In today's world of remote work, hybrid IT environments, and increasing cybersecurity threats, securing access to enterprise applications, especially legacy and on-premise ones, has become more critical than ever. That’s where Access Gateways come in.
Whether you're looking to modernize app access, add Single Sign-On (SSO) and Multi-Factor Authentication (MFA), or move away from traditional VPNs, Access Gateways offer a secure and scalable solution.
In this guide, we’ll explain exactly what an Access Gateway is, how it works, why businesses use it, and how solutions like miniOrange Access Gateway can help streamline secure access across your infrastructure.
What is an Access Gateway in Cybersecurity?
An access gateway in cybersecurity is like a ‘digital gatekeeper,’ which mediates access between the internal resources and external users.
This gatekeeper sits at the border of the network (or in the cloud) and starts authenticating and authorizing users to protect internal resources (data and apps).
The top traits of an access gateway are:
- Granular Access Control: Entry to resources is based on user roles, devices, location, and other relevant information.
- Multi-Factor Authentication (MFA): MFA can be clubbed with an access gateway tool to add an extra layer of security.
- Secure Proxy: A reverse proxy acts to shield backend apps from vulnerabilities.
- Centralized Authentication System: A combination of Single Sign-On (SSO) with the access gateway tool removes repeated authentication and creates a single channel for user access.
Now that we’ve a comprehensive understanding of the access gateway, let’s move on to its benefits and role in enterprises.
Why are Access Gateways Critical for Modern Enterprises?
Here are the top four reasons why access gateways are essential for modern enterprises.
1. Employees are Remote
The pandemic gave rise to remote work conditions and also gave employees the liberty to work from anywhere (not only from their homes) and on any devices. Conventional parameters of safety were no longer sufficient.
This is where an access gateway solution comes into play, a solution that authorizes and authenticates every user, at any time, irrespective of the location.
2. Presence of Apps on Cloud, Hybrid, and On-Prem
Nowadays, enterprises have their apps on all types of environments: cloud, on-prem, or hybrid. Managing safe access to this web of environments can be daunting without a centralized repository.
An access gateway fills the gap of a centralized channel, making user access easy.
3. To Overcome the Hurdle of Traditional VPNs
Virtual Private Networks (VPNs) offer access to a wider network, granting more permissions to users than necessary. So, VPNs can turn out to be both a compromised tool for user access and a helpful one if wanting to access a wide range of data.
Apart from being over-permissive, VPNs are also difficult to scale because, as the traffic and data grow, they can become bottlenecks, resulting in downgraded performance and slow connections.
Effective scaling requires substantial investments in the VPN infrastructure, last-mile network links, system redundancy, and more.
Due to the above reasons, access gateways prove to be a go-to solution for security for modern enterprises.
4. Access Gateways Secure Your Digital Perimeter
Access gateways provide an identity-aware and centralized access control, which helps to secure the digital perimeter of enterprises.
This stage is achieved through the implementation of least privilege access at the application level. Plus, MFA and SSO solutions are clubbed together with an access gateway to form a strong defense against cybercrimes.
How Does an Access Gateway Work Behind the Scenes?
