Zero Trust is a security mindset and architecture that assumes no user, device, or network is inherently trustworthy, requiring continuous verification for every access request. Unlike a single tool or product, it requires a holistic strategy that integrates strong identity controls, such as MFA and least privilege access.
Success with Zero Trust hinges on cultural shifts, executive buy-in, and ongoing adaptation to threats that emerge beyond the initial setup. Begin by mapping assets, users, and data flows to identify risks and gaps in trust assumptions. Roll out identity as the core pillar with robust IAM solutions, enforcing MFA everywhere and just-in-time access.
In this article, you will learn practical steps to build and sustain a Zero Trust framework.
Key Takeaways
- Zero Trust requires verifying every user, device, and session explicitly to eliminate implicit trust.
- Start by defining your protect surface and mapping data flows for zero trust implementation.
- Identity and device trust form the foundation of zero-trust architecture implementation.
- Microsegmentation reduces lateral movement in zero trust network implementation.
- Policies must be dynamic and continuously evaluated using real-time analytics.
What Is Zero Trust and Why Does It Matter?
Zero Trust is a security mindset and architecture that assumes no user, device, or network is inherently trustworthy, requiring continuous verification for every access request in zero trust implementation.
This means organizations must shift from traditional perimeter defenses like firewalls, trusting anything inside the network, to a model where "never trust, always verify" applies universally, regardless of location. Every transaction, whether from an employee on a corporate laptop or a vendor via cloud app, undergoes multi-factor checks on identity, device health, behavior, and context before granting access.
In practice, it eliminates implicit trust zones, treating the network as hostile territory where breaches are inevitable, thus prioritizing containment over detection alone. This approach, rooted in Forrester's 2010 framework and NIST SP 800-207, reduces attack surfaces by enforcing granular controls dynamically.
Core Pillars of Zero Trust security framework
Verify Explicitly
Verify explicitly means every user, device, app, and session must be authenticated and authorized using all available signals such as identity, device posture, location, and risk. Instead of relying on network location alone, access decisions are driven by continuous assessment so that each request is treated as untrusted until proven otherwise.
Use Least Privilege Access
Least privilege access restricts users and workloads to the minimum permissions necessary to perform their tasks. By tightly scoping roles, enforcing just-in-time and just-enough access, and regularly reviewing entitlements, organizations reduce the blast radius if an account or session is compromised.
Assume Breach
Assume breach treats the environment as if attackers are already inside, driving designs that minimize lateral movement and limit impact. This leads to tactics like microsegmentation, strict east-west controls, and rapid detection and response so that any intrusion is contained quickly and cannot spread widely.
Why Zero Trust Matters in Modern Security?
Traditional Security Limitations
Traditional perimeter-based security, relying on firewalls and VPNs, fails against modern threats like ransomware, insider risks, supply chain attacks, and sophisticated phishing, where attackers bypass defenses and dwell undetected for months.
Zero Trust counters this by enforcing continuous verification, reducing breach dwell time by up to 50% through explicit checks, limiting lateral movement, and applying least privilege to shrink attack surfaces dramatically. It shifts from static "castle-and-moat" models to dynamic protection that adapts to hybrid environments, preventing breaches like SolarWinds or Colonial Pipeline from escalating.
Compliance and Business Resilience
Zero Trust ensures compliance with stringent regulations like GDPR, HIPAA, PCI-DSS, NIST 800-207, and emerging DPDP Act requirements by embedding audit-ready controls into access decisions. It supports hybrid workforces, multi-cloud migrations, and ZTNA as a secure VPN replacement, enabling seamless remote access without exposing networks. Organizations report fewer incidents and millions in cost savings, building resilience against 2025 threats like AI-powered attacks and quantum risks.
Strategic Business Advantages
Beyond defense, Zero Trust accelerates digital transformation by enabling secure automation, DevSecOps, and third-party integrations critical for agility in competitive markets. It fosters a security-first culture, reduces insurance premiums through proven maturity, and positions firms as leaders, vital for sectors like healthcare, finance, and government facing zero trust implementation mandates.
Zero Trust Implementation Meaning
Zero Trust implementation fundamentally means operationalizing a "never trust, always verify" principle across your entire ecosystem, replacing outdated perimeter trust with continuous, context-based validation for every access attempt in zero trust implementation. This core shift involves mapping assets, enforcing granular policies via identity fabrics, and layering defenses like device checks and microsegmentation to create resilient architectures aligned with how to implement zero trust frameworks.
