Most organizations rely on Active Directory to manage user identities, control access to critical systems, and enforce security policies. But what happens when a user is added to a privileged group without approval, or when someone attempts to access sensitive data outside of office hours?
Nearly one-third of ransomware attacks were launched within just 48 hours of the attacker gaining initial access. Additionally, as per Mandiant research, 76% of these deployments occurred outside regular working hours, most often in the early morning.
In many cases, these actions go unnoticed—not because they’re harmless, but because no one’s watching.
Active Directory auditing helps close that visibility gap. It gives IT teams a way to monitor and track changes in the environment, from user logins and permission modifications to group policy updates and object deletions. And in today’s threat landscape, that kind of oversight isn’t optional.
This blog walks you through the key areas to audit in AD, how to set up auditing correctly, and best practices to help you strengthen both your security posture and compliance efforts.
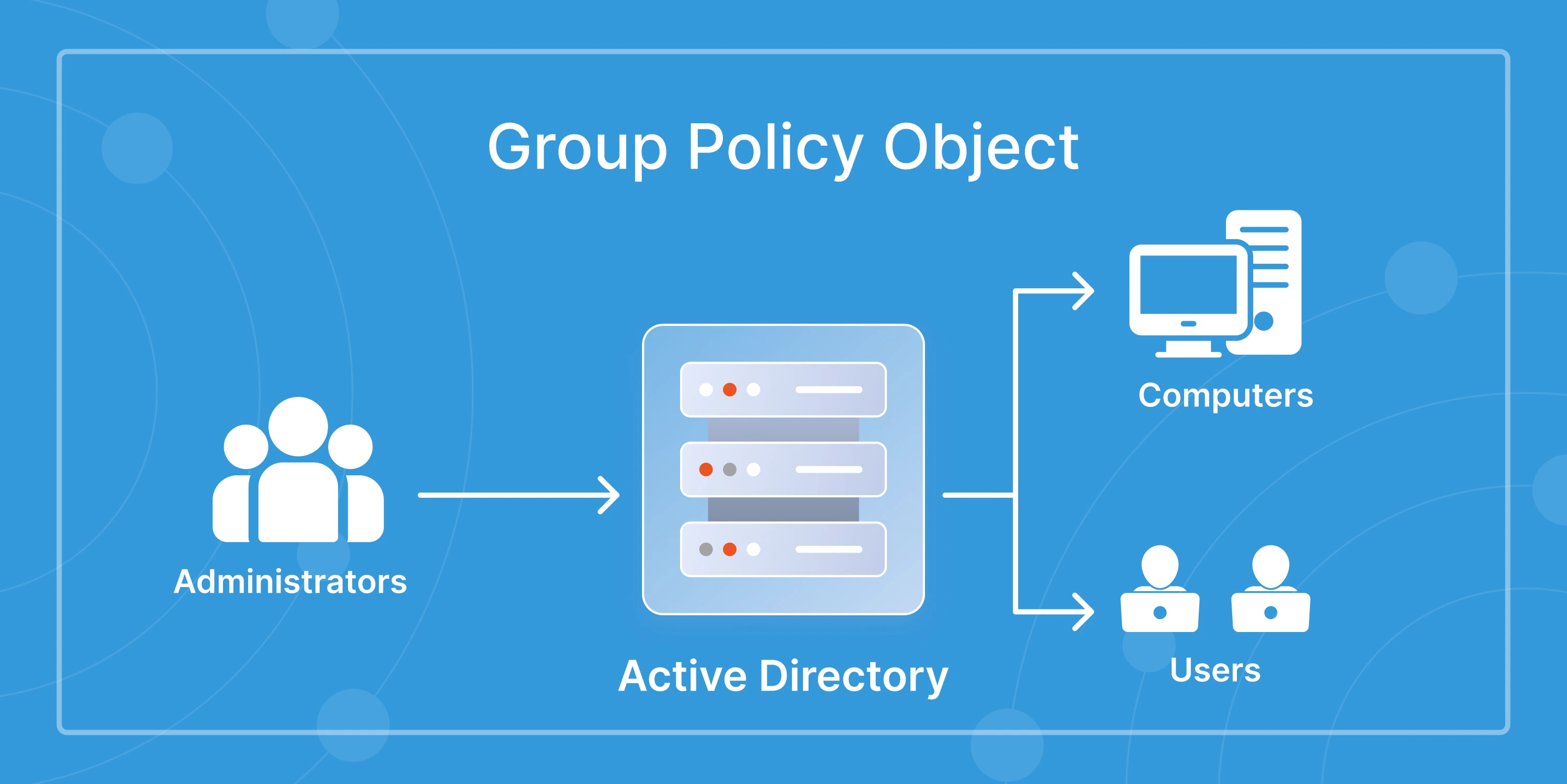
What is Active Directory (AD) Auditing?
