Key Takeaways from Cloud Security Best Practices
- Biggest challenges: Cyber fraud, human error, compliance complexities, misconfigurations, and insecure third-party integrations.
- Measures: Real-time detection, automated incident response, strong access management, and regular audits are some of the essential measures.
- Solutions: Using single security platforms like miniOrange CASB helps simplify visibility, management, and defense across your cloud setups.
Cloud Infrastructure Security Best Practices in 2025
Businesses are moving everything to the cloud, from documents to customer records and payroll data, even their day-to-day apps. Work feels faster, more flexible, and everyone loves being able to log in from anywhere.
But then comes the scary part. What if a simple mistake, like unauthorized access by an employee, leaves all business files wide open?
That’s the challenge with the cloud. It’s powerful and convenient, but if you don’t take security seriously, it can quickly become a weak spot.
But here’s the good news. By following a few cloud security best practices, you can protect your data and sleep a lot easier at night.
Key Challenges of Cloud Security Best Practices
Cloud security isn’t just about firewalls or antivirus. It’s a multi-layered approach that involves people, processes, and technology. By implementing thoughtful security practices, organizations can:
- Minimize risks of data breaches.
- Maintain compliance with evolving regulations.
- Enable secure remote access without slowing innovation.
Think of cloud security like locking the doors and windows of your house while still keeping it open and comfortable for guests.
Why Cloud Security Matters?
Cloud security isn’t always straightforward. Here are some of the biggest hurdles businesses run into:
1. Misconfigured settings: A small mistake, like leaving a Jira ticket or a document public, can expose sensitive business files.
2. Unauthorized access: Employees using weak passwords or logging in from unknown devices can create easy entry points for attackers.
3. Data leaks: Sharing files outside the company or storing them in the wrong place can quickly lead to data exposure.
4. Compliance worries: Regulations like GDPR or HIPAA mean businesses have to prove their data is secure, and audits can be stressful.
5. Shadow IT: Employees sometimes use unsanctioned apps or services without IT approval, creating blind spots for the security team.
Acknowledging these challenges helps businesses prepare rather than scramble after an incident.
Top 15 Best Practices for Cloud Security
Here’s a comprehensive list of cloud security tips & best practices to guide your strategy in 2025. Each comes with practical actions you can implement today.
1. CASB Software for Extra Control
Employees often use unsanctioned cloud apps, creating risk. A Cloud Access Security Broker (CASB) gives visibility and control.
- Identify risky apps.
- Set policies for secure file sharing.
- Get real-time alerts on suspicious activity.
2. Check Cloud Settings Regularly
Misconfigurations are one of the top causes of breaches.
- Scan for mistakes, like an openly accessible Google docs file or a storage bucket left open.
- Keep version control so you can roll back if someone makes an error.
- Make sure you’re not accidentally sharing sensitive files with “Anyone on the internet.”
3. Monitor Everything, All the Time
If you can’t see what’s happening, you can’t stop it.
- Turn on audit logging for every cloud service.
- Collect logs in one place so you can spot patterns.
- Set alerts for unusual behavior, like a user downloading gigabytes of data at 3 a.m.
4. Strengthen Your Cloud Infrastructure
Think of this as adding locks and alarms to your house.
- Patch systems often: Updates fix vulnerabilities that hackers look for.
- Segment networks: Keep sensitive systems separate, so if one is compromised, it doesn’t spread.
- Disable unnecessary services: Every extra service is another door someone could break into.
5. Secure Your APIs
APIs connect apps, but they can also be doors for attackers.
- Validate every input so no one can sneak in malicious commands.
- Use short-lived tokens so old ones can’t be abused.
- Watch for unusual API traffic, like thousands of requests in a short time.
6. Strong Identity and Access Management (IAM)
- Enforce multi-factor authentication (MFA) for all accounts.
- Implement role-based access controls (RBAC) to ensure users only access what they need.
- Regularly audit user access logs for unusual activity.
7. Prevent Data Loss (DLP)
Not all data leaks are malicious, sometimes people just make mistakes.
- Create rules to block sensitive files from being downloaded or emailed out using DLP security.
- Stop employees from accidentally sharing private docs outside the company.
- Teach teams what “sensitive” data really means.
