A CASB is the first line of defense to secure your cloud app access and keeps them ITAR compliant with the latest security standards. This keeps businesses highly efficient, productive and ensures all cloud services will run smoothly. With the industry standard CASB compliance requirements, company’s are forced to adhere to the strict guidelines to protect both, their business data and the customer information that they store.
Compliance and data security play pivotal role in in protecting a business from threat and are one of the key factors why any high grossing business is still running. In this blog, we will learn about the ITAR compliance, what ITAR Compliance is, and how your business can start using ITAR compliant cloud services with a CASB solution. So let’s get started!
What is ITAR Compliance?
ITAR or International Traffic in Arms Regulations is a compliance standard requirement that all resellers, brokers, exporters, manufacturers, defense services, and where all the data related to it is stored. ITAR is US givernment regulations to prevent any unauthorized data to be transferred out of the scope of access. For IT companies, ITAR Compliance is meant to protect how data flow between parties and prevent disclosure of any data to foreign parties.
The basic ITAR data security requirements for ITAR Compliant cloud services includes,
- Maintaining a strict information security policy across departments and parties involved in any capacity.
- Well-maintained firewall system in place and a unique user ID management for all users in the system.
- Unique user ID management for all users involved.
- Encrypting sensitive data related to any transactions, conducting regular system checks and thorough security tests.
- Monitor complete business infrastructure and conduct tests for potential data threats.
- Robust user access control policies needs to be implemented.
- Monitor user interaction with sensitive data and keep a track of it as well.
