Industry reports predict that 2026 will see a record-breaking year for mergers and acquisitions (M&A). However, this growth creates significant opportunities for cyber threats and vulnerabilities to emerge.
Most M&As are strategic partnerships designed to drive business growth, but what happens when they become your organization's biggest security weakness? A single breach during integration can result in devastating data exposure, financial losses, and irreparable damage to your company's reputation.
In this article, we'll explore M&A cybersecurity fundamentals, identify common threats that emerge during mergers, and explain how miniOrange, as your cybersecurity partner, can help you protect your organization's most valuable assets.
What is M&A Cybersecurity?
M&A cybersecurity refers to the security practices and risk management implemented throughout the merger and acquisition process. It covers everything from initial due diligence through post-merger integration, ensuring that combining two organizations doesn't create dangerous vulnerabilities that attackers can exploit.
When two companies merge, they're bringing together two completely separate IT environments. Each organization has its own security policies, user access controls, applications, cloud services, and existing vulnerabilities. M&A cybersecurity addresses this challenge by evaluating the security posture of target companies before deals close, identifying weaknesses that could become major problems, and developing integration strategies that protect both organizations.
This practice involves consolidating identity and access management systems, aligning compliance requirements across various regulatory frameworks, assessing risks associated with third-party vendors, and maintaining continuous monitoring throughout the transition period. The goal is straightforward: protect intellectual property, customer data, financial records, and proprietary information while ensuring the acquisition delivers its intended business value without introducing potential security failures.
Key Challenges for M&A Security

M&A being a long process, the involved companies face many challenges, including security threats. Other challenges include:
Protection During High-Risk Transition Periods
The merger and acquisition process creates extended timeframes where organizations become exceptionally vulnerable to cyberattacks. Temporary access permissions multiply as teams from both companies collaborate across organizational boundaries. Cybercriminals actively monitor M&A announcements because they know these transition periods offer prime opportunities to exploit weakened defenses and organizational confusion.
Preventing Massive Financial Losses
Security breaches during M&A transactions carry devastating financial consequences. Beyond immediate costs for incident response and system remediation, organizations face hefty regulatory fines. Research shows companies experiencing breaches during M&A activities can see acquisition valuations drop by 15-30%, directly eroding shareholder value and undermining the deal's financial logic.
Meeting Compliance Requirements
Merging organizations frequently operate under different compliance frameworks. One company might need to comply with GDPR for European customer data, while the other follows HIPAA regulations for healthcare information or PCI DSS standards for payment processing. Absence of M&A cybersecurity leads to penalties and operational restrictions that could shut down critical business functions.
Shielding Company Reputation
Customer trust takes years to build but can disappear overnight. A security breach during or immediately after an acquisition sends a clear message to customers, partners, and investors that your organization cannot manage complex operational transitions safely. This reputational damage extends far beyond immediate customer losses, affecting future partnership opportunities and competitive positioning in your market.
Discovering Security Liabilities
Target companies may be hiding undisclosed security incidents, compromised systems, or ongoing breaches that don't appear during standard financial due diligence. They might have outdated infrastructure with known vulnerabilities, weak authentication practices, or poor data protection policies. M&A cybersecurity uncovers these hidden liabilities before they become your responsibility, giving you critical information that would expose your organization to unacceptable risk.
Ensuring Business Continuity
M&A security is also about ensuring seamless business operations throughout the transition. Security incidents during integration can cause system downtime, disrupt customer service, halt production lines, and interrupt revenue-generating activities. Proper M&A security planning ensures both organizations can continue serving customers without interruption while systems are being merged and consolidated.
Common Security Threats Faced During M&A
Mergers and acquisitions come with more than just operational challenges. They expose your organization to a range of security vulnerabilities before, during, and after the deal.
Insider Threats and Privilege Abuse
M&A transitions create uncertainty among employees, and frustrated staff members may exploit their access before termination or role changes. This includes stealing intellectual property, exfiltrating customer data, or creating backdoors for future unauthorized access. The confusion of combining access systems makes it difficult to track who has permissions to what resources, enabling insiders to operate undetected.
Phishing and Social Engineering Attacks
Attackers launch sophisticated phishing campaigns targeting employees from both organizations during M&A announcements. These attacks impersonate executives, HR departments, or IT teams requesting credential updates, system migrations, or urgent access approvals. Attackers exploit this confusion to harvest credentials, install malware, or gain unauthorized access to sensitive systems.
