Not all single sign-on (SSO) solutions are made equal; some help with federated identities across multiple autonomous domains, and others help you log in to your favorite SaaS apps on the same domain. Single sign-on brings an intuitive dashboard with single-click logins everywhere. But how can you log in to applications that do not support a protocol? Well, that’s even possible today. Identity security has advanced significantly beyond merely safeguarding users and their data. It adds next-level convenience to our advanced multi-cloud and multi-device environment. While traditional SSO centralized logins within a corporate network, federated SSO extends access beyond that network's walls. This type of integration involves sharing authentication credentials with multiple cloud and external applications that utilize protocols such as SAML, OpenID Connect, and others. This blog clarifies federated vs. traditional SSO, shows when to use each, and demonstrates how miniOrange makes federated SSO simple to deploy. 2. Core Components of SSO vs. Federated SSO
More passwords make the system riskier and harder for the user to remember. SSO's major goal is to reduce the number of passwords in a system to the lowest possible level while still keeping users safe and making it simple for them to use. Both SSO and federated SSO try to make logging in less of a hassle at different levels and in different areas.
Single Sign-On
With SSO, users can log in to their apps safely without having to remember a list of passwords. It lets consumers log in to all of their favorite apps without putting their security at risk after they verify their identity once.
Core Components of Traditional SSO
- Access to Different SSO Apps: You can use all the apps you need with just one login. This makes it easier for users to remember various passwords by giving them a single-click option to access all applications through an easy-to-use dashboard.
- SSO Authentication Portal: A single, safe login page where users may enter their credentials or use an MFA method, like logging in using OTPs.
- Identity Database: A database (such as an identity provider, LDAP, or active directory) stores users and their identity information, like usernames, passwords, and profile traits. This known source checks usernames and passwords.
- Access Token: When the app sends an authentication request to the identity provider, it gets back a signed access token or assertion (usually a cookie or JWT) that apps use for the session.
- Session Management: Keeps track of how long tokens are valid for and takes care of automated renewals or logouts. When users log out, session management automatically prevents them from accessing apps.
Benefits of Traditional SSO
- Users forget fewer passwords and ask for password resets less often
- The IT staff gets roughly 50% fewer password-reset tickets.
- Centralized authentication makes it easy to add and remove users right away.
- Store all user session logs in one place for audits
- Make sure that all apps and systems follow the same rules for groups.
Federated Single Sign-On (SSO)
If your business depends a lot on customers, campuses, or partners from other countries, its trusted identity needs to be able to work across borders and in different domains. Federated SSO connects identity systems across domains so that SSO can work for more than one enterprise.
The main components are
- Identification Provider (IdP): Checks the user's identification against saved credentials or verified sources like single-use codes or PINs and then issues security tokens (via SAML or OpenID Connect).
- Service Provider (SP): Uses tokens given forth by the IdP to give users access to applications based on user groups, granular-level access, or individual user traits.
- Trust Relationship: Ensures that the SP only sends real authentication requests to the IdP using digital certificates or shared secrets. These connect IdP and SP using XML metadata exchange via email, secure file sharing, hosted metadata URL, or cryptographic trust utilizing SAML assertions that are signed with both private and public keys.
- Federation Protocols: Standards like SAML 2.0 or OAuth 2.0/OIDC spell out the token formats and exchange flows that are part of the authentication process.
Cross-domain trust lets different organizations (such as colleges and partner firms) recognize one another's credentials without any problems, even if they are outside of their firewalls.
Major Benefits of Federated SSO:
- No need to create, sync, or deprovision separate user accounts across domains; everything is done automatically.
- Great for joint ventures, mergers, and acquisitions
- Simple to add identity infrastructures while keeping directories
- Following the rules set by the government
- Strong identity protection across the whole company
Traditional SSO is still limited to one domain, where trust connections between IdP and SP only happen within that domain. In one domain, certificate trust, metadata exchange, and token validation all happen.
Federated SSO takes this a step further by letting users log in to various domains without having to make new accounts each time. Identity federation makes it possible to use the same user identities across several domains so that outside vendors, consumers, and cloud platforms can access services with credentials they already trust.
Difference Between Federated SSO and Traditional SSO
Both federated SSO and traditional SSO centralize authentication, although they are used in various ways and with different designs. Federated SSO expands trust across businesses, while traditional SSO retains users in one trusted domain.
