While you read this, thousands of digital entities silently authenticate and access your infrastructure without human intervention. These Non-human identities (NHIs) outnumber human users by a ratio of 45:1 in cloud environments, creating massive blind spots. These digital workers never take breaks but can cause devastating breaches when compromised, especially as agentic AI agents become targets for various types of cybersecurity attacks, including prompt injection, credential theft, and privilege escalation.
What Are Non-Human Identities?
Non-human identities are digital identities assigned to software, services, workloads, and devices that interact with systems without a human present, using credentials such as API keys, tokens, certificates, and service accounts to authenticate and authorize actions programmatically.
Core Characteristics
- Operate autonomously through scripts, services, and workloads that run continuously or on schedules without interactive logins, often authenticating thousands of times per minute in patterns unlike human users.
- Use programmatic access methods such as service accounts, API tokens, client certificates, workload identities, and device/machine credentials to perform system-to-system communication.
- Commonly have static, long-lived secrets and elevated permissions, creating risk when not rotated, scoped, or monitored according to least privilege.
Why They Matter
- Attackers increasingly target machine-to-machine pathways, exploiting unmanaged service accounts, embedded API keys, and over-privileged workloads to gain persistent, lateral access that evades human-centric controls like MFA and EDR.
- Poor lifecycle management causes secrets sprawl, excessive permissions, and blind spots in monitoring, significantly expanding the attack surface across cloud and hybrid environments.
Relationship to Zero Trust
- Zero Trust’s “never trust, always verify” and least privilege principles apply equally to NHIs, requiring explicit, context-aware authorization for every machine request rather than implicit trust based on network location or legacy perimeters.
- Extending Zero Trust and MFA software to NHIs entails continuous verification, granular authorization, and real-time policy enforcement for non-human workloads, not just human users, closing gaps where machine credentials bypass MFA and behavioral analytics.
Learn how IAM strengthens control over human and non-human identities.
Non-Human Identities vs Human Identities
| Aspect | Human identities | Non-human identities |
|---|---|---|
