Ransomware isn’t just a rising threat, it’s a daily reality for thousands of businesses around the world. These attacks are faster, smarter, and more damaging than ever, with global losses projected to reach $275 billion a year by 2031, according to Cybersecurity Ventures.
Understanding how ransomware works is the first step toward stopping it. In this blog, we’ll break down how these attacks unfold and what you can do to defend your systems. Along the way, we’ll show how miniOrange’s different Identity Access and Management (IAM) solutions give you practical ways to stay protected and respond with confidence if something goes wrong.
What is Ransomware in Cybersecurity?
Ransomware is a form of malware, malicious software designed to cause harm or take control of digital systems, locking you out of your files or devices until a ransom is paid. Typically, ransomware sneaks in through phishing emails, infected attachments, or compromised websites, often disguised as harmless files or links.
Once inside, it stealthily encrypts critical information, rendering it totally unusable without a unique decryption key that only the attacker has. The victim then receives a demand for payment with the promise of restoring access if the ransom is paid.
A ransomware attack encompasses the entire process, from the first infection, which is usually caused by a user clicking on a phishing link or downloading a trojan-laced attachment, to the moment the attacker delivers their ransom note and locks up important files or systems. Some attacks go further, threatening to leak or destroy sensitive data if the ransom isn’t paid, adding extra pressure on organizations to comply.
These attacks can disrupt services businesses and lead to significant financial and reputational damage, making ransomware one of the most serious cybersecurity threats today.
Explore the Top Cybersecurity Threats You Should Know
History of Ransomware Attack
Ransomware’s story begins in 1989, long before most people had even heard the word “malware.” The first known attack, called the AIDS Trojan, was the brainchild of Joseph L. Popp, a biologist who mailed 20,000 floppy disks to attendees of a World Health Organization (WHO) AIDS conference. Disguised as a medical questionnaire, the disk instead unleashed a trojan that quietly encrypted files and demanded a ransom, $189 sent to a P.O. box in Panama, in exchange for access. While primitive by today’s standards, this attack set the template: use deception, lock up valuable data, and demand payment.
Throughout the 1990s and early 2000s, ransomware attacks remained relatively rare and unsophisticated, often relying on simple trojans and basic encryption. But as the internet matured, so did the tactics. The mid-2000s saw the rise of more advanced ransomware viruses, and by 2010, screen-locking and file-encrypting variants were making headlines, targeting both individuals and organizations.
A significant shift occurred in 2013 when ransomware took a major leap forward with the introduction of powerful new encryption techniques and the use of digital currencies. Attackers started using strong encryption to lock files securely and demanded payment in Bitcoin, making it almost impossible for victims to recover their data without paying. The success of these tactics led to a wave of new ransomware campaigns, as cybercriminals realized the potential for profit. Organized groups soon began pouring time and resources into developing more sophisticated and targeted attacks, rapidly advancing the complexity and scale of ransomware threats.
Today, modern ransomware not only locks files but also threatens to leak sensitive data unless the ransom is paid, a tactic known as double extortion. This ongoing evolution underscores the need for constant vigilance and advanced security measures to protect against one of the most persistent and dangerous threats in the digital world.
How Does Ransomware Work?
