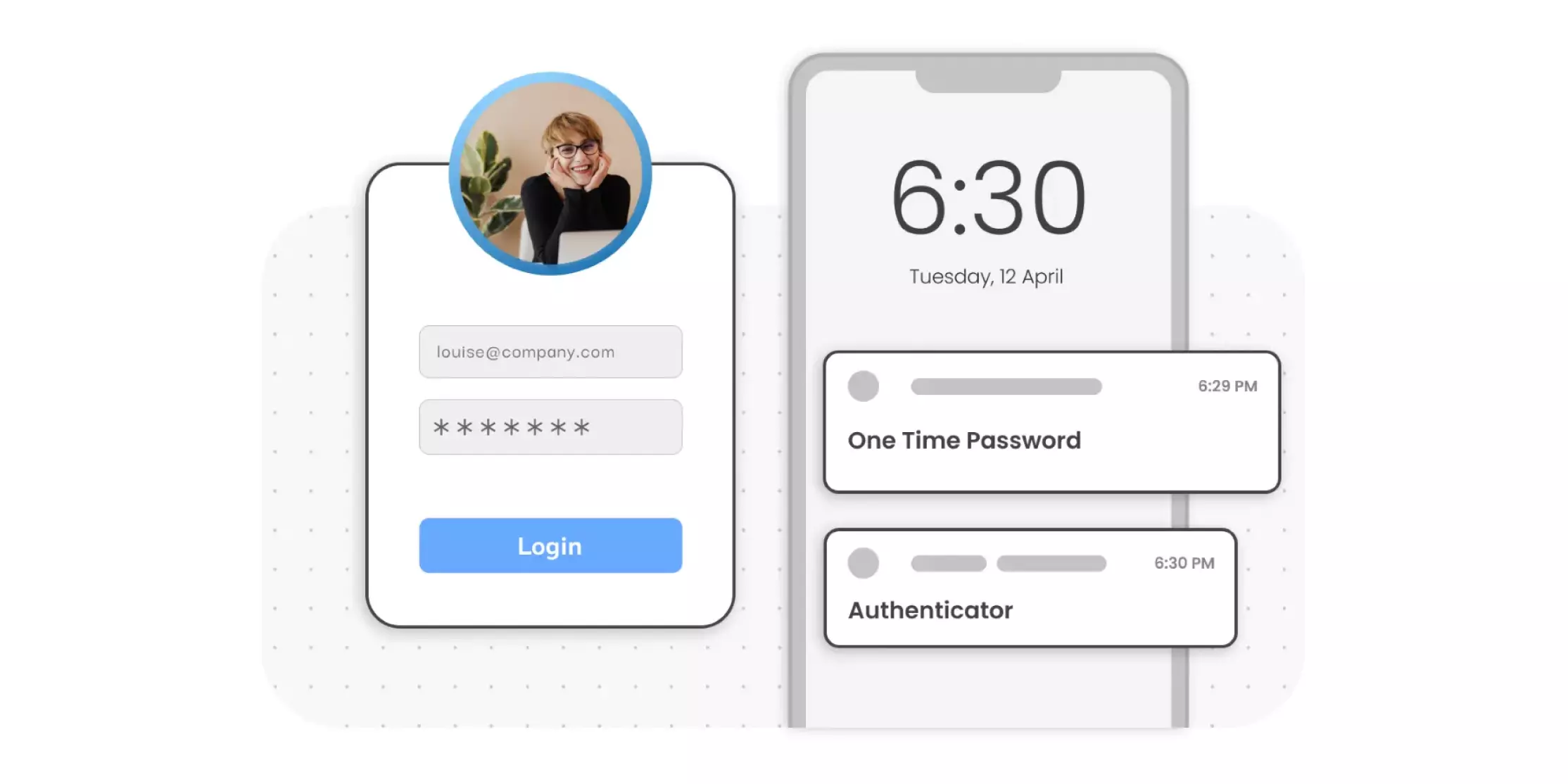
Multi-Factor Authentication (MFA) is an authentication method that requires the user to authenticate themselves for two or more factors, in order to gain access to company resources, applications, or a VPN. Enabling Multi-Factor Authentication (MFA) means that users need to provide additional verification factors apart from their username and passwords. These second-factor methods can range from OTP over SMS, OTP over Email, Push notification, Google/Microsoft authenticator, and many more.
