Need Help? We are right here!
Search Results:
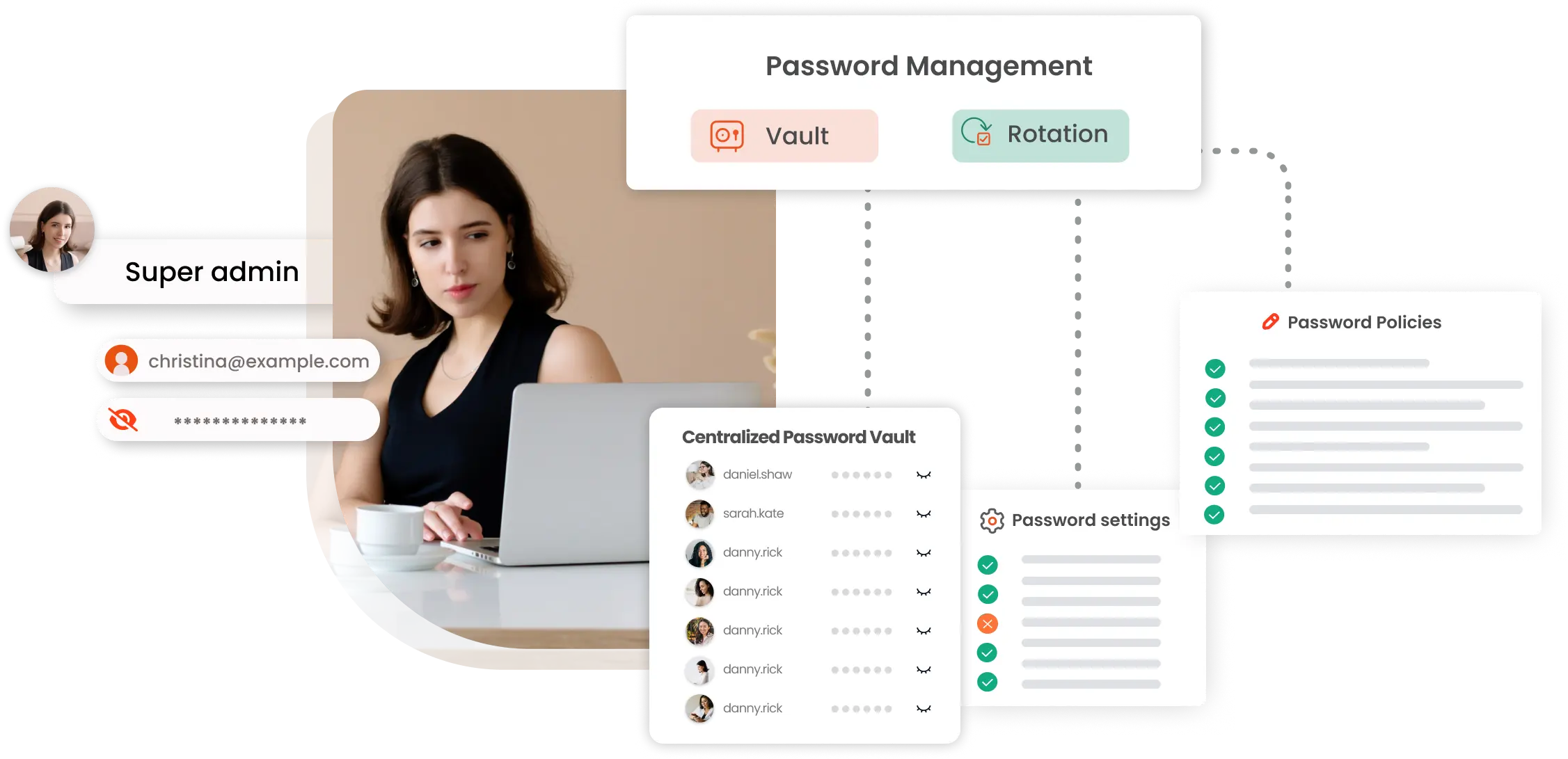
×JIT privileged access management provides users with temporary, elevated access to resources and systems for a limited period. Once the task is over, these elevated access rights are automatically revoked. Here’s what JIT has in store for you:







Users must justify their need for privileged access, and once approved, they can connect to specific resources for a limited time.