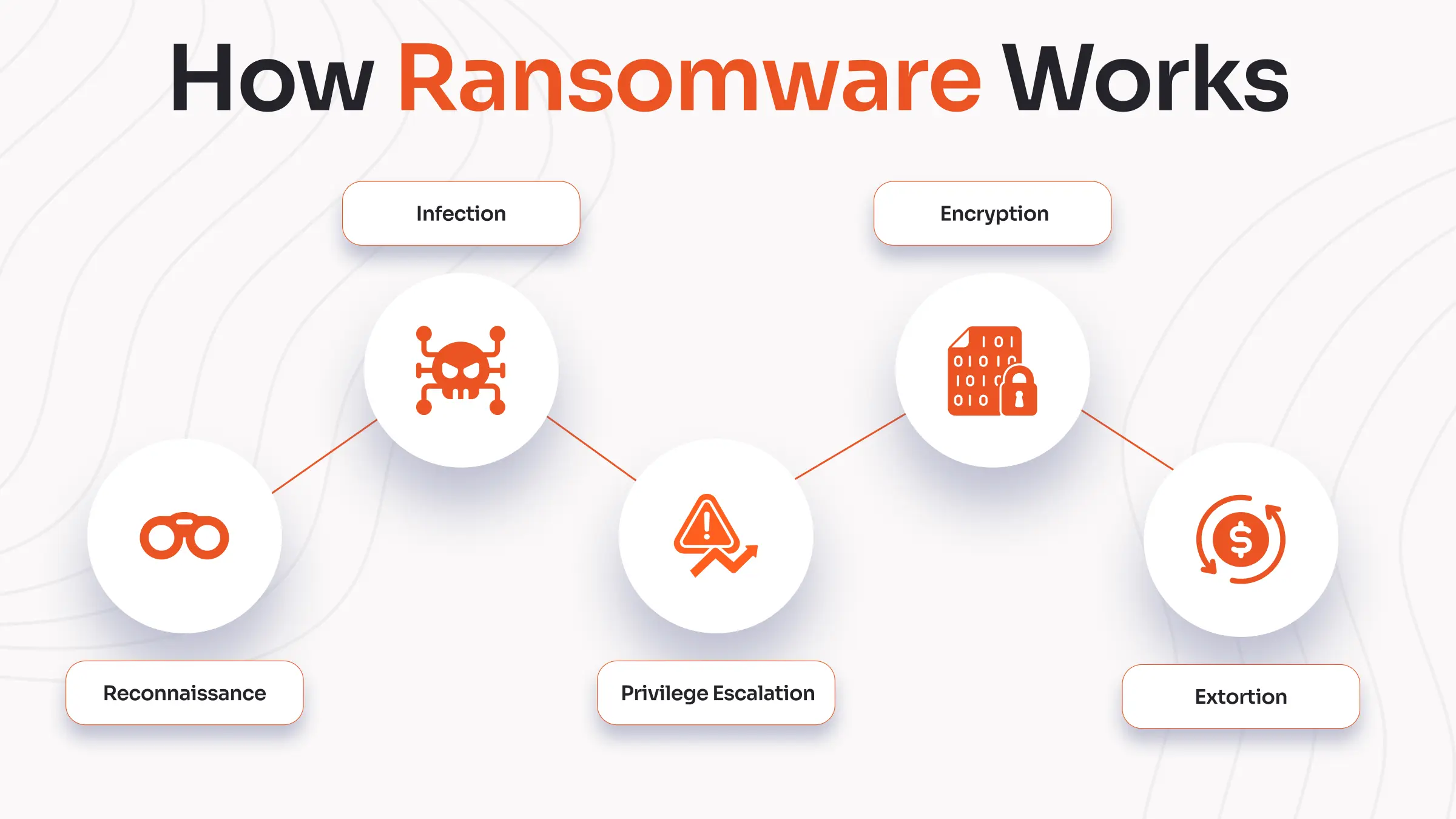
Ransomware attacks usually follow a series of steps, much like a break-in, but in the digital world. Here’s how it typically unfolds:
1. Reconnaissance - Scouting the Target
Before launching an attack, cybercriminals often “case the joint.” They look for weak spots in your defenses, such as outdated software, open network ports, or employees who might fall for phishing emails. For example, an attacker might search LinkedIn for new hires who may not be familiar with company security policies, making them easier targets.
2. Infection - Breaking In
Attackers use different tricks to get inside. The most common is a phishing email, think of it as a fake package delivery notice. If you click the link or open the attachment, the ransomware sneaks onto your computer. For example, a hospital employee might receive an email that looks like it’s from IT. The email says, “Update your password now!” and includes a link. And when the employee clicks, the ransomware gets installed. Sometimes, attackers exploit known software bugs or guess weak passwords to get in, similar to finding an unlocked window or door.
3. Privilege Escalation - Spreading and Digging Deeper
Once inside, the ransomware doesn’t always stop at one computer. It tries to move to other machines on the same network, searching for important files and sometimes stealing passwords to unlock more doors. This is like a burglar moving from room to room, looking for valuables.
4. Encryption - Locking Up the Valuables
After finding what it wants, the ransomware quietly locks up important files by encrypting them. It might even delete backups to make recovery harder. Suddenly, you can’t access your data, like finding all your valuables locked in a safe you don’t have the key for.
