Logging in to your systems in a secure manner is pivotal to all organizations. Hardware tokens bring the best of security with convenience. They promise zero trust by providing an authentication solution that verifies user identities and prevents cyberattacks from happening. On account of rising cyber threats and regulations, companies are on the lookout for secure ways like miniOrange to sign in without the hassle of interceptions that occur with many methods. This is where hardware-based tokens meet the requirements of contemporary authentication.
Understand Token-Based Authentication
Token-based authentication is a method of verifying a user’s identity, but in a more modern approach. The user does not need to store sensitive credentials or session data server-side, ever. Instead of providing a username and password every time, the server provides a secure token, and the user provides that token.
Token-based authentication can be used for APIs, mobile applications, zero-trust networks, and cloud-first environments.
What is Token?
A token is a small amount of encrypted data that establishes your identity. The server issues the token to you after successfully authenticating you. You send the token for EVERY request made to the server, and the server trusts the token is true or your identity. A token is like a digital badge, just secure and short-term.
Lifecycle of a Token
The token lifecycle is the process of issuing, storing, using, validating, expiring, and renewing or revoking a token during authentication.
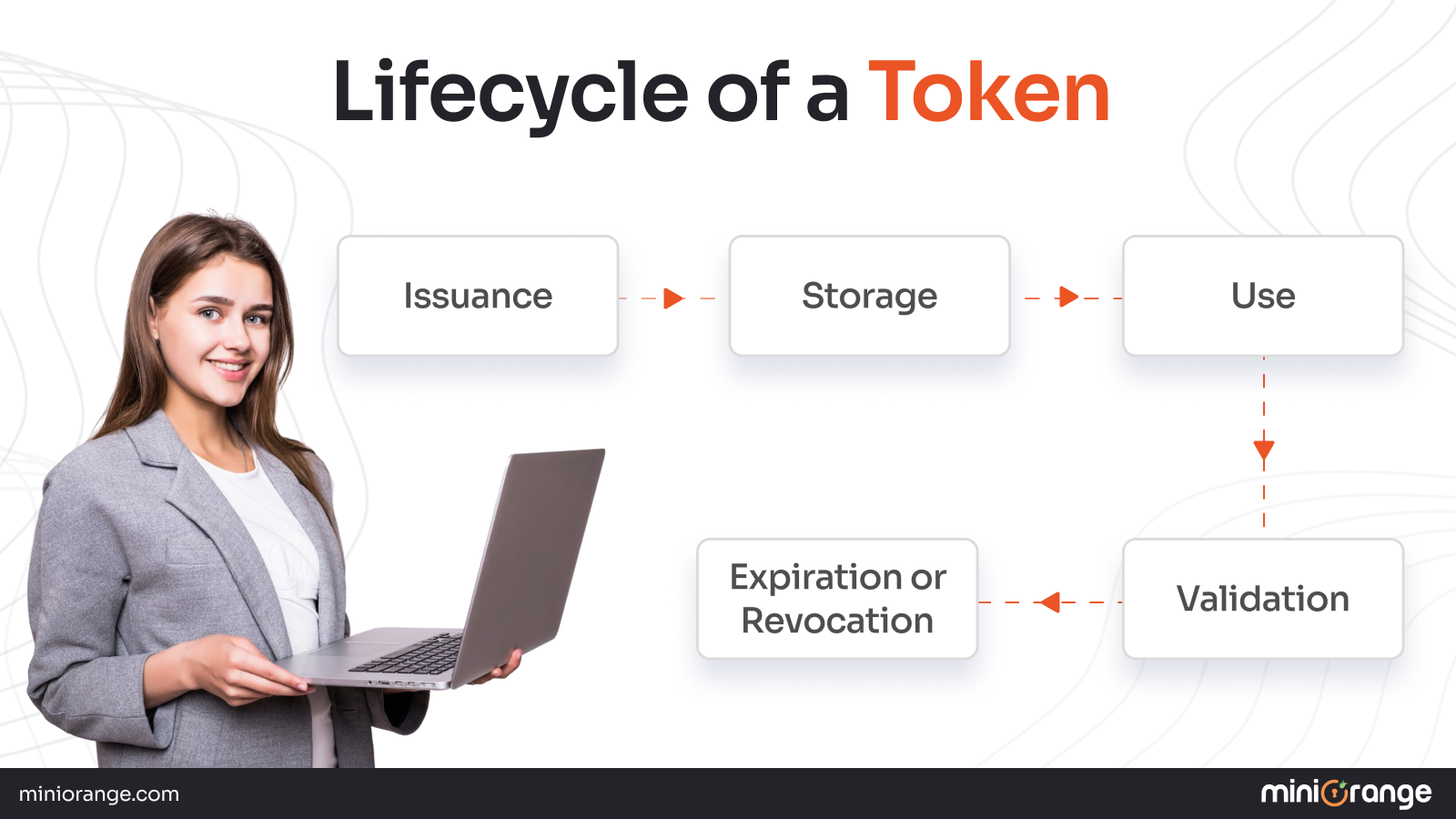
- Issuance: When the server issues a token after successful authentication
- Storage: The client stores a token somewhere secure (local storage, memory, or secure enclave).
