If a hacker is eavesdropping on your private conversations, capturing sensitive data like passwords, financial information and trade secrets, it causes identity theft, unauthorized accesses and some of the most targeted phishing and social engineering attacks. Lost information through compromised channels is a man-in-the-middle attack (MITM) that further results in intellectual property theft, legal liabilities and lasting, irreparable reputational damage.
The most common types of MITM attacks are ARP spoofing, DNS spoofing, wifi eavesdropping, session hijacking, SSL hijacking and email hijacking. In this article, you will understand how to detect and prevent MITM attacks and learn some examples along the way and how miniOrange helps stop MITM attacks.
What is a Man-in-the-Middle (MITM) Attack?
Under a man-in-the-middle (MITM) attack, cybercriminals surreptitiously intercept and alter messages between two people thinking they are directly connected. Operating as a covert eavesdropper, the assailant gathers private messages, credit card information, passwords, and sensitive data. They take advantage of security flaws by means of SSL stripping, DNS spoofing, and evil twin Wi-Fi networks.
These covert strikes let hackers watch activity, gather data undetectably, and add harmful stuff. Understanding these risks enables people and companies to put more robust cybersecurity systems into use.
Man-in-the-middle Attack Techniques
From ARP poisoning and DNS spoofing to SSL stripping and session hijacking, explore the strategies behind man-in-the-middle attacks that let attackers intercept and control data.
IP Spoofing:
By misrepresenting the sender's IP address in data packets, IP spoofing fools your computer into thinking dangerous traffic comes from a trusted source. Attackers create the source IP address to fit websites, genuine servers, or network equipment victims routinely interact with. By masking their actual name and location, this method avoids simple security filters and lets attackers collect sensitive data, reroute traffic to hostile services, or start distributed denial-of-service attacks.
DNS Spoofing:
DNS spoofing alters domain name system replies to send users from reputable websites to attacker-owned servers undetectably. When consumers enter trustworthy website URLs, hackers hijack DNS servers or poison DNS cache entries to provide fake IP addresses. While really connecting to identical-looking phony websites meant to gather login credentials, personal information, and financial data, victims assume they are accessing their bank, email provider, or social media platform.
HTTPS Spoofing:
Fake secure connections created by HTTPS spoofing show valid security indications while really running under attacker control. To create encrypted connections that seem safe to consumers, cybercriminals exploit compromised certificate authorities, false SSL certificates, or browser vulnerabilities. Particularly risky for online banking, shopping, and confidential corporate communications, this advanced method lets attackers grab data that consumers assume stays covered by HTTPS encryption.
SSL Hijacking:
SSL hijacking intercepts and takes over established safe sessions between users and websites, therefore leveraging active SSL/TLS connections. Attackers set themselves between victims and authorized servers then grab and play session cookies or login tokens to keep illegal access. Bypassing conventional login security mechanisms, this method lets attackers pretend to be verified users, access protected accounts, and execute financial transactions or data theft.
SSL Stripping:
SSL stripping downgrades safe HTTPS connections to unencrypted HTTP interactions, therefore exposing sensitive data to interception and modification. Attackers intercept first connection attempts and provide modified web pages preserving normal website design that delete HTTPS links and security elements while removing. Unknowingly sending passwords, credit card data, and private messages. In When using plain text, users inadvertently allow attackers to capture any information in real-time without raising suspicion or triggering browser security alerts.
Types of Man-in-the-Middle Attacks
To learn how attackers exploit every weak point in private communication, investigate the spectrum of man-in-the-middle attacks, including Wi-Fi eavesdropping, DNS spoofing, HTTPS spoofing, and session hijacking.
Email Hijacking:
Email hijacking is the practice of compromising email accounts or intercepting email messages to pilfer private data, run business email compromise scams, or start focused phishing campaigns. Attackers use illegal access to personal accounts, business email systems, or email servers to track continuous communications, gather private information, and pass for a trusted contact. Businesses especially suffer from this kind of attack since hackers exploit stolen CEO emails to enable fraudulent wire transfers, pilfer intellectual property, or coerce staff members into disclosing company secrets and security credentials.