Unlike deploying isolated tools, it requires a zero-trust implementation plan that assesses current gaps, prioritizes high-risk paths, and iterates through maturity stages per NIST 800-207, tackling zero-trust implementation challenges in 2026, such as hybrid cloud complexity and legacy interoperability. Effective zero-trust architecture implementation builds adaptive security that scales with threats, delivering measurable outcomes like reduced dwell times and compliance readiness.
6 Steps to Implement Zero Trust Architecture in 2026
Zero Trust implementation becomes practical when broken into clear, repeatable steps without trying to secure everything at once. This 6-step implementation plan and checklist helps organizations design Zero Trust architecture in a structured, low-risk manner.
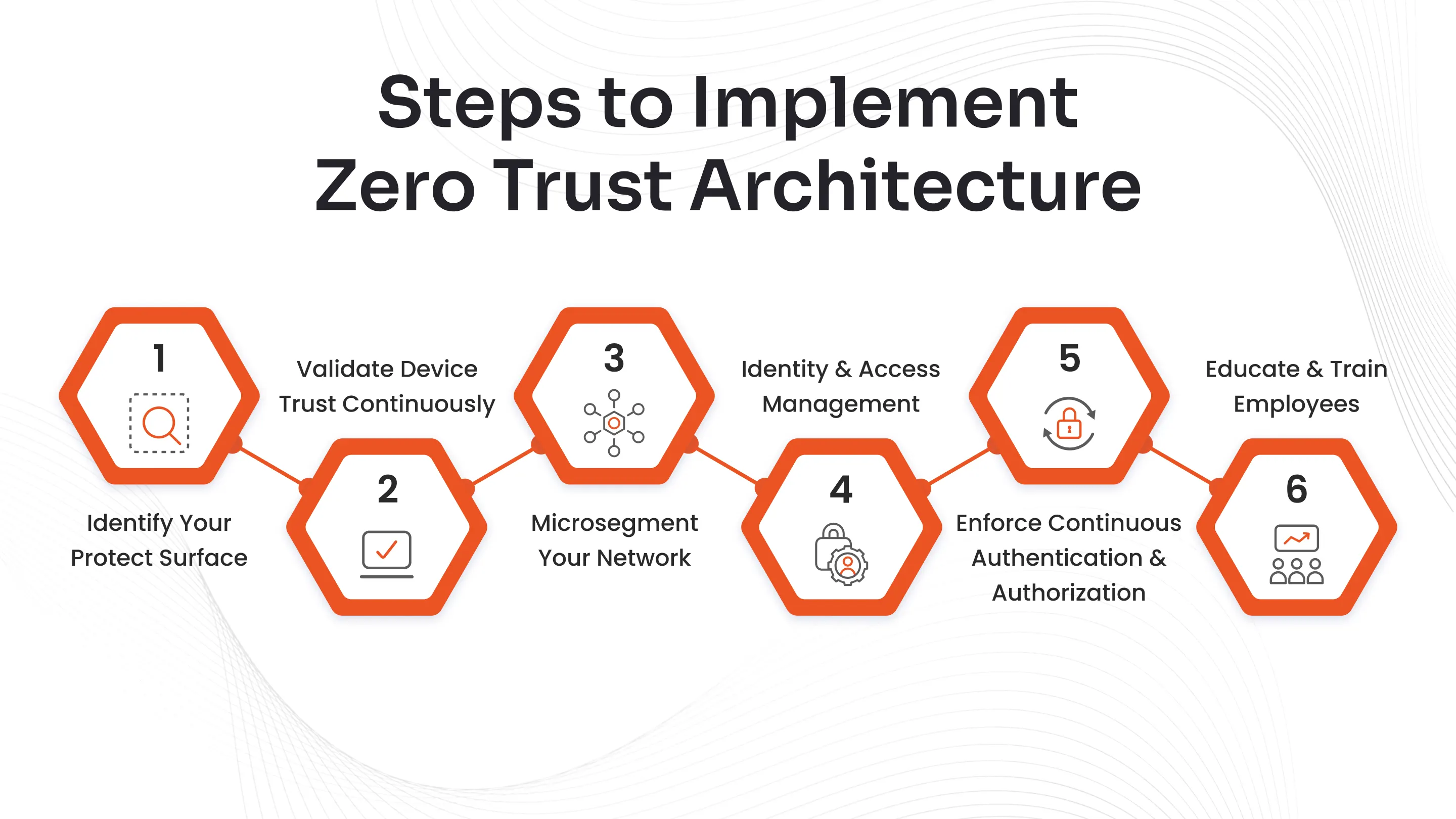
Step 1: Identify Your Protect Surface
The protect surface is the smallest, most critical set of assets to secure first, including high-value data, crown-jewel applications, essential services, and key user groups that could cause catastrophic damage if breached. Prioritize items like financial transaction systems processing payments, payroll databases with employee compensation, identity providers handling authentication, or patient records containing PHI in healthcare, where single compromises lead to regulatory fines, reputational harm, and operational halts.
