The digital world isn’t just evolving, it’s also under constant surveillance of malicious users and attackers. Every tap, click, or swipe opens doors not only to innovation but also to invisible intruders. With the rise in online activity and interconnected systems, the types of cybersecurity attacks have grown exponentially in numbers.
Cybercrime costs are on the rise. According to Statista’s cybercrime forecast, the global financial impact of cybercrime is projected to increase from $9.22 trillion in 2024 to $13.82 trillion by 2028. From phishing scams targeting everyday users to ransomware attacks on global enterprises, cybersecurity threats are no longer hypothetical; they’re happening in real time. The question isn't if you're at risk, but how much.
Whether you’re asking, “Are we under cyber attack?” or just trying to understand the common cybersecurity threats looming over businesses and individuals alike, this guide is your wake-up call. At miniOrange, we believe that staying informed is the first line of defense. That’s why we’ve curated a comprehensive list of cyber threats from the classics to the emerging, to help you identify, prepare, and protect.
What Are Cybersecurity Threats?
Cybersecurity threats refer to any malicious attempt to access, damage, or disrupt a digital system, network, or device. These threats can come in many forms, ranging from malware and phishing to advanced persistent threats and man-in-the-middle attacks, each posing serious risks to individuals and organizations. The most common cybersecurity threats today target sensitive data, financial information, and operational infrastructure. Whether it is a lone hacker or a state-sponsored entity, the intent remains the same: to exploit vulnerabilities. Understanding the types of cyberattacks and their sources is crucial in building a proactive defense strategy.
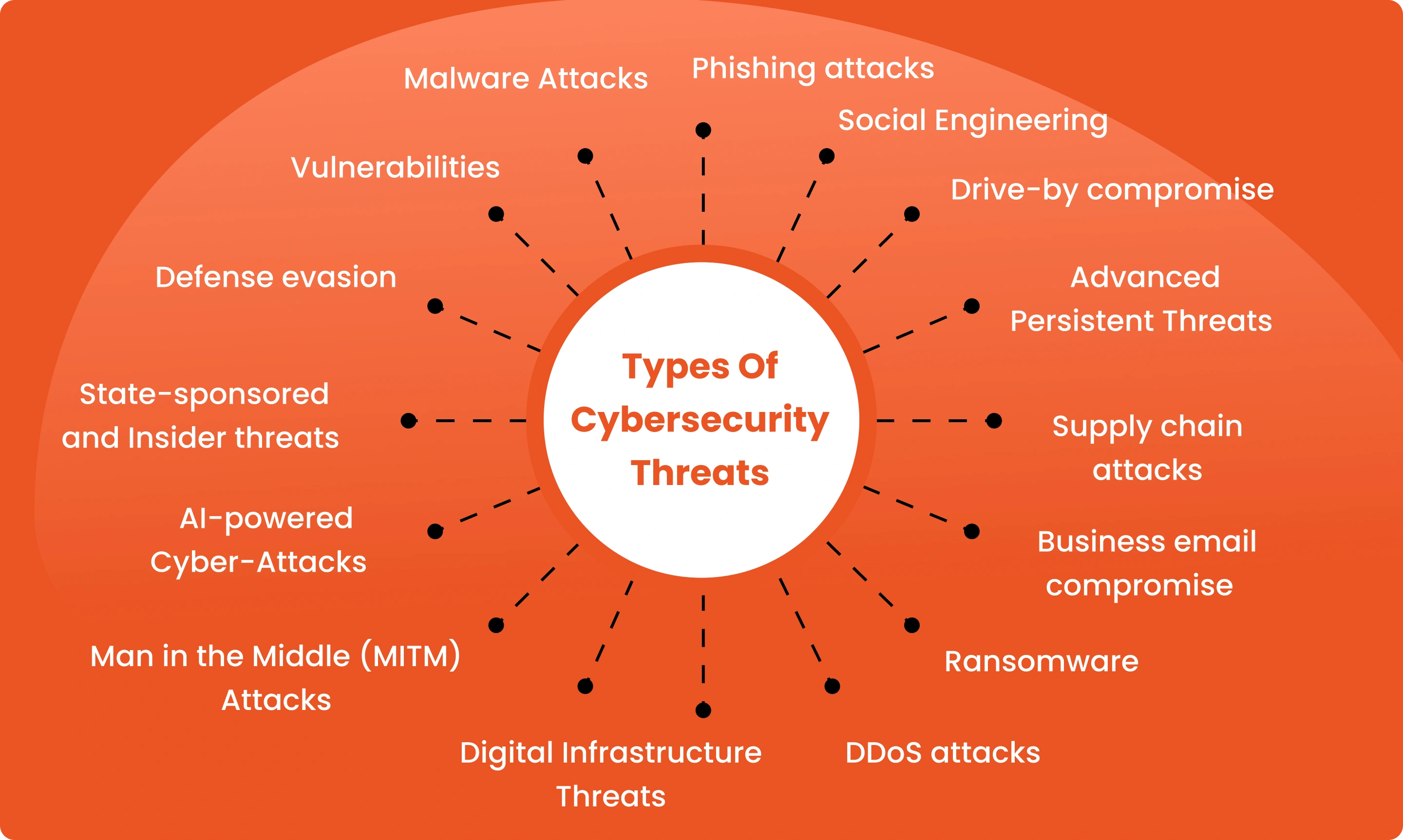
Top 15 Cybersecurity threats
Understanding the types of cybersecurity attacks is critical to building a resilient defense posture. These attacks often exploit human error, software vulnerabilities, or gaps in infrastructure. Below is a curated list of cybersecurity threats that are among the most common and damaging in 2025. Whether you’re an individual, a startup, or a global enterprise, knowing what you’re up against is the first step in safeguarding your digital environment.
1. Phishing Attacks
Phishing is a type of cyberattack where attackers impersonate trusted sources, like banks, colleagues, or well-known services, to trick individuals into revealing sensitive information. These scams usually arrive via email, text, or messaging apps, and often include malicious links or attachments. Once clicked, they can lead to credential theft, financial loss, or even malware infections. Since 2024, phishing tactics have become more advanced and convincing than ever.