- Dynamic system to isolate potential vulnerabilities to prevent it from spreading throughout the cloud infrastructure.
These security measures ensure that ITAR compliance is met and data is still easily accessible while staying protected against loss or unauthorized user access.
How can a CASB help make your business ITAR Compliant with cloud services and storage?
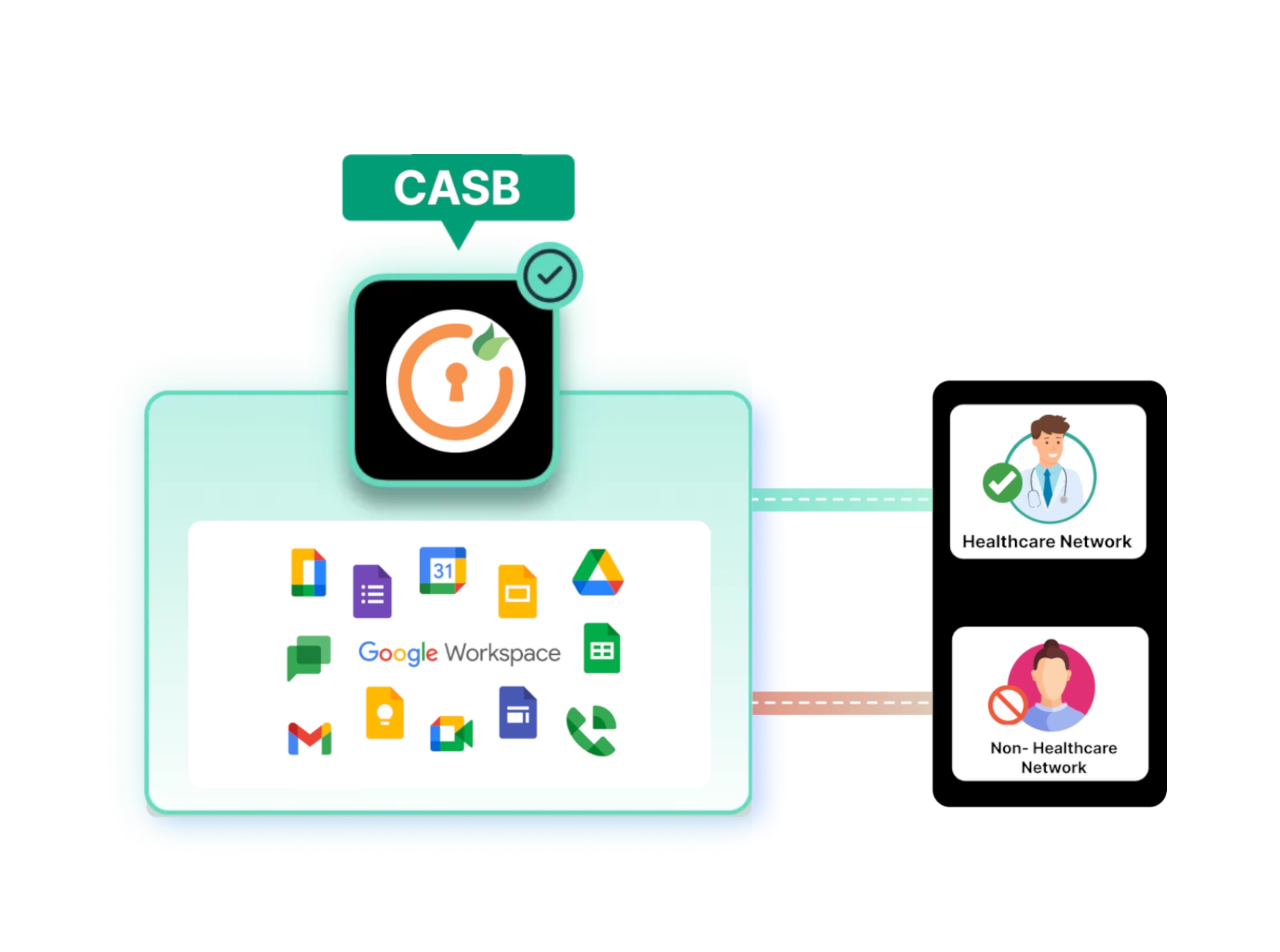
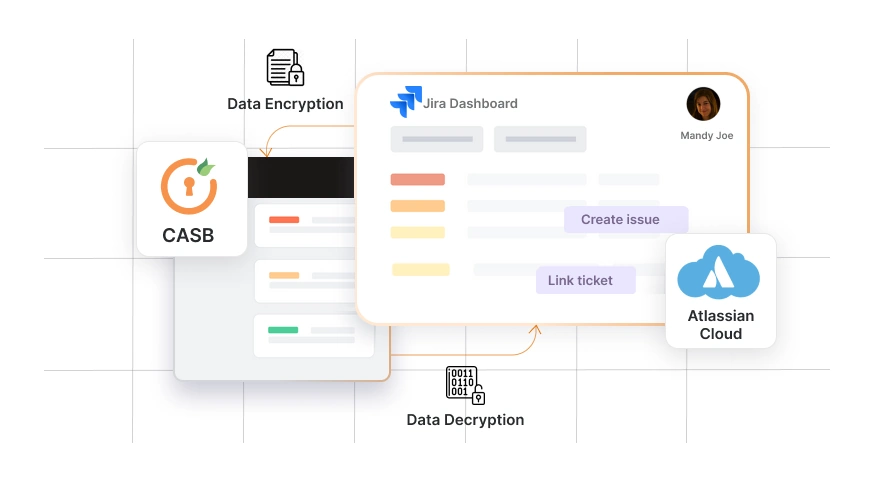
CASB or Cloud Access Security Broker, is an advanced security solution that’s designed for data protection and active threat detection while providing you visibility into user actions and controlling app access permissions. CASBs cover all the ITAR data security requirements for ITAR Compliance and more, to provide the best security features for your business so that you never run in to trouble related to ITAR. CASBs also help generate detailed reports of critical infrastructure components to find points of potential data threats.
Let’s understand how CASB can provide ITAR Compliance for cloud services with an example.
Working of CASB for ITAR Compliance for businesses cloud services
Neil, a cybersecurity specialist at a private defense company, aims to achieve ITAR compliance using a CASB (Cloud Access Security Broker) solution. He selects a CASB that offers data discovery, encryption, manages access controls, and real-time activity monitoring. The CASB scans the cloud storage, identifies ITAR-sensitive data, and classifies it appropriately. It enforces role-based access policies, ensuring only authorized personnel access sensitive information. Encryption safeguards data during transmission and storage. Real-time monitoring tracks user activity and detects anomalies. Neil's strategic implementation of the CASB ensures ITAR compliance, protecting defense-related data from unauthorized access and potential breaches.
This is how the CASB works in real time to make your business cloud services ITAR Compliant and provides an air tight data security solution.
