As organizations scale across cloud, hybrid, and remote-first environments, identity has become the most critical security layer. Traditional perimeter-based security models are no longer effective against modern threats such as credential theft, phishing attacks, insider risks, and unauthorized access to SaaS applications. This shift has made Identity and Access Management (IAM) a foundational requirement for enterprises of all sizes.
In 2026, businesses are actively investing in the best identity and access management tools to secure users, applications, APIs, and sensitive data regardless of location. Modern IAM platforms are expected to support Zero Trust security, adaptive authentication, regulatory compliance, and seamless user experiences across cloud and on-prem environments.
However, with dozens of vendors in the market, choosing the best IAM tools or the best IAM software can be challenging. Each solution differs in terms of security depth, deployment flexibility, governance capabilities, and suitability for remote workforces. Organizations today are looking for best rated identity and access management tools that not only protect access but also scale with business growth and evolving compliance needs.
In this guide, we evaluate the Top 11 Identity and Access Management tools in 2026, comparing leading identity and access management tools based on real-world enterprise use cases, security features, integration capabilities, and support for securing remote workforces. Whether you’re searching for the best IAM software for securing remote workforces, enterprise-ready IAM platforms, or specialized IAM security tools, this comparison will help you make an informed decision.
Why Identity and Access Management Tools Are Critical in 2026
In 2026, identity-based attacks have become one of the leading causes of security breaches, making identity and access management tools essential for protecting enterprise systems and data.
The best IAM tools help businesses enforce least-privilege access, continuously verify user identities, and secure access for remote and hybrid workforces. At the same time, modern IAM platforms support Zero Trust security principles and simplify compliance by centralizing identity controls and access auditing.
As a result, organizations increasingly depend on the best identity and access management tools to reduce risk, secure remote access, and maintain visibility over user identities in 2026.
Must-Have Features in the Best IAM Software
To effectively secure users, applications, and data in 2026, organizations must look beyond basic authentication. The best IAM software combines strong security controls with scalability, compliance readiness, and a seamless user experience. Below are the core features every modern IAM solution should include.
Single Sign-On (SSO)
Single Sign-On (SSO) allows users to access multiple applications with a single login, reducing password fatigue and improving productivity. It is a foundational capability of all leading identity and access management tools.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an additional layer of security by requiring multiple verification factors. The best IAM tools support adaptive and risk-based MFA to prevent unauthorized access.
Identity Governance and Administration (IGA)
IGA ensures proper identity lifecycle management through automated provisioning, deprovisioning, and access reviews, critical for compliance and audit readiness.
Role-Based Access Control (RBAC)
RBAC restricts access based on job roles, enforcing least-privilege principles and minimizing exposure to sensitive resources.
Access Request and Approval Workflows
Automated workflows simplify how users request access and how approvals are granted, reducing manual effort and access-related errors.
Cloud and On-Prem Integration
Modern IAM platforms must integrate seamlessly with cloud applications, on-prem systems, and legacy infrastructure to ensure consistent access control.
Self-Service Identity Management
Self-service capabilities allow users to reset passwords and manage access requests independently, improving user experience while reducing IT workload.
Reporting, Auditing, and Compliance
Detailed logs and reports help organizations monitor access activity, meet regulatory requirements, and respond quickly to security incidents..
Best Identity and Access Management Tools in 2026 (Quick Comparison)
With dozens of IAM vendors in the market, comparing solutions at a glance helps narrow down the right fit faster. The table below highlights the best identity and access management tools in 2026, based on deployment flexibility, core strengths, and ideal use cases.