Having this extra layer of security ensures that the information being accessed is well protected from activities such as phishing, malware, hacking, and many more. Having a strong MFA setup ensures a robust Identity and Access Management (IAM) for your organization and secures your resources.
The goal of leveraging MFA is to boost security and make a layered defense so that even if one factor (username-password) is stolen or a targeted cyber attacker still has at least one more barrier to breach before successfully breaking into the actual targeted device. The second barrier is also usually harder to breach as compared to simple username passwords.
Why use Multi-Factor Authentication (MFA)?
Passwords might be one of the supreme measures we use on a daily basis but what the newest cyber threat reports depict has raised concern regarding security issues. Regardless of how complex your password or the password management system is, it is never enough to prevent account takeover because all it takes is one simple phishing email or database breach and your password is out in the world.
Users also make it easier for hackers by choosing weak passwords, using the equivalent password for multiple applications, storing passwords in insecure locations and keeping the same password for long periods of time. These practices may help users remember their login credentials, but they invite hackers in through the front entrance.
The 2019 Data Breach Investigations Report found that 81 per cent of account breaches could be put right down to passwords that were either leaked or passwords that were easily feasible and approximately weak (e.g., “passw0rd, admin”).
- 92% of organizations have credentials for sale on the Dark Web.
- 81% of data breaches are the result of weak or stolen passwords.
- 90% of passwords can be cracked in less than six hours.
These all factors sum up the solution to why you ought to have an MFA as your daily asset whether it’s a corporation, institution, or any company. By combining your username and password with Multi-Factor Authentication methods your access becomes safer and impossible for an attacker to pass it even if they have your password.
How does MFA Work?
MFA works very well for improving security – the numbers don’t lie.
Here’s how it works:
As the user attempts to gain access to a specific resource, they are prompted with multiple authentication factors, instead of only one. The user credentials are then verified by a core identity provider (IdP) or directory services platform. Once authenticated, the user gains access to the requested resource.
The most common MFA systems use a unique one-time passcode commonly known as OTP with every login attempt that you simply make. miniOrange also provides a more modern and secure sort of MFA which is a “Push notification” on your smartphone. A push notification is sent to your registered smartphone and in order to gain access to your account, you’ve got to approve that notification. You can also use a hardware token to gain access to crucial resources using tokens such as Yubikey, or soft tokens via Google/Microsoft/miniOrange authenticator app.
Multi-Factor Authentication Methods
[MFA Authentication] (https://www.miniorange.com/products/multi-factor-authentication-mfa-methods) is based on various authentication factors. Multi-Factor Authentication takes the help of these factors to authenticate a particular individual.
- Knowledge Factor is something that a user remembers like “First Password”, “First School Name”, “A Pin” etc.
- Possession Factor is something the user has, such as a mobile device, smartphone app, or security token to approve authentication requests.
- Inherence Factor mainly referred to as a biometric factor, is something different in the user’s physical self. These could also be personal attributes like fingerprint, retina, or voice.
- Location factor usually denotes the location from which an authentication attempt is being made. Location-based MFA methods can limit user access when a user breaks out from the given location. Location-based MFA can also limit the authentication attempts made by the user to specific devices by tracking their Internet Protocol (IP).
- Time factor restricts user authentication to a specific time panel in which logging on is granted and restricts access to the system outside of that window. In simpler terms, we called it Time based OTP (TOTP). Mobile Apps like Microsoft Authenticator, Google Authenticator and miniOrange authenticator provide a key code that’s time-dependent up to limited seconds.