- Use: The client will send the token when making every request to the server.
- Validation: The server will check to see if it is valid and check to make sure it has not been tampered with in any way.
- Expiration or Revocation: Tokens can expire or may be revoked. When it expires, the client will need to request a new token.
How do tokens differ from sessions and cookies?
- Session: Sessions are data stored on the server. This introduces more complexity and is less scalable. Cookies: Cookies bind session IDs to users via the browser and thus tie users to one (the same) domain.
- Tokens: tokens are by definition stateless and portable (work on any domain, are not tied to one, and work across devices and APIs), are simpler to use than cookies, and are the preferred method of authenticating users for distributed systems.
Tokens in APIs, mobile apps, zero-trust environments
- APIs: Tokens provide machine-to-machine security.
- Mobile Applications: Tokens provide patterns of consistent authentication, not directly tied to cookies in the user's browser.
- Zero-Trust Networks: All requests must prove authenticating the user's real identity, even requests on private networks.
Token-based authentication vs. OAuth vs. JWT
- Token-based authentication: A generic term to describe when the server is proving the user's identity, and the server is issuing tokens.
- OAuth: A framework for authorization (inception in 2006) allowing a user to manage access to third-party applications without sharing the necessary credentials.
- JWT (JSON Web Token): A lightweight token (ratified 2010) that compacts tokens, making them both portable and self-contained; a JWT is part of the OAuth flow.
History of Token-Based Authentication
We have not always authenticated in our current pattern. By and large we have always been constrained by the static nature of usernames and passwords; however, authentication is built on rules and thinking that evolve over time:
- The limitations of passwords: the early logins, where all inline of static username and password.
- Session IDs and Cookies: Older web applications (that came to the forefront late in the 1990s) had a secure login to the server with session information stored on the server side.
- Tokenization: As distributed systems emerged, tokenization became the preferred method to implement authentication. We have observed the following.
- OAuth (2006): Established shared delegated access.
- JWT (2010): Supported making access tokens portable and self-contained.
- OpenID Connect (2014): Combined and linked authentication with delegated OAuth authorization.
- Passwordless methods (last few years): transitioned to tokens allowing users to log in without ever using passwords!
Benefits of Token-Based Authentication