Modern phishing attacks now weaponize familiarity. Cybercriminals increasingly exploit popular file-hosting platforms like SharePoint, OneDrive, and Dropbox to disguise malicious intent. As per a report by Microsoft, there has been a significant rise in such campaigns aimed at identity theft, often powered by AI-generated, hyper-realistic emails that easily bypass human suspicion.
How to defend yourself:
- Pause before you click : Always verify the sender’s email address and hover over links to check their destination. If something feels off, don’t engage.
- Enable multi-factor authentication (MFA) : Even if credentials are stolen, MFA can block unauthorized access.
- Use threat-aware email filters : Invest in security tools that scan for suspicious patterns, attachments, and URLs in real time.
- Train regularly, not just once : Simulated phishing tests and periodic awareness sessions keep teams alert and responsive.
2. Vulnerabilities
In cybersecurity, vulnerabilities are the invisible cracks that threat actors are constantly watching for be it outdated software, cloud misconfigurations, or mismanaged devices. These weaknesses, if left unpatched, can open doors to large-scale breaches and operational disruption.
Threat actors are aggressively exploiting unpatched systems, misconfigured cloud environments, and known flaws in popular technologies. For instance, a recent Check Point report highlights the alarming rise of cloud-based threats, urging businesses to prioritize AI-powered and prevention-first security strategies.
Real-World Breaches in 2024:
- A massive data breach at Toyota was traced back to a simple cloud misconfiguration—exposing sensitive information and reinforcing the importance of secure infrastructure.
- Another major incident affected millions of users when AT&T suffered a data breach involving compromised phone records, again linked to exploited vulnerabilities.
Since January 2024, over 84,000 alerts have been recorded related to vulnerabilities in edge devices, making them one of the most targeted components for attackers—particularly within Managed Service Providers (MSPs). This underscores the urgent need for improved visibility and control over an organization's digital environment.
How to Defend:
- Prioritize Patch Management : Regular updates are critical—unpatched systems are often the easiest targets.
- Leverage SIEM and Threat Intelligence : Implement a SIEM solution that continuously monitors and alerts for abnormal activity. Integrate threat feeds to stay ahead of known exploits.
- Embrace Attack Surface Management : Proactively identify and reduce your exposure by:
- Mapping and monitoring your entire digital footprint
- Patching known flaws and removing redundant services
- Applying strict access controls and secure configurations
3. Supply Chain Attacks
Supply chain attacks exploit the trusted connections between organizations and their vendors, software providers, or third-party services, turning those relationships into backdoors for breaching entire networks. Instead of attacking a company head-on, cybercriminals compromise a weaker link in the chain to reach their ultimate target.