It involves granting enhanced permissions to a process on an as-needed basis.
Privileged access is provided to users under two scenarios:
After this time frame ends, the elevated privileges are automatically withdrawn.
This type is known as temporary accounts or zero-standing privilege accounts. These accounts are created based on specific needs, sometimes called "one-time" accounts.
JIT provides precise control over privileges, granting only the minimum privilege needed for tasks, following the principle of least privilege (POLP).
Users submit requests for elevated access, which are reviewed and approved briefly. Users are granted temporary access to perform their designated tasks efficiently.
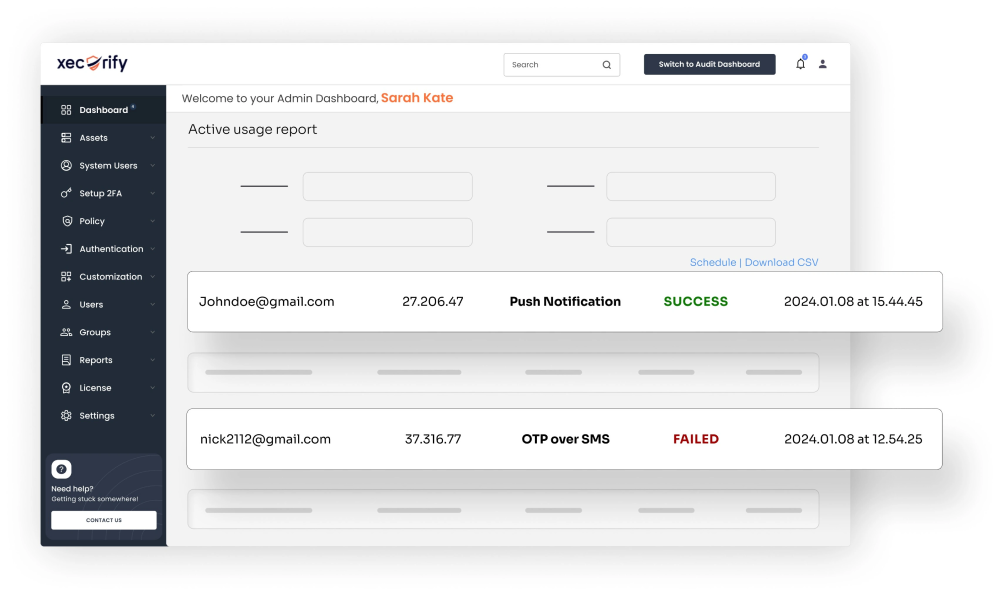
JIT solution offers comprehensive auditing & monitoring capabilities. It logs every access request, approval, and activity in privileged sessions, providing an audit trail to enhance security and meet compliance requirements.
JIT Access automatically revokes temporary privileges and terminates sessions after the authorized time elapses or the user completes their tasks. Explore Privileged Session Monitoring.
Features a smooth workflow for approvers to evaluate access requests, It assesses risks and then decides on approvals or further review.
