Picture this: a growing company with hundreds of employees and dozens of apps, from HR tools to project platforms. Each team member juggles multiple passwords, and IT spends hours every week resetting accounts. It’s not just frustrating, it’s risky. In fact, 54% of organizations experienced breaches due to compromised credentials, underscoring the fragility of password sprawl.
That’s where Single Sign-On (SSO) steps in. SSO allows users to log in once and access all authorized applications securely, making it essential for modern organizations that rely on multiple systems and cloud services. It simplifies authentication, reduces password-related risks, and improves employee productivity by cutting down login time and password resets.
But here’s the catch: when SSO is not properly configured, it can do more harm than good. Weak identity provider settings, misconfigured SAML responses, or missing MFA enforcement can make SSO a single point of failure. Attackers often exploit these weak links to gain unauthorized access, especially when token or session validation isn’t strictly enforced.
That’s why organizations must balance convenience with security. The goal isn’t just to make login easier but to ensure it’s safer. Enabling MFA, auditing identity provider configurations, and applying role-based access controls help achieve this balance.
To support this, miniOrange provides a trusted SSO solution for all business environments, whether cloud, on-premises, or hybrid. With enterprise-ready features, multi-protocol support, and strong security controls, miniOrange helps organizations simplify access while keeping their data and users protected.
Common Types of SSO Implementations
Every organization has a different mix of systems, some in the cloud, others on-premises, and a few legacy apps that still run critical operations. That’s why SSO implementation isn’t the same for everyone. Here are the most common types you’ll find in enterprise environments today:
SAML-based SSO
Commonly used in large enterprises for various applications. It relies on XML-based assertions to exchange authentication data between the Identity Provider (IdP) and the Service Provider (SP), ensuring secure access without repeated logins.
OAuth 2.0 / OpenID Connect
Best suited for web and cloud applications. It uses token-based authentication, allowing users to log in through trusted providers like Google or Microsoft without sharing passwords directly.
LDAP-based SSO
Ideal for internal or legacy applications. It authenticates users against existing directories such as Active Directory, making it easier to extend SSO to systems that don’t support modern protocols.
Kerberos-based SSO
Commonly used in Windows domains and on-premise environments. It uses encrypted tickets for user authentication, removing the need for users to re-enter credentials while keeping communication secure within the network.
Regardless of how diverse your IT environment is, miniOrange supports all major SSO protocols, SAML, OAuth, OpenID Connect, LDAP, and Kerberos, ensuring compatibility across both modern and legacy applications. This flexibility helps organizations connect every app under a single, secure identity framework without compromise.
Comparing SSO Protocols – SAML vs OAuth vs OpenID Connect
Not all SSO systems work the same way. The right protocol depends on where your apps are hosted, how users authenticate, and what kind of access control you need. Here’s a quick comparison of the most common SSO standards used across organizations today:
| Protocol | Best For | Key Strength | Common Use Case |
|---|---|---|---|
| SAML (Security Assertion Markup Language) | Enterprise and business apps | Uses XML-based assertions for secure exchange of identity data between the Identity Provider and Service Provider | Ideal for enterprise tools like Salesforce, SAP, or Oracle |
| OAuth 2.0 | Web, mobile, and API-based applications | Provides secure delegated access using tokens instead of passwords | Common in platforms like Google Workspace, LinkedIn, and GitHub |
| OpenID Connect (OIDC) | Consumer and hybrid login systems | Adds an identity layer on top of OAuth 2.0 for user authentication and profile data exchange | Best for cloud and SaaS apps with social or external logins |
Read our detailed blog “What is the Difference Between SAML, OAuth, and OpenID Connect?” to dive deeper into how each protocol works and when to use them.
What Makes an SSO Implementation Successful?
A well-executed SSO setup is more than linking apps; it’s about building a secure and scalable identity system that works across the organization. Here are the key factors that make an SSO implementation successful:
Understand your identity flow and application landscape – Map how users access systems, which apps are used, and where identities are stored. This ensures authentication flows stay consistent and efficient.
Integrate with a reliable Identity Provider (IdP) – The IdP is the backbone of your SSO setup. Choose one that supports multiple standards like SAML, OAuth, and OpenID Connect, and integrates easily with your user directories and MFA systems.
Streamline user provisioning and deprovisioning – Automate onboarding and offboarding so access is granted instantly when users join and revoked when they leave. This minimizes manual effort and reduces security risks.
Set consistent session and authentication policies – Define clear rules for session timeouts, MFA requirements, and re-authentication. Consistency in these settings ensures a balance between user convenience and data security.
Monitor authentication health and access logs – Continuously review access logs to identify unusual login attempts or suspicious activity early. Regular audits strengthen visibility and compliance.
When these practices come together, SSO becomes more than a convenience feature; it evolves into a core layer of secure, centralized access management that supports both productivity and protection.
