The digital transformation era has changed the way businesses operate, collaborate, and secure themselves. Organizations are moving faster than ever, but with this speed comes an equally fast-growing attack surface.
Traditional security models that gave broad, static, and long-term access to users are no longer sustainable. Too much access creates opportunity for attackers and increases the chances of insider misuse. Too little access hampers productivity and frustrates teams.
This is where Just Enough Access (JEA) comes into the picture. By giving users only the precise permissions they need for a task, and nothing more, JEA ensures organizations stay secure without slowing down operations.
For executives, developers, and future security professionals, understanding JEA is critical to building a safer, more efficient, and compliant business environment.
Key Takeaways:
- JEA limits user access to only those levels necessary to finish a job.
- Just Enough Access solution helps eliminate rising insider threats, reduce surface attacks, and maintain flexible, agile, and granular user access.
- Crucial use cases of JEA include securing financial transactions, safeguarding patient data, and protecting government systems.
What is Just Enough Access (JEA)?
Just Enough Access is a security principle of Identity and Access Management (IAM) that restricts user privileges to the exact minimum level necessary to complete a defined task or function.
Think of it like a hotel key card. You don’t get a master key that opens every room. Instead, your card opens only your room and perhaps shared areas like the pool or gym.
The same logic applies digitally. Developers fixing a database issue don’t need unrestricted access to HR files. Finance teams reviewing payroll data don’t need administrative access to cloud servers.
By granting access that is tightly controlled, time-bound, and task-specific, organizations reduce the attack surface dramatically.
Importance and Need for JEA
Why is Just Enough Access no longer optional but a necessity? The answer lies in the evolving threat landscape.
- Rise of Insider Threats: Many high-profile breaches come not from external forces but from employees or contractors who had more access than they should.
- Regulatory Pressures: Compliance standards such as GDPR, HIPAA, and PCI DSS demand strict access controls, often requiring demonstration that permissions are limited.
- Operational Agility: Static admin rights slow companies down or create bottlenecks. Cloud-native organizations especially need flexible, granular access and temporary access models.
- Attack Surface Minimization: Every excess credential is a potential entry point for attackers. Removing unnecessary access narrows down these chances.
Crucial Benefits of Just Enough Access
JEA is a preferred solution for organizations due to the following benefits offered:
1. Minimized Insider Threat Risk and Enhanced Security
By ensuring users operate strictly within the limits of what’s required, the risk of data leakage and unauthorized access falls substantially.
JEA closes down the paths for insiders, whether the intent is malicious or purely careless.
2. Improved Operational Efficiency and Productivity
Administrators spend significant time manually granting and revoking broad access. With JEA:
- Permissions can be pre-configured and task-specific.
- Access can be time-bound, meaning revocation happens automatically once tasks are complete.
- Admin workloads are reduced, freeing teams to focus on innovation and monitoring rather than repetitive access tasks.
This shift transforms access control from a cumbersome process into an enabler of productivity.
3. Supports Security Compliance
Auditing becomes straightforward with JEA. Regulators look for proof that sensitive information isn’t widely accessible. Since JEA enforces strict "who has access to what and why," it generates clean audit trails, aligns with compliance mandates, and reduces the chances of fines or penalties.
Additionally, PAM compliance benefits include meeting standards such as PCI DSS and GDPR, and adhering to local regulations.
4. Adheres to the Zero Trust PAM
Zero Trust operates on the principle of “never trust, always verify.” Zero Trust Privileged Access Management (PAM) is an advanced cybersecurity model that enforces continuous verification and strict control over privileged accounts, assuming no user or device is implicitly trusted.
It eliminates standing or permanent privileges by granting Just-in-Time (JIT) access, applies least privilege principles, and continuously monitors privileged sessions in real time. JEA embodies this principle by assuming no user inherently deserves all-access rights.
Implementing JEA: Step-by-Step Process
Implementing Just Enough access involves a series of strategic steps to make sure that minimal privileges are given to the users, along with maintaining operational efficiency.
1. Plan and Assess
Begin by auditing the existing system to identify all privileged accounts, access rights, and roles. Then, determine the crucial systems that need strong controls, such as accounts with sensitive files or data, domain administrators, etc.