| IAM Tool | Best For | Deployment Model | Core Strength |
|---|---|---|---|
| miniOrange | Overall IAM, compliance & PAM | Cloud, Hybrid, On-prem | Unified IAM + PAM platform |
| Okta | Cloud-first enterprises | Cloud | SaaS integrations |
| Microsoft Entra ID | Microsoft environments | Cloud / Hybrid | Native M365 identity |
| Ping Identity | Federated IAM | Hybrid | Adaptive authentication |
| CyberArk Identity | Privileged access–heavy environments | Hybrid | Advanced enterprise PAM |
| ForgeRock | Complex IAM architectures | Hybrid | Custom IAM & CIAM |
| JumpCloud | Zero Trust IAM | Cloud | Directory-first IAM |
| SailPoint | Identity governance | Cloud / Hybrid | IGA & access reviews |
| Auth0 | Developer & CIAM use cases | Cloud | API-first identity |
| OneLogin | SMBs & growing teams | Cloud | Simple SSO & MFA |
| AWS IAM | AWS-native environments | Cloud | AWS access control |
1. miniOrange – Best Overall Identity and Access Management Tool in 2026
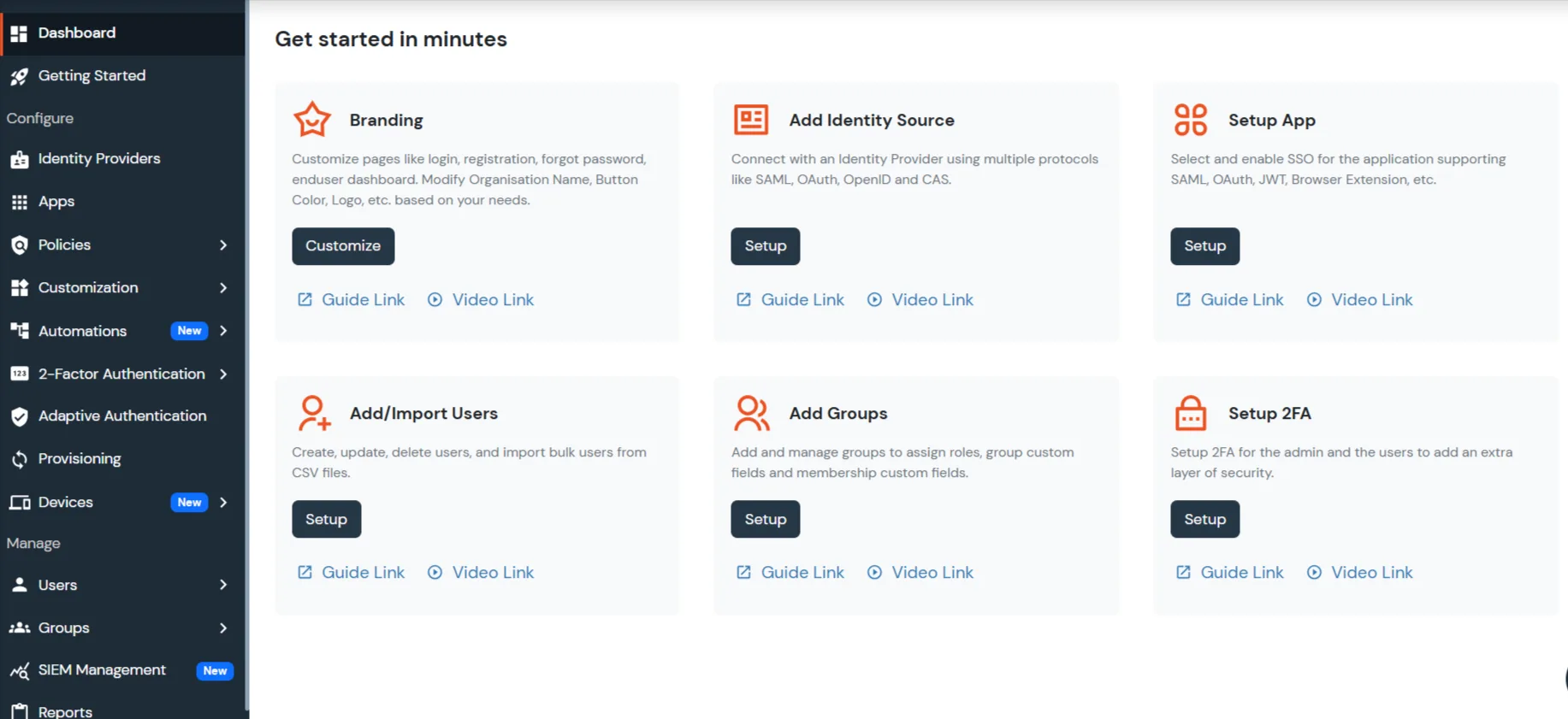
miniOrange ranks as the best identity and access management tool in 2026 due to its ability to deliver a comprehensive, enterprise-ready IAM platform that supports modern access needs across cloud, on-premise, and hybrid environments.
