Need Help? We are right here!
Search Results:
×






Discover the best-in-class MFA products and get optimal security for your devices, accounts, systems, and resources.
Enable users to self-enroll with admin-approved MFA methods during their first login, reducing IT overhead.
Enhance workforce productivity with Passwordless MFA through login options such as biometrics, push notifications, and authenticator apps, eliminating password fatigue.
Enforce dynamic security controls with a powerful MFA solution. Use Adaptive MFA for policies based on IP, device, location, and time to trigger actions like Allow, Challenge MFA, or Deny.
Assign MFA policies based on user roles or application access needs, ensuring precise security control.
Gain insights into user activity, audit logs, and session reports for phishing-resistant MFA, ensuring compliance with GDPR, HIPAA, SOX, and more.
Maintain secure access with backup authentication options, such as security questions or email OTPs, when primary methods are unavailable.
Secure every access point with a multi-factor authentication solution that protects VPNs, servers, apps, & devices without disrupting user productivity.
Secure VPN access with MFA for VPN across Fortinet, Cisco, Palo Alto, SonicWall, OpenVPN, Citrix, and more. It works with all RADIUS protocols (CHAP, PAP, etc.), and no extra proxy module is needed.
Explore MFA for VPN
Add MFA to Windows login, RDP, RD Web, SSH (Linux), and Mac, which also supports domain-joined and standalone machines. Get offline and off-domain authentication for secure access anytime.
Explore MFA for Windows and RDP
Protect firewalls, switches, and routers with RADIUS and TACACS+ MFA using the AAA framework. TACACS+ Authentication supports devices from Cisco, Juniper, Nokia, and Huawei. Secure your entire network infrastructure with an external proxy.
Explore MFA for Network Devices
Secure Cloud MFA, on-prem, and custom apps like PHP, .NET, React, Node.js, with MFA for web apps. It also supports SAML, RADIUS, OpenID, and JWT for seamless and secure authentication.
Explore MFA for Web Apps
Add MFA to Oracle EBS, SAP, QlikView, PeopleSoft, OWA, Siebel CRM, and more. Avail no-code integration, save time and resources, and no development is needed.
Explore Legacy App MFA
Assesses user risk, based on profile, location, device, and behavior, to determine the security level of each login attempt. Activates additional authentication steps only when unusual or high-risk activity is detected, keeping access simple for trusted situations.
Explore Adaptive MFA
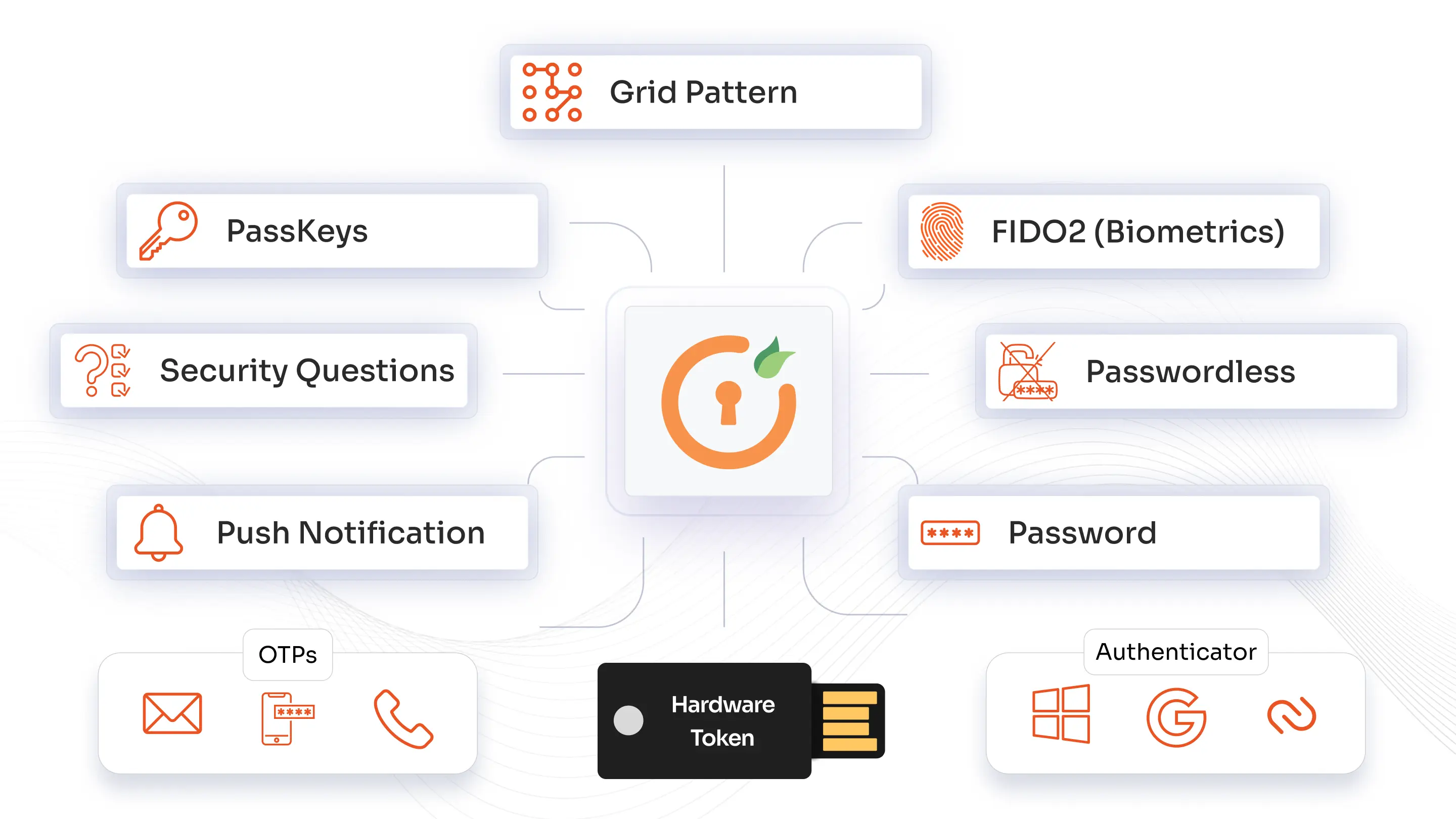
