Need Help? We are right here!
Search Results:
×






miniOrange’s Phishing-Resistant MFA eliminates weak security factors, protecting your organization from sophisticated phishing attacks. In support of the White House in Executive Order M-22-09, which mandates phishing-resistant MFA for all U.S. federal agencies, miniOrange helps government and private sector organizations implement compliant phishing prevention solutions.
We ensure secure, device-bound authentication that drastically reduces credential theft risks by leveraging Passwordless authentication such as FIDO2 and biometrics. Our frictionless access experience boosts productivity while safeguarding sensitive systems and meeting evolving cybersecurity standards.
miniOrange uses advanced technologies like FIDO2, WebAuthn, hardware security keys, and biometrics to enable secure, passwordless authentication. Credentials are never shared or transmitted, eliminating the vulnerabilities of traditional MFA methods, which are prone to phishing, interception, and social engineering.
Authentication factors are tightly linked to users' individual devices. Even if an attacker tries to deceive users with phishing kits or fake websites, access is denied without possession of the registered device.
miniOrange’s phishing-resistant MFA solution avoids static passwords and one-time codes, which are commonly exploited in replay and man-in-the-middle attacks. This architecture ensures that sensitive credentials cannot be intercepted or reused.
We enhance security with adaptive authentication that evaluates user behavior, device trust, and risk signals before access is granted. Suspicious login attempts are proactively blocked based on real-time risk-based controls.
Secures financial systems with strong, unphishable authentication methods that prevent credential theft and support regulatory compliance.
Protects patient data by enforcing secure, identity-verified access aligned with HIPAA standards and resistant to phishing attacks.
Enables strict identity verification across sensitive networks using authentication that eliminates reliance on passwords and resists impersonation.
Ensures safe access to cloud platforms and remote environments with modern login methods that block phishing and unauthorized entry.
MFA methods offered by miniOrange provide robust security by requiring users to verify their identity through multiple layers beyond just a password.
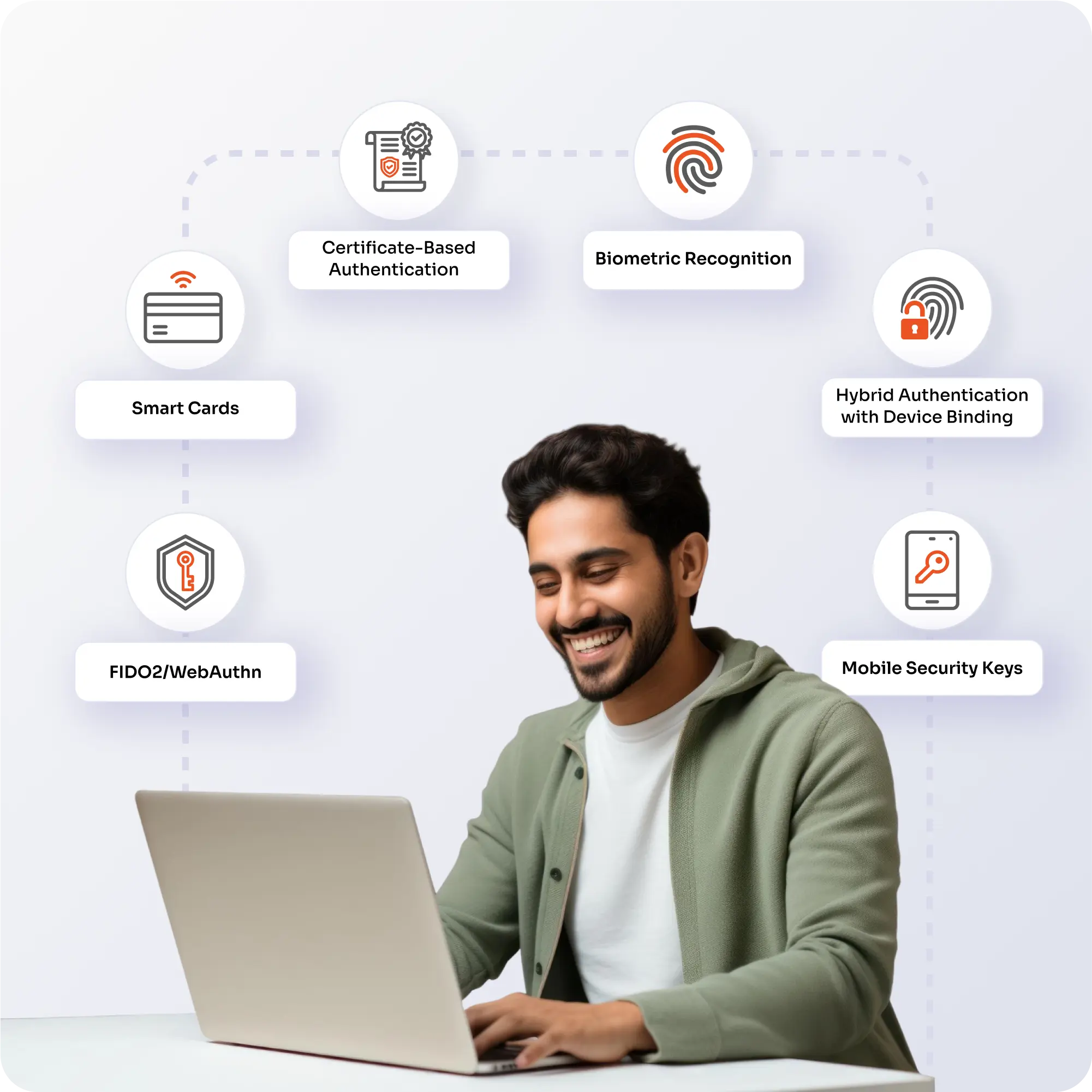
Modern, passwordless authentication using public key cryptography.
Government-grade credentials stored on secure physical cards.
Identity verified through digital certificates issued by trusted authorities.
Uses unique physical traits for secure and user-friendly login.
Combines multiple factors tied to a trusted device for enhanced security.
Portable hardware tokens enabling phishing-resistant login on mobile and desktop.
miniOrange's phishing-resistant MFA solution makes phishing attacks mathematically impossible, not just harder to execute.
Phishing-resistant MFA product from miniOrange supports desktops, laptops, and mobile devices using built-in authenticators or hardware tokens, with biometrics like Face ID and fingerprint for secure access.
