As organizations juggle a mix of legacy systems, modern cloud platforms, and specialized software, the challenge of managing user authentication across diverse environments becomes increasingly complex. While web-based solutions have evolved rapidly with robust identity protocols, many mission-critical applications still rely on desktop-based interfaces that demand a different approach.
This blog explores how organizations can unify access across these environments, reduce friction for users, and maintain strong security postures, all without compromising performance or usability. If you're an IT architect, security analyst, or just curious about how authentication works beyond the browser, this article will help you navigate the nuances of integrating identity into thick client ecosystems.
What Are Thick Client Applications?
Thick client applications are desktop-based software programs that perform the majority of their data processing operations locally on the user's device rather than relying heavily on remote server resources. Also known as "fat clients" or "rich clients," these applications are self-contained systems with significant computing power, storage capabilities, and graphics resources that enable them to function independently.
Unlike web-based applications that require constant server communication, thick clients can operate with minimal or intermittent network connectivity, making them ideal for environments where offline functionality is crucial. The term "thick" refers to the substantial amount of application logic, data processing capabilities, and user interface components that reside directly on the client device.
Types of Thick Client Applications
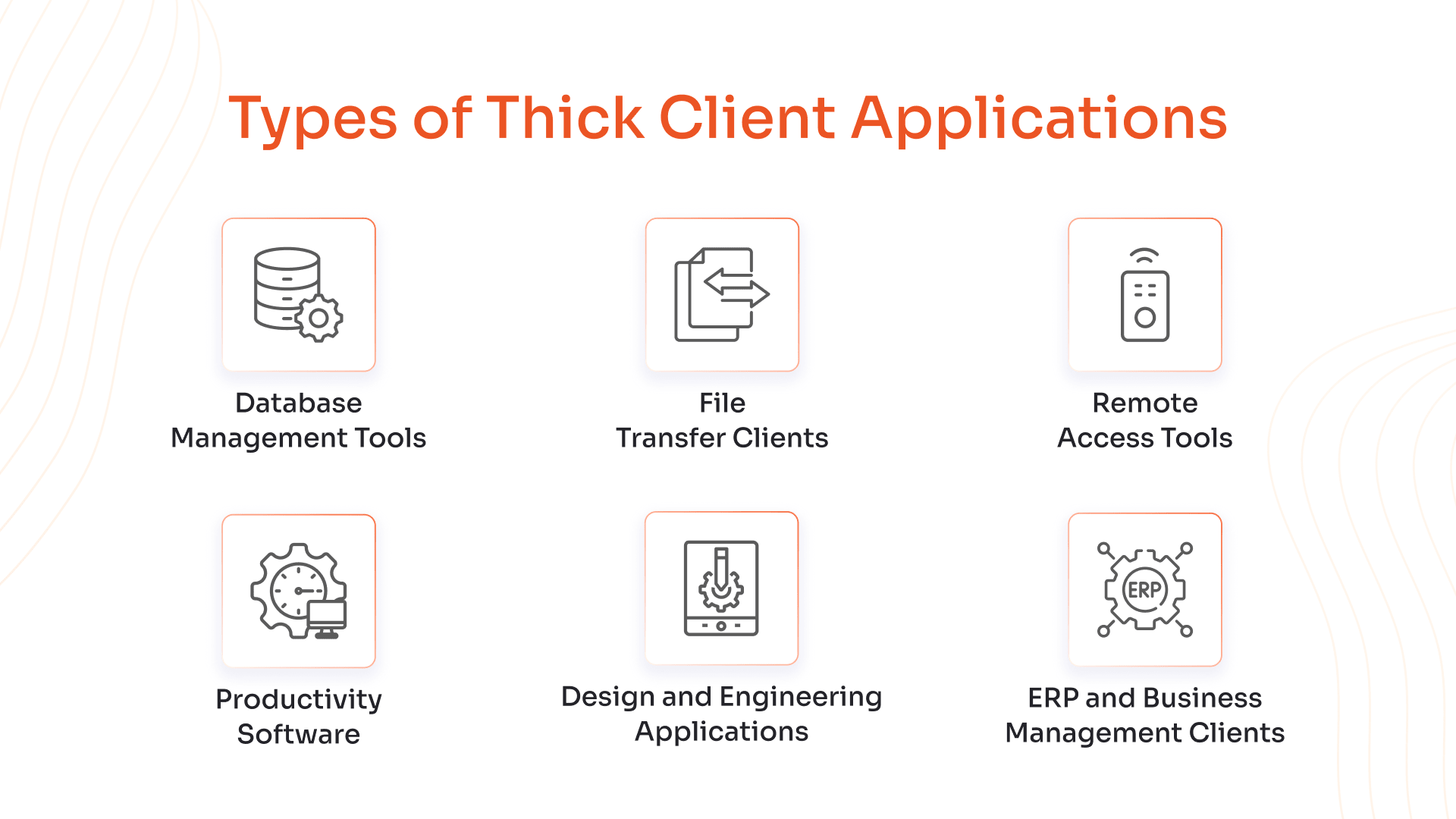
Database Management Tools
These applications allow users to design, query, and manage databases locally. They offer visual modeling, administrative controls, and direct server connections without relying on browser-based interfaces or cloud-only platforms.
File Transfer Clients
Used for secure file transfers between local and remote systems, these clients support FTP/SFTP protocols, encryption, and session control. They operate independently of browsers and manage connections from the desktop.
Remote Access Tools
These tools enable users to connect to and control remote machines. The client software handles session initiation, credential management, and display rendering locally, ensuring secure and responsive remote access.
Productivity Software
Installed on desktops, these applications support document creation, data analysis, and presentations. They offer full functionality offline, integrate with local storage, and provide advanced formatting and computational capabilities.
Design and Engineering Applications
Used in technical fields for CAD modeling, simulations, and drafting, these applications require high-performance local processing. They often interact with specialized hardware and support complex design workflows.