Token-based authentication provides enhanced security and flexibility beyond traditional login and authentication methods. The main benefits of using tokens instead of session keys are as follows:
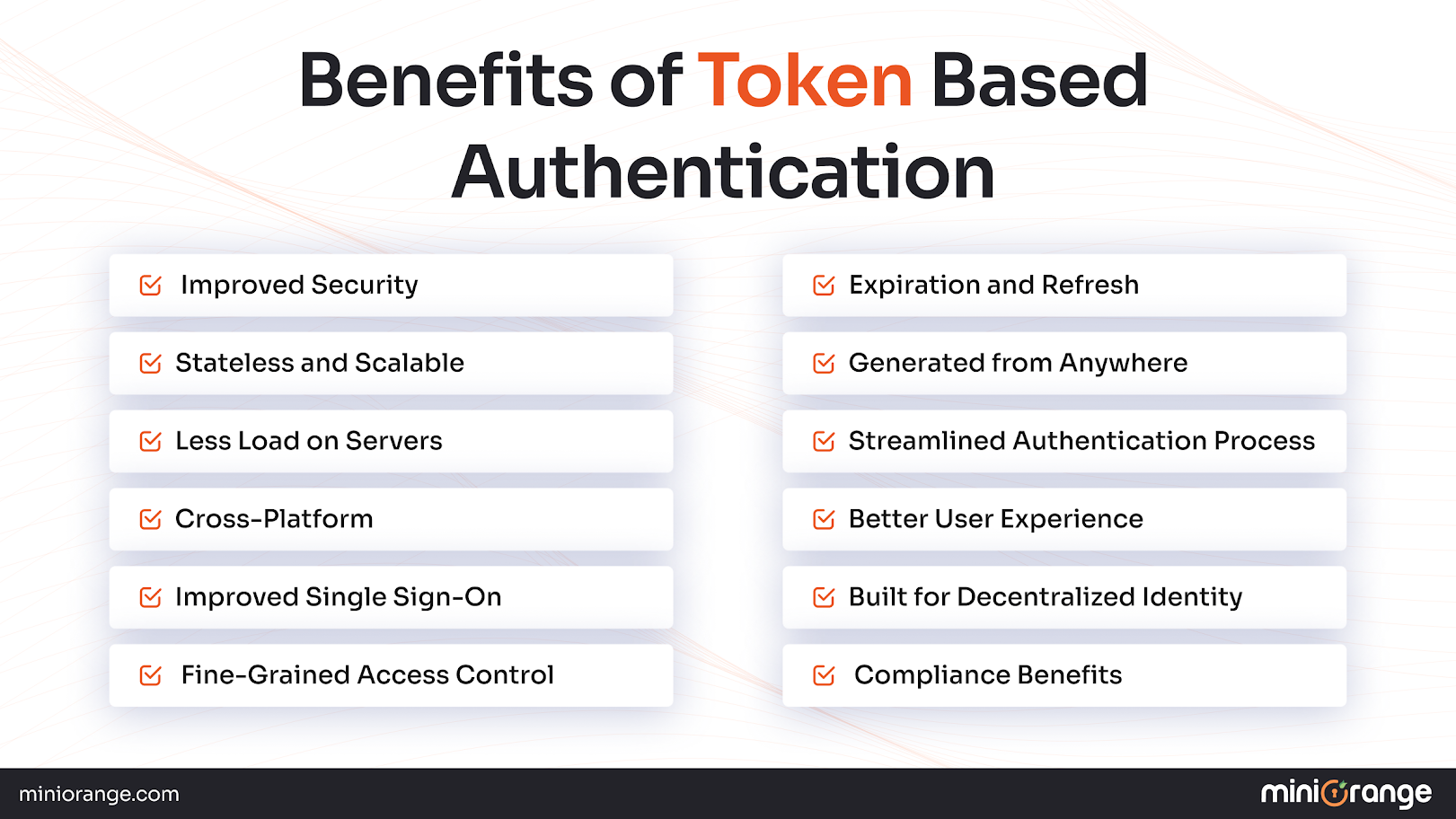
Improved Security
Tokens are lower risk because they do not pass raw credentials with every request. They are complete with encryption, signatures, and expiration, which help diminish the chance of session hijacking and replay, since tokens are not stored on a database.
Stateless and Scalable
Tokens are self-contained packages. Here, the servers for tokens do not need to store session persistence or the ongoing session every time they are in the database. This makes token-based authentication stateless, thus allowing it to scale across multiple servers and cloud environments without any hassle.
Less Load on Servers
Session management takes up considerable server resources. ID tokens can help relieve the server of session management, allowing it to focus on processing acts upon requests.
Cross-Platform
Tokens are universal across browsers, mobile apps, IoT devices, and APIs. They are portable (unlike cookies) across different servers and domains.
Improved Single Sign-On
Token-based authentication simplifies single sign-on. Users can login into an app once to access multiple apps or services within that domain. This simplifies enterprise identity management.
Fine-Grained Access Control
Tokens can carry claims and scopes to further define what a user or app can do, helping to limit access to sensitive resources.
Expiration and Refresh
Tokens can expire quickly in the interest of security or be set for durations that are longer for the interest of user experience. Tokens can have refresh tokens to allow ongoing use without having to log in constantly.
Generated from Anywhere
Tokens can be issued from any web app, mobile app, or identity provider, allowing for flexibility of integration in every system and environment.
Streamlined Authentication Process
Tokens enable less back-and-forth with the server. The handshake is simplified, and once the token is established, requests are faster.
Better User Experience
Users can login into their account once and use the same token across every device and app. This reduces friction and eliminates repeating password prompts.
Built for Decentralized Identity
Tokens can maintain the deciding features of identity without centralized control over access credentials and sessions. They are built for decentralized identity since that is the future of blockchain and Web3.
Compliance Benefits
Additionally, regulations like GDPR and HIPAA encourage tokenization—when a delivery token is passed with a claim, it lessens the risk of exposure of sensitive user data.
How Does Token-Based Authentication Work?