Wi-Fi Eavesdropping:
Especially in contexts where unsecured public or semi-secured networks are accessible, Wi-Fi eavesdropping is a common kind of MITM attack. Here attackers intercept data being transferred between devices and the network by setting up rogue access points or exploiting insecure wireless networks. Users of these hacked networks directly provide crucial corporate communications, login passwords, and personal information to the attacker. ARP spoofing and other methods let attackers change the information flow in the network, therefore facilitating data stream acquisition and manipulation without user knowledge. This vulnerability highlights for businesses the requirement of strong encryption systems and safe VPN policies, especially when staff members access company resources from public or remote sites.
Session Hijacking:
Once a user logs into a secure application, a session token is created to evade continuous re-authentication, therefore enabling session hijacking. Often by means of cross-site scripting (XSS) or network sniffing, attackers target these session tokens in order to pass for the duration of that session, so posing as the user. Using a stolen session, an enemy can operate on behalf of the authorized user, access sensitive information or complete transactions without setting off instant alerts. The fact that session tokens might not be securely kept or sufficiently safeguarded in transit aggravates the issue. Ensuring the safe processing of session data becomes essential to prevent unwanted eavesdropping and illegal access as systems get more complicated and users interact with many apps concurrently.
Real-world Examples of MITM Attacks
Discover significant real-life man-in-the-middle attacks that happened in the past that include complicated DNS spoofing techniques and Wi-Fi eavesdropping at public hotspots that expose weaknesses in daily digital interactions.
- Firesheep and Public Wi-Fi: 2010 saw the Firesheep program reveal weaknesses in public Wi-Fi by gathering session cookies from social media sites. Businesses moved fast to HTTPS, therefore enhancing encryption and lowering open network risk.
- DigiNotar Certificate Breach: Attackers hacked DigiNotar in 2011 and produced phony digital certificates for well-known websites. This hack eroded internet trust. The answer included enforcing rigorous certificate transparency rules and canceling compromised certificates.
- Lenovo Superfish Incident: Lenovo products included pre-installed Superfish adware loaded with a rogue root certificate in 2014. This weakness let attackers intercept encrypted messages. Lenovo deleted the software, issued a fix, and revoked the certificate, so enforcing more stringent security rules for packaged apps.
Every incident underlines in cybersecurity the requirement of strong software standards, ongoing awareness, and strong encryption to prevent MITM attacks. Knowing what is an MITM attack and how to perform an MITM attacks helps cybersecurity professionals reverse engineer to the roots and resolve them in a timely manner.
Who is at Risk of Man-in-the-Middle Attacks?
MITM attacks target individuals and remote workers most of all. Anyone using public or insecure Wi-Fi networks, in cafés, airports, or hotels, runs the danger of having their data hacked. The issue also covers workers and independent contractors who use personal networks for business, where inconsistent security policies and inadequate encryption expose critical information, including login credentials and financial data, to interception.
Along with big companies, small and medium-sized firms run major risks. Companies with few cybersecurity resources could be low-hanging fruit for attackers looking for high-impact breaches since they lack sophisticated protections. Even businesses with advanced security systems are not immune since highly valuable targets like C-suite executives and financial institutions typically have sensitive proprietary or transactional data. Maintaining confidence and operational integrity depends on strong protection all around, from personal users to corporate executives.
How Does a MITM Attack Work?
An attacker covertly places himself between two communicating parties, such as a user and a website, to intercept the data flow in a man-in-the-middle (MITM) assault. Usually starting with a victim connecting to an unprotected or compromised network or falling victim to phishing techniques enticing them into a false sense of confidence, an intrusion starts. Once the assailant has a footing, they reroute traffic using ARP spoofing or DNS hijacking, therefore capturing sensitive data, including login credentials, financial data, or private messages in real time.