Secure VPNs, virtual desktops, and thin clients with MFA that integrates seamlessly into remote setups, eliminating password reliance even in low-resource environments.
FIDO-certified tokens like YubiKey and SoloKeys offer USB, NFC, or Bluetooth-based authentication, while mobile biometrics verify identity securely without sharing credentials.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
Deploy our IAM solution within your existing infrastructure seamlessly, integrating with legacy systems through standard protocols.
Secure identity management across AWS, Azure, Google Cloud, and specialized clouds, offering flexibility with robust security and compliance.
Achieve unified IAM security across your entire ecosystem, bridging legacy systems and modern clouds for a phased modernization.
miniOrange is a leading cybersecurity company specializing in phishing-resistant MFA solutions that help organizations secure their digital assets and user identities.
Provides real-time defense against phishing, brute force, DoS, and malware attacks using automated threat detection and response across enterprise systems.
Uses device fingerprinting and user behavior analytics to identify anomalies and proactively block phishing attempts before data is exposed.
Ensures seamless compatibility with 6000+ integrations, including cloud platforms, web applications, and legacy systems, to maintain consistent security.
Implements multi-factor authentication, IP restrictions, and login attempt limits to prevent unauthorized access and credential compromise.
Supports both cloud-based and on-premises deployment models with centralized management for scalable and flexible infrastructure protection.
Allows tailored security policies, role-based access, and alert configurations to meet specific organizational requirements and compliance standards.
Phishing-resistant MFA uses public-key cryptography to eliminate shared secrets like passwords or OTPs, making it immune to phishing and man-in-the-middle attacks. Private keys remain securely on user devices and are never transmitted. This method is vital because over 80% of data breaches stem from stolen credentials, and traditional MFA still leaves gaps in protection.
It prevents phishing by binding the user’s identity to a device through cryptographic challenges that only legitimate servers can verify. Since the private key never leaves the device, attackers can't intercept or reuse authentication data, nor can they trick users with fake login pages.
TTop phishing-resistant MFA methods include FIDO2/WebAuthn, hardware security keys like YubiKey, biometric passkeys, and certificate-based authentication. These approaches eliminate reliance on passwords and can be enhanced with adaptive authentication based on user behavior and device risk.
Absolutely. It aligns with NIST and Zero Trust frameworks and supports compliance with HIPAA, GDPR, SOC 2, and more. By removing the main attack vector for credential theft, it reduces breach risk, saves on incident response costs, and strengthens secure access for remote workforces.