5. Extortion - The Demand
Typically, the victims of these ransomware attacks see a ransom note on their screens, demanding money (usually in cryptocurrency) for the decryption keys of their files. In some cases, attackers don’t just lock your data, they also steal a copy of it and threaten to leak or sell it if you refuse to pay. This is known as “double extortion,” because now you’re not only at risk of losing access to your files but also of having your sensitive information exposed publicly or sold to criminals.
Taking it a step further, some attackers use “triple extortion,” where they threaten to contact your customers, and partners, or even launch additional attacks like denial-of-service (DDoS) against your business if you still don’t pay. With each layer, the aim is to pile on more consequences and force victims into paying up.
In a nutshell, ransomware attacks are like digital burglaries: criminals sneak in, lock up your stuff, and demand cash to give it back. The best defense against such attacks is strong security, regular backups, and a healthy dose of skepticism with emails and links.
Types of Ransomware Attacks

Ransomware attacks constantly evolve to catch people off guard. Let’s break down the main types of ransomware attacks and see how each one plays its own game of digital hostage-taking.
1. Crypto Ransomware or Encryptors
This kind of ransomware scrambles your files so you can’t open them unless you pay for a special code. For example, if you suddenly can’t access any of your documents and see a message asking for payment to get them back, you’re likely dealing with crypto ransomware. Well-known examples include CryptoLocker and Ryuk.
2. Lockers Ransomware
Locker ransomware takes things a step further by blocking you from using your entire computer or device. You might turn on your laptop and find you can’t get past a ransom message that covers your whole screen, no access to your desktop, no opening apps, and nothing until you pay up.
3. Scareware
Scareware displays fictitious alerts about infections or system issues in an attempt to scare you into paying. Numerous pop-ups may appear telling you that your computer is infected and requesting that you purchase software to fix it. Sometimes, it just floods your screen with alerts, but it can also lock your device or install more malware if you fall for the trick.
4. Doxware
Doxware, also called Leakware, doesn’t just lock your files, it threatens to publish your sensitive information online if you don’t pay. Imagine a message saying, “Pay us, or we’ll leak your private documents or company secrets.” This adds extra pressure, especially for businesses worried about their reputation or legal trouble.
5. Ransomware as a Service (RaaS)
RaaS works like a criminal franchise. Skilled hackers create ransomware and rent it out to others who want to launch attacks but don’t have the technical know-how. The developers take a cut of every ransom paid, making it easier for more people to get involved in cyber extortion.
6. Wipers
Wipers are especially destructive. Instead of holding your data for ransom, they just erase it from your system. Sometimes, attackers pretend it’s ransomware to trick you, but their real goal is to destroy your files and cause chaos, not make money. Wipers have been used in cyberwarfare and sabotage for wiping out data beyond recovery.
Common Ransomware Attack Vectors
Attackers have become experts at picking the weakest link, whether it’s a convincing email, a forgotten software update, or a careless click on a website. Understanding how these threats get in is the first step to keeping them out.
Email Attachments and Phishing
Attackers send emails that look real, like fake invoices or delivery updates. If you open the attached file or click a link, ransomware installs itself. For example, you might get an email from “HR” about a new policy, but the attachment actually locks your files.
Exploit Kits
These are hacker tools hidden on websites. If you visit a site with an outdated browser, the kit finds weak spots and secretly drops ransomware onto your computer. Imagine browsing for recipes and, without clicking anything, your computer gets infected because your browser wasn’t updated.
Remote Desktop Protocol (RDP) Brute Force
Remote Desktop Protocol (RDP) lets you access computers from afar, but if you use weak passwords or leave RDP open to the internet, attackers can break in by guessing or stealing login details. After gaining access, they can spread ransomware throughout the network. This is a common way businesses get hit, especially if remote work setups aren’t properly secured.
Drive-by Downloads
Sometimes, just landing on a hacked or malicious website is enough for ransomware to start downloading in the background, without any clicks or warnings. These “drive-by” attacks take advantage of browser flaws or outdated plugins, making it easy for ransomware to slip through unnoticed.
How to Prevent Ransomware Attacks
Staying ahead of ransomware means more than just hoping for the best, it’s about putting smart, layered defenses in place so attackers never get an easy win. Here’s how you can build real protection into your daily operations, with practical steps and tools that make a difference.

Utilize Best Practices
Start with the basics: train everyone on your team to spot suspicious emails, avoid risky downloads, and use strong, unique passwords. Even the most advanced security tools can’t help if someone clicks a fake invoice or reuses “password123.” Regular security awareness sessions and simulated phishing tests keep everyone sharp and less likely to fall for common traps.