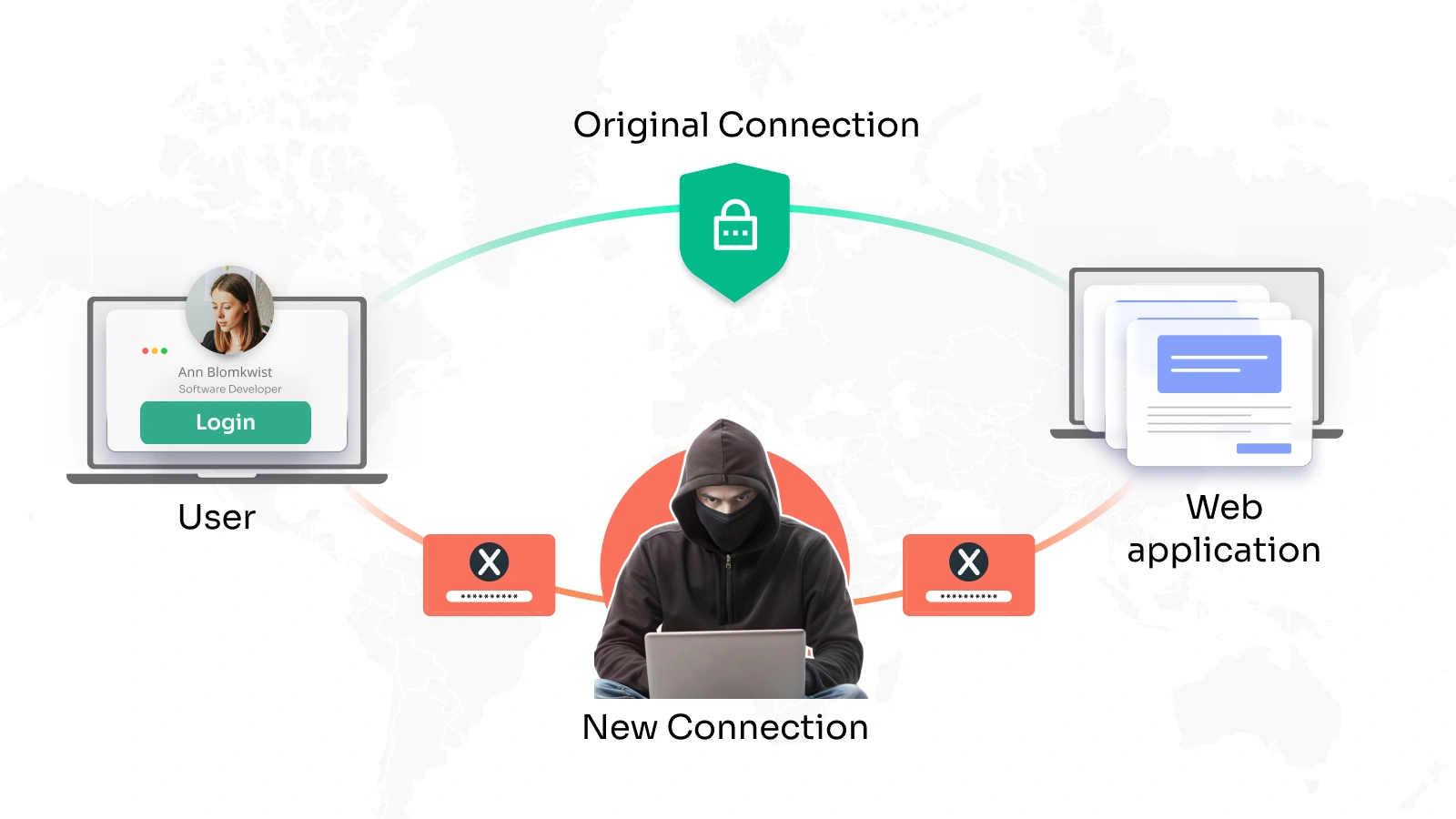
Once the data has been intercepted, the assailant can decode and control the material without the awareness of the pertinent individuals. This enables illegal access or even data modification, therefore perhaps causing financial embezzlement or a compromise of business security. For companies depending on strong identity providers, this emphasizes the vital need for layered defenses, including implementing end-to-end encryption, using safe VPN protocols, and enabling multi-factor authentication, which can help prevent possible Man-in-the-Middle (MITM) attacks.
How to Detect Man-in-the-Middle Attacks?
Look for strange things in network data, make sure ARP/DNS works right, and make sure SSL/TLS certificates are real to find man-in-the-middle attacks. Check out these steps:
Observing slow or disconnected services:
Early warning indicators of an MITM attack can be unexpected network slowness, regular disconnections, or uneven network performance. An interceptor's rerouting or tampering with data often results in delays or disruptions in service that show up as slow-loading websites or sporadic connectivity problems.
Seeing obscure websites or email addresses:
If you suddenly find strange or slightly changed domain names or if your email correspondence appears to originate from non-standard, obscure addresses, be aware. Sometimes cybercriminals utilize versions of legitimate addresses to deceive consumers; verifying digital certificates and checking URLs helps to validate authenticity.