| Authentication methods | Authenticate with usernames, passwords, MFA, and sometimes biometrics; interactive challenges are expected and enforced. | Authenticate with API tokens, client secrets, certificates, workload identities, and service accounts. |
| Access patterns | Primarily UI/console access, session-based, irregular, and context-rich actions across apps during working hours. | Programmatic, system-to-system calls via APIs/SDKs, & high-frequency. |
| Credential management | Centrally governed via IAM/HR processes; periodic password resets and MFA policy enforcement are standard. | Often decentralized in DevOps/app teams, secrets can be long-lived or embedded. |
| Monitoring complexity | User activity is visible in standard logs; UEBA and SIEM detect anomalies based on behavior baselines and policy. | High-volume, machine noise makes anomalies harder to spot. |
| Permission lifecycle | Roles and entitlements are reviewed during joiner-mover-leaver cycles; stale accounts are typically pruned. | Created ad hoc by pipelines or scripts; can persist after use, becoming orphaned or “zombie” identities. |
| Ownership/governance | Clear owner (employee/contractor) with defined accountability and access reviews. | Ownership is often ambiguous across teams or services. |
| Least privilege | RBAC/ABAC applied to job functions with periodic access reviews and approvals. | Often over-permissioned for convenience; requires granular scoping. |
| Threat profile | Phishing, credential stuffing, and session hijacking; mitigated by MFA and risk-based authentication. | Secret leakage, token theft, supply-chain abuse, over-privileged service accounts. |
| Lifecycle automation | On/offboarding integrated with HR-driven workflows and certification campaigns. | Needs CI/CD integration for issuance, rotation, and revocation; event-driven deprovisioning to prevent drift and sprawl. |
| Compliance/audit | Mapped to individuals for audits and attestations; straightforward accountability. | Mapping to services/workloads is harder; it requires inventory, ownership tags, and traceability for audit evidence. |
Common Examples of Non-Human Identities
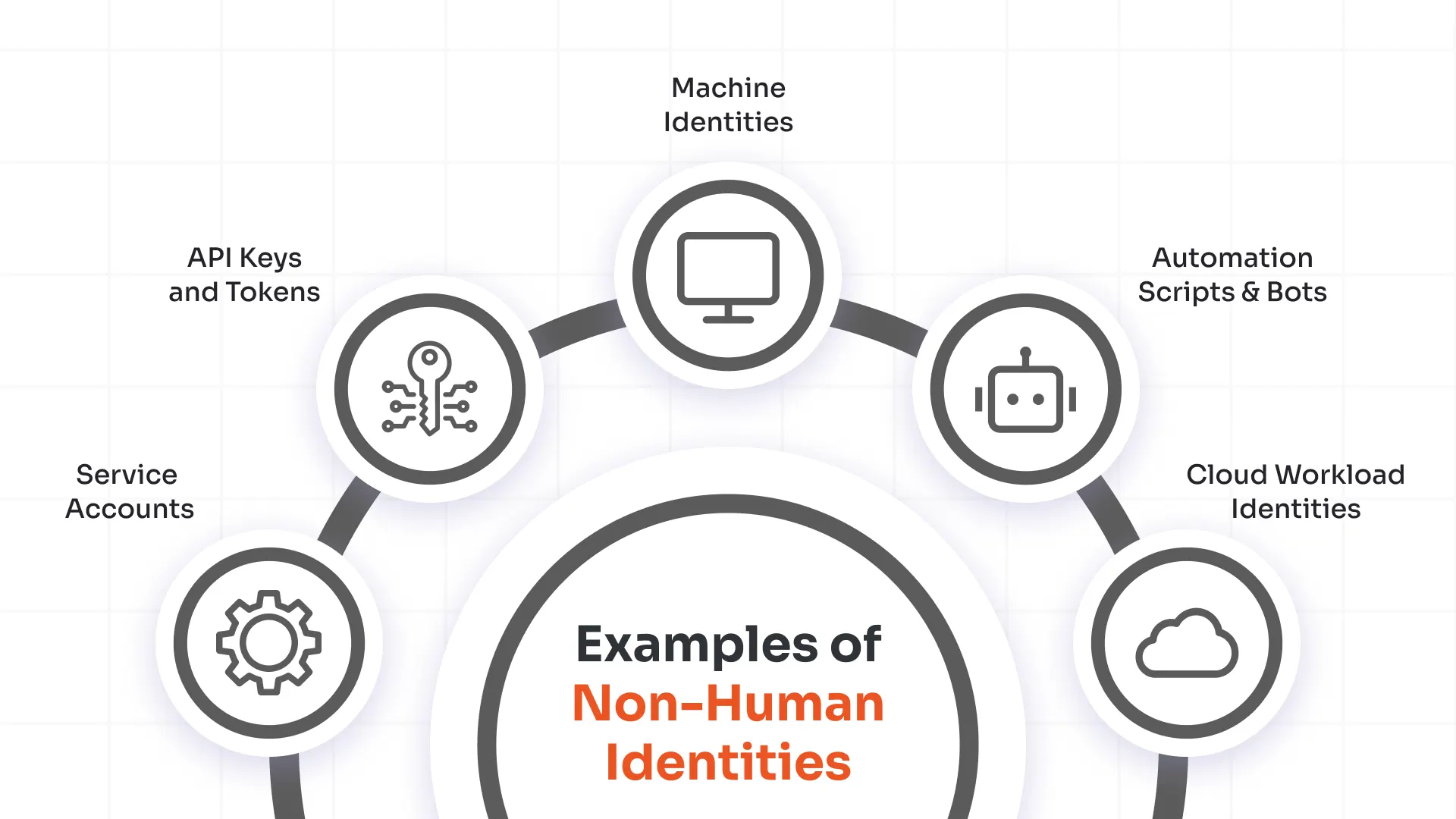
Service Accounts
Service accounts are dedicated identities for applications and services to access resources like databases, queues, and cloud APIs without human interaction. They power app-to-app integrations and background jobs, often with elevated permissions. Risk concentrates in over-permissioning, weak or static credentials, and orphaned accounts left after decommissioning, enabling stealthy lateral movement and persistent access if compromised.
