SIM swapping attacks are rising, putting SMS-based OTPs at risk. An authenticator app can provide a solution that is less penetrable by hackers. If you find yourself in a situation where internet access is unavailable at a specific time or location, an auth app can provide the solution. SMS- or email-based login solutions offer the security of multi-factor authentication. By 2025, authorities in Singapore, India, Malaysia and the U.S. (such as FINRA and the U.S. Patent and Trademark Office) will move away from SMS-based OTP delivery as an approved way to 2FA login because of SIM-swapping and SS7 interceptions.
The rate of TOTP-based authenticator adoption, as stated in a survey by Statista in 2023, is as high as 68%, rather than just 56% for SMS OTPs and 51% for email OTPs. This means organizations are favoring getting OTPs via authenticator apps even more than ever before.
In this blog, we extensively discuss the topic of authentication, what an authenticator app or a verification app, its working, its types, uses and how miniOrange can help you achieve your goals with the help of an authenticator app using multi-factor authentication methods.
What is an Authenticator Application?
Whenever you log in, an authenticator app (also known as a verification app) sends a push notification or produces a one-time code for your device. You type that code into the app or touch "Approve." It uses time-based or hash-based techniques to sync your phone and the server behind the scenes, so only you can sign in.
An authenticator app is mobile or desktop software that works with your current password. Google Authenticator, Microsoft Authenticator, or miniOrange Authenticator App could be the one you need. Each of these apps makes secure codes that are only good for a short period. You scan a QR code in your authenticator app to create a unique secret key when you sign up for an account. Your authenticator app will need to prove who you are in real time every time you want to log in by entering an instant new code generated.
Adding this "something you have" layer lowers the danger of account takeover by more than 99%, stops phishing attacks, and meets regulatory requirements, all without slowing down daily operations. An authenticator app gives you simple yet effective protection in the form of one of the most secure multi-factor authentication methods, whether you're protecting your email or your private or company data.
How Does Authenticator App Work?
Understanding how an auth app works provides you confidence and helps you fix problems when codes don't work. Authenticator apps make one-time passwords (OTPs) using a secret key and either a time or usage counter. Here’s how it all comes together:

Time-based one-time passwords (TOTPs)
A TOTP combines your secret key with the current time stamp to generate a six-digit code that changes every 30 seconds (RFC 6238). Because codes only last for a short time, stolen or intercepted codes are worthless within seconds. This is why TOTP is the backbone of most major MFA systems.
HMAC-based one-time passwords (HOTPs)
RFC 4226 says that HOTPs mix your secret key with a counter that keeps becoming bigger. The counter goes up and makes a new password every time you ask for a code. HOTP codes, on the other hand, stay valid until you use them. This is useful if your device is offline for a short time.
QR codes for easy setup
When you enable an authenticator app, the service displays a QR code embedding your unique secret key. Scanning that code with your auth app auto-configures the secret—no manual entry, no typos. This one-scan setup takes under 10 seconds and ensures accuracy from the get-go.
Time-syncing
Accurate timekeeping is vital. Authenticator apps sync with internet time servers to align your device clock with the server’s. Even a drift of 30 seconds can trigger “code mismatch” errors, so most apps include automatic or manual time-correction tools to keep your logins seamless.
How to Link Your Auth App?
- You open your account’s security settings for multi-factor authentication on a computer and choose “Enable Authenticator App.”
- The site displays a QR code that encodes your unique secret key.
- You launch the auth app on your phone, scan the QR code, and the app automatically stores that secret.
- With the secret in place, your phone and the server share a synchronized key for future code generation.
How Do You Log in Using a Time-Sensitive Code from the Authenticator App?
- When you sign in, you launch the authenticator app and see a six-digit code that refreshes every 30 seconds. You type (or paste) that code into the login screen on your computer.
- The server calculates the expected code using the same secret key and timestamp—if they match, you’re in.
- This simple, offline-capable step thwarts phishing and boosts security without slowing you down.
Using an authenticator app is easy and safe, and miniOrange is your partner for security software solutions that provide the toughest security and convenient logins at your fingertips.