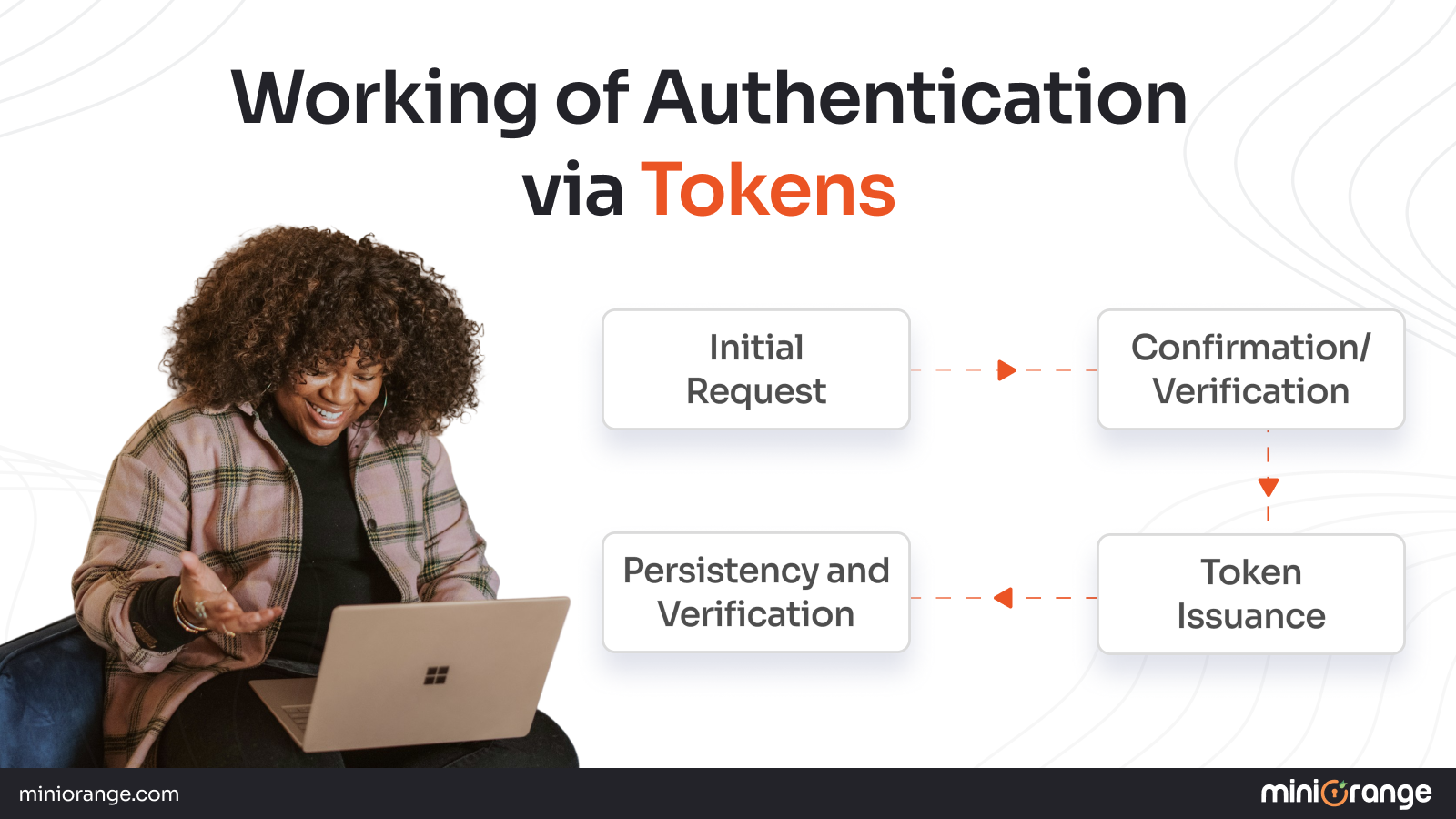
Token-based authentication is a simple but secure exchange. The aim is to verify identity just once and provide tokens to use for other access without repeatedly sending passwords.
Working of Authentication via Tokens
Step 1: The Initial Request
The user or app sends login credentials (username/password, biometric identifier, or an external identity provider) to initiate the authentication.
Step 2: Confirmation/Verification
The server or identity provider verifies the credentials. If the credentials are valid, the user’s identity is confirmed, even with delegated trust through an external identity provider (e.g., Signal OAuth, OIDC).
Step 3: Token Issuance
Once an identity is verified, the system issues a secure token in the form of a JWT. A token carries a set of identity claims, a time period of validity, and permissions encoded in the token. Tokens are either signed or encrypted to limit tampering.
Step 4: Persistency and Verification
The client stores its token in a secured place (e.g., browser storage, device keychain or application memory). The server verifies the token each time the client issues a request, completing permissions or rights verification.
Where Common Standards Fit In
- OAuth (2006): OAuth does access delegation. Instead of sharing your password with someone, you will get an PROTECTED OAuth "Access Token" that will limitedly manage resources.
- SAML (Security Assertion Markup Language): SAML is an XML-based token to implement Single Sign-On (SSO). SAML is widely implemented by enterprises.
- OpenID Connect (OIDC, 2014): OIDC is built on OAuth 2.0 for standardization; OIDC authentication also adds standardized authentication. OIDC is perfect for new web mobile logins.
- CIBA (Client-Initiated Backchannel Authentication): CIBA is an authentication flow for high-trust credentials, like banking. CIBA authenticates the user out-of-band (e.g., push notification without a browser).
- JWT (JSON Web Token, 2010): JWT is a popular access token that is compact, portable, and self-contained. It was introduced to enable authentication data transfer across APIs and distributed systems.