And the impact? Staggering.
According to the Identity Theft Resource Center’s 2023 Annual Data Breach Report, supply chain attacks have surged by 2,600% since 2018. In 2023 alone, more than 54 million individuals were affected — a 15% increase year over year.
The financial consequences are just as severe. Industries like aerospace, healthcare, defense, and energy saw an average of $82 million in annual losses per organization, as per the Interos Supply Chain Survey. These attacks not only disrupt operations but also erode trust between partners and clients.
What makes supply chain attacks dangerous?
- They target implicit trust between systems and vendors.
- They often go undetected until widespread damage is done.
- A single compromise can cascade across multiple organizations.
4. Business Email Compromise
Business Email Compromise (BEC) is a targeted cyberattack that manipulates trusted communication channels—most often email, to deceive employees into transferring funds, revealing sensitive information, or granting unauthorized access. What makes BEC especially dangerous is its stealth: it doesn't rely on brute force but on social engineering, trust exploitation, and human error.
The FBI identifies BEC as one of the most financially damaging online crimes, with businesses worldwide facing billions in losses annually.
How Business Emails Get Compromised:
- Phishing: Fraudulent emails mimic trusted sources—banks, suppliers, or executives—to trick employees into sharing login credentials or financial info.
- Malware: Viruses or trojans infect a user’s system, enabling attackers to hijack email accounts and monitor or manipulate communications.
- Social Engineering: Attackers impersonate top executives or IT admins to pressure employees into taking risky actions, like urgent fund transfers.
- Weak Passwords: Reused or easy-to-guess passwords leave email accounts vulnerable to brute-force attacks.
How to Defend Against BEC:
- Educate Employees: Train teams regularly to identify phishing attempts and verify unusual requests, especially those involving money or sensitive data.
- Strengthen Password Hygiene: Enforce strong, unique passwords paired with two-factor authentication (2FA) for all business accounts.
- Update and Monitor Systems: Keep cybersecurity tools and software patches up to date to block malware and known exploits.
- Deploy Email Security Measures: Use advanced spam filters, domain authentication (DMARC, DKIM, SPF), and AI-driven threat detection.
5. State-Sponsored and Insider Threats
In today’s digital landscape, two of the most challenging threats facing organizations are state-sponsored cyber attacks and insider threats. While one strikes from foreign governments with strategic intent, the other originates from within, often leveraging trusted access to inflict damage.
Nation-State Cyber Activities are sophisticated operations driven by political, economic, or military agendas, often involving espionage and sabotage. Backed by substantial resources, these attacks are precise, persistent, and hard to detect.
Insider Threats come from employees, contractors, or partners misusing their access, either maliciously or unintentionally, making them uniquely difficult to identify and control.
For instance:
- Russian government-sponsored groups targeting critical infrastructure in the United States and Ukraine have used malware and DDoS attacks to disrupt essential services and gather intelligence, as highlighted by Stanford’s FSI.
- Chinese cyber units conducting prolonged espionage have exfiltrated trillions worth of intellectual property from major multinational corporations, as reported by CBS News, focusing on long-term strategic gains.
How to Defend:
- User and Entity Behavior Analytics (UEBA): Identify anomalies in user behavior that may signal malicious activity.
- Access Control & Least Privilege: Limit user access to only what is essential for their role.
- Ongoing Audits & Security Training: Regular internal audits and targeted training help employees recognize risks and act responsibly.
Mitigation Strategies:
- Against nation-state threats: Strengthen your geopolitical threat posture, incorporate threat intelligence feeds, and establish cross-border cybersecurity collaborations.
- Against insider threats: Implement Data Loss Prevention (DLP) tools, enforce strict access policies, and ensure your incident response strategy includes insider scenarios.
6. Ransomware
Ransomware remains one of the most disruptive cyber threats today—crippling hospitals, halting businesses, and breaching government systems. By encrypting critical files and demanding payment for their release, attackers hold data hostage, often causing massive financial and reputational damage.
2024 Spotlight:
The Change Healthcare ransomware attack marked the biggest breach of US medical data in history, compromising the sensitive information of 190 million individuals.
Meanwhile, authorities struck back—2024 also saw the FBI seize servers and release over 7,000 decryption keys from the notorious Lockbit ransomware group, disrupting one of the world’s most active Ransomware-as-a-Service (RaaS) operations.
