Need Help? We are right here!
Search Results:
×A Privileged Access Management (PAM) audit is a structured evaluation of how your organization controls, monitors, and secures privileged accounts with elevated access rights. It ensures that privileged users comply with internal security policies and external regulations.
The audit process involves reviewing access levels, monitoring privileged user activity, and analyzing audit trails to identify unauthorized behavior or policy violations.
A PAM audit tracks privileged user and session activities in real time, logs key events such as user actions, IP addresses, and session timestamps, and helps detect suspicious behavior before it becomes a threat. It also ensures alignment with security standards like SOX, HIPAA, and ISO 27001, reinforcing both compliance and overall organizational security.







Find and list all accounts with special access in your organization. This includes system admins, automated accounts used by applications, and temporary accounts.
Don’t forget to find unused or abandoned accounts (also known as inactive accounts), as they can be risky. Having an entire list is the first step to managing access well.
Look at who has access to which systems and why. Make sure everyone only has the access they really need to do their job.
Watch out for accounts with too many permissions or that can move across different systems. Use role-based rules to control access and note any exceptions.
Make sure privileged accounts have strong login methods like Multi-Factor Authentication (MFA). Look out for weak spots like shared passwords or static, never-changing passwords. Modern methods like passwordless login or risk-based MFA make access safer without annoying users.
Check how passwords for privileged accounts are stored, changed, and protected. Use a secure vault to keep passwords safe and avoid reuse. Make sure passwords are complex and changed regularly to reduce the risk of theft or misuse.
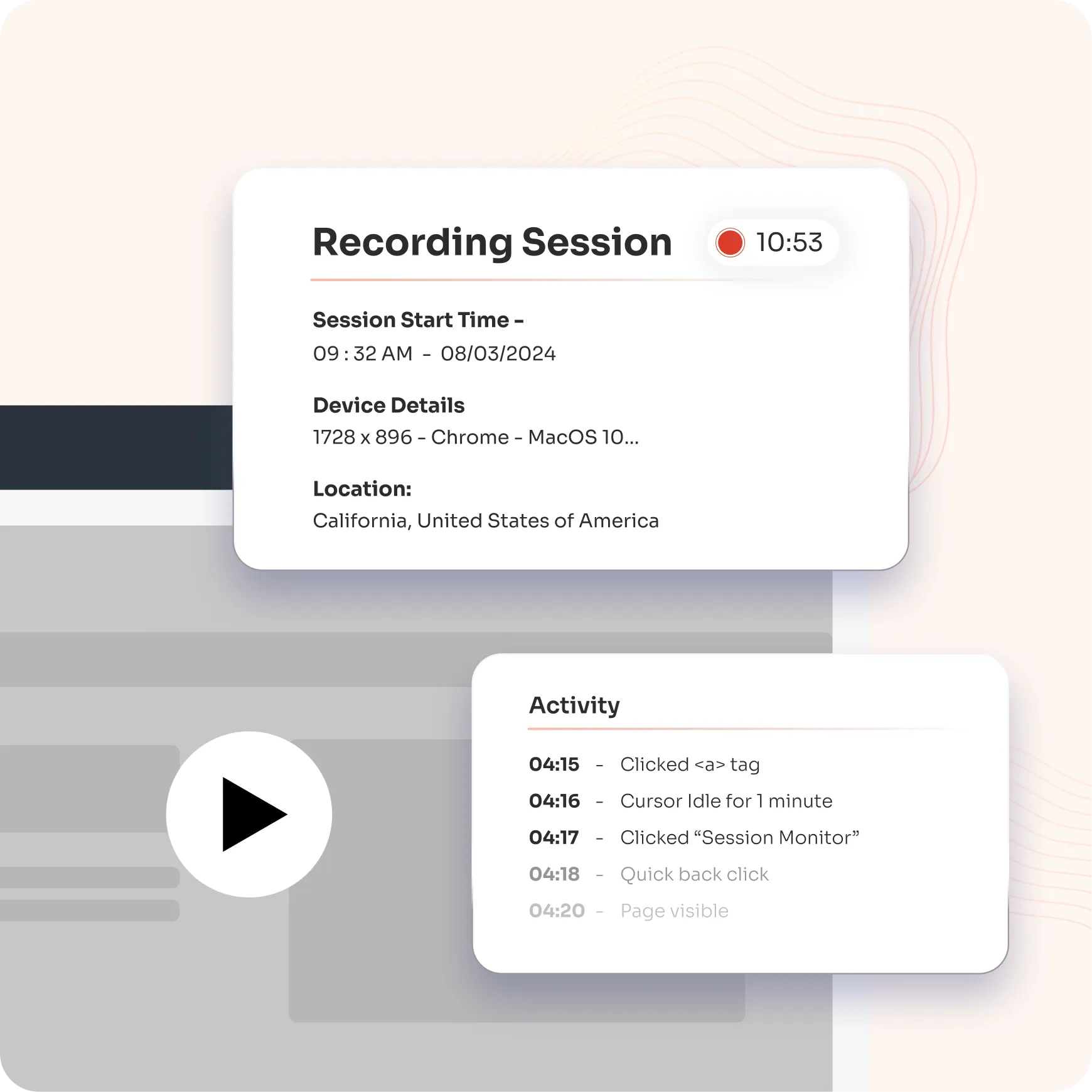
Make sure all activities done by privileged accounts, such as logins, commands run, data accessed, and any changes made, are tracked.