Multi-Factor Authentication Vs Two Factor Authentication
The major difference between 2FA and MFA is: In https://www.miniorange.com/two-factor-authentication-(2fa) there are only two authentication methods: one traditional username-password and another one like (OTP, Push notifications). While in MFA there are no such restrictions, you can opt for multiple authentication methods according to your way.
Challenges of Multi-Factor Authentication
Users who have to remember multiple passwords will find it difficult to use MFA if they add security features. MFA aims to simplify MFA for users. These are some main approaches to simplifying MFA.
Adaptive MFA
This applies business rules and policies to user-based elements such as location or device. A corporate VPN may know that a user can sign in from their home, seeing their location and assessing the risk of misuse or compromise. An employee accessing the VPN through a coffee shop can trigger the system and will be required to enter MFA credentials.
Push Notification
This method allows the security system to issue a third, single-use ID code to the user’s smartphone. To access a secure system, users can enter their user ID or password. A security system will then issue a third single-use code to their mobile devices. To gain access, users must enter the code into the system. Push authentication makes MFA easier by giving users the third code. This eliminates the need for them to remember it.
Multi-Factor Authentication Use Cases
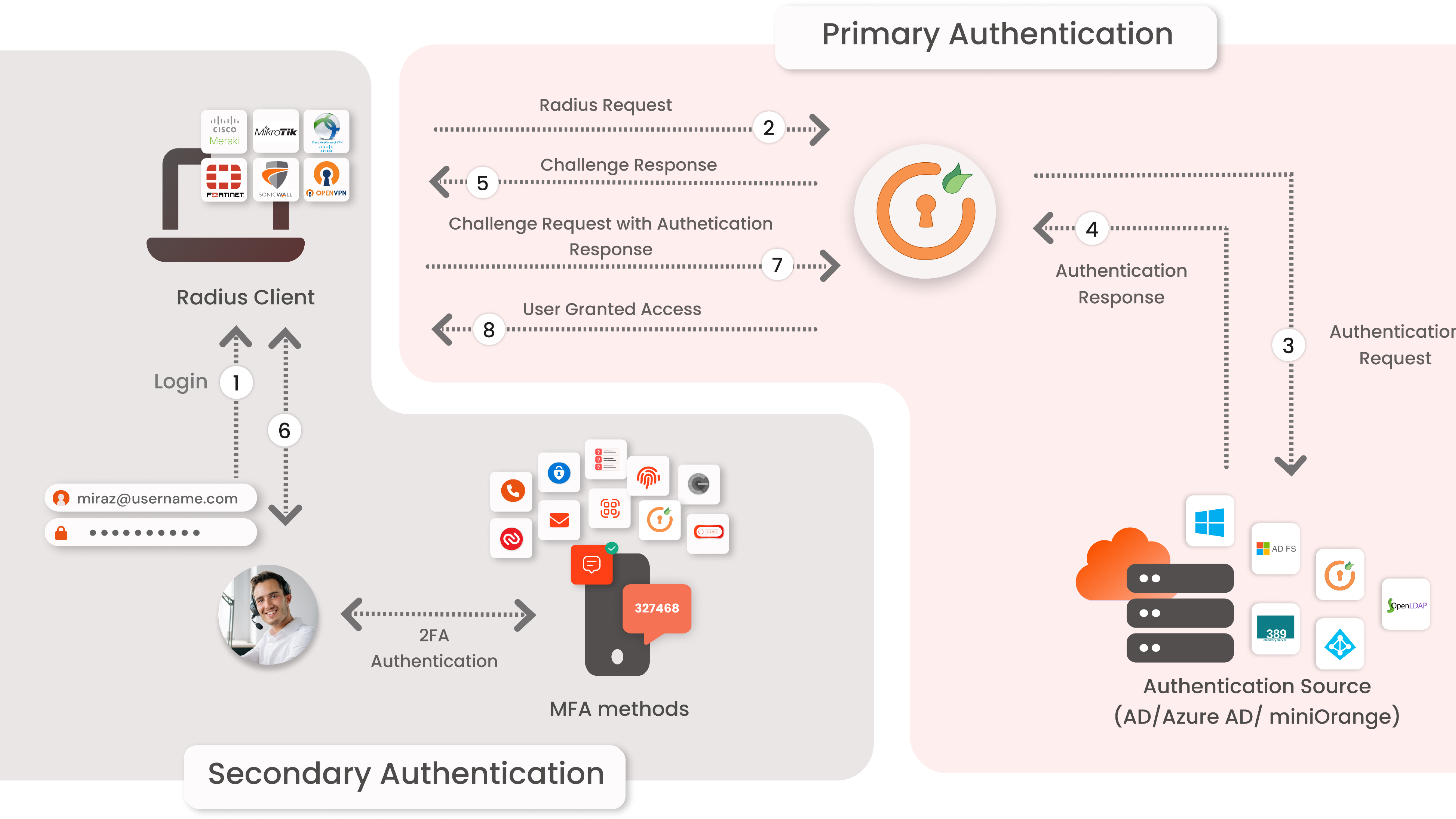
miniOrange provides Multi-Factor Authentication (MFA) on top of VPN Authentication. This secures access to protected resources rather than counting on only the VPN username & password. To accomplish this miniOrange uses the RADIUS Protocol.
RADIUS stands for Remote Authentication Dial-In User Service, it’s a client/server protocol that gives client authentication and authorization.
The RADIUS server is liable for authenticating the users, while RADIUS clients are nothing but the Network Access Servers (NAS) which authenticate users with RADIUS servers and support responses from the RADIUS server to grant/deny the access.
MFA for Office 365
Microsoft provides MFA only via their default application with limited MFA methods and you can not configure any additional MFA authentication method. In some cases, you need to spend an enormous amount for licensing and user differentiation, and if you need to activate or deactivate for the particular user you have.
