According to a report, more than 100 trillion signals are processed by Microsoft, blocking almost 4.5 million new malware attempts, examining 38 million for identity risks, and screening 5 billion emails for phishing and malware.
The use of AI is expected to accelerate malware, ransomware, and phishing attacks, making cybercrime an evergreen, ever-present threat in our lives.
The solution is to enforce Zero Trust Architecture (ZTA), which is a security model or approach built to counter the rising threat entities. Security systems can be built or onboarded that align with the ZTA principle ‘Never Trust, Always Verify.’
miniOrange offers best-in-class ZTA-aligned solutions like Single Sign-On (SSO), Privileged Access Management (PAM), Multi-Factor Authentication (MFA), access gateway, and more.
In this article, we will be talking about how an access gateway can help to achieve Zero Trust principles across hybrid and legacy applications. Let’s start by understanding a little more about ZTA.
What is Zero Trust Architecture (ZTA)?
Zero Trust Architecture is a security approach that defines how organizations can protect their systems, resources, users, and data from looming threat entities for both on-prem and cloud environments.
ZTA focuses on core principles, which the organizations can adhere to, and they are as follows:
1. Never Trust, Always Verify
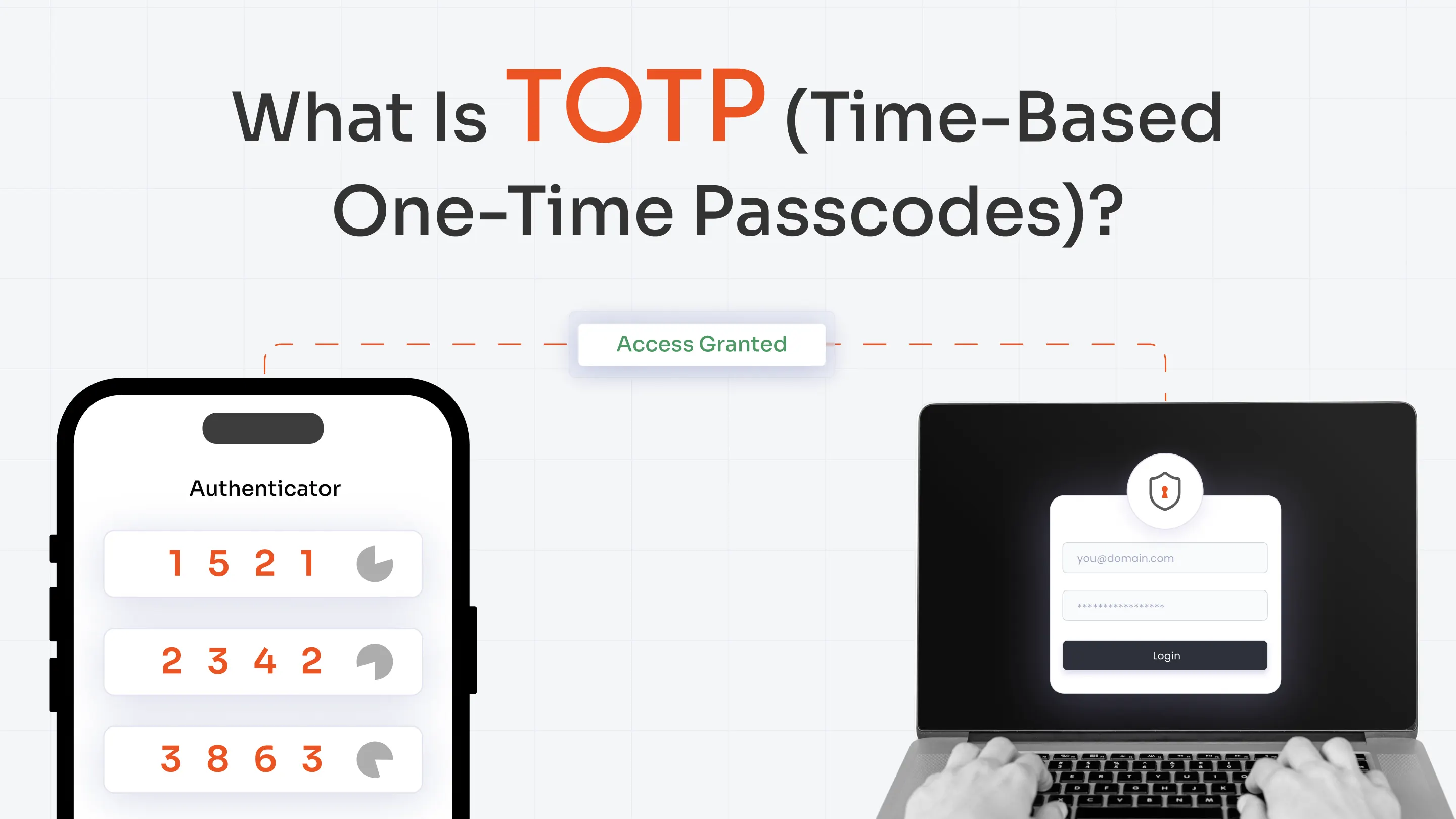
Do not assume trust for any entity, whether it is a known user, device, network connection, or an external source, even if they are on-premise. Every request must be verified and authenticated with MFA to avoid unauthorized access and severe cases of breaches.
