Quick Intro
Your company is using dozens of cloud apps every day, Google Workspace, Slack, Salesforce, Zoom. It feels smooth and productive until one day you realize sensitive files are being shared outside your company. Or someone logs in from a suspicious location.
You ask yourself: How do I keep all these cloud apps secure?
That’s where SSPM (SaaS Security Posture Management) and CASB (Cloud Access Security Broker) come in. Both protect your business, but they work in very different ways.
Let’s break it down in plain English.
What is SaaS Security Posture Management (SSPM)?
SSPM is a cloud security solution designed to fix misconfigurations, monitoring access, ensure compliance, and secure SaaS (Software-as-a-Service) applications like Google Workspace, Microsoft 365, Salesforce, Slack, Zoom, etc.
Most SaaS breaches don’t happen because of hackers, they happen because of misconfigurations. SSPM finds and fixes those before they cause damage.

Key Features of SSPM
- Misconfiguration detection: Continuously scans for risky settings, like public file sharing, disabled MFA, or unused admin roles.
- Compliance assurance: Maps security posture to standards like GDPR, HIPAA, ITAR, DORA, SOC2, and ISO. This reduces audit headaches.
- Automated remediation: Suggests quick fixes or automates them, closing risks before they escalate.
- Continuous monitoring: Unlike a one-time audit, SSPM checks your apps daily, so new risks are flagged right away.
- Risk scoring: Provides visibility into which SaaS apps pose the biggest threats, so IT can prioritize.
Example: If Microsoft 365 has weak password policies, SSPM detects it and recommends strengthening them immediately.
What is a Cloud Access Security Broker (CASB)?
Cloud Access Security Broker (CASB) solution is a security tool that is placed between your users and cloud apps, making sure only the right people access the right data, under the right conditions.
Think of it as a security checkpoint for cloud services like Google Workspace, Microsoft 365, Salesforce, Dropbox, etc. Whenever a user tries to access, upload, download, or share data in these cloud apps, the CASB enforces the organization’s security policies.
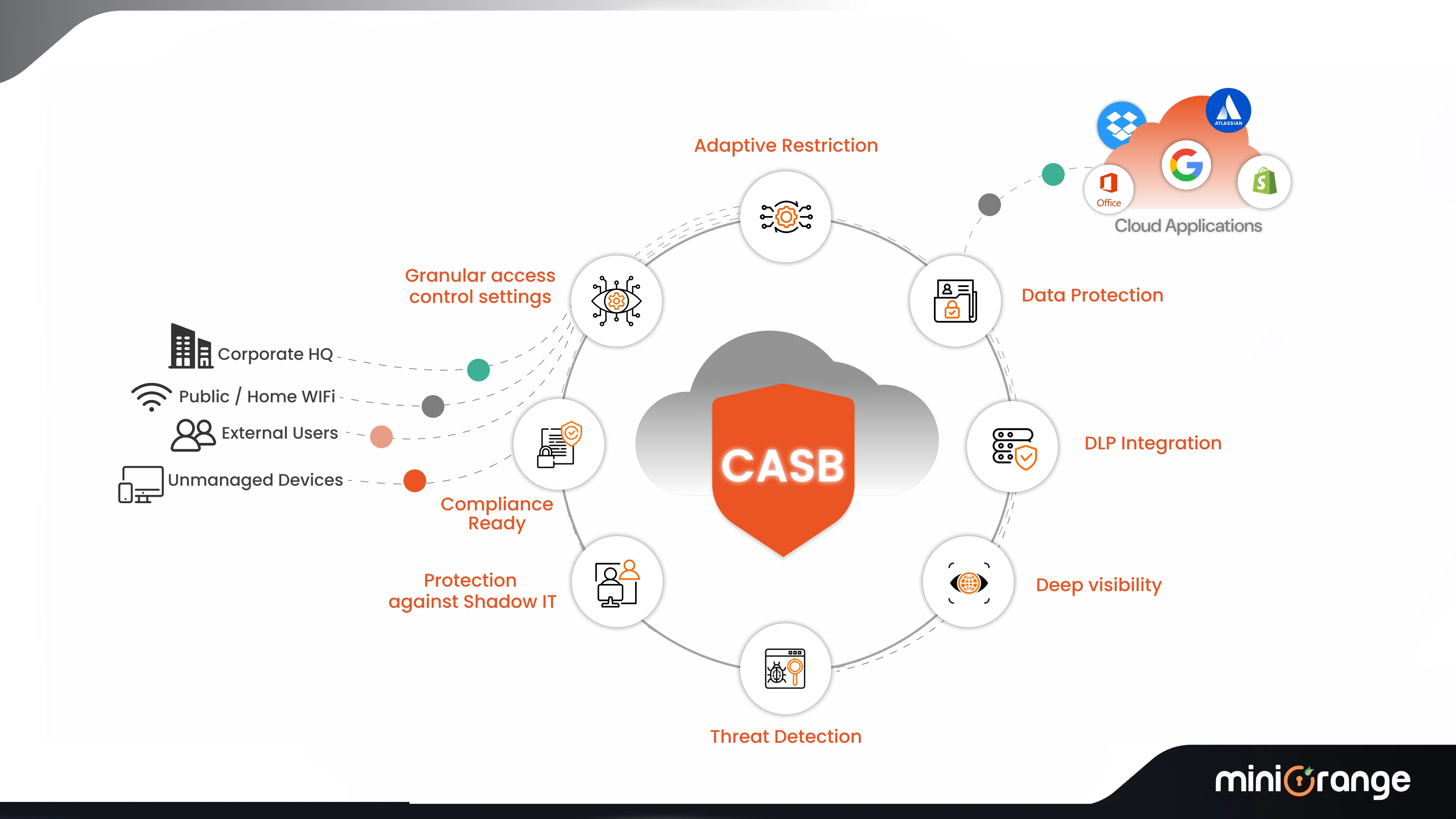
Key Features of CASB Solution
- Cloud Visibility & Shadow IT Detection: See which apps employees use (even unauthorized ones). Identify risky or non-compliant apps instantly.