Active Directory auditing is the process of monitoring and recording events and changes within an AD environment. This includes activities like user logins, group membership changes, permission modifications, and the creation or deletion of objects such as users, computers, and organizational units.
The primary goal is visibility—knowing who did what, when, and where. This information is critical for detecting suspicious behavior, investigating incidents, and ensuring that changes align with internal policies or external compliance requirements.
Unlike simple logging, AD auditing involves configuring policies to capture relevant security events and storing them in a centralized location, usually the Windows Event Log under the Security category. These logs can then be reviewed manually or fed into SIEM solutions for automated threat detection.
For example, if a user is suddenly added to the "Domain Admins" group at midnight, a properly configured audit policy would flag this high-risk change for immediate review.
Windows Server supports two types of auditing:
- Basic Auditing: Tracks limited actions such as successful or failed logon attempts.
- Advanced (Directory Services) Auditing: Provides fine-grained tracking, such as which attribute of a user object was changed, and by whom.
Whether you're trying to meet regulatory requirements (like SOX, HIPAA, or GDPR) or just maintain tighter control over your environment, AD auditing is a foundational layer of enterprise security.
Essential Areas to Audit in Active Directory
Once auditing is enabled, the next step is deciding what to monitor. Tracking every possible change can overwhelm your logs and obscure real threats. Instead, focus on high-impact areas that directly affect security, access, and compliance.
Here are the key areas every AD audit checklist should include:
1. User Account Activities:
- Creation, deletion, or disabling of user accounts
- Password resets or changes
- Lockouts or failed login attempts
Why it matters: These events help detect brute-force attacks, insider threats, and unauthorized account provisioning.
2. Group Membership Changes:
- Users added to or removed from:
- Privileged groups (Domain Admins, Enterprise Admins)
- Application-specific groups (e.g., SharePoint, SQL Server)
Why it matters: Group memberships control access. A single unauthorized change could grant admin-level access to a malicious user.
3. Permission & Access Control Changes:
- Modifications to ACLs on OUs, shared folders, or user objects
- Delegation of control or changes to inheritance
Why it matters: These actions often precede privilege escalation attempts or misconfigurations that open doors to attackers.
4. Group Policy Object (GPO) Changes:
- Creation, modification, or deletion of GPOs
- Changes in GPO links or enforcement settings
Why it matters: A single GPO can change security settings across the domain. Tracking GPO edits is essential for policy integrity.
5. Organizational Unit (OU) Modifications:
- Moving, deleting, or renaming OUs
- Changing the delegation on an OU
Why it matters: OUs structure your AD. Changes can impact how policies apply and who manages what.
6. Logon and Logoff Events:
- Successful and failed logon attempts
- Remote logins or after-hours access
- Interactive vs. service logins
Why it matters: Anomalous logon patterns often reveal compromised credentials or lateral movement.
7. Schema and Configuration Changes:
- Schema updates (rare but high-risk)
- Forest or domain trust changes
- FSMO role transfers
Why it matters: These changes affect the entire AD structure. They should be tightly monitored and rarely occur.