2. Least-Privilege Access
The Principle of Least Privilege (PoLP) follows one simple rule: grant users access to only specific resources that they need to complete a particular task, and no more. This way, the confidential information stays safe, limited to only certain people (usually the executives and managers).
3. Assume a Breach
Develop security with a mindset that a data breach is inevitable or has already taken place.
With this mindset, the blast radius of an attack can be minimized through the implementation of encrypting all communication channels, data storage, and backup, and using predictive analytics to detect threats in advance, and responding to them on time.
4. Risk-Based Access Governance
ZTA evaluates risks based on the context behind every access request. So, for this, variables such as IP address, geolocation, device, time of the day, and user behavior are scrutinized before authenticating the users.
5. Risk Adaptation and Constant Monitoring
Systems and networks are constantly monitored at all entry points, within the system, and at exit points, to spot anomalies as they occur in real-time. Continuous, adaptive risk management is crucial to respond to threats dynamically.
Where Traditional Security Falls Short?
Traditional security models were built with the assumption that anything within the network can be trusted. This perimeter-based approach is no longer effective in today’s distributed, hybrid, and cloud environments. Traditional security systems cannot cope with remote work settings, SaaS apps, high-tech devices, and collaborations with third-party networks.
Furthermore, legacy systems are not equipped to cope with the evolving cyber threats; however, they can be integrated with the modern Identity and Access Management (IAM) solutions to defend against them.
Additionally, increased dependency on VPNs for remote and hybrid employees has pushed away the need for using traditional security channels.
Also, conventional methods have static access rules (where the user is verified based on only their credentials), which are no longer sufficient due to AI-driven phishing and social engineering attacks.
So, there is a need for modern security approaches like an access gateway for organizations that work on cloud, on-prem, and hybrid systems. Access gateways follow the ZTA principles, and modern IAM solutions can be integrated with them for better security.
What is an Access Gateway?
An access gateway acts like a gatekeeper and assures secure access management between the users and the applications (on-premise or cloud) they want to access. It basically boosts application security by acting like a reverse proxy, where it intercepts the user’s request to access an application or a resource.
Access gateway redirects this request for authentication to an Identity Provider (IdP), where the users can also be verified against multiple factors via MFA methods. After access policies (Role-Based Access Control) are checked, the user is granted access via the access gateway.
Take a deep dive intoAccess Gateway vs. VPN
Role of Access Gateway in Zero Trust Architecture
Now that we’ve comprehended the access gateway and ZTA, let’s understand in-depth the critical role played by the access gateway in ZTA.
1. Identity-Based Access Control
Identity-Based Access Control (IBAC) is a type of security method where access to accounts, data, and resources is granted after verifying a user's identity.
Access gateway implements this approach by integrating with the modern IAM solutions to authenticate every user request.
This can be accomplished by intercepting the incoming user requests and redirecting them for authentication via passwordless authentication methods, Single Sign-On (SSO) through an IdP, or MFA methodologies (which aligns with the Zero Trust Network Architecture principles).
2. Continuous Verification
Unlike the traditional methods, where full access is granted with just credentials, continuous verification combined with an access gateway creates a strong security model, which adheres to the Zero Trust Network Architecture (ZTNA).
This model rigorously enforces dynamic access control by evaluating real-time risks based on the context for every user request. It also enables access policies throughout the user session.
3. Secure Access for Legacy Applications
Safeguarding legacy applications and aligning them with the ZTNA can be achieved with the access gateway. This method offers MFA and SSO without needing any code changes to the legacy applications.
Additionally, legacy apps use outdated authentication methods like form-based or header-based authentication that don’t match the modern protocols like SAML or OIDC. The access gateway acts as a Zero Trust enabler for these apps, so they fit within the Zero Trust framework.
4. Centralized Policy Enforcement
Centralized policy enforcement is a core aspect of the Zero Trust model and is crucial for managing safe access across complex hybrid environments.
This approach helps to reduce the overall attack surface, monitors threats in real-time, and maintains consistent access control.
How miniOrange Access Gateway Enables Zero Trust?
The miniOrange Access Gateway solution is developed to speed up the Zero Trust strategy by integrating with the existing IAM or IdP system.
It is also compatible with MFA solutions, risk-based authentication, and adaptive access control, for both modern and legacy applications, encompassing Oracle EBS, SAP, IIS, etc. This helps organizations to strengthen their security posture across all infrastructure.
With SSO, reverse proxy, and centralized access management, the access gateway holds the key to Zero Trust adoption.
Learn how miniOrange Access Gateway can help modernize your Zero Trust integration.
Access Gateway: Your Zero Trust Enabler
The miniOrange Access Gateway helps businesses bridge the gap between traditional perimeter-based security and advanced Zero Trust models, offering a unified platform that manages user access to both legacy and cloud applications without compromising security or user experience.
By adopting miniOrange Access Gateway, organizations can future-proof their digital infrastructure and streamline the transition to a Zero Trust framework, supporting business agility and security resilience.
Start your Zero Trust journey with miniOrange Access Gateway today. Get in touch with us to consult with an expert.



Leave a Comment