Unlike many IAM vendors that focus primarily on cloud-only use cases or limited identity layers, miniOrange provides a full-spectrum IAM solution designed to manage user identities, authentication, authorization, and governance from a centralized platform. This makes it particularly well-suited for organizations operating complex IT environments with diverse applications and access requirements.
Strong Identity and Access Management Capabilities
At its core, miniOrange excels as an IAM platform by offering all essential identity security capabilities required in 2026:
- Single Sign-On (SSO) to securely access multiple applications with one identity
- Multi-Factor Authentication (MFA) with adaptive and risk-based policies
- Passwordless authentication to reduce credential-based attacks
- Identity lifecycle management, including user provisioning and deprovisioning
- Role-Based Access Control (RBAC) to enforce least-privilege access
- Identity Governance and Administration (IGA) for compliance and audit readiness
These features allow organizations to maintain consistent access controls while improving both security posture and user experience.
Built for Hybrid and Enterprise Environments
One of miniOrange’s key strengths as an IAM solution is its deployment flexibility. The platform supports cloud, on-premise, and hybrid IAM deployments, making it ideal for enterprises that cannot rely on cloud-only identity solutions.
miniOrange integrates seamlessly with:
- Active Directory and LDAP
- Cloud platforms and SaaS applications
- Legacy systems
This ensures organizations can modernize identity management without disrupting existing infrastructure.
Support for Advanced Access Scenarios (Without Complexity)
In addition to workforce and application identity management, miniOrange also supports advanced access use cases, including elevated and sensitive access scenarios, within the same identity framework. This enables organizations to apply consistent authentication and access policies across all users without managing multiple disconnected tools.
Importantly, IAM remains the primary focus, with privileged access handled as an extension of identity control rather than a separate, siloed system.
Why miniOrange is the Best IAM Platform Overall
miniOrange stands out among the best-rated identity and access management tools because it offers:
- Deep IAM functionality
- Flexible deployment options
- Strong integration coverage
- Compliance-ready identity governance
- Scalability for both growing and large enterprises
Verdict: For organizations evaluating the best IAM tools or best IAM software in 2026, miniOrange offers the most complete and balanced identity and access management platform.
2. Okta
Okta is one of the most widely adopted IAM platforms for organizations that operate primarily in cloud and SaaS-based environments. It is commonly chosen by enterprises that need fast deployment, broad SaaS integrations, and centralized identity management without maintaining on-prem infrastructure.
Core Identity and Access Management Capabilities
Okta focuses strongly on cloud identity use cases and offers the following core IAM features:
- Single Sign-On (SSO) across thousands of SaaS applications
- Multi-Factor Authentication (MFA) with adaptive access policies
- Automated user provisioning and deprovisioning
- Lifecycle management for employees and contractors
- Centralized identity control for distributed teams
These capabilities make Okta one of the best IAM tools for organizations with a cloud-first security strategy.
Best Fit and Limitations
Okta performs best when identity management is centered around SaaS applications and cloud services. However, organizations with significant on-premise infrastructure or complex hybrid requirements may find it less flexible compared to broader IAM solutions.
- Best for: Cloud-native and SaaS-heavy enterprises
- Limitation: Higher cost and limited on-prem IAM flexibility
Summary: Okta remains a strong choice among identity and access management tools for cloud-first businesses, but it is best suited for environments with minimal on-prem or legacy system dependencies.
3. Microsoft Entra ID
Microsoft Entra ID (formerly Azure Active Directory) is a widely used identity and access management tool for organizations that rely heavily on Microsoft technologies. It is tightly integrated with Microsoft 365, Azure, and Windows environments, making it a natural IAM choice for businesses already operating within the Microsoft ecosystem.
Core Identity and Access Management Capabilities
Microsoft Entra ID provides essential IAM functionality designed to secure identities across Microsoft platforms:
- Single Sign-On (SSO) for Microsoft 365, Azure, and supported SaaS applications
- Multi-Factor Authentication (MFA) with conditional access policies
- User and group management tied to Microsoft services
- Device-based and location-based access controls
- Built-in identity protection and risk detection
These features make Entra ID a reliable option among IAM platforms for organizations seeking native Microsoft identity integration.