The Best Authentication Apps Compared
Choosing the best authenticator software will help you find the right mix between security and ease of use. Here is a brief overview of six top solutions, each designed for a particular use scenario, from commercial deployments to settings that put privacy first.
miniOrange Authenticator
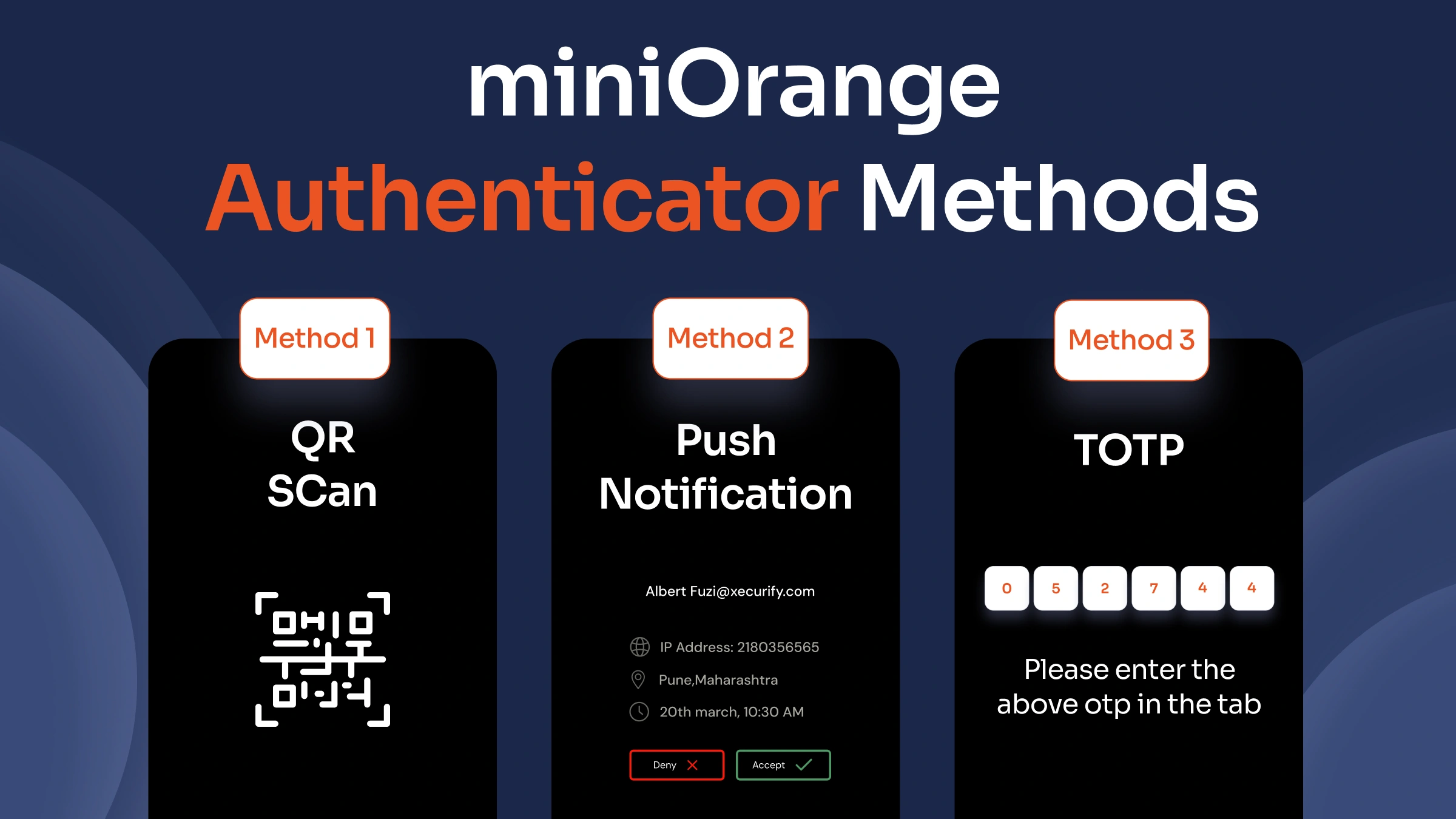
With miniOrange Authenticator, businesses can regulate MFA down to the smallest details, including 6- to 8-digit TOTP, QR codes, and one-tap push approvals. It works perfectly with the miniOrange IAM platform and enforces regulations across more than 200 apps. Your TOTP codes are time sensitive, ranging from 15 seconds to 60 seconds, allowing offline access in use cases where connectivity is limited. The miniOrange Authenticator app is available on the App Store and Google Play Store for your phones and tablets and will also support wearables. It is easy to configure by scanning a QR code from the miniOrange MFA software dashboard when using it for the first time. You will never lose access since your cloud backup is encrypted and your keys are managed by policy.