Adding to the threat landscape is the rise of data extortion without encryption. Groups like RansomHub now steal confidential data and threaten to leak it, bypassing traditional ransomware detection tools altogether.
The financial impact? Ransom demands are skyrocketing. The average ransom fee surged by 500% last year, according to Sophos, underlining the growing financial pressure ransomware places on businesses.
How to Defend Against Ransomware:
- Perimeter & Endpoint Security: Stop ransomware at the gate and at the device level.
- Network & Data Protection: Monitor traffic for anomalies and encrypt sensitive data.
- System Hardening & Regular Patching: Eliminate vulnerabilities before attackers find them.
- Multi-Factor Authentication (MFA): Add friction to prevent unauthorized access.
- Managed Security Services: Outsource monitoring to catch and respond to threats faster.
7. Defense Evasion
Defense evasion refers to the stealth tactics cybercriminals use to bypass detection and stay under the radar. Instead of brute-forcing their way in, attackers disguise their presence, often using sophisticated methods to blend into legitimate system activity, allowing them to lurk undetected for days, weeks, or even months.
These techniques include: Obfuscating malicious code to prevent detection by antivirus tools. Disabling or bypassing security controls, like EDR or firewalls. Masquerading as legitimate processes to avoid triggering alerts.
This hidden persistence often leads to data exfiltration, credential theft, or ransomware deployment, all while security teams remain unaware.
How to Defend Against Defense Evasion:
- Behavior-Based Detection: Go beyond signatures—use tools that monitor for abnormal patterns, not just known malware.
- Endpoint Detection and Response (EDR): Implement solutions that provide real-time visibility and automated responses.
- Application Whitelisting: Allow only approved programs to run, reducing the chance of malicious code executing undetected.
- Regular Security Audits: Review system logs and configurations to uncover signs of hidden activity.
8. Malware Attacks
Malware, short for malicious software, is a broad category of cyber threats designed to infiltrate, damage, or disrupt systems without the user’s consent. From viruses and worms to trojans, spyware, and rootkits, malware can silently breach defenses, steal sensitive data, hijack operations, or crash entire networks. It can spread widely and act as a precursor to larger attacks, including credential theft, surveillance, or lateral movement within networks. Malware remains one of the most versatile and persistent tools in a hacker’s arsenal.
Today, malware is becoming increasingly sophisticated, with AI powering its ability to evade detection and adapt to security measures. In fact, 60% of IT professionals globally now consider AI-enhanced malware their top cybersecurity concern.
How to Defend Against Malware Attacks:
- Real-Time Threat Detection: Use antivirus and EDR tools that scan for both known signatures and suspicious behaviors.
- Regular Software Updates & Patch Management: Close vulnerabilities that malware commonly exploits.
- Secure Web & Email Gateways: Filter out malicious content before it reaches endpoints.
- Network Segmentation: Isolate sensitive systems to limit malware spread.
- Employee Training: Teach users how to identify suspicious files, links, or downloads.
9. Drive-By Compromise
Drive-by compromise attacks occur when users unintentionally visit compromised websites that automatically download and install malware without their knowledge. These attacks exploit browser vulnerabilities and require no user interaction beyond visiting the malicious site. Keeping software updated and using reputable security tools can mitigate such risks.
10. DDoS Attacks
Distributed Denial-of-Service (DDoS) attacks aim to overwhelm a target's servers or networks with excessive traffic, rendering services unavailable to legitimate users. By leveraging botnets, networks of compromised devices, attackers can disrupt operations, causing reputational and financial harm. Implementing traffic filtering and redundancy can help defend against DDoS attacks.
11. Social Engineering
Social engineering attacks manipulate human behavior rather than exploiting technical flaws. Cybercriminals use deception, urgency, and trust to trick individuals into revealing confidential information, clicking malicious links, or granting unauthorized access—all without breaching a single firewall.
What makes social engineering so dangerous is its simplicity and success rate. It’s easier to fool a human than break into a secured network. According to Verizon’s 2024 Data Breach Investigations Report, 68% of all data breaches involve some form of non-intentional human interaction, reinforcing just how crucial this threat vector has become.
Common Social Engineering Techniques:
- Phishing: Fraudulent emails, texts, or DMs posing as trusted sources to steal login credentials or financial data.