Best Fit and Limitations
Microsoft Entra ID works best when identity management is centered around Microsoft products. While it supports third-party integrations, its strongest capabilities are realized within Microsoft-managed environments.
- Best for: Organizations standardized on Microsoft 365 and Azure
- Limitation: Less flexibility for non-Microsoft or complex hybrid IAM scenarios
Summary: Microsoft Entra ID is a strong and dependable IAM solution for Microsoft-centric enterprises, but organizations with diverse infrastructure may require a more flexible identity and access management platform.
4. Ping Identity
Ping Identity is a well-established identity and access management platform designed for enterprises with complex authentication needs, large user bases, and identity federation requirements. It is commonly used by organizations that manage identities across multiple domains, partners, and customer-facing applications.
Core Identity and Access Management Capabilities
Ping Identity is particularly strong in scenarios where identity must be shared securely across systems and environments:
- Federated Single Sign-On (SSO) using standards like SAML and OpenID Connect
- Adaptive and risk-based authentication
- Passwordless authentication options
- Support for workforce IAM and customer IAM (CIAM)
- Scalable identity services for high-volume authentication
These capabilities position Ping Identity among the best IAM tools for enterprises operating at scale.
Best Fit and Limitations
Ping Identity is best suited for organizations with mature identity requirements and in-house technical expertise. While powerful, its setup and management can be more complex compared to simpler IAM platforms.
- Best for: Large enterprises with federated identity and CIAM needs
- Limitation: Higher implementation complexity and cost
Summary: Ping Identity is a strong choice among identity and access management tools for large-scale and federated environments, but it may be more than what smaller or less complex organizations require.
5. CyberArk Identity Security
CyberArk is best known for securing high-risk and privileged identities in enterprise environments. While it is not positioned as a full-spectrum IAM platform, CyberArk plays an important role in organizations where protecting administrative access and sensitive systems is a top priority.
Core Identity and Access Management Capabilities
CyberArk’s identity capabilities are centered around controlling and monitoring elevated access:
- Strong authentication for privileged and administrative users
- Least-privilege access enforcement
- Privileged session monitoring and control
- Integration with broader identity ecosystems for centralized access enforcement
These capabilities make CyberArk relevant among identity and access management tools when privileged access is a major risk factor.
Best Fit and Limitations
CyberArk is most effective when used in environments that require deep control over privileged accounts. However, it is typically deployed alongside a broader IAM solution rather than replacing one entirely.
- Best for: Enterprises with heavy privileged access and administrative risk
- Limitation: Not designed to act as a standalone IAM platform for all users
Summary: CyberArk is a strong choice for organizations that need advanced protection for privileged identities, but it is best viewed as a complement to a broader IAM platform, rather than a complete identity and access management solution on its own.
6. ForgeRock
ForgeRock is an enterprise-grade identity and access management platform designed for organizations with highly complex IAM requirements. It is commonly used in large-scale environments that require extensive customization across workforce identities, customer identities, and digital services.
Core Identity and Access Management Capabilities
ForgeRock provides a flexible and extensible IAM framework that supports advanced identity use cases:
- Workforce IAM and Customer IAM (CIAM) from a unified platform
- Single Sign-On (SSO) and strong authentication options
- Identity federation and standards-based integrations
- Directory services for managing large identity volumes
- Support for IoT and non-human identities
These capabilities place ForgeRock among the more advanced IAM platforms available for enterprises with complex architectures.
Best Fit and Limitations
ForgeRock is best suited for organizations with mature identity programs and dedicated technical teams. Its flexibility comes at the cost of higher implementation effort and ongoing management complexity.
- Best for: Large enterprises requiring highly customizable IAM solutions
- Limitation: Steep learning curve and resource-intensive deployment
Summary: ForgeRock is a powerful option among identity and access management tools for complex, large-scale environments, but it is often excessive for organizations seeking simpler or faster-to-deploy IAM solutions.
7. JumpCloud
JumpCloud is a modern identity and access management platform built around a cloud-based directory and Zero Trust principles. It is often adopted by IT teams looking to replace traditional on-prem directories while maintaining centralized identity control.