Ransomware Exploitation
Cybercriminal groups specifically target organizations undergoing M&A, knowing that operational disruptions during critical integration phases create maximum pressure to pay ransoms quickly. These attacks aim to encrypt critical systems right as companies are merging databases, migrating applications, or consolidating infrastructure, moments when downtime has an exponential business impact.
Supply Chain and Third-Party Risks
Acquisitions often bring extensive networks of third-party vendors, contractors, and service providers whose security practices may be unknown or substandard. Each vendor relationship represents a potential entry point into your combined network. Attackers exploit these trusted third-party connections to bypass perimeter defenses and gain access to sensitive systems.
Shadow IT and Unauthorized Applications
During M&A integration, employees frequently adopt unauthorized tools and applications to maintain productivity while official systems are being consolidated. This shadow IT creates unmonitored access points, stores sensitive data in unsecured locations, and bypasses security controls. These unauthorized applications give attackers easy targets that security teams don't even know exist.
Legacy System Vulnerabilities
Acquired companies often operate outdated systems with unpatched vulnerabilities that your security standards wouldn't normally tolerate. These legacy systems become weak points in your expanded infrastructure, providing attackers with easy entry paths to access your entire network once systems are interconnected. The technical debt inherited through acquisitions can take months or years to remediate.
Lifecycle of the M&A Security
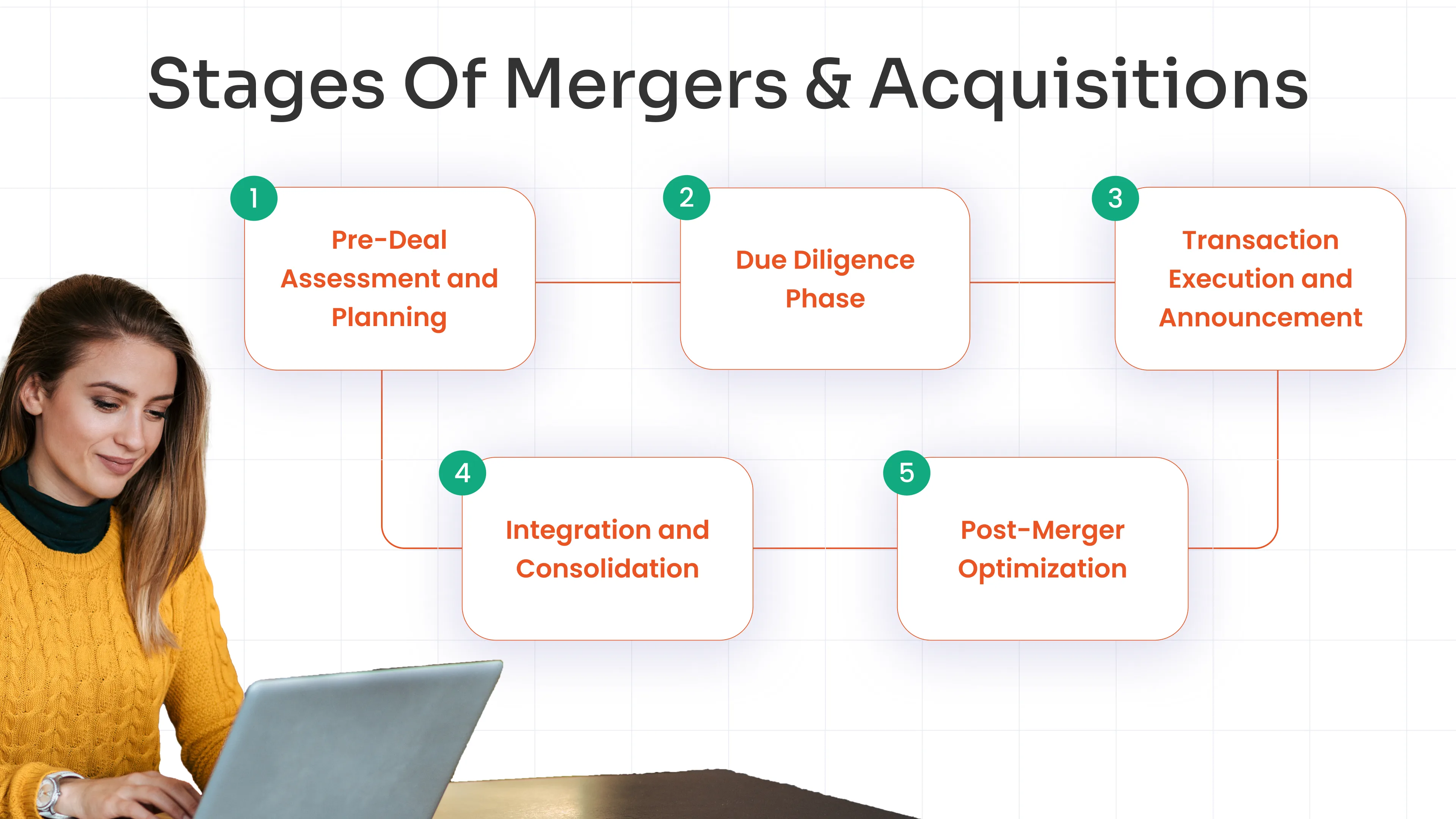
The M&A security lifecycle spans multiple critical phases, each with unique cybersecurity challenges. Understanding these stages helps organizations implement appropriate security measures at the right time, protecting assets and ensuring smooth integration.