ERP and Business Management Clients
Enterprise applications that manage operations like finance, HR, and logistics. Thick client versions offer robust interfaces, local caching, and secure communication with backend systems for transactional efficiency.
Examples of Thick Client Applications
MySQL Workbench
A desktop-based database tool for designing schemas, executing queries, and managing servers. It provides visual modeling and administrative features without relying on browser-based access or cloud-only environments.
FileZilla
An FTP client that facilitates secure file transfers. It runs locally, supports multiple protocols, and allows users to manage sessions, credentials, and encryption settings directly from the desktop.
Remote Desktop Connection
A Windows application that lets users access and control remote computers. It manages session setup, authentication, and display rendering locally, ensuring secure and efficient remote interactions.
Microsoft Word
A word processor installed on desktops, offering offline document creation, editing, and formatting. It integrates with local storage and supports advanced features like templates, styles, and macros.
Microsoft Excel
A spreadsheet tool used for data analysis, calculations, and visualization. It operates offline, supports complex formulas, and integrates with local files and external data sources for reporting.
AutoCAD
A CAD application used for architectural and engineering design. It performs rendering and modeling locally, supports technical drawing standards, and integrates with hardware like plotters and 3D printers.
SAP GUI
A desktop interface for accessing SAP ERP modules. It enables users to perform business transactions, manage workflows, and interact with enterprise data securely through local processing and server communication.
Thick vs Thin Client Comparison
| Aspect | Thick Client | Thin Client |
|---|---|---|
| Processing Location | Local client-side processing with minimal server dependency | Server-side processing with client handling only display |
| Installation | Locally installed applications with full features | Browser-based installation with limited local storage |
| Network Dependency | Intermittent connectivity required; can work offline | Continuous server communication necessary |
| Data Validation | Client-side data verification and processing | Server-side data verification required |
| Resource Usage | High local hardware requirements and power consumption | Minimal local resources needed |
| Deployment Cost | Higher initial investment but lower server load | Lower hardware costs but higher server requirements |
| Security | More vulnerable to local threats but better offline security | Centralized security management with fewer local risks |
| Customization | Highly customizable with user control over configurations | Limited customization options |
Why thick client SSO is different from web SSO?