Narrow focus avoids tackling the entire attack surface, which includes thousands of dynamic endpoints, apps, and flows that overwhelm resources and delay value. Instead, map dependencies, run threat modeling with asset inventories, and apply controls iteratively per NIST 800-207 guidelines. This delivers quick wins, measurable progress, and scalable maturity without exhausting teams or budgets upfront.
Step 2: Validate Device Trust Continuously
Device trust requires users to prove endpoint health and compliance before gaining access, shifting from one-time checks to perpetual validation in Zero Trust. Deploy agents or NAC solutions to assess OS versions, patch levels against active exploits, full-disk encryption, firewall configurations, and EDR tool presence, automatically blocking outdated or vulnerable hardware from networks.
Extend monitoring to detect unauthorized software installs, sideloaded apps evading controls, outdated client versions, or privilege escalation indicators like rogue admin processes. Route signals to gateways for quarantine, remediation prompts, or denial, safeguarding hybrid environments with BYOD, IoT, and remote devices from insider or external threats effectively.
Step 3: Microsegment Your Network
Microsegmentation divides networks into granular, isolated zones, enforcing default-deny policies, permitting only strictly necessary east-west communications between approved entities. Leverage software-defined networking (SDN), host agents, or cloud-native services to enforce identity-contextual policies, providing full visibility and auditing of data flows across environments.
Key examples: Prevent payroll systems from interacting with marketing applications to stop credential spread; limit HR databases to authorized personnel only; restrict critical apps to posture-verified devices via explicit allow-lists. This containment strategy thwarts ransomware propagation, as demonstrated in SolarWinds-style attacks, scaling seamlessly over on-premises, cloud, and hybrid infrastructures without requiring complete redesigns.
Step 4: Identity and Access Management
IAM forms Zero Trust's foundation, authenticating user identities rigorously while dictating precise post-verification permissions to eradicate standing privileges entirely. Roll out MFA universally, using biometrics, hardware tokens, or adaptive push notifications, alongside least-privilege scoping that matches exact task requirements and durations.
Incorporate just-in-time (JIT) elevations through approval workflows, robust RBAC for entitlement consistency, and HR-integrated automation for provisioning new access and instant deprovisioning on role changes or terminations. These measures slash over-privileged accounts by up to 80%, enable SIEM-integrated auditing, and underpin privileged access management (PAM) critical for compliance in finance, healthcare, and government sectors.
Step 5: Enforce Continuous Authentication & Authorization
Continuous authentication fuses identity, device posture, location, time, and behavioral signals into ongoing real-time risk scoring throughout every session, beyond initial login. Tools like UEBA and CASBs flag anomalies such as abrupt IP changes, unusual data volumes, or keystroke anomalies, prompting step-up challenges, session limits, or immediate terminations seamlessly.
Access remains fluid: Full privileges for verified onshore users during standard hours, but revocation triggers for offshore anomalies, malware hints, or hijack attempts across applications, APIs, and multi-cloud setups. AI/ML-driven adaptability ensures proactive threat neutralization, embodying true "never trust, always verify" across distributed, dynamic enterprises.
Step 6: Educate and Train Employees
Human factors derail Zero Trust if unaddressed, so structured training converts employees into proactive security allies via comprehensive, recurring programs. Teach core principles like universal verification, hands-on new processes such as MFA handling and access denials, plus realistic phishing, vishing, and social engineering simulations to sharpen detection instincts.