Active Directory Audit Checklist (Quick Reference)
| Area | What to Monitor |
|---|---|
| User Accounts | Creation, deletion, password changes, lockouts |
| Group Membership | Privileged group modifications |
| Permissions/ACLs | Changes to access control or delegation |
| GPOs | New, modified, or deleted GPOs |
| OUs | Movement or delegation changes |
| Logon Events | Failed logins, after-hours access |
| Schema/Config | Domain trust changes, FSMO transfers |
Benefits of Active Directory Auditing
Active Directory auditing isn’t just about collecting logs—it’s about turning those logs into actionable security intelligence. When configured and monitored correctly, AD auditing provides measurable benefits across security, compliance, and operational efficiency.
1. Detect Unauthorized Access and Misuse:
AD auditing helps identify when users attempt to access resources they shouldn’t, log in during unusual hours, or modify critical objects without approval.
Example: A user being added to the “Domain Admins” group outside business hours can be flagged immediately for review, preventing a potential privilege escalation attack.
2. Strengthen Compliance Readiness:
Most regulatory frameworks—including HIPAA, SOX, GDPR, and ISO 27001—require evidence of access control and change tracking. AD auditing provides a detailed, time-stamped log of who did what, which satisfies these requirements during security assessments or audits.
3. Accelerate Incident Response and Forensics:
When a security incident occurs, time is critical. AD audit logs help incident response teams quickly trace the source of changes—whether it’s a disabled account, a rogue GPO update, or an unauthorized login attempt.
With complete logs, security teams can answer:
- What was accessed?
- When did the breach begin?
- Who made the change, and from which IP?
4. Enable Proactive Monitoring and Alerting:
Many organizations integrate AD audit logs into a Security Information and Event Management (SIEM) platform to detect suspicious behavior in real time.
For example:
- Multiple failed login attempts across several accounts
- A spike in permission changes in a short time window
- Logons from unfamiliar geolocations
Such patterns often precede a breach. With the right alerting rules, AD auditing can help stop an attack before damage is done.
5. Generate Audit-Ready Reports:
Auditing tools can generate clean, structured reports that simplify internal reviews or external compliance audits. These reports can show trends in account activity, group membership changes, and administrative behavior over time.
Some third-party tools even allow exporting reports tailored to specific standards (e.g., SOX, NIST, GDPR), cutting down manual effort during audits.
Developer Tip: Pairing native auditing with third-party tools like miniOrange AD Auditing or Change Auditor can provide enriched reporting, real-time alerting, and easier log correlation across domains.
Active Directory Auditing Best Practices
Enabling AD auditing is only the first step. Without a structured approach, organizations can end up with overwhelming logs, missed alerts, or worse, critical events going unnoticed. These best practices help ensure your auditing strategy is both effective and manageable.
1. Start with High-Impact Audit Categories:
Focus on auditing actions that carry the greatest security risk:
- User account creation, deletion, and lockouts
- Changes to privileged groups (like Domain Admins)
- Modifications to Group Policy Objects (GPOs)
- Directory Service Changes (object edits, permission changes)
Audit selectively at first—monitoring everything can flood your logs and increase storage costs without adding real value.
2. Enable Directory Services Advanced Auditing:
Advanced auditing in Windows Server provides granular control over what events are captured. You can track specific actions like which attribute of a user account was modified and by whom, rather than logging every single directory access.
This helps reduce noise and makes your logs far more actionable.
3. Centralize Logs Across Domain Controllers:
By default, audit logs reside on individual domain controllers. Centralizing them using a SIEM or Windows Event Forwarding (WEF) improves visibility, simplifies correlation, and ensures no critical log is missed.
Developer Tip: Centralization also allows for easier long-term storage and backup, important for both compliance and incident response.
4. Set Up Real-Time Alerts for Critical Events:
Pair auditing with real-time alerting rules. For example:
- Alert when a user is added to an administrative group
- Alert on multiple failed logon attempts
- Alert when GPOs are modified
These notifications can help your security team respond before a threat spreads laterally through your network.
5. Regularly Review and Tune Your Audit Policy:
Auditing isn’t “set it and forget it.” Schedule periodic reviews of:
- What you’re auditing
- Where logs are going
- Who has access to them?
- Whether alerts are triggering appropriately
Adjust as your environment or compliance requirements evolve.
6. Protect Your Audit Logs:
Ensure that the audit logs themselves are tamper-proof. Limit who can access or clear logs and regularly back them up. In some attacks, clearing the Security Event Log is one of the attacker’s first actions.