Use this side-by-side comparison of federated SSO vs. SSO to find the model that best fits your security demands and the ecosystem of your partners.
| Feature | Traditional SSO | Federated SSO |
|---|---|---|
| Authentication Domain | A single IdP provides and validates security tokens. | Federated SSO supports multiple autonomous domains and cross-validates the IdP-issued security tokens. |
| User Base | Internal employees are users in traditional SSO. | Federated SSO can support both internal and external users. |
| Trust Setup | Within the corporate network, the trust in SSO relies on directory sync or a unified IdP. | Outside the corporate network, trust in federated SSO relies on exchanged metadata and X.509 certificates with the help of protocols like SAML, OAuth or OIDC. |
| Use Case | Access to company-wide apps like email, intranet, and SaaS apps. | Access to the B2B partner portal, cross-organizational cloud integration. |
Traditional SSO makes things easy and gives you full control if you work in one domain. Federated SSO lets you access any domain without any problems if you work with people from other companies or outside partners.
To maximize security and user convenience, make sure your pick fits with your user base and expansion ambitions. As per your organizational needs for expansion, miniOrange helps you achieve both traditional SSO and federated SSO within your company and beyond.
miniOrange is at the forefront of low-code deployment options for cloud and on-premise SSO and federated identity management.
How should you choose an SSO solution for your business?
There are two questions you need to answer to make your choice:
- Who are the people who utilize your product? Are your employees, partners, and customers going to use your system, and what kind of security do you need?
- What is your ecosystem? Is it single-tenant or multi-domain federation?
Choose the SSO model that fits your plan, and then let miniOrange set it up in hours instead of weeks.
Start using a safe and flexible SSO solution from miniOrange. Set up your free demo and get results right now.
When to Use Federated SSO vs. SSO?
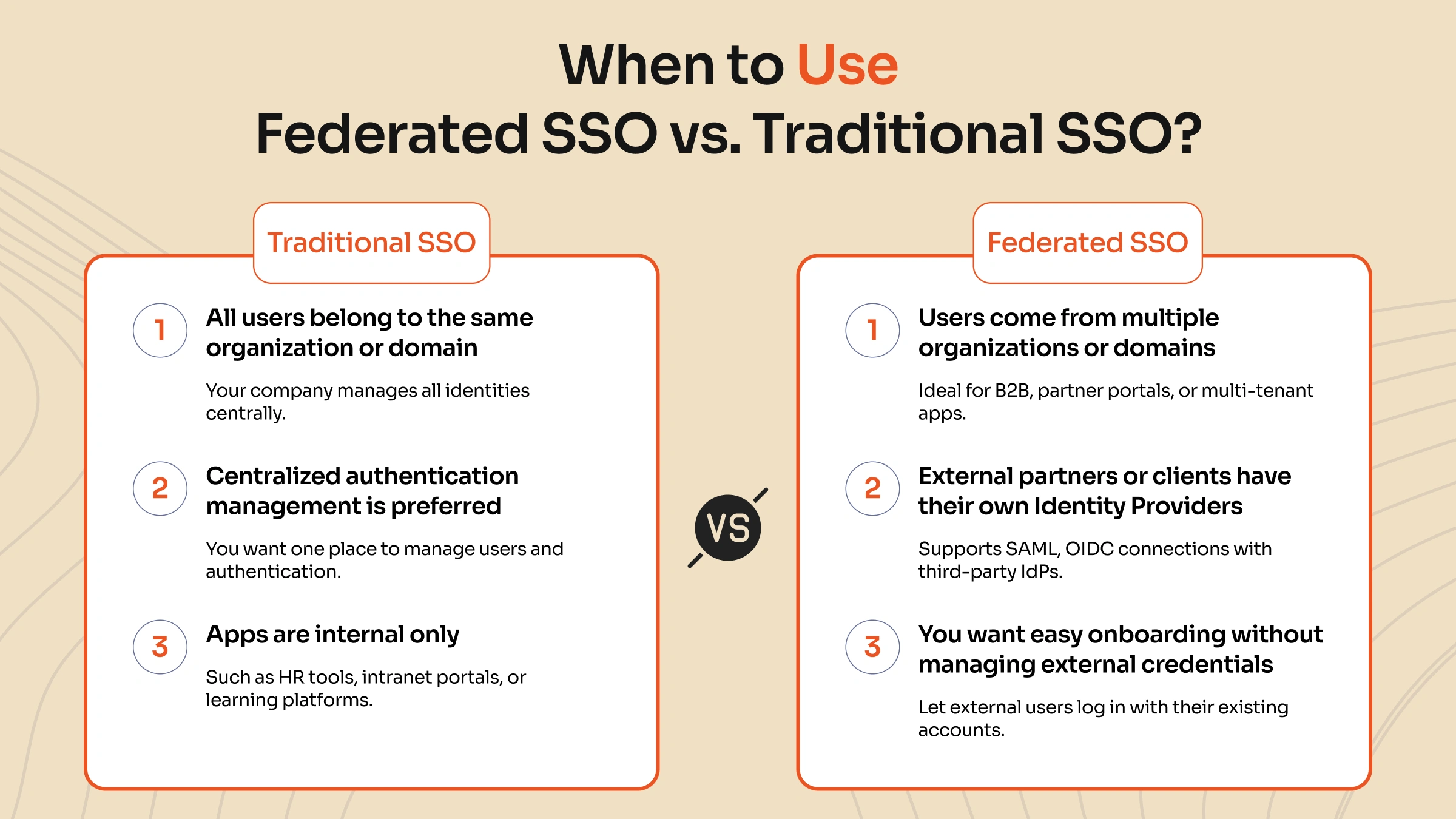
It's not simply a technical choice to choose between federated SSO and traditional SSO; it's also a strategic one. It depends on who your users are, where they come from, and how your systems work together.