Core Identity and Access Management Capabilities
JumpCloud focuses on unifying identity, device, and access management through a directory-first approach:
- Cloud-based directory services
- Single Sign-On (SSO) and Multi-Factor Authentication (MFA)
- Device trust and policy enforcement
- Centralized user and device management
- Integration with popular SaaS applications
These features make JumpCloud a practical choice among IAM platforms for organizations adopting Zero Trust security models.
Best Fit and Limitations
JumpCloud works best for organizations that want a modern alternative to traditional directory services. However, it offers more limited identity governance features compared to full enterprise IAM suites.
- Best for: Mid-sized organizations moving to Zero Trust
- Limitation: Limited depth in identity governance and advanced IAM workflows
Summary: JumpCloud is a strong option among identity and access management tools for Zero Trust adoption, particularly for organizations seeking simplified directory and access management in cloud-centric environments.
8. SailPoint
SailPoint is widely recognized for its strong focus on identity governance and administration (IGA). It is commonly used by large enterprises that need strict access controls, regular access reviews, and audit-ready identity processes.
Core Identity and Access Management Capabilities**
SailPoint specializes in governance-centric IAM capabilities that help organizations maintain visibility and control over user access:
- Identity governance and administration (IGA)
- Automated access certifications and reviews
- Policy-based access controls
- Risk-based identity insights
- Integration with existing IAM platforms and directories
These capabilities make SailPoint a key player among identity and access management tools when compliance and governance are primary requirements.
Best Fit and Limitations
SailPoint is most effective in environments with complex compliance obligations and large user populations. However, it typically functions as a governance layer alongside other IAM solutions rather than as a standalone IAM platform.
- Best for: Large enterprises with strict regulatory and audit requirements
- Limitation: Requires integration with other IAM tools for full access management
Summary: SailPoint is a strong choice for organizations that prioritize identity governance and compliance, but it is best used as part of a broader IAM platform strategy rather than a complete end-to-end IAM solution.
9. Auth0
Auth0 is a developer-focused identity and access management solution designed primarily for securing customer-facing applications and APIs. It is widely adopted by SaaS companies and product teams that need flexible, scalable authentication without building identity infrastructure from scratch.
Core Identity and Access Management Capabilities
Auth0 is optimized for application and customer identity use cases rather than workforce IAM:
- API-first authentication for web and mobile applications
- Support for OAuth, OpenID Connect (OIDC), and SAML
- Built-in Single Sign-On (SSO) for customer identities
- Multi-Factor Authentication (MFA) and adaptive login flows
- Scalable infrastructure for high-volume user authentication
These features position Auth0 among the best IAM software options for developer-led and CIAM scenarios.
Best Fit and Limitations
Auth0 performs best when used to secure applications and digital products. However, it lacks the broader governance and lifecycle management features required for enterprise workforce IAM.
- Best for: SaaS products, development teams, and CIAM use cases
- Limitation: Not designed as a standalone IAM platform for workforce access
Summary: Auth0 is a strong choice for organizations building customer-facing applications, but it is best complemented with a full identity and access management platform when workforce identity and governance are required.
10. OneLogin
OneLogin is an identity and access management tool designed for small to mid-sized businesses that need core IAM functionality without the complexity of enterprise-heavy platforms. It is often chosen by growing teams looking to centralize access control quickly and efficiently.
Core Identity and Access Management Capabilities
OneLogin focuses on delivering essential IAM features that are easy to deploy and manage:
- Single Sign-On (SSO) for cloud applications
- Multi-Factor Authentication (MFA) with multiple verification methods
- User provisioning and deprovisioning
- Centralized access management for SaaS tools
- Basic directory and role management
These features make OneLogin a practical option among identity and access management tools for organizations that are early in their IAM journey.
Best Fit and Limitations
OneLogin works best for businesses that require straightforward IAM without advanced governance or complex hybrid deployments.
- Best for: SMBs and fast-growing teams
- Limitation: Limited depth in identity governance and advanced IAM workflows
Summary: OneLogin is a solid IAM solution for smaller organizations seeking simplicity and quick deployment, but larger enterprises may require a more robust IAM platform as they scale.
11. AWS IAM
AWS IAM is a native identity and access management service designed specifically to control access within Amazon Web Services environments. It enables organizations to define and manage permissions for users, roles, and services operating on AWS.