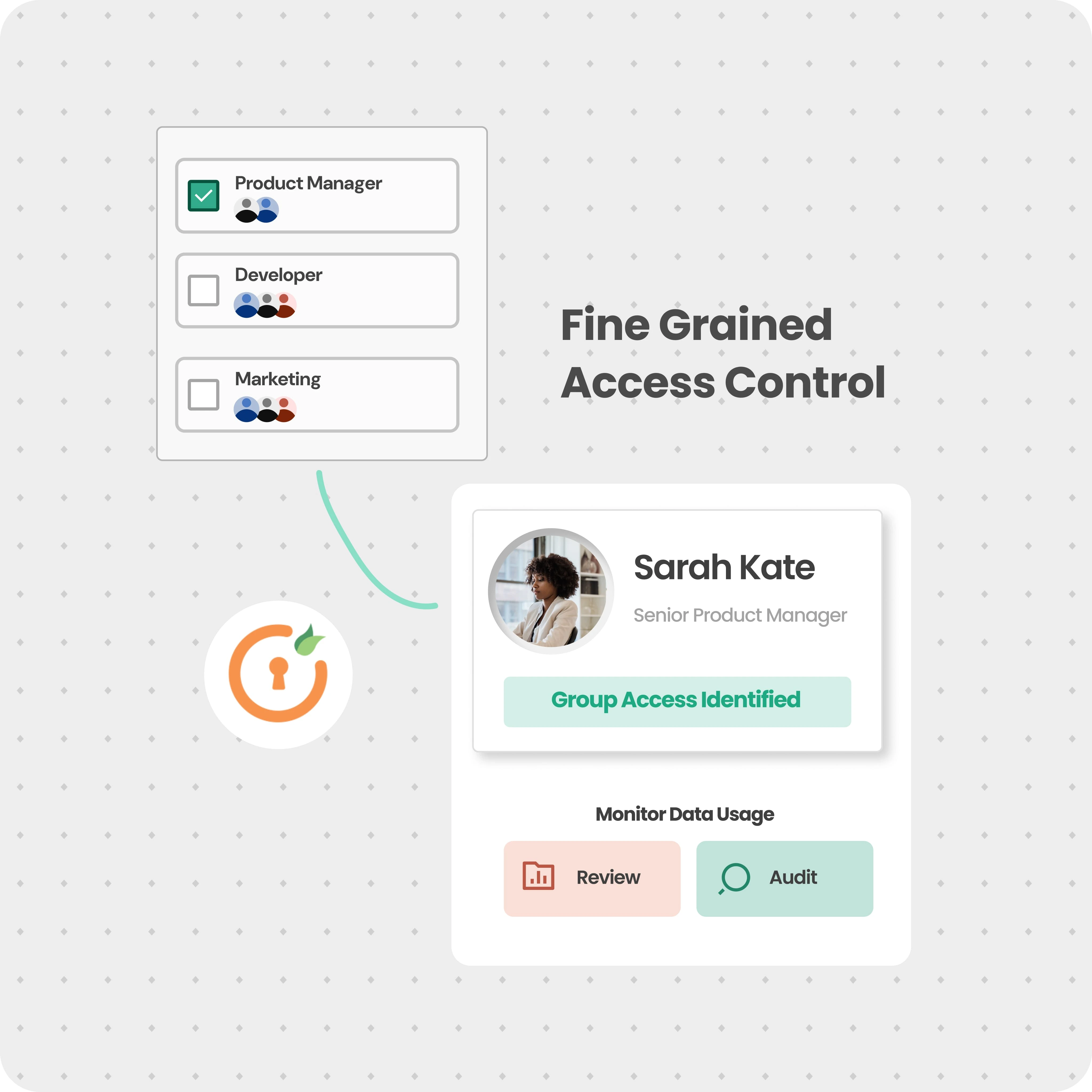
Limit privileged access to only when needed. Reduce security risks, prevent unauthorized access, and strengthen defenses.
Grants only the access needed, when needed, for external vendors and contractors, enhancing security.
Streamlines workflows, saving time and providing fast, secure access without compromising productivity.
Privileged Access Management seamlessly integrates into your existing infrastructure, ensuring secure and
managed access to critical systems





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
JIT can help reduce the attack surface, limit insider threats, and prevent unauthorized access. After applying temporary access to your organization, you can align better with the Zero Trust Principles and manage access smoothly.
For Just-in-Time access management, it's best to:
To put Just-in-Time Privileged Access in place, you'll want to:
- Figure out which jobs or roles need special access.
- Set up a system where they can ask for access whenever needed.
- Use tools or software that can automatically give access for a short time and then revoke after the completion of a designated task.
JIT in Active Directory means using the JIT principles to manage privileged access within the Active Directory. It helps control who gets to do what by only giving temporary admin rights when needed.
Just-in-time admin access is about giving admin rights to a user for a short period only when necessary. It's a way to make sure that only the right people have high-level access and only when they need it.
Just-in-Time Network Access Control is a security measure that gives users temporary access to network resources. It's about making sure people can only connect to your network or use certain services when it's needed for their job, helping to keep your network safer.