Reduce the Attack Surface
Think of your network as a building, every open door or window is a chance for ransomware to slip in. Reduce these entry points by disabling unused services, limiting who can install software, and segmenting your network so ransomware can’t spread freely. For example, you can use miniOrange’s Privileged Access Management (PAM) solutions to tightly control who gets access to sensitive systems for a streamlined way to manage these permissions.
Deploy Anti-Ransomware Solution
Modern threats need modern defenses. Traditional antivirus software often misses today’s fileless or stealthy ransomware. Instead, deploy advanced endpoint protection to spot suspicious activity before it becomes a crisis. These solutions act like vigilant guards, constantly watching for anything out of the ordinary.
Multi-factor Authentication (MFA)
The importance of MFA is rising as password-based attacks continue to compromise websites of all sizes. Hackers often succeed by using brute-force techniques, credential stuffing, or leaked passwords from other breaches. MFA adds a critical layer of defense by requiring users to complete an extra step, such as entering a code from their device or using a biometric scan. This added verification helps stop attackers in their tracks, even if they know the password.
Learn How to Select the Best Multi-Factor Authentication Types
Regular Backups and Patch Management
Ransomware’s power comes from locking up your data, so regular, secure backups are your safety net. Follow the 3-2-1 rule: keep three copies of your data, on two different types of media, with one stored offline or in the cloud. Test your backups often to make sure they actually work when you need them. At the same time, patch your software and systems as soon as updates are available, many ransomware attacks exploit known bugs that already have fixes.
Endpoint Detection and Response (EDR)
EDR tools actively hunt for threats, isolate infected machines, and help you respond quickly if something slips through. They give you visibility into what’s happening on every device, making it easier to catch and contain ransomware before it spreads. For organizations looking to centralize identity and access management alongside EDR, miniOrange’s IAM solutions offer a unified approach to securing users and endpoints.
By weaving together best practices, smart tools, and regular training, you make your organization a tough target for any ransomware attack. For more on strengthening your authentication and access controls, explore miniOrange’s authentication solutions and see how layered security can keep your data safe.
How to Remove Ransomware?
When ransomware strikes, panic is natural, but a clear, step-by-step response can make all the difference between a total loss and a controlled recovery. Acting quickly and methodically not only limits the damage but also helps you avoid costly mistakes that could make things worse. Here’s how to take back control if ransomware ever locks down your systems:
Isolate the Infection Immediately
First, cut off the attack’s reach. Disconnect the infected device from the network, unplug the Ethernet cable, turn off Wi-Fi, and disable Bluetooth. This stops ransomware from spreading to other computers or shared drives. If you’re in an office, alert your IT team right away so they can contain the threat across the network.
Identify the Ransomware Strain
Knowing exactly what you’re dealing with helps you plan your next move. Use a reputable ransomware identification tool or check the ransom note for clues. Some strains have known decryption tools, while others require a different approach.
Do Not Pay the Ransom
Paying the attacker might seem tempting, but it rarely guarantees you’ll get your files back. You could also mark yourself as an easy target for future attacks. Instead, focus on proven recovery steps.
Eliminate the Ransomware
Use trusted anti-malware or ransomware removal tools to clean the infected system. Run a full scan and follow the software’s instructions to quarantine or delete malicious files. If the infection is advanced, you may need to boot into Safe Mode or use a rescue disk for stubborn threats.
Restore from Backups
Once you’ve cleared the ransomware, restore your files from clean, recent backups. Make sure the backup itself isn’t infected before copying files back. This is where regular, offline backups really pay off, if you’ve kept them up to date, you can recover quickly with minimal data loss.
Patch and Strengthen Defenses
After recovery, update all software, reset passwords, and review your security practices. If you haven’t already, implement multi-factor authentication and endpoint protection to prevent a repeat incident.
Report the Attack
Notify relevant authorities or regulatory bodies if required, especially if sensitive data was involved. Reporting helps track ransomware trends and could aid investigations that protect others in the future.
Removing ransomware is never pleasant, but a calm, structured response puts you back in control. With strong backups and a solid incident plan, you can turn a crisis into a lesson, and come out stronger on the other side.