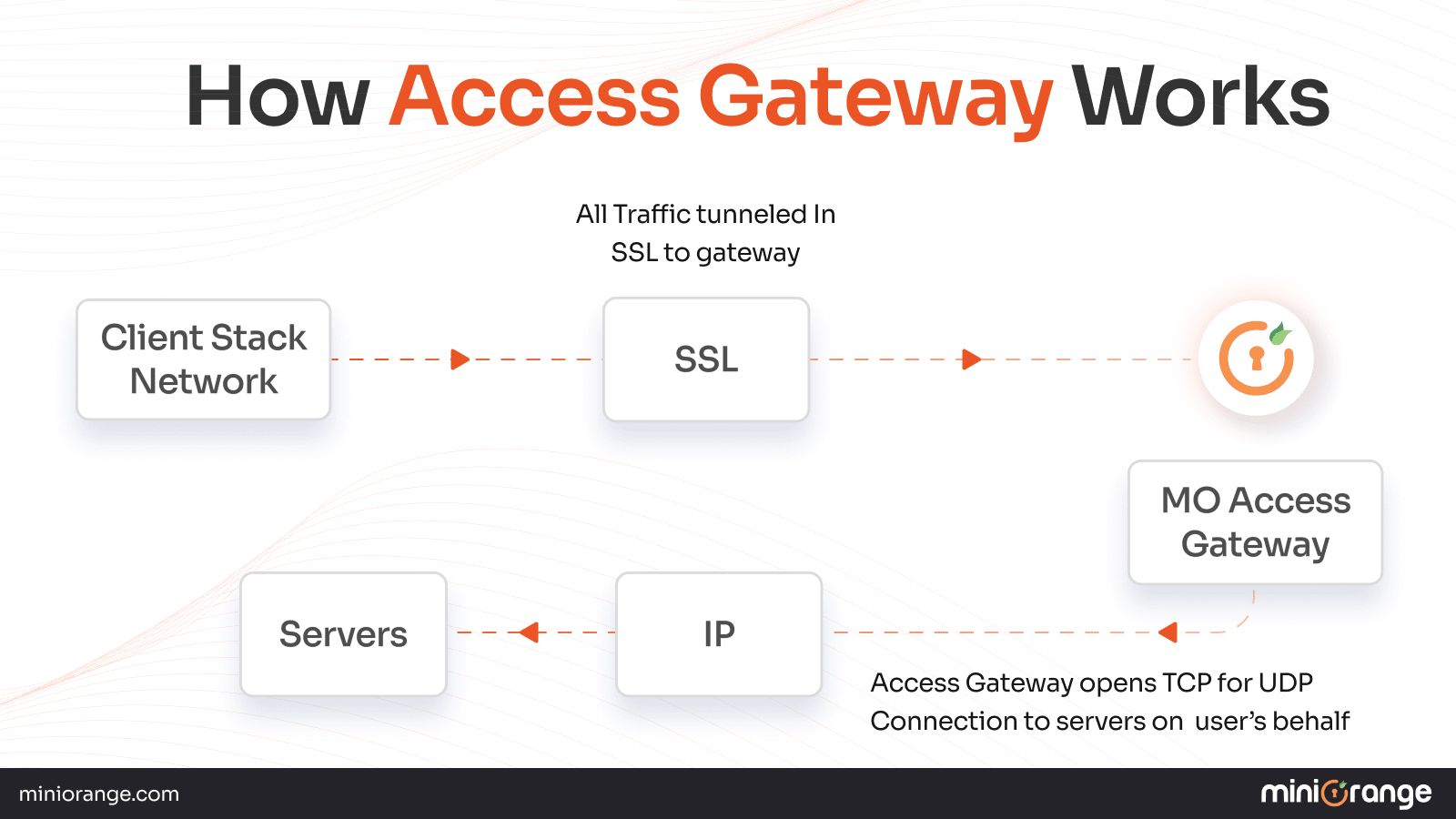
Here’s what you need to know about the mechanics of an access gateway so you can use it in a better way.
What is the Access Flow in an Access Gateway Solution?
Let’s understand what the access flow is in an access gateway solution.
- User Tries to Access an App: The user tries to log in to an application.
- Gateway Intercepts and Redirects to an Identity Provider: The access gateway intercepts the user login attempt and redirects the user to an Identity Provider (IdP) such as Google, Azure AD, or Microsoft for authentication.
- The MFA Challenge: In case the MFA is enabled to gain access to an app, the user is required to complete their authentication via an OTP, an authenticator app, or biometrics.
- Access Policy Validation: The access gateway scrutinizes access policies such as least privilege, data access, Role-Based Access Control (RBAC), etc.
- Secure Proxy Access to the App: Once the users are validated, they’re routed to the applications or resources via a proxy server. This server adds an extra layer of security by hiding the user’s IP address, inspecting traffic for malware, and encrypting the traffic between the user and the proxy server.
With the miniOrange Access Gateway, this flow is automated and scalable, integrating seamlessly with your existing SSO or Identity and Access Management (IAM).
Key Benefits of Using an Access Gateway
Let’s look at the benefits of using an access gateway tool over traditional VPNs and how miniOrange can help to take these advantages a notch higher.
What are the Top Benefits of Access Gateways Over Traditional VPNs?