- Spoofing: Attackers imitate official email addresses or websites with slight alterations to deceive users.
- Whaling: Targeted phishing attacks aimed at executives or high-level personnel, often seeking wire transfers or classified information.
- Baiting: Fake offers or freebies trick users into downloading malware or entering personal information.
How to Defend Against Social Engineering:
- Employee Awareness Training: Make users the first line of defense with regular training and simulated attack scenarios.
- Email & Web Filtering: Block suspicious domains and filter malicious content before it reaches the user.
- Verification Protocols: Encourage verification of unexpected requests, especially those involving data or money transfers.
- Incident Response Playbooks: Incorporate procedures to detect and respond swiftly to social engineering attempts.
12. Man-in-the-Middle (MITM) Attacks: The Silent Interceptor
Man-in-the-Middle (MITM) attacks occur when a cybercriminal secretly intercepts the communication between two parties, without either side realizing the conversation has been compromised. This allows the attacker to eavesdrop, steal sensitive information, or even alter the content of the communication in real time.
MITM attacks are especially common on unsecured public Wi-Fi networks, where data like login credentials, financial details, or confidential files can be hijacked in transit.
How to Defend Against MITM Attacks:
- Use Encryption: Always use HTTPS-enabled websites and incorporate strong encryption protocols to secure communications.
- VPN Usage: Encrypt internet traffic using a Virtual Private Network (VPN), especially on public or untrusted networks.
- Certificate Pinning & TLS: Ensure proper certificate validation and enforce transport layer security for apps and web services.
- Avoid Public Wi-Fi for Sensitive Transactions: Educate employees to avoid logging into business platforms over open networks.
13. Advanced Persistent Threats (APTs): The Long Game of Cyber Espionage
Advanced Persistent Threats (APTs) are stealthy, sophisticated cyberattacks where intruders infiltrate a network and remain undetected for extended periods. Unlike smash-and-grab cybercrime, APTs are patient and persistent, designed for long-term surveillance, data theft, or sabotage.
These attacks are often state-sponsored and typically target high-value entities like government agencies, defense contractors, and large enterprises. APTs move laterally across networks, escalate privileges, and exfiltrate sensitive data, often without triggering traditional security alerts.
How to Defend Against APTs:
- Continuous Network Monitoring: Detects subtle anomalies and long-dwell-time behaviors.
- Threat Intelligence Integration: Incorporate advanced threat feeds and behavior analytics to flag early indicators.
- Zero Trust Architecture: Validate every user and device, regardless of location or role.
- Incident Response Readiness: Ensure teams are prepared with playbooks and simulations to respond to covert threats.
14. Digital Infrastructure Threats
As our dependence on technology grows, so does the attack surface of digital infrastructure. Power grids, transportation systems, communication networks, and cloud ecosystems are now deeply interconnected and increasingly under threat.
Cyberattacks on digital infrastructure can lead to massive service outages, data breaches, and even national security risks, making them some of the most high-stakes cyber threats in existence.
A major driver of this expanding risk is the Internet of Things (IoT). These smart, connected devices, from industrial sensors to smart meters, are often shipped with weak security protocols or insecure firmware, creating easy entry points for attackers. According to Statista, the number of IoT-connected devices will soar to over USD 32.1 billion by 2030, nearly doubling from 2023 levels, exponentially increasing the risk landscape.
Real-World Threat Scenarios:
- IoT-powered botnets are used in large-scale DDoS attacks targeting essential services.
- Cloud misconfigurations expose sensitive business or government data.
- Supply chain compromises cascade through transportation, healthcare, and energy sectors.
How to Defend Digital Infrastructure:
- Secure IoT Environments: Incorporate firmware updates, replace default credentials, and segment networks to isolate vulnerable devices.
- Cloud Security Posture Management: Continuously monitor configurations, enforce access controls, and train teams on best practices.
- Supply Chain Risk Management: Vet all third-party vendors, enforce strict cybersecurity compliance, and embed security into contractual agreements.
- Cross-Sector Collaboration: Encourage real-time information sharing across public and private sectors to tackle infrastructure-wide vulnerabilities.
15. AI-Powered Cyber-Attacks
Artificial Intelligence has become a double-edged sword in cybersecurity. While it strengthens defenses, it also empowers attackers with faster, smarter, and more targeted attacks. AI-driven threats use machine learning to exploit vulnerabilities and automate phishing, ransomware, and deepfake-based attacks at scale.
