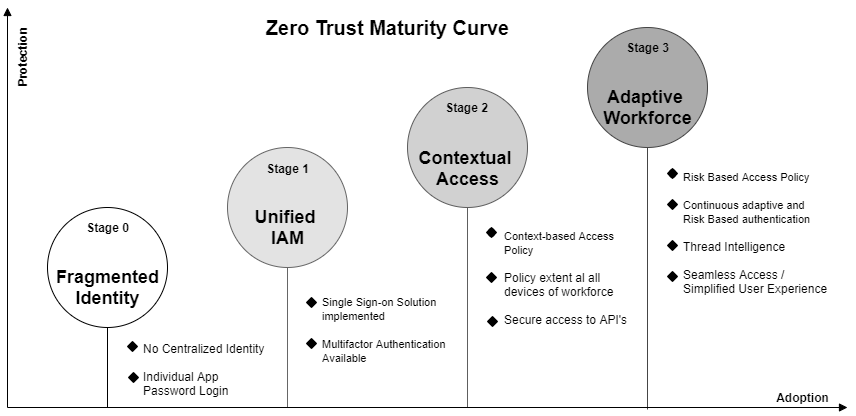
Stage 0: Fragmented Identities
Organizations use multiple On-premise and cloud applications, and most of them are not connected with each other or a centralized directory. Identities for the different applications are stored on a number of devices.
Due to these fragmented Identities, Securing and managing access to various applications becomes a challenge for IT, as it leaves large windows for attackers to exploit, and for users too, as it means they will need to maintain different login credentials for different applications.
This further increases the security concerns for IT probability of password fatigue or weak login credentials.
Stage 1: Unified IAM
This involves resolving the challenges from fragmented Identity. This can be accomplished by adopting an Identity and Access Management (IAM) or Single Sign-On (SSO) solution. It would enable identity defragmentation by unifying all identities into a single IAM system and ensuring smooth access to both on-premise and cloud apps with a single set of credentials.
A second-factor authentication method can also be implemented for additional security. Using access policy and group policy, securely access the Applications and resources.
Stage 2: Contextual Access
This involves adding a layer of context-based access policy on top of Unified IAM to gather context regarding, user, application, device, network and provide access based on these context markers. These policies will allow organizations to fine-tune the access policy and better control and monitor access to resources and secure access to API.
For example, Asking for 2-factor authentication if a user logins from a new location or device.
Stage 3: Adaptive Workforce
This can be defined as the last stage of Zero Trust implementation and focuses on Authentication & authorization access. At this stage, Authentication is a recurring process throughout the user experience through adaptive authentication and risk-based assessment to identify potential threats. Sessions are continuously monitored and Risk scores for sessions are calculated based on assessment. Security is increased through Risk intelligence while risk-based access help simplify the user experience.
Zero Trust History
The concept of zero trust has been around for a long time, dating back to the early 2000s. Zero trust is now a popular security model.



Leave a Comment