Protocol Support and Compatibility
Web SSO typically relies on browser-native protocols like SAML, OAuth, and OpenID Connect, which are designed for HTTP-based communication. Thick clients, however, may not support these protocols natively and often require custom integration or use of Kerberos, NTLM, or proprietary mechanisms.
Authentication Flow
In web SSO, the browser redirects users to an identity provider, handles token exchange, and returns to the application all within the browser session. Thick clients lack this redirect capability and must handle authentication internally, often requiring embedded browser components or external token brokers.
Token Management
Web applications rely on cookies or browser storage to manage tokens. Thick clients must store and refresh tokens securely within the application itself, which introduces complexity around encryption, session persistence, and token renewal.
Integration Complexity
Web SSO is often plug-and-play with modern identity providers. Thick client SSO requires deeper integration, sometimes modifying application code, using wrappers, or deploying middleware to bridge the gap between the client and identity provider.
User Experience
Web SSO offers seamless login across browser tabs and apps. Thick client SSO must replicate this experience without browser support, which can be challenging when dealing with legacy UI frameworks or limited protocol support.
Security Considerations
Thick clients often run in trusted environments and interact with local resources, making secure token handling and credential storage critical. Web SSO benefits from sandboxed browser environments and centralized session control.
Thick Client SSO Protocols
Kerberos
Kerberos serves as the cornerstone authentication protocol for enterprise thick client environments, utilizing symmetric key cryptography for secure client-server communications. This mature protocol operates through a ticket-granting system where the Key Distribution Center (KDC) issues time-limited tickets that clients present to access services without repeatedly transmitting passwords over the network.
Enterprise Integration: Most enterprise thick clients like database management tools and enterprise resource planning systems natively support Kerberos, making it the preferred choice for organizations with existing Windows infrastructure.
NTLM (NT LAN Manager)
NTLM provides backward compatibility for legacy thick client applications that cannot support modern authentication protocols. While less secure than Kerberos, NTLM remains essential for maintaining access to critical legacy desktop applications in mixed environments.
Legacy System Support: NTLM's challenge-response mechanism works effectively with older thick client applications that lack support for newer protocols, ensuring business continuity during gradual system modernization.
OAuth 2.0
OAuth 2.0 transforms thick client authentication by enabling secure authorization without exposing user credentials to desktop applications. This framework allows thick clients to obtain limited access tokens for specific resources while maintaining centralized identity management.
Modern Integration: Contemporary thick client applications increasingly adopt OAuth 2.0 for integrating with cloud services, enabling desktop applications to access APIs securely without storing long-term credentials.
OpenID Connect (OIDC)
OpenID Connect builds upon OAuth 2.0 to provide standardized identity verification specifically designed for modern thick client applications. OIDC delivers both authentication and authorization capabilities through JSON Web Tokens (JWT) that thick clients can process locally.
Growing Adoption: Leading technology companies like Google and Microsoft actively promote OIDC as the preferred protocol for thick client authentication, making it increasingly supported by desktop application frameworks.
SAML (Security Assertion Markup Language)
SAML enables federated authentication for thick client applications through XML-based security assertions that carry user identity and authorization information between identity providers and service providers. This protocol excels in enterprise environments requiring detailed attribute exchange and complex authorization policies.
Integration Complexity: While SAML provides robust security features, implementing SAML in thick client environments requires careful consideration of certificate management, XML processing, and secure assertion handling within desktop application architectures.
Advantages of Thick Client SSO
1. Qualify Cybersecurity Audits
Thick client SSO provides a comprehensive record of all user login attempts, granting visibility into access patterns and facilitating compliance with regulations like GDPR, HIPAA, and PCI DSS. By reducing the number of systems where sensitive data is accessed, thick client SSO helps minimize the risk of data breaches and ensures compliance with data privacy laws.