Core Identity and Access Management Capabilities
AWS IAM provides fine-grained control over access to AWS resources:
- Role-based and policy-driven access control
- Permissions for AWS users, roles, and services
- Integration with AWS services and workloads
- Temporary credentials and role assumption
- Centralized management of AWS access policies
These capabilities make AWS IAM a key component of cloud security within AWS-centric environments.
Best Fit and Limitations
AWS IAM is highly effective for managing access inside AWS but is not designed to function as a cross-platform IAM solution.
- Best for: Organizations operating primarily on AWS
- Limitation: Not suitable as a standalone IAM platform for non-AWS systems
Summary: AWS IAM is essential for securing AWS resources, but organizations with multi-cloud or hybrid environments typically pair it with broader identity and access management platforms.
Benefits of Using Identity and Access Management Tools
Using identity and access management tools helps organizations secure access, streamline identity operations, and maintain compliance across modern IT environments. Below are the key benefits businesses gain by implementing the best IAM tools.
- Stronger security posture
- Enforces Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), and least-privilege access
- Reduces risks from credential theft, phishing, and unauthorized access
- Centralized access control
- Manages user identities and permissions across cloud, on-prem, and hybrid environments
- Improves visibility into who has access to what
- Improved operational efficiency
- Automates user onboarding, offboarding, and role changes
- Reduces manual IT effort and access-related errors
- Compliance and audit readiness
- Maintains detailed access logs and audit trails
- Supports regulatory requirements through access reviews and policy enforcement
- Better user experience
- Enables Single Sign-On (SSO) for seamless access across applications
- Reduces password fatigue and login friction
- Scalability for growing organizations
- Adapts easily to remote workforces, SaaS adoption, and business growth
- Supports secure access without increasing administrative complexity
How to Choose the Best IAM Tool for Your Business
- Define access scope
- Identify workforce, customer, partner, and privileged access needs
- Assess environment complexity
- Cloud-only, hybrid, or on-prem infrastructure requirements
- Evaluate policy flexibility
- Ability to define role-based, context-aware, and risk-based policies
- Check standards and protocol support
- SAML, OAuth, OIDC, SCIM compatibility
- Review governance controls
- Access reviews, approvals, and audit reporting
- Plan for future growth
- Ability to scale users, apps, and integrations
- Validate vendor maturity
- Product roadmap, documentation, and long-term support
Future of Identity and Access Management Tools
Identity and access management is evolving rapidly as organizations adopt Zero Trust, AI-driven security, and remote-first operating models. Below are the key trends shaping the future of identity and access management tools.
- AI-driven identity security
- Use of machine learning to detect anomalous login behavior
- Risk-based authentication decisions in real time
- Passwordless authentication adoption
- Increased use of biometrics, passkeys, and hardware-backed authentication
- Reduced reliance on passwords to prevent phishing attacks
- Zero Trust as the default security model
- Continuous verification of users, devices, and sessions
- No implicit trust based on location or network
- Unified identity across environments
- Centralized identity management across cloud, on-prem, hybrid, and SaaS systems
- Consistent access policies regardless of infrastructure
- Greater focus on privacy and compliance
- Stronger access controls aligned with evolving data protection regulations
- Built-in governance, audits, and reporting
- Automation in identity governance
- Automated access reviews, approvals, and remediation
- Reduced human error in identity lifecycle management
FAQs
What are identity and access management (IAM) tools?
Identity and access management tools are solutions that help organizations manage digital identities and control access to applications, systems, and data. They ensure that the right users have appropriate access while preventing unauthorized entry.
Which are the best identity and access management tools in 2026?
The best identity and access management tools in 2026 include platforms like miniOrange, Okta, Microsoft Entra ID, Ping Identity, and others. The best choice depends on deployment needs, compliance requirements, and whether the organization operates in cloud, hybrid, or on-prem environments.
How do IAM tools help secure remote workforces?
IAM tools secure remote workforces by enforcing Multi-Factor Authentication (MFA), Single Sign-On (SSO), and context-based access controls. Many organizations rely on the best IAM software for securing remote workforces to ensure secure access regardless of user location or device.




Leave a Comment