API Keys and Tokens
API keys and OAuth/JWT tokens enable third-party integrations, microservices communication, and SaaS connections programmatically. They authenticate requests at scale without user prompts. Vulnerabilities arise from hardcoded credentials in code and images, insecure storage in repos or CI logs, excessive scopes, and long lifetimes without rotation, making leakage or interception highly exploitable across multiple services.
Machine Identities
Machine identities represent devices, workloads, and services through certificates and cryptographic keys, enabling mutual TLS and device-to-device trust. They secure IoT fleets and infrastructure components through certificate-based authentication. Challenges include PKI at scale, is issuance, renewal, revocation, and inventory across heterogeneous platforms, plus preventing key sprawl and ensuring policies enforce least privilege and short-lived, auditable credentials.
Automation Scripts and Bots
Automation identities authenticate CI/CD pipelines, deployment tools, monitoring agents, and schedulers to perform builds, releases, configuration, and alerting. These run non-interactively and need scoped, time-bound access. Risks stem from secrets stored in pipelines, logs, or runners, broad permissions for convenience, and missing deprovisioning, which can allow tampering with build artifacts, environment variables, or production systems.
Cloud Workload Identities
Cloud workload identities map containers, Kubernetes service accounts, and serverless roles to fine-grained permissions for services and data. They enable auto-scaling operations and dynamic provisioning without embedding secrets, ideally using short-lived credentials. Misconfigurations such as overly broad IAM roles, permissive service accounts, or weak trust boundaries can expose sensitive resources, escalate privileges, and amplify the blast radius in ephemeral environments.
Security Risks and Challenges
Over-privileged Access
Non-human identities frequently receive excessive permissions during initial provisioning for convenience, violating the principle of least privilege. Service accounts and API keys often retain broad database, admin, or cloud-wide access beyond their actual requirements. This over-permissioning creates attractive targets for attackers, enabling lateral movement and privilege escalation once compromised, amplifying breach impact significantly.
Poor Visibility
Shadow NHIs proliferate across cloud environments without centralized inventory or documentation, making comprehensive discovery challenging. Ownership attribution is frequently unclear across DevOps teams, leading to forgotten credentials and "zombie" accounts persisting after project completion. Organizations struggle to classify and track these identities consistently, creating blind spots where unauthorized access can go undetected for extended periods.
Credential Exposure
Secrets are commonly hardcoded in source code repositories, stored in plaintext configuration files, or embedded in container images accessible to unauthorized users. Insecure storage practices include secrets in CI/CD logs, environment variables, and shared development environments. These exposed credentials can be discovered through code scanning, leaked repositories, or insider threats, providing direct access pathways without sophisticated attack methods.
Lack of Governance
NHI creation often occurs ad hoc without standardized processes, leading to inconsistent security controls and missing lifecycle management. Organizations frequently lack formal expiration policies, automated rotation schedules, and regular access reviews for machine identities. This governance gap creates compliance violations, audit challenges, and the accumulation of stale privileges that persist indefinitely without oversight or accountability.
Expanded Attack Surface
Non-human identities operate silently in the background without user interaction, making malicious activity harder to detect through traditional behavioral monitoring. Compromised NHIs enable prolonged undetected access since they lack the anomalous patterns that trigger alerts for human accounts. They facilitate lateral movement through system-to-system connections and can establish persistent backdoors, allowing attackers to maintain stealth access.