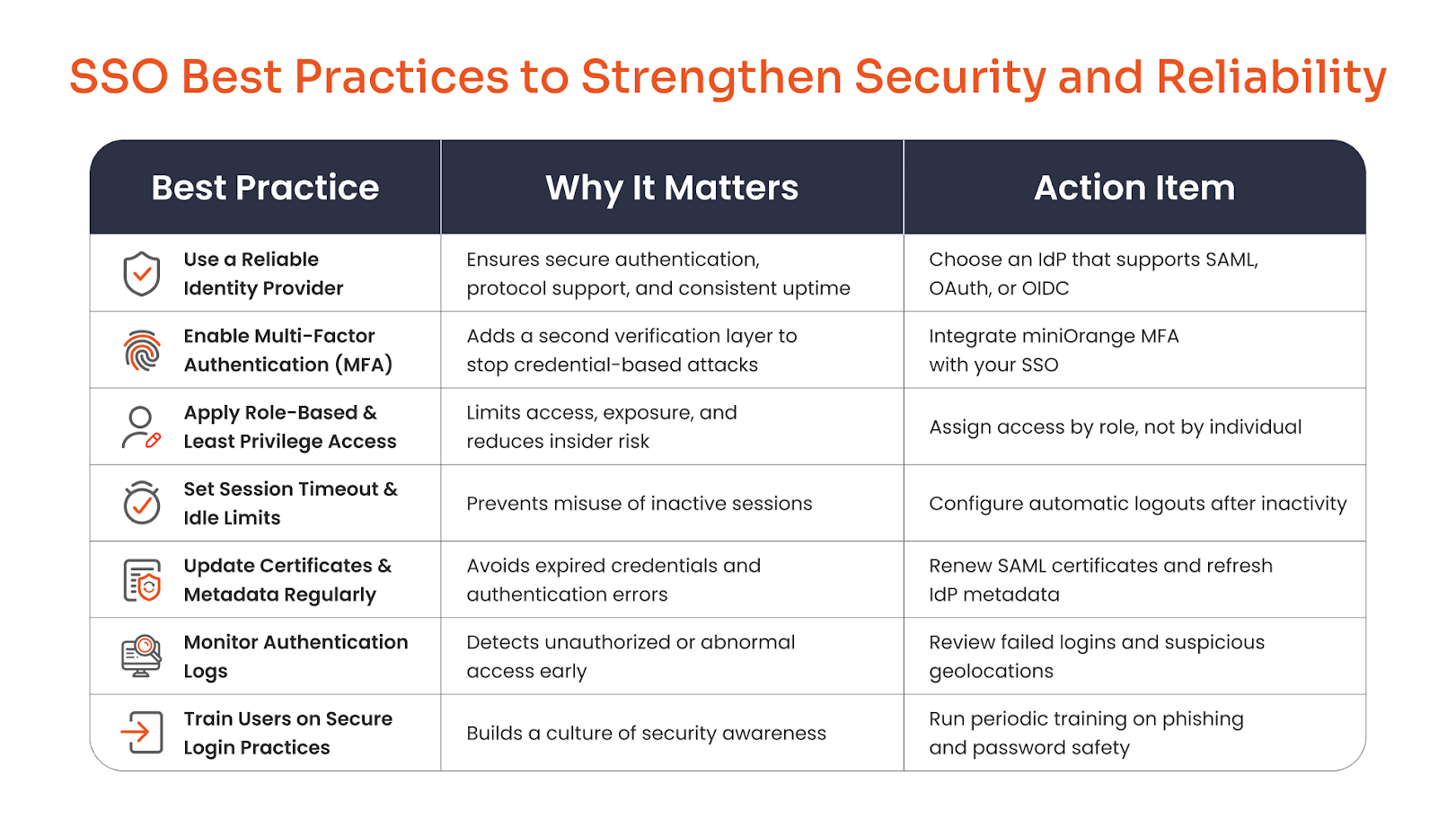
SSO Best Practices to Strengthen Security and Reliability
A well-implemented SSO system is only as strong as the practices that support it. Here are key steps every organization should follow to secure and stabilize its Single Sign-On setup.
1. Use a Reliable Identity Provider
Choose a trusted Identity Provider (IdP) that supports modern protocols such as SAML, OAuth, or OpenID Connect (OIDC). A dependable IdP ensures consistent authentication, high uptime, and smooth integration with your existing directory and cloud infrastructure.
2. Combine SSO with Multi-Factor Authentication (MFA)
Pairing SSO with MFA adds an essential layer of protection, especially for admins and privileged users. Even if credentials are compromised, MFA prevents unauthorized access. Explore Multi-Factor Authentication (MFA) solution by miniOrange to strengthen your identity security.
3. Apply Role-Based and Least Privilege Access
Not every user needs access to every application. Apply role-based access control (RBAC) and follow the principle of least privilege to limit permissions only to what’s necessary, minimizing the potential damage from compromised accounts.
4. Set Proper Session Timeout and Idle Limits
Avoid keeping sessions active indefinitely. Configure session timeout and idle limits so users are automatically logged out after inactivity. This helps prevent misuse from unattended or shared devices.