- Access Control: Define who can access which apps, from which devices, and under what conditions. For example, block access from unmanaged devices.
- Data Loss Prevention (DLP): Prevent sensitive data (like customer PII or financial reports) from leaving your network. Our DLP solution inspects uploads, downloads, and sharing in real time.
- Threat Protection: Detect abnormal login attempts, risky user behavior, or suspicious locations. Stop account takeovers before damage is done.
- Compliance Support: Meet data security requirements for regulations like GDPR, PCI-DSS, HIPAA, and more.
- Granular Policy Enforcement: Apply rules such as “Finance team can’t upload data to personal cloud apps” or “Block downloads of confidential files to personal devices.”
Example: If an employee tries to download confidential sales reports from Salesforce onto a personal device, CASB can block it in real time.
SSPM vs CASB – Key Differences
| Aspect | SSPM | CASB |
|---|---|---|
| Focus | Secures SaaS configurations | Secures access and data usage |
| Where it works | Inside SaaS apps (settings, permissions, compliance) | Between users and apps (access control, monitoring) |
| Best for | Organizations needing stronger SaaS governance | Organizations needing access control and real-time protection |
| Example | SSPM detects a weak MFA setup in Microsoft 365 | CASB blocks login from an unmanaged device in another country |
| Prevents | Misconfigurations, compliance gaps | Shadow IT, data leaks, account takeovers |
| Key Features | Configuration monitoring, remediation, compliance, risk scoring | Access control, DLP, shadow IT detection, policy enforcement |
In short: the difference between SSPM and CASB is that:
- SSPM keeps SaaS apps secure from the inside. It focuses on configurations, permissions, and compliance.
- CASB guards access and usage from the outside. It monitors logins, data sharing, and user behavior in real time.
When to Choose CASB vs. SSPM
Choose SSPM if:
- You use SaaS apps heavily and want to prevent misconfigurations.
- Compliance is critical (finance, healthcare, education, government).
- You want proactive, posture-based security.
Choose CASB if:
- You want visibility into shadow IT and app usage.
- You need real-time control over data transfers and logins.
- You must enforce DLP and prevent unauthorized access.
In reality, most organizations need both, because SSPM and CASB solve different but complementary problems.
SSPM and CASB Use Cases
Both SSPM and CASB tackle different angles of cloud security. Here are some real-life situations that show how they work in practice:
1) SSPM Example Your HR team integrates a third-party payroll app with your HR management system. The app has an open API connection that accidentally exposes sensitive employee salary data. SSPM immediately scans the configuration, detects the risk, and provides remediation steps before attackers can exploit it. This prevents costly compliance violations and protects employee trust.
2) CASB Example: A design contractor working remotely tries to upload confidential product blueprints into a personal Dropbox account. CASB spots this action in real time, blocks the transfer, and alerts the IT team instantly. This prevents intellectual property theft and ensures sensitive designs never leave approved systems.
Together: When SSPM and CASB are combined, they create a layered defense strategy. SSPM ensures apps are configured securely from the inside, while CASB enforces security policies on user behavior from the outside. This one-two punch significantly reduces risks like data leaks, shadow IT, and compliance gaps.
Final word
Cloud apps are the backbone of modern work. From collaboration to sales, they fuel productivity, but they also introduce hidden risks if left unsecured.
- SSPM protects you from misconfigurations, risky integrations, and compliance gaps.
- CASB protects you from unauthorized access, shadow IT, and real-time data leaks.
On their own, each tool is powerful. But together, they provide end-to-end SaaS protection, inside and out. Think of it as locking both the front door (CASB) and the windows (SSPM) of your house.
Ready to see which solution fits your needs? Book a start your free trial today.
Frequently Asked Questions: SSPM vs CASB
1) What is the main difference between SSPM and CASB?
SSPM focuses on preventing misconfigurations inside SaaS apps (like weak settings, overly broad permissions, or risky integrations). CASB focuses on securing access and monitoring how apps are used (like blocking unauthorized logins or data sharing).
2) Do I need both SSPM and CASB?
In most cases, yes. SSPM is your proactive defense, fixing weaknesses before they’re exploited. CASB is your reactive guard, monitoring activity in real time and stopping unsafe actions. Together, they cover both configuration risk and user behavior risk.
3) Which is better: SSPM or CASB?
It’s not about one being better, it’s about what problem you need to solve.
- If compliance and SaaS misconfigurations are your biggest worry → SSPM is essential.
- If shadow IT, data leaks, and access control are your priority → CASB is the answer. For most modern businesses, combining both gives the most complete cloud security.





Leave a Comment