Real-World Attack Examples
BeyondTrust API Key Compromise
In December 2024, attackers exploited a zero-day vulnerability to steal a BeyondTrust infrastructure API key, which was then used to reset passwords for 17 customer instances. The attack was later linked to Chinese APT groups targeting U.S. Treasury systems through the same vulnerability. BeyondTrust revoked the API key, quarantined affected instances, provided replacement services, and engaged federal law enforcement and forensic teams highlighting the growing need for stronger identity controls and phishing-resistant MFA in high-risk environments.
Microsoft AI Researchers SAS Token Exposure
Microsoft AI researchers accidentally exposed a Shared Access Signature (SAS) token in a public GitHub repository, granting access to 38 terabytes of sensitive internal data for nearly three years. The overpermissive token provided full access to employee workstation backups and internal Teams messages. Microsoft implemented additional SAS token scanning tools and revised secure-by-default policies following the discovery by security researchers at Wiz.
Okta Service Account Breach (2023)
Attackers compromised credentials stored in an Okta employee's personal Google account, gaining access to the customer support system and extracting HAR files containing session tokens for 134 customers. The stolen credentials enabled unauthorized session hijacking and MFA bypass attempts. Okta faced significant reputational damage, regulatory scrutiny, customer churn, and invested heavily in incident response and security infrastructure overhauls.
Best Practices for NHI Security
Implementation Strategies
Organizations must adopt a comprehensive approach to secure non-human identities by implementing zero-trust architecture, automated credential rotation, just-in-time access controls, and regular permission audits.
Zero trust principles require treating every NHI as untrusted by default, verifying all access requests through cryptographic attestation and workload identity frameworks like SPIFFE/SPIRE. Regular audits using AI-driven tools continuously analyze permissions against usage patterns to identify over-privileged accounts and suggest right-sized access controls.
Monitoring and Detection
Effective NHI security requires establishing baseline behavior patterns and deploying machine learning algorithms to detect anomalies such as unusual data transfers, unexpected geographic access, or privilege escalation attempts. Organizations must implement continuous monitoring that correlates NHI activities across all systems, integrating with SIEM platforms to provide contextual alerts and enable rapid incident response.
Governance Framework
Comprehensive NHI governance establishes standardized lifecycle management covering creation, provisioning, monitoring, rotation, and decommissioning phases with clear approval workflows and ownership assignment. Every non-human identity must have a designated human owner accountable for security posture and lifecycle management, documented in configuration management databases with automated notifications for security events.
Technology Solutions and Tools
Modern NHI management requires identity governance platforms for centralized visibility and control, privileged access management solutions designed for machine identities with session recording and JIT access, and dedicated secret management platforms like HashiCorp Vault or cloud-native services for encrypted credential storage and automated rotation.
Conclusion
As non-human identities now outnumber human identities by 25-50x in modern enterprises and represent one of the fastest-growing attack surfaces, organizations must fundamentally shift toward machine-centric identity management integrated within comprehensive zero-trust architectures.
Security teams should immediately begin comprehensive NHI discovery, implement centralized secret management, establish ownership accountability, and prepare for AI-driven systems that will require even more sophisticated behavioral analytics and real-time policy enforcement. The future demands dynamic, context-aware identity systems that adapt to rapidly changing workload requirements while maintaining strict security controls, making NHI security not just a technical imperative but a business-critical foundation for digital transformation.
FAQs
What is an example of a non-human identity?
A non-human identity is a digital credential used by machines or applications, such as API keys, service accounts, automation scripts, or certificates that access systems and perform tasks without direct human involvement.
What impacts do non-human identities have on cybersecurity?
Non-human identities can introduce security risks like unauthorized access, privilege misuse, and data exposure. Their scale and lack of visibility make them difficult to manage, requiring strong controls to maintain cybersecurity.
Do organizations need non-human identity security policies?
Organizations need policies to manage non-human identities effectively. These should cover lifecycle management, access controls, and monitoring to reduce risk, ensure compliance, and maintain secure operations across systems and environments.




Leave a Comment