2. Determine Access Levels
Based on the audit reports, determine specific access levels and controls required for every user to accomplish their tasks. Utilize Role-Based Access Control (RBAC) to assign users to pre-defined roles (granular access control) to perform their tasks.
3. Set up Access Policies
Once the access levels are determined, set up clear policies to make sure that users can utilize resources based on their designated roles, maintaining granular access controls.
4. Make Use of IAM
Deploy Identity and Access Management (IAM) solutions for user authentication, authorization, and enforcement of access policies.
These tools help maintain compliance and accountability, especially in complex environments.
5. Constant Monitoring
Ongoing review, monitoring, and adjustment of access controls are essential to respond to changes in roles, responsibilities, or organizational structure.
Continuous monitoring ensures access stays aligned with job requirements and security policies.
Industry Use Cases of Just Enough Access (JEA)
JEA can be applied across the following verticals:
1. Securing Patient Data in Healthcare
Hospitals handle vast amounts of sensitive patient data. Nurses may need limited access to treatment history, while billing staff require details about insurance claims.
JEA ensures that only authorized teams view specific categories of data, preventing misuse or accidental leaks.
2. Protecting Financial Transactions and Records
Banks and financial institutions face huge risks if employees or contractors have unnecessary database access.
With JEA, a user can process customer withdrawals without getting into back-end systems meant only for auditors or system admins.
3. Safeguarding Government and Defense Systems
Defense environments are targets for espionage. Allowing a contractor or even a junior-level employee to have broad system access could compromise national security.
JEA ensures every individual has the bare minimum permissions aligned with their clearance level.
4. Controlling Access in Manufacturing Operations
Plant operators may need access to machinery control systems but not to company-wide financial records.
Similarly, engineers fixing an IoT sensor shouldn’t have the right to deploy company software stacks. JEA makes tight segregation possible.
5. Managing Privileges in Technology and IT Services
IT services often require teams working on specific client issues. Instead of permanent admin credentials, JEA ensures they only get privileges during engagement. Once their task is completed, the access withdraws automatically, preventing misuse.
Just-in-Time (JIT) Access vs. Just Enough Access (JEA)
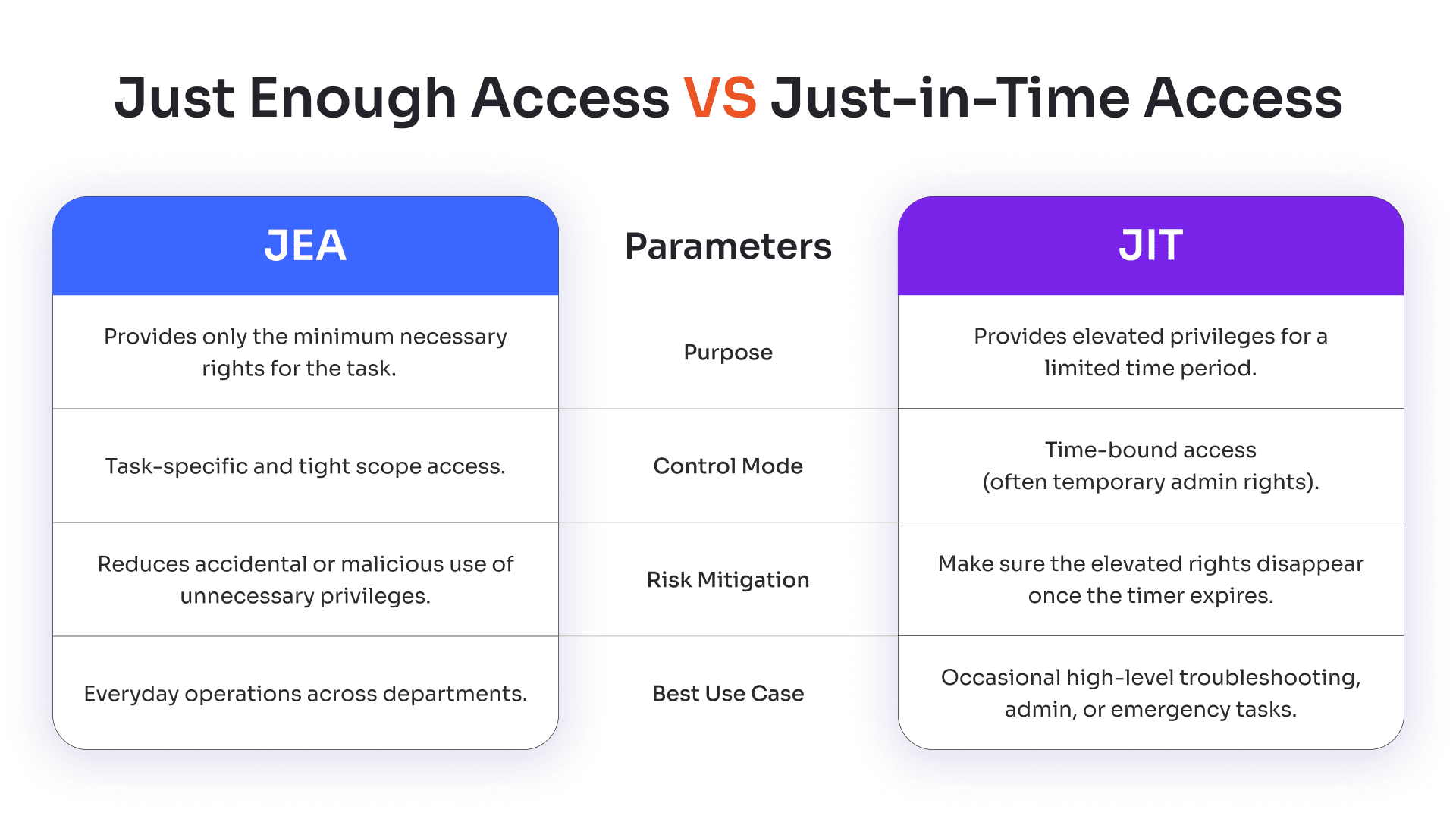
Both JEA and Just-in-time (JIT) solutions tackle the problem of excessive privileges, but they differ. Let’s see a quick JEA vs JIT comparison to see how they handle excessive privileges differently:
| Parameter | Just Enough Access (JEA) | Just-in-Time Access (JIT) |
|---|---|---|
| Purpose | Provides only the minimum necessary rights for the task. | Provides elevated privileges for a limited time period. |
| Control Mode | Task-specific and tight scope access. | Time-bound access (often temporary admin rights). |
| Risk Mitigation | Reduces accidental or malicious use of unnecessary privileges. | Make sure the elevated rights disappear once the timer expires. |
| Best Use Case | Everyday operations across departments. | Occasional high-level troubleshooting, admin, or emergency tasks. |
Many organizations combine JEA and JIT for maximum effect, limiting permissions and ensuring they’re revoked promptly after use.
Enable Just-Enough-Access Offered by miniOrange?
miniOrange offers Just-Enough-Access (JEA) capabilities as part of its Privileged Access Management (PAM) solution. The platform enforces least privilege principles by granting users minimal, task-specific access rights that are precisely tailored to their roles and responsibilities.
Access can be time-bound, automatically revoked after task completion, and conditioned on formal approval workflows, aligning with zero trust principles.
Want to see how JEA can be enforced in your organization? Download the miniOrange PAM Buyer’s Guide:
Final Thoughts
Just Enough Access offers a practical, scalable, and compliance-friendly way to minimize risks without slowing down the workforce.
For executives, it means confidence in security resilience. For developers, it ensures systems aren’t compromised by misused keys. For security teams, it’s the missing link that combines productivity and protection.
JEA is not just about security; it’s about trust, compliance, and enabling business innovation without fear.
FAQs
Can Just Enough Access prevent insider threats?
Yes, by ensuring users only get the minimal required privileges, JEA lowers the risk of both malicious and accidental insider breaches.
How does JEA improve compliance and audits?
JEA generates clean audit logs of who had access to what systems and when. This transparency makes proving compliance with regulations far easier.
Can JEA be combined with multi-factor authentication (MFA)?
Absolutely, while JEA limits access rights, MFA strengthens identity verification. Together, they create a layered defense against both external attackers and insider threats.
What is the difference between Just Enough Access and Privileged Access Management (PAM)?
JEA is a principle focused on granting minimal necessary permissions, while Privileged Access Management (PAM) is a comprehensive solution that enforces JEA by managing, controlling, and auditing privileged accounts and access.





Leave a Comment