Pre-Deal Assessment and Planning
Before announcing any merger or acquisition, organizations must conduct preliminary security assessments of potential target companies. This early stage involves indirect inspection to identify publicly visible security issues, review for leaked credentials or data breaches associated with the target, and analyzing the target's digital footprint for vulnerabilities.
Security teams should develop a cybersecurity playbook that outlines objectives, scope, and assessment methodologies that will be applied throughout the transaction. This preparation phase sets the foundation for informed decision-making and helps identify deal-breakers before significant resources are committed.
Due Diligence Phase
The due diligence phase represents the most critical period for cybersecurity assessment. Security teams conduct comprehensive evaluations of the target organization's security posture, including reviewing its information security policies, procedures, and practices against established frameworks like NIST or ISO 27001.
This phase involves penetration testing and red team assessments to uncover exploitable weaknesses, evaluating third-party vendor risks, assessing regulatory compliance gaps, and identifying hidden data breaches or ongoing security incidents. The goal is to quantify cybersecurity risks and calculate the potential costs of remediation, which directly impacts deal valuation and negotiation strategies.
Transaction Execution and Announcement
Once the deal is announced publicly, cybersecurity risks escalate drastically. Threat actors actively monitor M&A announcements and launch targeted attacks during this vulnerable period. Security teams must implement heightened monitoring across both organizations, establish clear incident response protocols with defined roles and responsibilities, and protect against phishing campaigns targeting employees from both companies. This phase requires strategic decisions about how security operations will eventually integrate while maintaining strong defenses during the transition period.
Integration and Consolidation
The integration phase involves merging two distinct security environments into a unified framework. This includes consolidating identity and access management systems, harmonizing security policies and procedures, migrating and securing data transfers between organizations, and remediating high-priority vulnerabilities identified during due diligence.
Organizations must develop detailed integration roadmaps with realistic timelines for addressing immediate concerns within the first three months, followed by medium and long-term remediation extending through the first year. The complexity of this phase often makes it the most challenging part of the entire M&A process from a cybersecurity perspective.
Post-Merger Optimization
After the initial integration, continuous monitoring ensures both organizations operate under consistent security standards. This final phase focuses on ongoing vulnerability assessments, compliance verification across the combined entity, and refinement of security controls based on lessons learned during integration.
Security teams must ensure the acquired organization meets the acquiring company's requirements for confidentiality and integrity while following unified policies and procedures. Regular review meetings track remediation progress and address emerging security concerns as the two organizations fully merge their operations and cultures.
How You Can Secure Your Organization During M&A
Start Cybersecurity Planning Early
Involve your cybersecurity team from the very beginning of M&A discussions. This ensures proper risk assessment and allows security experts to spot weaknesses before any integration starts. Early engagement helps you build a custom strategy for identifying risks and preparing for potential threats.
Conduct Thorough Due Diligence
Carry out comprehensive cybersecurity assessments of the target company. This includes examining their policies, network architecture, data protection practices, vendor relationships, and history of security incidents. Use both external threat intelligence and internal audits to spot hidden vulnerabilities.
Prioritize Third-Party Risk Management
Evaluate third-party vendors that could affect your security posture. Review contracts and SLAs to make sure they include strong cybersecurity and compliance clauses. Weaknesses in the target’s supply chain can pose major risks after the merger.
Plan for Integration and Risk Remediation
Develop a clear roadmap for cybersecurity integration. Align policies, consolidate identity and access management controls, and schedule data migrations with strict security monitoring. Establish both short-term and long-term plans to remediate any gaps found during due diligence.
Synchronize Regulatory Compliance
Merge compliance practices and test for gaps between both organizations, such as GDPR, HIPAA, or PCI DSS requirements. Train staff on changed policies and new systems, ensuring ongoing monitoring and adherence to all regulations.