miniOrange authentication methods secure user access with SMS and phone callback for mobile validation, time-based OTP tokens via popular authenticator apps like Google or Microsoft. Users can also verify via secure email links or codes, use physical USB hardware tokens for added security, and authenticate through personalized knowledge-based security questions.
Identity solutions from miniOrange can be easily deployed in your organization's existing environment.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Our enterprise MFA solution is meticulously developed for large organizations, offering scalability to accommodate tens of thousands of users and support complex IT environments without compromising performance or reliability.
By integrating adaptive, context-aware authentication and risk-based access controls, our MFA security solution enables real-time threat detection and continuous security monitoring, which are essential pillars of a zero-trust architecture.
Applying layered security measures like phishing-resistant MFA and Two-Factor Authentication (2FA) builds confidence with the workforce, clients, and partners by preventing illegal access and protecting privacy.
The MFA platform can substantially minimize IT management costs by reducing security breaches and decreasing the number of help desk calls related to password issues. This lessens the workload burden on security teams.
Establish flexibility and productivity for users by providing over 15 different MFA methods that meet their style and preferences.
MFA solution requires users to verify their identity using two or more different factors, such as a password plus a phone code or fingerprint, before accessing an account or system.
Multi-factor authentication software works by asking for varied proofs of identity from different categories (something you know, something you have, or something you are). Even if one factor is compromised, unauthorized access is prevented.
By adding extra layers of verification, the MFA security solution blocks unauthorized users even if passwords are leaked. It helps protect against credential theft, phishing, and brute-force attacks, ensuring safer access.
MFA tokens are used in multi-factor authentication to check the identity of a user while logging into the system. It is one of those factors where the users need to prove they are who they are.
Yes, miniOrange offers a modern MFA tool that is designed for easy integration with existing systems and applications, enabling quick deployment while maintaining a smooth user experience and strong security.
Yes, miniOrange offers a 30-day free trial for its MFA solution to test and experience the product’s capabilities.