Main Types of Authentication Tokens for Your Business
There are different types of authentication tokens designed for various security and context needs. Here are the types you should be familiar with:
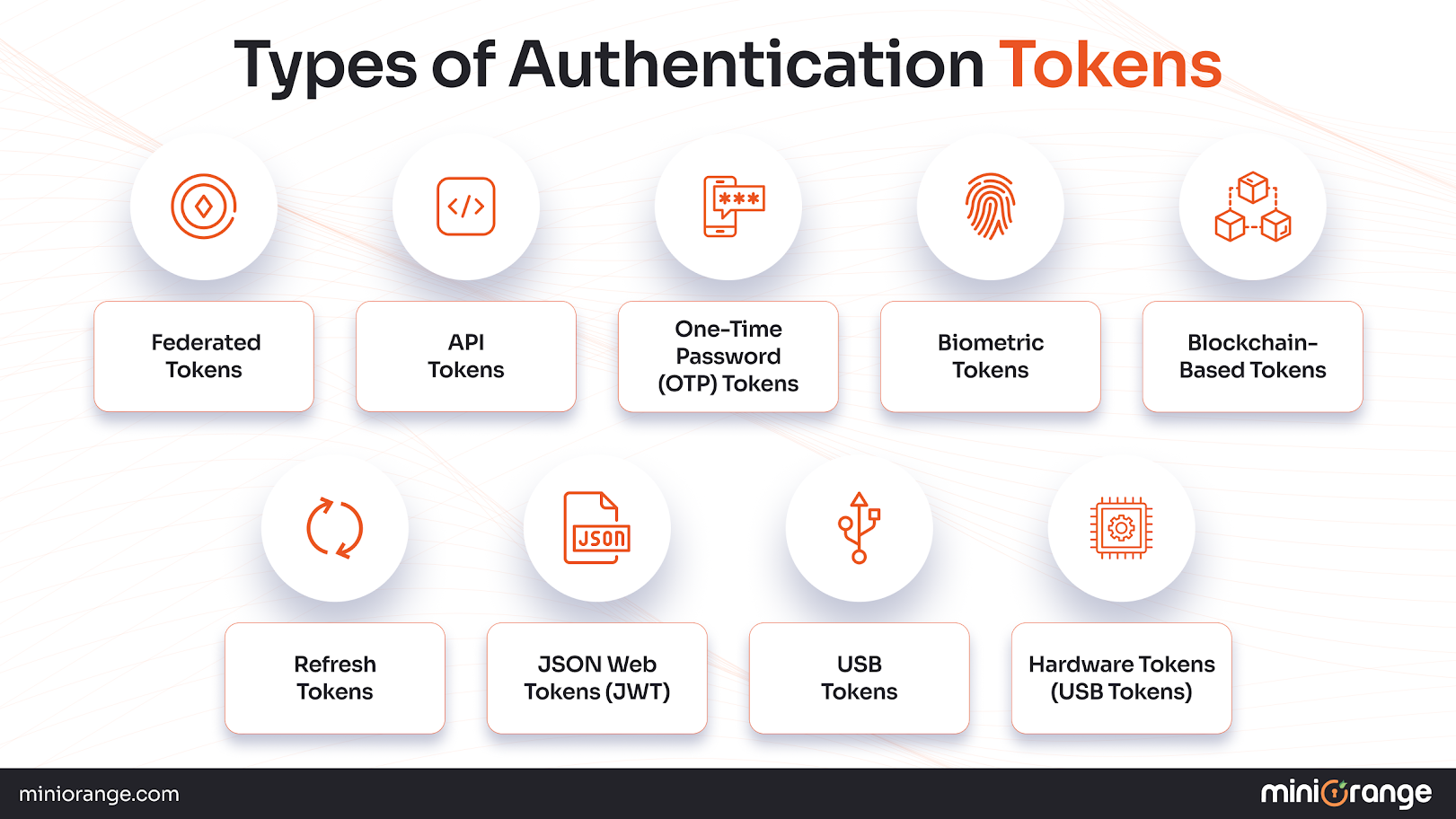
USB Tokens and Others
- Connected tokens enter an instrument to authenticate (the token is typically plugged in via USB).
- Disconnected tokens are capable of generating codes without a physical connection to the instrument.
- Contactless tokens utilize either near-field communication (NFC) or Bluetooth capabilities to communicate, generally used for proximity orientation or mobile authentication.
JSON Web Tokens (JWT)
JWTs are compact, self-contained tokens that are ubiquitous in web and mobile applications. They contain claims in JSON format that are digitally signed to help prevent tampering.
Refresh Tokens
Refresh tokens are used to extend sessions and do not require the user to re-login. Refresh tokens help request new access tokens when existing access tokens expire. This method provides seamless, long-lived sessions.