7. Test Your Audit Configurations:
After enabling policies, simulate critical events (e.g., add a user to a group or change a GPO) and confirm that logs are being captured correctly. This validation step is often skipped, and it’s where many audit setups fail.
By following these best practices, you’ll ensure that your AD auditing is both efficient and effective, giving you the oversight needed to detect threats early and meet audit requirements with confidence.
Industry-Specific AD Auditing Considerations
While the fundamentals of Active Directory auditing are the same across organizations, specific industries often have unique compliance obligations and risk profiles. Your Active Directory audit policy should be aligned not only with internal security standards but also with the regulatory landscape your business operates in.
Below are key considerations by industry:
1. Healthcare (HIPAA Compliance)
What to audit:
- Access to systems handling Electronic Protected Health Information (ePHI)
- Logon/logoff activity of clinical staff
- Privileged account use (e.g., IT admins accessing patient data)
Best practice:
Use Directory Services Advanced Auditing to monitor attribute-level changes to patient records and ensure proper access segregation between departments.
HIPAA requires detailed audit trails and access logs to demonstrate that only authorized users accessed health records.
2. Finance (SOX, GLBA, PCI-DSS Compliance) What to audit:
- Account creation and privilege escalation
- GPO and password policy changes
- Access to systems processing financial transactions
Best practice:
Generate Active Directory audit reports that track permission changes and login patterns. These are often required during internal and external SOX audits.
PCI-DSS 10.2 specifically mandates logging of all access to system components, including audit trail history and log review procedures.
3. Government & Public Sector (CJIS, FISMA) What to audit:
- Any changes to user or device access
- Logins outside approved hours or locations
- Group policy and schema modifications
Best practice:
Implement geo-location-based auditing rules and maintain immutable logs. Use a centralized Active Directory management tool that supports role-based access and chain-of-custody tracking for log integrity.
Agencies must prove accountability and traceability of every administrative action to comply with CJIS or FISMA frameworks.
4. Enterprises with Global Presence (GDPR) What to audit:
- Data access logs
- Changes to user roles and security groups
- Remote and after-hours access
Best practice:
Map audit data to GDPR Article 30 (Records of Processing Activities) and ensure personal data access is logged and reviewed.
GDPR penalties for non-compliance can reach up to €20 million or 4% of annual revenue, making audit policies critical for risk management.
Choosing the Right Tools for Industry-Grade AD Auditing
Native auditing in Windows Server is powerful but can be limited in terms of reporting, real-time alerting, and cross-domain visibility.
To address these gaps, many organizations use third-party Active Directory auditing and reporting tools that offer:
- Pre-built compliance report templates (e.g., for SOX, HIPAA, GDPR)
- Real-time alerts and dashboards
- Secure log storage and retention policies Integration with SIEMs for centralized incident response
If your organization is subject to multiple compliance regimes, a purpose-built AD management platform like miniOrange AD Audit Tools can simplify policy enforcement, reporting, and investigation workflows.
Conclusion
Active Directory auditing is no longer a “nice to have”—it’s a core security and compliance requirement for any organization that relies on AD to manage user identities and access. From tracking privilege changes to detecting insider threats and meeting audit obligations, the benefits are clear: visibility, accountability, and faster incident response.
But visibility without structure can lead to noise. That’s why it’s essential to go beyond just enabling audit logs. You need a strategy—one that includes targeted auditing, centralized log collection, real-time alerts, and audit-ready reports.
Whether you're operating in a highly regulated industry or simply want to reduce your attack surface, the right Active Directory audit policy makes all the difference.
Simplify Your AD Auditing with miniOrange
If you’re looking for a scalable, compliance-ready solution, miniOrange AD Auditing offers:
- Pre-configured audit templates for SOX, HIPAA, and GDPR
- Real-time alerts on critical changes (like group membership updates)
- Visual dashboards and exportable audit reports
- Seamless integration with existing SIEM tools
From IT administrators to compliance officers, our tool helps teams gain control over AD activity without having to sift through endless logs.



Leave a Comment