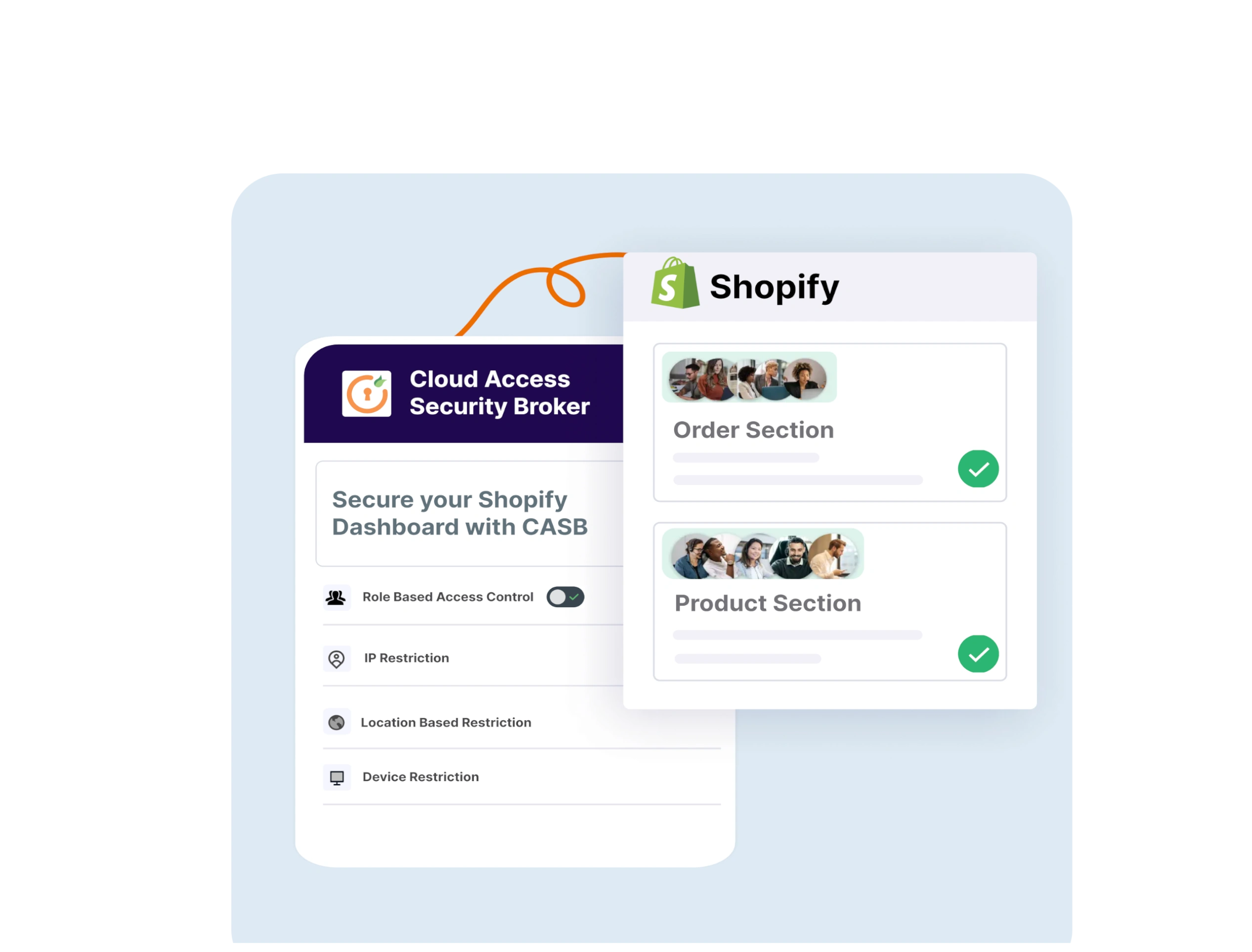
Benefits of using a CASB for any Cloud Service
CASBs come with a lot of features and benefits once deployed. Here are the top advantages of using a CASB,
1. Compliance Inclusion : Keep your business compliant and updated with the latest security standards and protocols to be followed in the industry.
2. Data Protection : Protect Cloud data access from unknown and unauthorized user access at run time.
3. Threat Detection : Actively monitor for potential threats targeting your cloud infrastructure and mitigate them by isolating the threat vectors.
4. Deep Visibility : Get deep insights into user actions and gain visibility into what they are accessing and the cloud resources they are using.
5. User Entity and Behavior Analytics : Assign a user risk score to each user for every suspicious activity, and once the score crosses a threshold completely restrict the user from accessing any more cloud apps and alert the SOC team.
6. Threat Reports : Generate detailed threat reports with the miniOrange CASB to gain deep insights into your cloud app usage and infrastructure security status.
In Summary
In this blog, we saw how the miniOrange CASB helps turn your business ITAR Compliant with the necessary security regulations, provide complete data protection, actively monitors for potential threat vectors and provides deep visibility into user actions with all the popular cloud services for Atlassian Cloud ITAR, AWS ITAR, GCP ITAR, and Azure ITAR Compliance. So if you are on the market looking to turn your business ITAR Compliant for cloud services and cloud storage, miniOrange CASB is the go to solution to meet all your security needs. Our competitive pricing and globally recognized support team is what keep us ahead of our competition to provide you with the best cloud security experience.
So what are you waiting for? Drop us a query at info@xecurify.com and we will get right back to you to address all your CASB needs.
Reference links
Author