The Role of Zero Trust in Ransomware Defense

Zero Trust security operates on a simple rule: trust nothing, verify everything. Instead of giving users or devices blanket access once they’re inside the network, it requires constant proof of identity and intent at every step. It is especially effective against ransomware attacks, which often spread by exploiting excessive permissions and moving laterally between systems.
The following are some key ways in which zero trust helps defend against a ransomware attack:
Continuous Identity Checks
Every access request gets double-checked, not just at login. If an attacker grabs an employee’s password, they still need to pass multi-factor authentication and device checks. For example, if someone tries to log in from a new country or an unrecognized device, Zero Trust will flag or block that attempt.
Least Privilege Access
Access is limited strictly to what individuals need to perform their tasks. If ransomware infects a finance team member’s laptop, it can’t jump over and start encrypting engineering files or cloud backups.
Micro-Segmentation
With Zero Trust, you separate your network into distinct, manageable sections. Think of it as putting fire doors between every room, if ransomware gets into one area, it can’t spread unchecked. For instance, a breach in the marketing department won’t automatically put customer databases at risk.
Device Health Verification
Devices must meet strict security standards before accessing sensitive data. If your laptop’s missing critical patches or running outdated antivirus, Zero Trust blocks it from connecting to important systems. This stops ransomware that tries to sneak in through unpatched vulnerabilities.
And as more companies move to hybrid work and cloud apps, Zero Trust’s flexible, always-on approach keeps defenses tight, no matter where your team logs in from.
Stay Secure with miniOrange’s Ransomware Defense
Serving more than 25k+ organizations globally and backed by over ten years of experience in cybersecurity, miniOrange is your security software solution provider you can rely on for round-the-clock protection against ransomware. As your dedicated partner, our all-in-one security platform delivers solutions like Multi-factor Authentication (MFA), Single Sign-On (SSO), and Cloud Access Security Broker (CASB), specifically designed to address the vulnerabilities cybercriminals target. With 6,000+ ready-to-use integrations, miniOrange ensures seamless protection for both legacy systems and the latest cloud applications.
Our end-to-end identity and access management solution suite provides complete oversight and control over sensitive information. Plus, miniOrange’s expert support team is available 24/7, so your security never takes a break.
See how miniOrange can strengthen your ransomware defenses, sign up now for a 30-day free trial, and experience robust protection firsthand.
Conclusion
Defending against ransomware now requires more than just a single security measure. Real protection comes from combining several layers that work together. By using different types of authentication, such as one-time passwords (OTPs), security keys, and biometrics, you create a system that is much harder to compromise. For example, biometric authentication advantages include unique physiological identification, resistance to password theft, and quick and convenient access that is difficult for attackers to replicate. These features make biometric authentication one of the most effective factors in modern MFA solutions. When supported by context-based authentication, your security shifts from basic protection to active prevention. This approach not only lowers risk but also gives you the confidence to face future threats with clarity and control.
FAQs
What Is a Ransomware Attack and How Can It Be Prevented?
A ransomware attack is when malware locks or steals your data, demanding payment for its release. Prevent it by using strong authentication (like MFA and biometrics), keeping software updated, training staff to spot phishing, and backing up data regularly.
What Are the Five Stages of a Ransomware Attack?
A ransomware attack typically goes through five stages, which are as follows:
- Initial access (often via phishing or exploits)
- Lateral movement (spreading through the network)
- Privilege escalation (gaining higher-level access)
- Data encryption or exfiltration
- Ransom demand and extortion
What Is the First Action Against Ransomware?
Immediately isolate the infected device from the network to stop the spread. Then, alert your IT/security team and begin an incident response.
Can VPN Stop Ransomware?
Although a VPN encrypts your internet traffic, ransomware cannot be blocked by it. Attackers can still deliver ransomware through phishing, exploits, or compromised credentials, even over a VPN.
Can You Recover Ransomware Files?
You can recover files if you have clean, recent backups stored offline. Decryption tools may exist for some ransomware strains, but paying the ransom doesn’t guarantee recovery.
What Is the Most Effective Control Against Ransomware?
A multi-layered defense: strong authentication (especially MFA and biometrics), PAM, regular backups, patch management, and real-time monitoring.
How Long Do Ransomware Attacks Last?
The attack itself can unfold in minutes, but recovery may take days or weeks, depending on backup availability, the scope of infection, and incident response readiness. The faster you detect and contain the attack, the less downtime and damage you’ll face.




Leave a Comment