5. Keep Certificates and Metadata Up to Date
Expired or outdated certificates can cause authentication failures and open security gaps. Regularly renew SAML certificates, update IdP metadata, and verify connection integrity to maintain a healthy SSO setup.
6. Monitor Authentication Logs
Track login activity and review authentication logs for anomalies. Spotting failed login spikes or unusual geolocations early helps you act before a potential breach occurs.
7. Train Users on Secure Login Practices
Technology alone isn’t enough; users must know how to protect themselves. Conduct regular awareness sessions on phishing, password hygiene, and MFA adoption to build a culture of secure access.
Common Mistakes to Avoid During SSO Implementation
Even the best security tools fail when they’re not configured right, and SSO is no exception. A few oversights during setup can quickly weaken your entire access framework. Here’s what to watch out for:
Misconfigured certificates or time synchronization issues – Expired or mismatched certificates are among the top causes of SSO failure. Also, if your server and IdP clocks aren’t synchronized, authentication requests may get rejected due to timestamp mismatches.
Lack of redundancy or failover IdP setup – Relying on a single Identity Provider can bring everything to a halt if it goes down. Always configure backup IdPs or failover routes to keep authentication running smoothly during outages.
Ignoring user role mapping – Without proper role or group mapping, users may gain unnecessary privileges or lose access they need. Make sure every role in your IdP aligns with the right permissions in your applications.
Not testing SSO for all apps and user groups – Many teams test SSO for a few applications and assume it works everywhere. Run end-to-end tests for every app, department, and user group to uncover hidden misconfigurations before rollout.
Overlooking MFA for admin accounts – Admin accounts are the most targeted in attacks. Failing to enforce MFA here can undo all your security layers. Always pair admin logins with strong MFA methods.
How miniOrange Helps You Build a Secure SSO Environment
Implementing SSO shouldn’t mean spending weeks on custom integrations or endless troubleshooting. miniOrange makes it simple to build a secure, scalable SSO setup that fits right into your existing IT ecosystem.
Pre-built connectors for 5000+ apps and platforms – Connect instantly to popular business tools without writing complex code. miniOrange’s ready-to-use integrations save time and ensure reliability from day one.
Works with any Identity Provider (IdP) – Whether you use Azure AD, Okta, Ping, ADFS, or any other IdP, miniOrange ensures full compatibility. It supports all major protocols, SAML, OAuth, OpenID Connect, and LDAP, for flexible, secure authentication across environments.
Built-in MFA, adaptive access, and conditional policies – Security doesn’t stop at login. miniOrange integrates Multi-Factor Authentication, adaptive risk-based access, and conditional policies to strengthen protection without disrupting user experience.
On-premise, cloud, and hybrid deployment flexibility – No matter where your applications reside, miniOrange fits right in. You can deploy SSO entirely on-premise, in the cloud, or through a hybrid setup that connects both worlds.
24/7 technical assistance for setup and troubleshooting – miniOrange’s expert team is available around the clock to help configure, test, and optimize your SSO environment, ensuring smooth authentication and ongoing compliance.
With miniOrange, organizations can secure access, streamline user experience, and stay compliant, all through a single, unified identity platform.
Fixing these early helps prevent login disruptions, compliance issues, and unauthorized access, turning SSO into a secure gateway rather than a single point of failure.
Conclusion
Following the right SSO best practices helps organizations maintain both strong security and seamless productivity. A well-planned SSO strategy not only streamlines user access but also minimizes credential-based risks that often lead to breaches.
Pairing Single Sign-On (SSO) with Multi-Factor Authentication (MFA) creates the right balance between convenience and control, making it harder for attackers to break in while keeping access simple for users.
Looking to simplify secure access?
Contact miniOrange to set up SSO for your organization today and experience a unified, secure, and hassle-free authentication environment.
FAQs
What is the most important SSO best practice?
Always use a reliable Identity Provider (IdP) that supports modern protocols and pair it with Multi-Factor Authentication (MFA). Continuous login monitoring and timely certificate updates also help maintain long-term security.
Should I use SSO with MFA?
Yes. MFA adds a critical extra layer of protection against compromised credentials. Even if a password is stolen, MFA ensures that unauthorized users can’t access sensitive systems.
How do I monitor SSO security?
Enable login auditing within your IdP, set up alerts for unusual patterns such as repeated failed logins or unexpected geolocations, and review access logs regularly to catch anomalies early.
What are common SSO mistakes?
Common pitfalls include misconfigured metadata, expired certificates, and untested user role mappings. These small oversights often lead to access issues or potential breaches if not caught in time.
Does miniOrange support all SSO protocols?
Yes. miniOrange supports all major SSO standards, including SAML, OAuth, OpenID Connect, Kerberos, and LDAP, ensuring secure and consistent access across cloud, on-premise, and hybrid environments.





Leave a Comment