Deploying packet inspections:
By routinely doing packet inspections with Wireshark, managers can examine data packets for anomalies. Unusual traffic patterns or unexpected changes in packet headers could point to an interceptor either changing or grabbing data between transmission points.
Connecting to unsecured WiFi or websites:
Using open, unencrypted networks greatly raises the interceptive danger. Before sending sensitive data, always confirm whether a network is safe; spotting rogue, unsecured WiFi hotspots or automatic redirection to non-HTTPS websites should cause instant caution and more research.
How to Prevent Man-in-the-Middle Attacks?
Strengthen your network with encryption like multi-factor authentication and stricter certificate validation techniques to stay away from MITM attacks. Here are some tips to help you prevent a man-in-the-middle attack in cybersecurity:
1. Update and secure home Wi-Fi routers:
Usually the first line of protection is your home network; hence, update and secure home Wi-Fi routers. Replace any default administrative passwords and routinely update the software on your network. Set your router to use the most recent encryption techniques (like WPA3), then turn off remote administration tools that might let strangers access your network.
2. Use a VPN when connecting to the internet:
Especially important on public or untrusted networks, a VPN encrypts your online traffic when connecting to the Internet. A reliable VPN hides your digital footprint and stops intruders from intercepting or reading your conversations by forwarding your data across a safe server.
3. Use end-to-end encryption:
Choose services that enable end-to-end encryption whenever at all feasible. This method guarantees that your sensitive data is encrypted on the sender's device and only deciphered by the intended recipient, therefore excluding any possibility for middlemen to access it.
4. Install patches and use antivirus software:
Install patches and use antivirus software to routinely address weaknesses that attackers could find in systems and applications. Reputable antivirus and anti-malware programs concurrently offer real-time monitoring and threat elimination, so keep your devices free from recently developing hazards.
5. Use strong passwords and a password manager:
Strong, unique passwords are absolutely necessary to stop unwanted access; use a password manager. By helping you create, save, and manage complicated passwords safely, a trustworthy password manager helps to reduce credential stuffing or brute-force attacks.
6. If available, deploy multi-factor authentication (MFA):
By requiring further verification, such as a one-time code or biometric confirmation, beyond the conventional password, MFA offers even more protection. Even with a password hacked, this additional step drastically lowers the possibility of illegal access.
7. Only connect to secure websites:
Check website URLs to be sure they use HTTPS, therefore signifying that an SSL/TLS certificate encrypts the sent data. Steer clear of visiting websites without safe protocols or triggering browser warnings since these could let someone access your information through interception.
8. Encrypt DNS traffic:
DNS searches should be encrypted using DNS over TLS (DoT) or DNS over HTTPS (DoH), therefore shielding the domain resolution process from prying eyes. This encryption stops attackers from guiding you to dangerous websites or learning which websites you visit.
9. Adopt the zero-trust philosophy:
The zero-trust paradigm holds that no device or user is automatically trusted. At every layer of a network, enforce rigorous identity verification and access restrictions. Constant validation of every access request, even within your own network, helps to lower the possible risk for breaches.
10. Deploy a UEBA solution:
Standard network behavior is monitored, and deviations are flagged by UEBA, User and Entity Behavior Analytics tools. UEVA products provide an early warning system against abnormalities that can indicate MITM attacks or related harmful activity by examining trends across consumers and devices.
MITM Attacks in Cybersecurity
Among the most sneaky dangers in the cybersecurity scene of today are man-in-the-middle (MITM) attacks. In these assaults, a malevolent actor covertly sits between two communicating parties, say a user and a website, to intercept or control data without either party knowing. From login passwords to financial data, attackers use these weaknesses, which range from unsecured public Wi-Fi to hijacked networks to sophisticated phishing techniques, to grab sensitive data. This covert infiltration immediately compromises business integrity and individual privacy in addition to eroding faith in digital communications.
Cybersecurity experts have to use a tiered defense approach to offset these changing dangers. Strong encryption methods, frequent system and software updates, and User and Entity Behavior Analytics (UEVA) to instantly identify anomalies in real time constitute part of this as well. Strengthening defenses equally depends on adopting a zero-trust approach and using robust multi-factor authentication (MFA). These steps are crucial for companies, especially those in sectors depending on trustworthy identity providers, to preserve digital transactions, safeguard private information, and keep the general confidence of their stakeholders.