1. Application-Level Access
Traditional VPNs permit users to access the entire network, but with an access gateway, this isn’t possible. It restricts users to certain resources and apps that are needed to complete a task.
This minimizes the risk of potential malicious attacks that could lead to data breaches, fraud, or scams.
2. Granular Policy Enforcement
The access gateway system is designed to enforce a detailed access rule. It allows you to control who can gain entry to what, from where, and when.
So, this level of admittance to resources is missing in the traditional VPNs, making it more appealing for enterprises looking to opt for group-based permissions.
3. No VPN Clients Needed
There’s absolutely no need to maintain a special VPN software. The entry to resources is browser-based, and MFA and SSO solutions make the experience more secure.
Absence of VPN software decreases IT overhead costs and makes the onboarding and offboarding of users much easier.
4. Supports Legacy and Modern Apps Alike
Access gateways are compatible with both legacy systems and modern cloud-based apps.
With features such as header-based injection, the legacy systems can be protected to secure the access flow without making any major changes to the application itself or rewriting the code.
5. Reduces Attack Surface
Since users are allowed to access only what they require, and the backend apps are not exposed to the public network, the risk of compromises is reduced.
Hackers can no longer move laterally via the network or even detect hidden resources, which is a common vulnerability with VPNs.
6. Easier Compliance
Access gateways bank on a centralized logging system and policies, making it easier to comply with regulations such as GDPR, HIPAA, or SOC 2.
You can generate reports quickly and know who accessed what, which is essential for investigations and audits.
How Does miniOrange Amplify These Benefits?
Here’s how our solution will help you out:
1. Quick Deployment on Cloud or On-Prem
miniOrange provides flexible deployment options, allowing you to set up access gateways on either cloud or on-prem, and sometimes both.
We offer detailed instructions on how to install the access gateway in your system, along with consultation calls around the clock.
2. Built-in SSO, MFA, and Adaptive Policies
The miniOrange access gateway solution is equipped with SSO and MFA solutions that make sure the users log in once and gain access to all authorized apps without repeated logins.
A combination of SSO and MFA with an access gateway adds layered security, so the resources are protected from invaders.
3. Detailed Access Logs for Auditing
Every user login activity is tracked and monitored in detail (who, what, when, and why something was accessed). User logs are centralized and readily accessible via the admin portal.
Logs are a great tool for detecting malicious activity and quickly responding to threats, preventing major cyberattacks.
4. Header-Based Injection for Apps
Header-based injection attacks involve manipulating HTTP headers by adding spiteful content within a request. The access gateway misinterprets the added content, resulting in a cyberattack.
Now, header-based injection attacks can occur for apps that lack SAML or OIDC protocol support. However, miniOrange access gateway tools work with apps without SAML or OIDC protocols.
This is achieved with HTTP security headers, Web Application Firewalls (WAF), usage of HTTPS, and more.
5. Custom Branding and Control Panel
miniOrange offers a customized admin portal, so you can apply your brand logo, schemes, and domains. The control panel comes with a dashboard for handling policies, users, logs, and apps.
Access Gateway vs. VPN: What’s the Difference?
| Feature | VPN | Access Gateway |
|---|---|---|
| Access Level | Network-wide | App-specific |
| Security Model | Perimeter-based | Identity-based (Zero Trust) |
| User Experience | VPN client required | Browser-based login (SSO/MFA) |
| Legacy App Support | Limited | Full via header injection |
| Deployment Flexibility | Static setup | Cloud, on-prem, hybrid (miniOrange) |
miniOrange Access Gateway is designed to replace outdated VPNs with zero-trust, scalable security.
Related Read: Access Gateway vs VPN – A Better Fit for Zero Trust
Real-World Use Cases for Access Gateways
Let’s have a look at what problems an access gateway solution solves:
1. Temporary Vendor/Contractor Access with an Expiration
Sometimes, you have to allow external entities, like contractors or vendors, when you’re outsourcing work, to access internal resources.
You can create access gateways to set up time-based entry to apps, which can be revoked after a certain duration.
2. Enabling Legacy Apps for External Users Securely
It is quite difficult to secure legacy apps for external users, as they lack authentication systems used in today’s time, such as biometric authentication or authenticator apps.