If you are looking to use Yubikey or any other hardware token as an authentication method while accessing Office 365, it’s supported by miniOrange and can be integrated quickly.
miniOrange MFA integration for Microsoft Applications allows you to use Yubikey (or the other method from 15+ available MFA methods) as the multi-factor to login into your Office 365 or any of your Microsoft Applications.
MFA for Virtual Desktop Infrastructure
Virtual Desktop Infrastructure offers a complete solution for managing and providing access to virtualized desktop environments hosted in the data centre.
MFA for Virtual Desktop Infrastructure enables organizations to securely simplify administration, reduce operating costs, increase the utilization of existing IT assets, and boost security by moving on from a vulnerable traditional desktop environment to MFA enabled VDI.
MFA for Web Apps
Our MFA can be enabled for any of your web apps anywhere on the internet, to ensure a secure and efficient way of accessing your critical resources.
Benefits of MFA
Enhanced Security
Multi-Factor Authentication (MFA) decreases the probability that an attacker can mimic a user and may gain access to the system. miniOrange Multi-Factor Authentication (MFA) solution allows users to log in using Username and OTP thus, preventing the necessity to enter the Password.
More Productivity and Flexibility
Organizations are accepting mobility because it helps in increasing productivity. With mobile MFA employees can securely login and access corporate applications and resources from virtually any device and from any location, without putting the corporate network to risk.
Fraud Prevention
Multi-Factor Authentication verifies who you say you’re before letting you progress forward. It prevents unauthorized access to your website by providing a further layer of authentication.
Improved Customer Trust
Multi-factor authentication (MFA) provides a layer of protection to your enterprise and your customers. It protects consumer data from identity theft. Therefore, companies that store consumer information should consider more than one authentication. This will allow them to build and maintain customer trust.
Reduced Operating Costs
Implementing MFA reduces the probability of data breaches, resulting in reduced investment.
Further Reading
Author