Google Authenticator
Google Authenticator is a free, lightweight TOTP solution that works even when you're not connected to the internet. You scan a QR code once, and then every 30 seconds, you can make six-digit codes without being connected to the internet. It can manage an unlimited number of accounts and installs in seconds, making it perfect for small companies and students. Just remember to export your keys by hand before you transfer devices.
Microsoft Authenticator
Microsoft Authenticator combines TOTP and push-based MFA with biometrics or a PIN to let you sign in without a password. You can impose conditional access controls and single sign-on across all of your business apps because they are deeply integrated with Azure AD and Microsoft 365. Keys automatically back up to your Microsoft account, so staff can get back in right away. This tool reduces the number of help desk tickets and makes big rollouts go more smoothly.
LastPass Authenticator
LastPass Authenticator adds easy two-factor authentication to your LastPass vault using push notifications and codes that change over time. Users can unlock their vault and MFA keys with biometric data and encrypted backups, so they only need one interface. Cross-device recovery cuts down on support calls and keeps students and workers moving. If you already trust LastPass to keep your credentials safe, it's a good choice.
Authy
Authy is different since it lets you sync your TOTP keys across many devices and backs them up in the cloud with encryption. You can install it on phones, tablets, and PCs, and codes will keep being made even if you lose your internet connection. The app is protected by a PIN or biometric lock, and team users may utilize secure sharing settings to ensure that everyone has access to the content. Group account management and recovery solutions make it easier for decision makers to control.
2FA Authenticator
2FA Authenticator is an open-source way to do TOTP-based MFA that puts privacy first. It reads QR codes to set up right away and makes codes that work offline and are only good for a short period without ever contacting other servers. Encrypted import/export and limited permissions protect user privacy, making it great for students, nonprofits, and groups who are on a tight budget. You receive strong security without being locked onto a vendor.
Each program has its own benefits, such as easy cloud backup, strong integration with other apps, or open-source transparency. Choose the authenticator that works best for your workflow and risk profile by weighing these features against your personal or business needs.
How to Choose Authenticator Apps for Your Purpose?
As a leader, you have to find a balance between making things easy for users, following the rules, and lowering risks. Choosing the appropriate authentication solution can help you avoid breaches (MFA stops 99.9% of account compromise attempts), lower the number of help desk tickets, and fulfill standards like PCI-DSS or ISO 27001—all while keeping end users happy.
Evaluation Criteria for Authenticator Apps
1. Compatibility
• Make sure that your identity providers (miniOrange, Azure AD, Okta, Ping) and SSO portals work well together.
• Make sure that iOS, Android, Windows, macOS, and browser extensions all work together so that all employees can sign up without having to do anything special.
2. Following the rules
• Choose an app that natively supports TOTP (RFC 6238) and HOTP (RFC 4226) to make sure it works with both cloud and old systems.
• If you want to protect yourself against phishing attacks and progress toward passwordless logins, be sure that FIDO2 or WebAuthn is supported.
3. Recovery and Key Management
• Search for encrypted backup or key-escrow options that adhere to policies. These tools help you restore or revoke credentials from one place if a device is lost.
• Check how well it works with your current key management service (KMS) or hardware security modules (HSMs) for business-level control.