Federated Tokens
Federated tokens enable users to access applications on behalf of external identity providers, e.g., Google, Microsoft, or Facebook. Federated tokens allow a user to have a single sign-on (SSO) across systems or organizations.
One-Time Password (OTP) Tokens
One-Time Password (OTP) tokens generate codes with a limited lifespan, typically for a single login. OTP tokens can be in the form of per-app (Google Authenticator) or hardware (RSA tokens).
API Tokens
API tokens are used to authenticate apps or services and not people. This type of token secures the service-to-service communication aspect of distributed systems and microservices.
Hardware Tokens (USB Tokens)
Actual physical devices like FIDO2 keys, YubiKeys, or OTP hardware devices (C100, C200, and C300 series) offer strong security for authentication that helps protect against phishing attacks; they need you to have the device on hand because the secret information is safely stored on it.
Biometric Tokens
Biometric tokens authenticate users using personal identifying markers such as fingerprints, voice samples, facial recognition, or iris scans. This type of token provides assurance and convenience because the credential is tied to the user’s body.
Blockchain-based tokens
In decentralized apps, blockchain tokens act as markers of identity. They offer a way to prove identity that can't be easily changed, without needing central organizations or identity providers, and are made to work with the decentralized identity systems of Web3.
Session Tokens vs. Access Tokens
| Feature | Session Tokens | Access Tokens |
|---|---|---|
| Definition | Session tokens are generated by servers with identifiers that map to a user session on the server. | Access tokens are self-contained tokens (like JWTs) that hold the information of user identity and the entitled permissions. |
| Storage | These are stored in server memory or session store. The browser usually holds a session ID in a cookie. | Stored on the client (local storage, memory, or mobile device). |
| State Management | Stateful – server must track and maintain session data. | Stateless – token itself contains all necessary claims. |
| Scalability | Harder to scale because every server must access session storage. | Scales easily across servers and services since no central store exists. |
| Lifespan | Often tied to browser sessions or manually invalidated by the server. | Short-lived by design; renewable with refresh tokens. |
| Use Case | Best for traditional web apps needing simple authentication. | Ideal for APIs, mobile apps, microservices, and zero-trust networks. |
| Cross-Domain Use | Browser cookies restrict usage to a single domain. | Tokens travel easily across domains, APIs, and multiple platforms. |
| Security Risks | Susceptible to session hijacking if cookies aren’t secured. | Susceptible to token theft if stored poorly; mitigated with encryption and short expirations. |
What is Token-based Authentication for Web APIs?
Token-based authentication is the foundation of secure API communications. Instead of passing around passwords, clients use tokens to provide identity and claims of permission. This works for REST APIs as well as some more advanced protocols like GraphQL, WebSockets, and gRPC.
Token Authentication in REST APIs
Tokens travel with each HTTP request in REST. REST APIs tend to include the token in the Authorization header of the request, typically in the form of a Bearer Token. For an API to get access to a protected endpoint, it first validates the token.
GraphQL APIs and Token Auth
GraphQL APIs offer extreme flexibility with queries, and that flexibility may leak potentially sensitive data. Further, tokens embed user roles and scopes for fine-grained access control over GraphQL objects/fields/connections/actions. Tokens also help enforce limits by way of query depths and rate limits to protect the server.
WebSockets Authentication
WebSockets is a stateful protocol with a long-lived connection. Consequently, validation happens at the start of the connection establishment handshake. The client usually sends the access token as part of the connection request. The server validates the access token prior to finalizing or establishing the channel. Tokens could be refreshed on the server while connected to the server to protect against hijacking.
gRPC APIs Token Handling
gRPC uses HTTP/2 for communication, and when clients connect to gRPC APIs, there is metadata passed for token exchange. Access tokens are passed in the metadata for all subsequent calls. This allows for mutual TLS + token-based authentication so gRPC APIs can offer enterprise-grade security in microservices.
How Does Token-based Authentication Work for REST APIs?
Token-based authentication in REST APIs gives each request proof of identity while avoiding session state on the server. The process is simple:
User or App Performs Credential Send
The client (browser, mobile application, or service) sends their identity credentials (username, password, or external identity provider identity) to the API's authentication endpoint.
Server Performs Credential Validation
The REST API, or the identity service it uses, performs the credential validation. If valid, the system issues an access token, often a JWT, that has claims about the user and permissions.
Token Delivered to Client
The server responds to the client with the token. The client then stores it temporarily and securely (local storage for browsers, secure keychain for mobile apps, or memory for backend apps).
Token Sent with Each Request
For every API call, the client adds the token in the Authorization header as Bearer. This provides proof of identity without resending the password.
Server Performs Token Validation
The REST API authenticates the token by validating its signature, expiration, and claims. If valid, access is granted. If expired, or if the signature does not validate, it is rejected.