How miniOrange Simplifies MITM Attack Protection
miniOrange integrates security right into the authentication process and helps companies defend against MITM attacks. Our Single Sign-On (SSO) system guarantees a securely encrypted every login request and simplifies identity verification. The miniOrange SSO product lowers the attack surface by centralizing access, therefore sealing holes that attackers might find to intercept or hijack sessions. This centralized solution not only streamlines user management but also combines modern encryption standards and certificate validations, therefore greatly reducing the risk of data modification during transmission.
miniOrange's Multi-Factor Authentication (MFA) product provides a necessary degree of protection to complement SSO. MFA needs an extra verification step, such as a one-time code or biometric confirmation, even if attackers manage to intercept main credentials, so almost no unauthorized access is created. miniOrange helps companies to adopt a zero-trust posture by aggregating strong SSO. This includes both MFA solutions and other security measures under a single identity management system. This all-encompassing defense strategy not only shields important digital communications from MITM attacks but also supports business continuity and stakeholder confidence in a cybersecurity environment growing increasingly dangerous. Talk to an expert at miniOrange to control MITM attacks and start a 30-day free trial of MFA and SSO today.
Read More:- Top 15 Cybersecurity Threats in 2025
Your Powerful Toolkit Against MITM Attacks
No one defense system is sufficient in the cybersecurity scene of today to stop the complexity of man-in-the-middle attacks. Knowing the distinctions between authentication and authorization is a fundamental first step. While authorization controls what rights a user or device is granted, authentication certifies their identification. Determining authentication for your company can be a challenge; however, choosing among the right types of authentication is easy if your goals for policy governance are clear. Including context-based authentication which evaluates elements like the user's location, device, or login time, in your security system guarantees that access is constantly assessed against the current risk environment rather than provided just on a stationary credential.
By including more login process verification steps, multi-factor authentication (MFA) enhances this layered security even more. Even if attackers get user credentials, the additional elements MFA offers make it quite difficult to breach systems. Combining strict identity verification procedures with contextual checks and real-time risk assessments in this robust toolbox creates a necessary barrier against MITM intrusions. Maintaining confidence, safeguarding private information, and guaranteeing continuous corporate operations in an always-changing threat environment depend on adopting these approaches.
FAQs
1. Who are the three main participants in a man-in-the-middle attack?
In a typical man-in-the-middle attack, there are three key players involved. First, there’s the victim, usually someone trying to access a website or online service. Then, there’s the legitimate party the victim is trying to connect with, like a bank or an email provider. Finally, there’s the attacker, who secretly slips in between the two, intercepting and sometimes even changing the messages being sent back and forth, all without the knowledge of either side.
2. What causes a man-in-the-middle attack?
Man-in-the-middle attacks are carried out by malicious hackers that exploit the weak spots in our websites, systems, and communication channels. Things like using public Wi-Fi without proper security, visiting websites that don’t use encryption, or falling for phishing scams can open the door for attackers. Sometimes, even technical missteps, like poorly set up security certificates or outdated software, can give hackers the chance to sneak in and eavesdrop on private conversations or data exchanges.
3. What is the effect of a man-in-the-middle attack?
The impact of a man-in-the-middle attack is serious. Attackers tend to steal sensitive information, such as credentials, credit card numbers, personal messages, and personal secrets. This can lead to attackers impersonating user identities with identity theft, gaining unauthorized access to your accounts, or even causing financial loss. In some cases, attackers go a step further and send malicious software to your device or intercept your communications to receive messages and calls that are meant for you without you even suspecting, causing even more trouble down the line.
4. Is man-in-the-middle a DoS attack?
No, a man-in-the-middle attack is different from a denial-of-service (DoS) attack and not the same. While both types of hacks are carried out by cyber attackers, they inflict different damage from each other. A man-in-the-middle attack is all about intercepting and altering communication in a channel, whereas a DoS attack is designed to render a system or website not functional and unavailable to the users by sending bot traffic or simulating a lot of website visitors. That said, hackers use information extracted from a man-in-the-middle attack to help launch a DoS attack; however, they’re different tactics.



Leave a Comment