2. Shield Against Rising Security Threats
All authentication processes are handled by a single, trusted authority, reducing the risk of credential theft and unauthorized access. SSO can enforce stricter password policies, such as requiring complex passwords, regular changes, and multi-factor authentication, further enhancing security. By consolidating authentication, SSO can help identify and mitigate security threats more effectively.
3. Kill Password Fatigue
Users only need to remember one set of credentials, simplifying the login process and reducing frustration. SSO enables users to seamlessly navigate between multiple applications without having to re-enter their credentials, improving productivity and satisfaction. By eliminating the need to manage multiple passwords, SSO helps reduce password fatigue and the associated risks of compromised accounts.
4. Cut Down Wasted Login Time
Users can quickly access the applications they need without being hindered by multiple login screens and password entry. SSO can reduce the burden on IT support by minimizing the number of password reset requests. By streamlining the login process, SSO can help users focus on their tasks and improve overall workflow efficiency.
5. No More Password Reset Tickets
IT administrators can manage user access policies and privileges from a single location, simplifying the process of granting and revoking permissions. SSO can enforce consistent security policies across all applications, ensuring compliance with organizational standards. By automating authentication and access control processes, SSO can reduce the IT department's workload and free up resources for other tasks.
Step-by-Step SSO Implementation of Desktop Apps
1. Assessment & Planning
Begin by auditing your desktop applications, user workflows, and existing authentication mechanisms. Identify which apps support modern protocols and which require custom integration. Define security goals and compliance requirements.
2. Choosing the Right SSO Solution
Select an identity provider (IdP) that supports desktop integration, such as Azure AD, Okta, miniOrange or Ping Identity. Ensure it offers support for protocols like Kerberos, SAML, or OAuth for non-browser environments.
3. Implementation Process
Integrate the desktop application with the chosen IdP. This may involve embedding authentication libraries, configuring token brokers, or using middleware to bridge legacy protocols with modern identity standards.
4. Testing & Deployment
Conduct thorough testing across different user roles, devices, and network conditions. Validate token handling, session persistence, and fallback mechanisms. Roll out in phases to minimize disruption and gather feedback.
5. User Training and Support
Educate users on the new login experience, especially if MFA or passwordless methods are introduced. Provide clear documentation and support channels to handle onboarding and troubleshooting.
6. Monitoring & Optimization
Implement logging and monitoring to track authentication flows, detect anomalies, and measure performance. Use analytics to refine token lifetimes, session policies, and error handling over time.
Resolving Challenges in SSO Implementation for Thick Clients
Legacy Application Integration
Older desktop applications may lack support for modern identity protocols. Use wrappers, proxy services, or custom plugins to intercept and translate authentication requests into SSO-compatible formats.
Offline Access
Thick clients often need to function without constant connectivity. Implement token caching and refresh strategies that allow limited offline access while maintaining security boundaries and expiration controls.
Multi-Factor Authentication
Integrating MFA into desktop apps can be complex. Use external authenticators, smart cards, or biometric devices that interface with the operating system or IdP, rather than embedding MFA directly into the app.
Performance Concerns
SSO should not degrade application responsiveness. Optimize token validation, reduce unnecessary network calls, and ensure that authentication components are lightweight and well-integrated with the app’s startup flow.
miniOrange SSO Solution for Desktop Apps
miniOrange offers a robust Single Sign-On (SSO) solution for desktop applications that streamlines user authentication across enterprise environments. By integrating with identity providers like Azure AD, Okta, and Google Workspace, miniOrange enables seamless access to thick client applications without repeated logins.
Our support for Multi-Factor Authentication (MFA) adds an essential layer of security, ensuring that access is granted only after verifying user identity through methods such as OTP, biometrics, or push notifications. This combination of SSO and MFA helps organizations enhance security posture while improving user experience across legacy and modern desktop platforms.
Our Thoughts
As enterprises continue to modernize their identity infrastructure, miniOrange stands out as a practical solution for bridging the gap between legacy desktop applications and modern authentication standards. Our ability to unify access, enforce strong security controls, and support diverse environments makes it a valuable tool for organizations seeking to simplify login experiences without compromising protection.


Leave a Comment