However, this issue can be resolved with the miniOrange access gateway solution, which offers SSO integrated with MFA software, permitting external users to log in safely to the legacy systems.
3. Implementing Zero Trust Strategies
The zero trust framework operates on the principle that no device or user is trusted by default, irrespective of whether they’re inside the network or outside.
The miniOrange access gateway verifies every user and device request and applies access policies. This reduces the lateral movement of hackers, safeguarding your business.
With miniOrange, you can configure time-bound access, geo-restrictions, and detailed user-level logging, all from one console.
Top Features to Look For in an Access Gateway
Let’s have a look at the top-notch features in an access gateway tool.
Which Features Matter Most in Access Gateway Solutions?
- Integration with IdPs: Access gateways can be easily integrated with Identity Providers (IdPs) such as Google, Azure AD, Okta, and more.
- Reverse Proxy Support: Here, the legacy apps are safeguarded from vulnerabilities, as they don’t support modern authentication techniques.
- Granular Access Policies: Control access to internal resources or applications based on user roles, IP address, device, or location.
- Audit Logs and Compliance Reports: Craft detailed logs of user activities and also compliance reports, which can be used for audits and to detect malicious activities.
- Multi-Tenant and Role-Based Admin Portals: A multi-tenant creates an isolated space (tenants) within the same access gateway. Whereas, with role-based admin portals, different levels of privileges can be assigned to the users.
How Does miniOrange Check All these Boxes?
- Out-of-the-Box SSO/MFA Integrations: So, miniOrange taps into one-of-a-kind SSO and MFA solutions that blend together with access gateways and can be configured easily with multiple IdPs.
- Header-Based Login Support: Here, the user authentication data passes through the HTTP headers and is usually used for SSO in on-prem or legacy systems.
- Real-Time Risk Scoring and Adaptive Access: Allows you to evaluate the risks associated with every user login attempt and adjust security requirements accordingly. This is a dynamic way of offering a flexible defense system.
- Comprehensive Documentation and 24/7 Support: Simply obtain a detailed document on how to install the access gateway in your system, with support from the experts around the clock.
- Scales from Startups to Enterprise Environments: Access gateway systems are more scalable than VPNs, making them an ideal choice for all business structures. Also, you can deploy them on any environment: cloud, hybrid, or on-prem.
How Access Gateways Fit Into Zero Trust Architecture
Here’s a comprehensive overview of the critical role played by access gateways in establishing zero trust architecture.
What Role Does an Access Gateway Play in Zero Trust?
It is an essential component of the zero trust architecture because it verifies every user access, irrespective of the user’s network or location (even if the user is an insider).
Furthermore, every entry into an application is cross-checked and validated against the organization’s policies. Once the user is granted permission, access is limited to certain apps or resources to maintain safety.
Moreover, logs are created after every user activity, and these are reviewed regularly to spot any anomalies.
miniOrange’s Access Gateway integrates with Zero Trust engines and enforces contextual policies per user, session, and app.
Choosing the Right Access Gateway: Why miniOrange Stands Out
Let’s dive deeper into why miniOrange can be a better solution for you.
Why is miniOrange the Ideal Access Gateway Solution?
Because we have proven expertise in IAM, SSO, MFA, PAM, and other secure access tech.
Our access gateway solution offers a wide range of support to the legacy systems, on-premises and in the cloud. The miniOrange access gateway solution is developed with zero trust principles in mind, offering solid security systems that validate users and devices before granting permissions.
Additionally, miniOrange solutions are trusted by over 25000+ global customers, making us a pioneer in the field of IAM and related technologies.
Whether you're a small IT team or an enterprise security leader, miniOrange Access Gateway simplifies, secures, and scales with your needs.
Final Thoughts: Modernize Your Access Strategy Today
The pandemic made sure that the digital landscape grew, giving way to technologies such as an access gateway to protect resources from external threats.
Access gateway is a safe, secure, scalable, and powerful alternative to traditional VPNs, ensuring identity-driven access to applications.
With the miniOrange access gateway solution, it is possible to build a zero-trust architecture and protect your business from cybercrimes in today’s time.





Leave a Comment