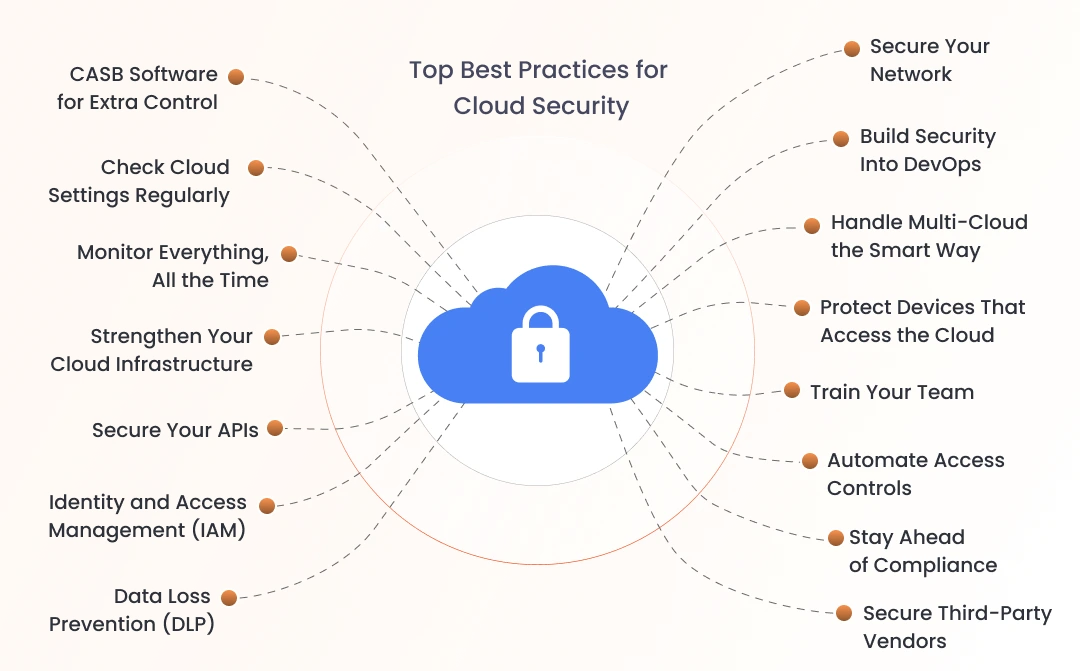
8. Secure Your Network
Think of this as fencing off your property.
- Use firewalls and intrusion detection systems.
- Apply Zero Trust rules, never assume a connection is safe.
- Keep development and production environments separate.
9. Build Security Into DevOps
If you’re building apps, security needs to be part of the process.
- Run code scans during development, not just after launch.
- Use verified container images, not random ones from the internet.
- Limit who can access your pipelines.
10. Handle Multi-Cloud the Smart Way
Many companies use more than one cloud provider. That adds complexity.
- Use the same security policies across providers.
- Keep track of which teams own which assets.
- Monitor connections between clouds, they’re easy to overlook.
11. Protect Devices That Access the Cloud
Your cloud is only as safe as the devices connected to it.
- Secure laptops and phones with endpoint protection.
- Use Mobile Device Management (MDM) to enforce rules.
- Block access from devices you don’t recognize.
12. Train Your Team
People are often the weakest link.
- Teach staff how to spot phishing attempts.
- Run practice drills to see how they respond.
- Remind them that cloud security isn’t just IT’s job, it’s everyone’s job.
13. Automate Access Controls
Manual checks aren’t enough.
- Automate least-privilege rules so employees only get access they need.
- Review permissions regularly.
- Cut off access instantly when roles change.
14. Stay Ahead of Compliance
Regulations are complex, but ignoring them isn’t an option.
- Map your systems to the relevant laws (GDPR, HIPAA, PCI).
- Generate reports for auditors.
- Stay flexible, laws change, and so should your policies.
15. Secure Third-Party Vendors
Your security is only as strong as the partners you trust.
- Check vendors before signing contracts.
- Ask for certifications like SOC 2 or ISO 27001.
- Monitor integrations to catch issues early.
Comparison Table: Risks vs Best Practices
| Cloud Risk | Matching Best Practice |
|---|---|
| Misconfigurations | Regular audits + automation |
| Weak passwords/access | IAM with MFA + RBAC |
| Data leaks | DLP + CASB policies |
| Shadow IT | CASB software for visibility |
| API exploits | API security + traffic monitoring |
| Compliance failures | Regular audits + compliance automation |
Cloud Security Tips & Best Practices Checklist
To keep things simple, here’s a quick checklist:
- Enforce strong IAM and MFA.
- Audit and fix misconfigurations.
- Monitor all cloud activity in real time.
- Strengthen cloud infrastructure security.
- Secure APIs with proper controls.
- Use CASB software for visibility and control.
- Apply cloud data protection and DLP rules.
- Secure your network with Zero Trust.
- Build security into DevOps.
- Handle multi-cloud environments wisely.
- Protect endpoint devices with MDM.
- Train employees regularly.
- Automate access controls.
- Check vendor security compliance.
- Continuously review and improve policies.
To Sum Up
Cloud security is a balancing act. No solution is perfect, and each organization faces unique risks. By applying these cloud data protection best practices thoughtfully, you can reduce exposure, safeguard sensitive information, and confidently embrace the cloud’s advantages in 2025 and beyond.




Leave a Comment