4. Usability for the end user
• Choose apps that let you approve things with one swipe and use biometrics to get rid of the need to enter codes by hand. This can save login time by up to 50%.
• Set up a pilot group to see how many help-desk tickets go down and get feedback on the onboarding process.
5. Trust and support from the vendor
• Ask for SOC 2 Type II or ISO 27001 accreditation, public vulnerability disclosures, and a clear schedule for patching.
• Check the SLAs, support channels, and roadmap visibility to make sure the vendor can grow with your business.
Have your security and IT teams do a brief pilot. Monitor metrics such as the number of registrations, successful logins, and the number of MFA-related tickets. Use those findings to make a deployment plan that balances security, cost, and user experience. Such an approach will make MFA a competitive advantage instead of a problem.
How to Use Authenticator Apps with miniOrange
Ready to make your multi-factor authentication easier without making the user experience worse? In only a few minutes, you can get miniOrange Authenticator up and running.
- Go to console.miniorange.com and make a free account.
- Turn on two-factor authentication in Security Policies and choose miniOrange Authenticator.
- Get the miniOrange Authenticator app from the App Store or Google Play and install it.
- You can either scan the QR code that shows up on your console or type the secret key into the app.
- To check that everything is set up correctly, either approve the test push notice or input the six-digit TOTP.
- From now on, every time you log in, you'll need to input a one-tap push or time-based code. This is protected by corporate controls, cloud-based recovery, and centralized reporting.
Get enterprise-grade MFA and easy recovery for your accounts today. You may start protecting your logins right away by signing up for a miniOrange MFA trial.
Authenticator Apps Usage Trends Forecast
- The market for authenticator apps will rise from $2 billion in 2025 to $6 billion by 2033 (15% CAGR).
- Tens of millions of people are using authenticator apps to better protect their digital identities.
- Authenticator apps are moving away from one-time passwords (OTPs) and toward passkeys, biometrics, and credentials that are tied to a specific device.
- More privacy-focused and open-source authenticator apps are coming out, along with those from big tech companies.
- Authenticator apps are becoming more like decentralized identity and unified IAM platforms.
Get Started
For security that can't be hacked and easy integration with IAM, get the miniOrange Authenticator App from the App Store or Google Play.
FAQs
Does an authenticator app work offline without a network?
Yes, an authenticator app can work without being connected to the internet. It uses a time-based one-time password (TOTP) method to make codes depending on the current time and a secret key that is kept on your device. You don't need a phone or internet connection to acquire your code and log in to your accounts. This feature is mostly useful for logging in at places without connectivity, such as secluded or highly secure private environments.
Do I need an authenticator app?
You should use an authenticator app to make your online accounts safer. It makes it much tougher for someone to get into your accounts without your consent because it adds a second layer of protection on top of your password.
What's the easiest authentication application to use?
Microsoft Authenticator and Google Authenticator are easy to use for a lot of people because they are straightforward to set up and have a user-friendly design. miniOrange Authenticator is another popular choice that lets you approve requests with a push. There is a lot of support for all of these apps, and they all have clear directions for adding accounts.
Can an authentication app be hacked?
Authenticator applications are safer than SMS codes, but hackers can still get into them. Your accounts could be at risk if someone gets access to your device or fools you into giving them your backup codes. Always keep your backup codes and devices safe.
Are OTP authenticator apps secure?
Authenticator apps are thought to be particularly safe because they make codes on your device instead of sending them through SMS, which can be intercepted. They lower the likelihood of someone getting into your account without your permission by a lot. It is one of the most secure multi-factor authentication methods.
Can I get push notifications for approval on the authenticator app?
Yes, certain authenticator apps, such as Microsoft Authenticator, send push alerts to let you know when you can sign in. But for your gadget to get and respond to these notifications, it needs to be connected to the internet.
What kind of encryption does an authenticator app use?
Authenticator apps employ a time-based one-time password (TOTP) algorithm that makes codes based on a shared secret key and the current time. Your device keeps the shared secret safe, and the process employs regular cryptographic methods to keep your codes private.



Leave a Comment