Maintain Continuous Threat Monitoring
During and after the merger, actively hunt for cyber threats and monitor systems for suspicious activity. This includes vulnerability scans, penetration testing, and regular reviews of access controls. Prompt threat detection and response help prevent breaches and data loss.
Enable Change Management and Staff Training
Organizational change isn’t just about technology; prepare your team with security awareness training and readiness for new processes. Engage project management and change enablement resources to ensure everyone in the company can operate securely and confidently post-merger.
miniOrange for M&A Identity Security
Unified Identity Platform for Merging Organizations
During mergers and acquisitions, consolidating identity management across both organizations becomes critical. The platform combines Single Sign-On, Multi-Factor Authentication, and Customer IAM in one solution, eliminating multiple vendors and ensuring consistent security policies throughout the transition.
Flexible Integration Across Legacy and Modern Systems
M&A transitions often involve integrating vastly different technology stacks. Support for modern protocols like SAML, OAuth, and OpenID Connect, alongside connections to legacy systems through the Access Gateway, enables seamless integration without requiring immediate infrastructure overhauls, allowing acquired companies to connect securely during the transition period.
Privileged Access Management for High-Risk Environments
Privileged accounts become prime targets during organizational changes. PAM capabilities secure privileged credentials with session management, real-time monitoring, time-limited access, and privilege elevation controls, minimizing risks from overly privileged accounts that could be exploited during merger transitions.
Adaptive MFA for Context-Aware Security
Security requirements shift dynamically during M&A as employees access unfamiliar systems from new locations. Adaptive MFA adjusts security measures based on location, device, IP address, and user behavior, providing robust protection during transitions without hindering employee productivity across both organizations.
Role-Based Access Control and Least Privilege
Determining appropriate access levels for employees from acquired organizations requires granular control. The platform enforces role-based access using predefined roles and permissions, ensuring employees only access resources necessary for their specific roles while minimizing insider threats during the integration phase.
Automated User Provisioning for Seamless Transitions
Employee roles change frequently during M&A, requiring efficient access management. Automated workflows streamline user onboarding, role changes, and immediate access revocation for departing employees, reducing IT burden while eliminating common security vulnerabilities that emerge during organizational change.
Compliance and Audit Capabilities
Merged organizations must maintain compliance across multiple regulatory frameworks. The solution supports GDPR, PCI-DSS, HIPAA, and ISO 27001 through comprehensive audit logging, session monitoring, and periodic access reviews, enabling compliance verification across different regulatory requirements inherited through acquisitions.
Cloud, Hybrid, and On-Premise Deployment
Different organizations have varying infrastructure preferences and regulatory requirements. Flexible deployment models, including cloud, on-premise, and hybrid options, accommodate these differences while ensuring seamless integration during M&A activities, allowing each organization to maintain its preferred infrastructure approach.
Conclusion
The M&A lifecycle demands proactive security measures at every stage, from insider threats and ransomware attacks to compliance gaps and legacy system weaknesses. Organizations that prioritize IAM solutions during these transitions protect their data, maintain customer trust, and ensure regulatory compliance. With miniOrange's comprehensive IAM solutions, you can navigate M&A complexities confidently, securing privileged access, automating user provisioning, and establishing unified security policies that safeguard your combined organization's most valuable assets.
FAQs
What is M&A cybersecurity, and why is it important?
M&A cybersecurity refers to security practices implemented throughout mergers and acquisitions to protect digital assets and infrastructure. It's critical because M&A transitions create vulnerability windows where cybercriminals exploit weakened defenses, potentially causing data breaches, financial losses, and reputational damage that can reduce deal valuations significantly.
What are the biggest security threats during M&A?
Major threats include insider access abuse, phishing campaigns targeting employees during transitions, ransomware attacks exploiting integration chaos, third-party vendor vulnerabilities, shadow IT applications, and legacy system weaknesses. These threats are amplified because security teams are stretched thin, and organizational changes create confusion that attackers actively exploit.
How does miniOrange help secure M&A transitions?
miniOrange provides unified identity and access management that consolidates SSO, MFA, and PAM across both organizations. It integrates legacy and modern systems, enforces role-based access controls, automates user provisioning and de-provisioning, and maintains compliance with GDPR, HIPAA, and other regulations, all essential for protecting merged organizations during complex transitions.
When should cybersecurity planning start in the M&A process?
Cybersecurity planning should begin during the earliest pre-deal assessment phase, before any merger announcement. Early involvement allows security teams to conduct thorough due diligence, identify hidden vulnerabilities, quantify remediation costs that impact deal valuation, and develop integration strategies that protect both organizations throughout the entire transaction lifecycle.



Leave a Comment