According to a 2023 survey, 85% of cybersecurity professionals believe AI is a key driver behind the rise in attacks. As phishing scams grow more personalized and believable, 95% of businesses agree they’re harder to spot than ever.
But AI isn’t just a threat, it’s also part of the solution. Tools like IBM’s AI threat detection systems are helping organizations stay ahead of the curve with smarter, faster, and more proactive protection.
How to Defend Against AI-Driven Threats:
- Incorporate AI into Security Systems: Use AI-powered tools for anomaly detection, behavioral analytics, and automated threat response.
- Enhance Phishing Detection: Train systems and users to spot AI-generated phishing content and impersonation attempts.
- Red Teaming with AI: Simulate attacks using generative AI to discover system weak points before attackers do.
- Ongoing Employee Awareness: Ensure teams are educated on the evolving nature of AI threats and know how to react in real-time.
How miniOrange Helps Protect Against Cybersecurity Threats
Authentication is one of the most critical layers in any cybersecurity strategy. When implemented correctly, it acts as a gatekeeper, preventing unauthorized access, blocking credential-based attacks, and reducing the impact of breaches. In today’s landscape, where phishing, ransomware, insider threats, and supply chain attacks are growing more sophisticated, strong authentication is not optional—it’s foundational.
miniOrange MFA Solution
Multi-Factor Authentication (MFA) adds an extra layer of security beyond passwords, requiring users to verify their identity using two or more independent credentials. The miniOrange MFA Product offers flexibility with biometrics, OTPs, mobile authenticators, and push notifications, ensuring secure access without sacrificing user convenience. This helps mitigate threats like phishing, credential stuffing, and man-in-the-middle attacks by making stolen passwords useless on their own.
miniOrange 2FA Tool
Two-Factor Authentication (2FA) is a simplified yet powerful subset of MFA that provides a significant security boost. With the miniOrange 2FA, organizations can quickly implement 2FA across cloud and on-premise applications. It’s lightweight, easy to deploy, and essential for defending against brute-force and unauthorized access attempts, especially in environments with remote workers and third-party vendors.
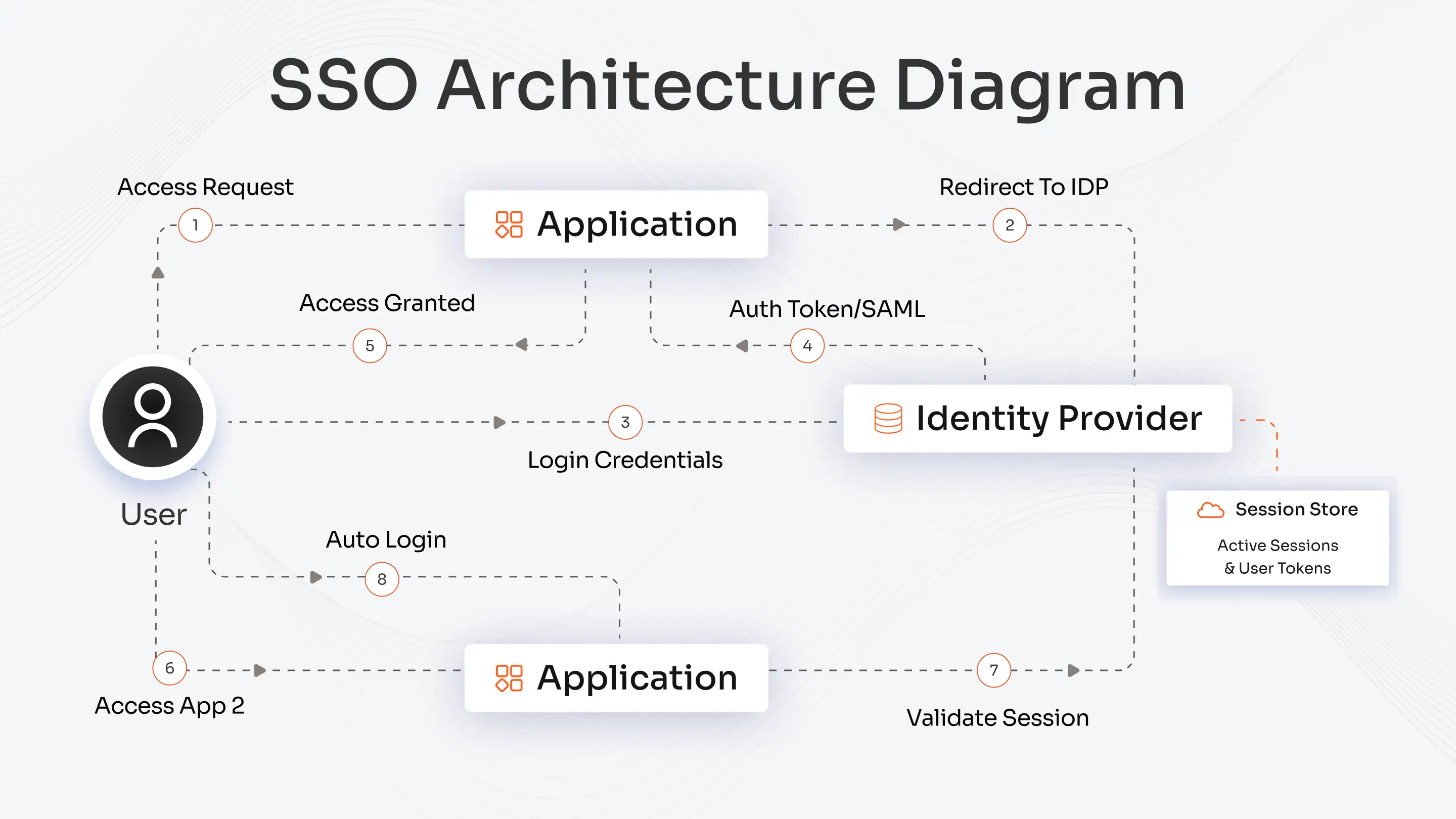
miniOrange SSO Solution
Single Sign-On (SSO) streamlines user access by enabling them to log in once and access multiple applications without re-entering credentials. While it simplifies the user experience, it also reduces password fatigue and centralizes security enforcement. The miniOrange SSO Solution integrates seamlessly with identity providers and business apps, minimizing the attack surface and ensuring consistent authentication policies across the board.