Token Expiry and Refresh
The lifespan of tokens is limited to reduce the risk of misuse. When the access token expires, the client can potentially use a refresh token (if provided) to request a new token without forcing the user to log in again.
How Does Token-Based Authentication Enhance Multi-Factor Authentication (MFA)?
Multi-Factor Authentication (MFA) protects login access by mandating more than one factor for authentication. Token-based authentication allows for more seamless, diverse, and scalable MFA.
Tokens as a Second Factor
Tokens serve to replace the simplest second factor of secret knowledge, passwords. MFA is a system of providing tokens to users as a second factor. For example, OTP tokens can be either app-based or hardware-based. Users can use an OTP token (one-time password) as an authentication token after entering a password.
Beyond Passwords
Tokens move the MFA authentication process away from secret-knowledge-based passwords. If an outside party steals a password, they cannot access the child's account unless they also acquire the token, which blocks credential stuffing attacks, phishing, and other bad actors.
Biometrics as a Token-Factor
MFA can use biometric data generated by a phone's built-in sensors (i.e., fingerprint or facial recognition). Biometric data can be used to generate or unlock an authentication token. Biometrics on the phone add user convenience but still maintain a connection to cryptographic security.
Tokens used for Push Authentication and Out-of-Band Authentication
Tokens can also create the security connection to push notifications to the user or create a CIBA flow, where a user triggers a login request and a secure token confirmation request is sent to another device in a manner that is secured (an example would be a banking transaction).
Many Token Methods Available for MFA
Using time-based OTP tokens is a great option for MFA since they generate codes across a set time period.
Single-use or hardware tokens (YubiKeys, FIDO2 keys) can serve as a possession-based factor token and leverage the difficulty (human factor) of trying to phish.
JWTs and refresh tokens help streamline repeated MFA "flows" and limit the opportunities for user-experience interruptions.
User Experience Benefits
Using token-based MFA will help minimize login fatigue by authenticating once and then thereafter relying on tokens stored in their devices and other second factors for seamless and secure login access across applications.
MFA + Token Authentication
Multi-Factor Authentication (MFA) becomes far more effective when combined with hardware tokens or token-based authentication, offering a strong alternative to password-only systems. This shift supports a passwordless future, where security is enforced through easy-to-use methods like biometrics and cryptographic tokens. By tying authentication to something the user has (a token or device) and something they are (a biometric), businesses can strengthen protection against phishing while improving convenience across different devices and platforms.
Compared to time-based one-time passwords (TOTPs), which require users to manually enter expiring codes, token-based MFA methods like hardware keys, push notifications, or biometric-triggered tokens streamline the process. They eliminate human error, reduce friction, and provide stronger resistance against credential theft and replay attacks. Since tokens are tied directly to devices or biometrics instead of shared secrets, token MFA not only ensures faster and smoother logins but also delivers a much higher level of security, making it the preferred path forward.
Is Token-Based Authentication Secure?
Token-based authentication can be a secure mechanism if adequate protections are properly implemented. The greatest vulnerabilities are replay attacks (taking someone else's token and reusing it). for access and interception of the token (which is not protected with any encryption protocol) in transit via an unprotected communication channel such as an HTTP connection, or the tokens being retained as credential identifiers in improperly protected client-side storage. As tokens are bearer credentials, whoever possesses the token is granted access to the resources that the token is associated with, so tokens must be well protected.
To maintain reasonable security, ensure that all service calls are done over HTTPS and tokens issued are limited in life (but can be refreshed) and that your keys are rotated regularly. Although tokens are stateless and extend that it is going to be harder to hijack them than cookies in a session, this doesn't eliminate the need for a robust security program. Rather, token-based authentication can be a more scalable and secure solution when achieved in a managed way with an expiry; encrypted in transit; and key rotation, rather than using session-based authentication, which still requires a strong security focus.
Pros and Cons of Software-Based Tokens
A software-based token offers exceptional authentication features—but as always, there are good and bad.
Pros of a Token
- Eliminates the Password: The user is logged in and no longer needs to enter a password and has a much friendlier experience.
- Flexibility and Control: Tokens can carry claims, scopes, and roles, allowing more granular access.
- Security: Tokens significantly reduce the risk of user password exposure, can support encrypted authentication, and encourage a zero-trust model.
Cons of a Token
- Secret Key or Signing Key Exposure: Tokens represent an actual signature for a distinct body of data. So if an attacker has the signing key, then the attacker will be able to provide a valid token (with their own claims).
- Data Overhead: Tokens can be filler—not token filler in the case of a JWT—even very much filler. The larger the token, the more it affects the requests made to the server, which at times increases data overhead.
- Not intended for long-lived authentication: Short expiration times assist in securing tokens but are partially balanced by needing to discover the token in order to revoke it if necessary, as well as refresh workflows on both the client and server.
- Constant Validation: Calling the authentication validation method on every request can make validation and verification needlessly expensive for the server.