When to utilize traditional SSO:
- Everyone who uses it is part of the same organization or domain.
- You want to be able to handle users and authentication from one place.
- Your apps are for internal use only (such as HR portals, intranet tools, and LMS).
When to Use Federated SSO:
- When you need to verify users from more than one organization or domain.
- You work with outside partners, vendors, or consumers who already have their identity providers.
- You want to make it easier for new users to get started and not have to deal with managing credentials for outside users.
Quick Tip:
Federated SSO is the best solution for a growing ecosystem that goes beyond your firewall, such as B2B portals, multi-campus colleges, or SaaS platforms.
Still not sure? Ask yourself, "Do I have control over all user identities, or do I have to rely on others to verify their users?"
Getting Started with Identity Federation with miniOrange
Organizations now require safe, scalable access that works with a wide range of partners, customers, and apps. miniOrange gives you a single experience that makes things safer and easier, whether you are using portals as a user or managing B2B interactions.
How miniOrange Can Help with SSO vs. Federated SSO
- Plug-and-Play Connectors: You can connect to hundreds of apps right now without having to write any code.Also supports WordPress SSO integration, enabling seamless, secure login for your WordPress sites via SAML/OIDC, with easy-to-install miniOrange plugins.
- Protocol Support: Works with SAML, OIDC, and OAuth to fit any identity stack.
- Cross-Domain Federation: Add new partners in minutes instead of weeks, and keep trust between domains.
- Self-Service Onboarding: Give users the power to set up their access, which can cut IT tickets by as much as 50%.
One of the leading finance companies decreased its IT password resets by 70% and cut the time it took to onboard partners from 10 days to 2 days when it migrated its B2B portal to miniOrange Federated SSO. Teams are now able to focus on growth instead of setting up accounts by hand.
When creating your well-rounded security strategy that verifies your users everywhere with the same credentials, look into how multi-factor authentication (MFA) works with various SSO approaches. It could make your security plan even better, which is something worth looking into for more advanced uses.
miniOrange makes it quick and easy to start your identity federation. Try miniOrange SSO free for 30 days or schedule a call with an engineer at miniOrange today.
FAQs
What are the steps to migrate from SSO to federated identity management?
It is easy to migrate from SSO to federated identity management. First, look at how your present SSO is set up, figure out what federation requirements you have, and choose the right federation protocols and identity providers. Integrate and test your apps to ensure their compatibility with federated identity, then gradually transition users while closely monitoring the process to ensure a smooth transition.
How can organizations maintain security and compliance when using FIM?
Use multi-factor authentication, role-based access controls, and full logging to make identity governance stronger. Regular audits and constant monitoring in accordance with industry regulations ensure that security and compliance remain current. Also, using automation and SIEM solutions makes it possible to quickly find and fix new threats.
What are the most common mistakes companies make when choosing between SSO and FIM?
Companies often mix up the ease of use of SSO with the full identity governance of FIM and thus choose a simpler solution when stronger, federated controls are needed. They also don't think about the problems that come with integration, scalability, and changing regulatory requirements, which leads to security and compliance loopholes.
What is the difference between SSO vs federation in identity management?
Single Sign-On (SSO) lets users log in once and access many apps in the same security domain. Federation takes that idea and applies it across organizational or security borders by creating trust between multiple identity providers and service providers. This is usually done with standards like SAML, OAuth, or OpenID Connect.
How does federated identity management vs. SSO compare in securing user access?
Federated identity management lets a trusted outside identity provider handle authentication and authorization via federation protocols. This makes it easy for people from different organizations to access each other's resources. Traditional SSO stores all credentials in one identity store for a domain, making it easier to set up, but it only works with apps in the same trust boundary.
What are the pros and cons of federated login vs. SSO?
1. Federated login
- Pros: access across domains, one credential per user, and security policies that are the same for everyone
- Cons: more complicated to set up, relies on outside identity suppliers, and could cause latency.
2. SSO
- Pros: faster to set up, quick authentication routines, and a single user store
- Cons: can't work with outside partners, and if there are several domains, credentials could get spread around.

Leave a Comment