Deliver role-tailored content, governance for executives, secure coding for developers, hygiene basics for all, enhanced by gamification, newsletters, and quarterly drills to embed habits. Metrics like phishing simulation success rates and policy compliance track efficacy, often yielding 40-70% incident reductions while minimizing change resistance and maximizing architectural reinforcement through cultural alignment.
Zero Trust Implementation Common Challenges 2026
Organizations pursuing zero trust implementation in 2026 face persistent hurdles that can derail progress if unaddressed, from strategic confusion to technical roadblocks. This section outlines five common challenges with practical mitigation strategies to ensure smoother zero trust architecture implementation amid evolving threats and hybrid complexities.
Not Knowing Where to Start
Many teams feel overwhelmed without a clear entry point, unsure whether to prioritize identity, networks, or endpoints first in zero trust implementation. Start with the protect surface, map your crown-jewel assets like customer data or core apps using NIST 800-207 roadmaps. Conduct maturity assessments with free tools from CISA or Forrester to build phased plans, avoiding analysis paralysis and delivering quick visibility wins within 90 days.
Implementation in Complex Infrastructure
Hybrid multi-cloud environments with on-prem, SaaS, and edge create policy enforcement gaps during zero trust rollout. Use agentless orchestration platforms that unify visibility across silos without a rip-and-replace. Begin with high-risk paths via traffic flow mapping, then federate identity across providers for consistent controls, scaling incrementally to handle infrastructure sprawl effectively.
Lack of Continuous Monitoring
Teams treat Zero Trust as "set and forget," missing real-time anomaly detection essential for dynamic policy enforcement. Integrate SIEM with UEBA platforms for behavior baselines across logs, endpoints, and networks. Automate alerts and responses via SOAR, ensuring 24/7 visibility that evolves with threats rather than static configurations.
Being Tied to Legacy Systems
Legacy apps without modern APIs resist microsegmentation and continuous auth, blocking full zero-trust network implementation. Deploy API gateways or shadow agents to wrap incompatible systems, enabling policy enforcement without refactoring. Prioritize containerization roadmaps and integrate via service meshes, gradually modernizing while maintaining operations and containing risks in brownfield deployments.
Cost Concerns
Zero Trust demands upfront investments in MFA, ZTNA, PAM, IGA, and EDR tools, plus skilled talent in identity, networking, and cloud security amid tight budgets. Phase investments by ROI, start with identity (cheapest, highest impact) and train internally via certifications. Cloud consumption models cut CapEx 40%, while reduced breach costs justify spending long-term per Gartner analyses.
Privileged Access Management to Implement Zero Trust
Privileged Access Management (PAM) Solutions are essential in a Zero Trust strategy because it removes always-on admin rights, strictly verifies every privileged request, and continuously monitors high-risk activities across servers, databases, and admin consoles. It enforces Just-In-Time (JIT) privileged access, stores and rotates credentials in secure vaults, adds step-up authentication like MFA or biometrics, and records every privileged session with real-time controls to detect anomalies, stop misuse, and prevent credential-based attacks.
miniOrange combines IAM and PAM to deliver a unified Zero Trust-aligned security stack, helping organizations centralize identities, enforce least privilege, and secure privileged access across cloud and on-prem environments with strong MFA, JIT access, session monitoring, and endpoint controls.
FAQs
What are the three main principles of Zero Trust implementation?
The three main principles are verify explicitly (authenticate every request using all signals), enforce least privilege access (grant minimal permissions needed), and assume breach (design as if attackers are inside, minimizing lateral movement).
Is Zero Trust difficult to implement?
Implementation is manageable when approached in phases, starting with identity and high-value assets like the protect surface, then layering network and monitoring controls iteratively per NIST guidelines.
What is an example of Zero Trust?
A common example is replacing VPNs with ZTNA, where remote employees access specific SaaS apps only after MFA, device compliance checks, and behavior analysis, with no full network exposure.
How long does it take to implement Zero Trust?
Timelines vary by organization size: small firms achieve initial maturity in 6-12 months via phased roadmaps; enterprises take 18-36 months for full coverage, focusing on quick wins first.
Is Zero Trust better than VPN?
Yes, Zero Trust surpasses VPNs by providing granular app-level access without exposing entire networks, continuous verification beyond login, and reduced attack surface, ideal for hybrid work versus VPN's broad trust model.





Leave a Comment