Software-based tokens are secure, flexible, and user-friendly, even if there are pitfalls if keys, size, and lifecycle are not well managed.
How to Implement Token-based Authentication for Your Enterprise?
Token-based authentication is ready for the enterprise when the implementation consists of a structured, step-by-step process.
Step-by-Step Token Authentication Flow:
1. User authentication: Client sends credentials (username/password, SSO, or biometric-based) to the auth endpoint.
2. Code verification: The server or IdP verifies the submitted credentials and validates the identity of the user.
3. Token issuance: The system issues an access token (usually a JSON Web Token, or JWT) and a refresh token if desired.
4. Token Storage (Client): Tokens are stored by the client in a safe environment (browser session storage, mobile secure keychain, or in-memory on the backend).
5. Token Transmission: The client attaches an access token in the Authorization: Bearer header for each API call it makes.
6. Token Validation (Server): The server will verify the token signature, claims and expiration.
7. Token Refresh Flow: Tokens should be refreshed with a refresh token, or the user should be prompted for re-authentication.
8. Revoke and Rotate: Support revoking tokens, late binding secret rotation, and auditing any token requests.
Login → Issue Token → Client saves token → client sends token to requests → server validates → access granted/denied
Framework-Specific Things to Consider
- Spring Boot (Java): Use filters/interceptors to validate JWT on each request at the request entry, integrating with spring security.
- Django (Python): Use the Django REST Framework and libraries (JWT or OAuth2 available, like djangorestframework-simplejwt).
- Node.js (JavaScript): Using middleware, such as express-jwt or passport-jwt, decode and validate tokens in your API routes.
- ASP.NET (C#): Enable the JWT authentication middleware and configure the token validation parameters in the Startup.cs or Program.cs files.
Using Identity provider
Enterprises often push the responsibility of issuing and managing token lifecycle to an Identity Provider (IdP):
- miniOrange is an identity provider that helps you have more control over your users using tokens for logging in.
- Auth0 & Okta are both cloud-first IdPs and offer easy integrations to enterprises.
- Keycloak is also considered an IdP; it is an open-source identity and access management solution. It can be deployed on-prem or on a private cloud.
- Azure AD and AWS Cognito are cloud-first identity services, but they are tied into their respective enterprise ecosystems.
- An IdP handles user authentication and provisioning (SSO), federation (using federation-based SSO), MFA, and compliance, while your applications simply receive and validate issued tokens.
Implement token auth using a defined flow, use libraries that are native to your framework for validation, and use an enterprise-grade IdP for scalability, security, and compliance.
How Can miniOrange Help with Token-Based Logins and Their Future?
Hardware tokens are an integral part of the authentication process and they are less prone to misuse and hacks. miniOrange helps you use them as a part of your security control program. Here are some of the future possibilities with hardware tokens to dodge any AI cyber apocalypses:
- Zero-Trust: Tokens verify the request; miniOrange manages zero-trust at scale.
- Decentralized Identity & WebAuthn: Offers support for DID, hardware keys, and biometric token logins.
- AI Detection: AI detects unusual token usage and stops replay or misuse of tokens.
- Passwordless Future: miniOrange powers logins by tokens and biometrics to eliminate password fatigue.
miniOrange enables enterprises to graduate from passwords to secure, zero-trust, AI-first and passwordless token-based ecosystems. Get the miniOrange MFA Software advantage for your enterprise today. Try our state-of-the-art MFA for 30 days.
FAQs
Can tokens replace passwords?
Yes, tokens can function like passwords when authenticating users since tokens can be lock-in-time credentials to establish identity and curb the risk of the credentials being compromised and later exposed.
Which is safer, cookies or tokens?
Generally, token-based authentication is a more secure option than cookie-based authentication for APIs since tokens are not limited by the browser model. Similarly, when using HTTP headers, token-based authentication is even more secure too, while cookies can also be usable with same-origin policies, but cookies are fundamentally susceptible to cross-site scripting and cross-site request forgery attacks.
What makes JWT not secure?
There are plenty of things that can potentially make JWTs unsecure on their own, including unsecure signing algorithms, poor key management, and not properly validating the signature on the token. Any of these misuses can expose sensitive data and allow an application to be exploitable.
Which token format is better for APIs, opaque tokens or JWT?
Opaque tokens are typically the preferred format for tokens used by APIs. Opaque tokens do not disclose internal payload data to reduce the size of the attack surface for exploitation, while JWTs mostly disclose all the internal data and are only secure if the token is encrypted or validated.
Why is token authentication more secure than sessions?
Token authentication can be more secure than sessions because token-based authentication is stateless and not reliant on data as stored by the server; token authentication removes the ability for session hijacking, and tokens can be rotated or revoked simply as possible if compromised.



Leave a Comment