miniOrange PAM Tool
Privileged Access Management (PAM) is vital for securing access to critical systems and sensitive data. The miniOrange PAM Product ensures that privileged accounts are tightly controlled, monitored, and audited. It includes features like password vaulting, session monitoring, and granular access control, helping businesses detect and block insider threats and misuse of elevated permissions before damage is done.
Conclusion
In an era where cyber threats are not just probable but inevitable, staying one step ahead is essential. From phishing attacks to AI driven breaches, the cybersecurity landscape is evolving faster than ever. That’s why understanding authentication and adopting modern methods like WebAuthn is critical to maintaining security.
At miniOrange, we provide the tools and technologies to help you stay resilient, compliant, and secure. Whether you’re an enterprise managing thousands of identities or an individual user, about MFA, it’s more than just a buzzword. It’s your front line of defense. Start your 30-day free trial today and explore how our MFA, SSO, PAM, and 2FA solutions can fortify your digital ecosystem. Got questions or need a custom security plan? Contact us, we’re here to help.
FAQs
Are we under cyber attack today?
Yes, we are always under some form of cyber attack. The digital ecosystem is constantly exposed to threats like phishing, ransomware, malware, and DDoS attacks, many of which operate silently in the background. Even if your business hasn’t faced a direct breach, chances are your data, systems, or networks are being scanned for vulnerabilities right now. This is why real-time threat monitoring, firewall protection, and multi-factor authentication (MFA) are critical components of a strong cybersecurity strategy.
What’s the difference between types of cyberattacks and cyber threats?
A cyber threat is the possibility of a malicious attempt to exploit a system, while a cyberattack is the execution of that threat. For example if phishing emails, zero-day vulnerabilities, or unpatched software flaws are the threats, then when an attacker uses them to steal data or disrupt services, that’s a cyberattack. Understanding both is essential for building a proactive cybersecurity defense, including using Privileged Access Management (PAM) and threat detection systems to reduce your attack surface.
How do I know if my business is being targeted?
Cybercriminals work silently, but signs like failed logins, network slowdowns, unusual traffic, and phishing attempts can indicate a threat. Tools like UBA, SIEM, and endpoint monitoring help detect these early. Adopting advanced cybersecurity solutions can stop threats before they escalate.


Leave a Comment