Use tools to record sessions for later review if needed. Set up alerts for suspicious actions and keep logs secure and connected to your main security monitoring system.
Make sure logs and activity from privileged accounts are sent to your Security Information and Event Management (SIEM). This helps automatically find strange behavior, like someone suddenly gaining extra access or working at odd hours. Advanced tools can help prioritize risks for faster action.
Privileged access should only be given through clear approval steps via a ticketing system. Review how access requests are made and approved, and how long access lasts. Look for missing approvals or poor record-keeping. Use Just-in-Time (JIT) access to limit how long someone has special permissions and keep track of all approvals.
Privileged access should never be “set and forget.” Regularly check if users still need their elevated permissions. Make sure managers approve access and remove it when people change jobs or leave. This keeps your system secure and limits unnecessary access.
Audit not just the technology, but also the rules and management of PAM. Check if policies are clear, up-to-date, and follow industry standards.
Determine whether policies are aligned with frameworks such as NIST 800-53, ISO 27001, or CIS Controls. Strong policies help make sure controls are followed and can stand up to audits.
Gain constant visibility into all privileged operations with a real-time dashboard that offers a comprehensive view of administrator activities. This feature ensures enhanced oversight and security, helping administrators monitor and manage privileged access effectively.
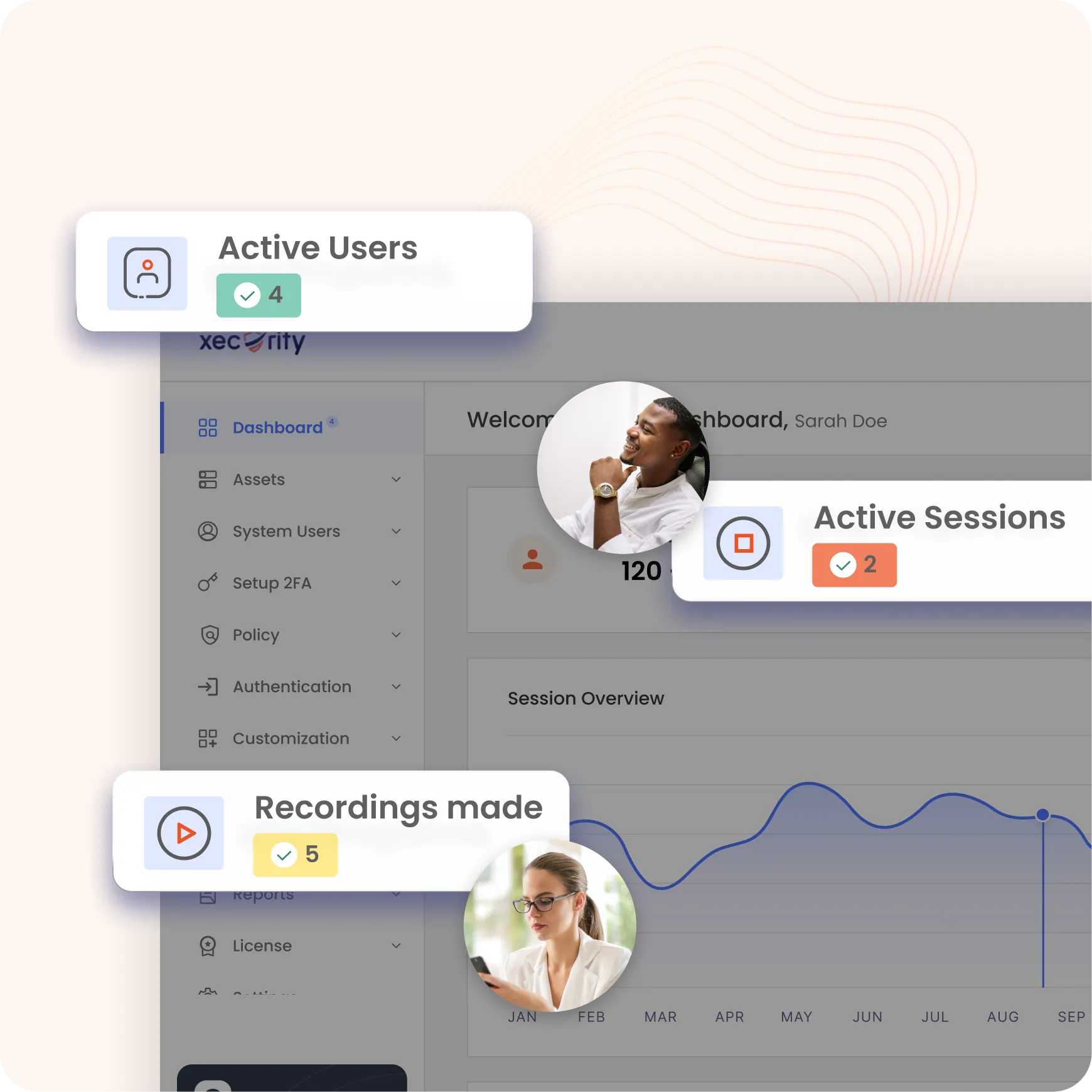
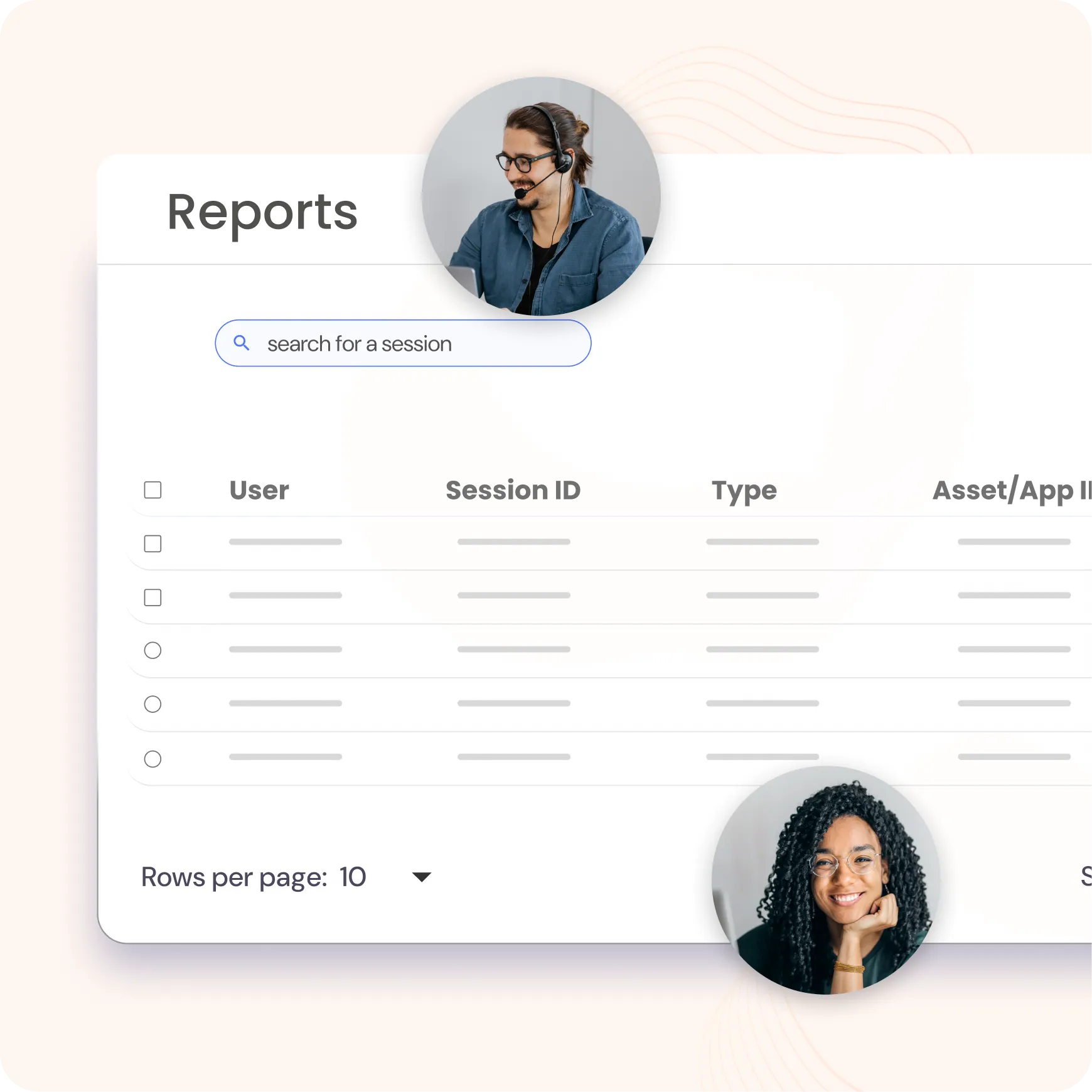
Customize your reporting process with flexible options to generate reports on user-defined schedules, on-demand, or at regular intervals. Access detailed and scheduled reports across key categories, including:
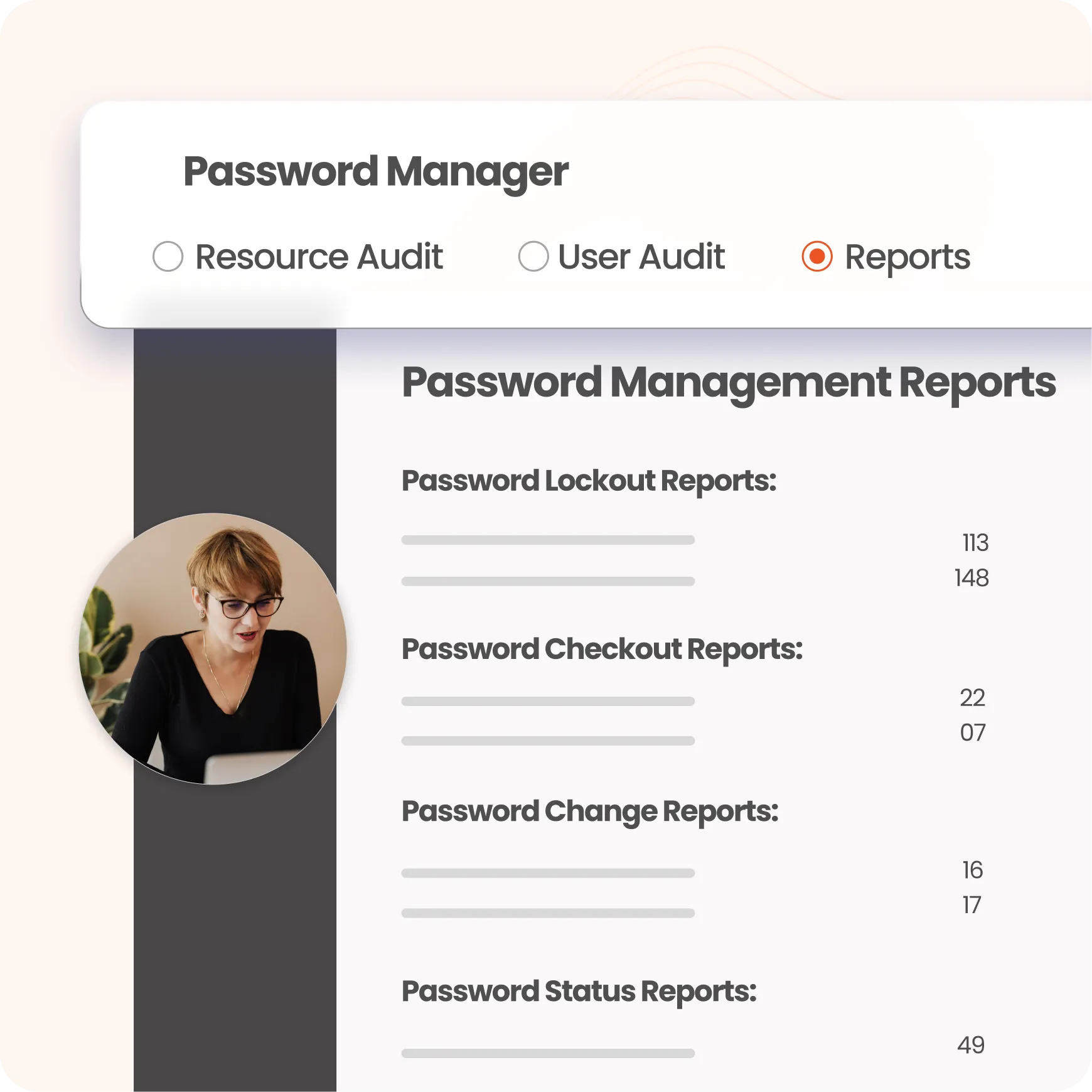
Enhance security with comprehensive password management reports, including:
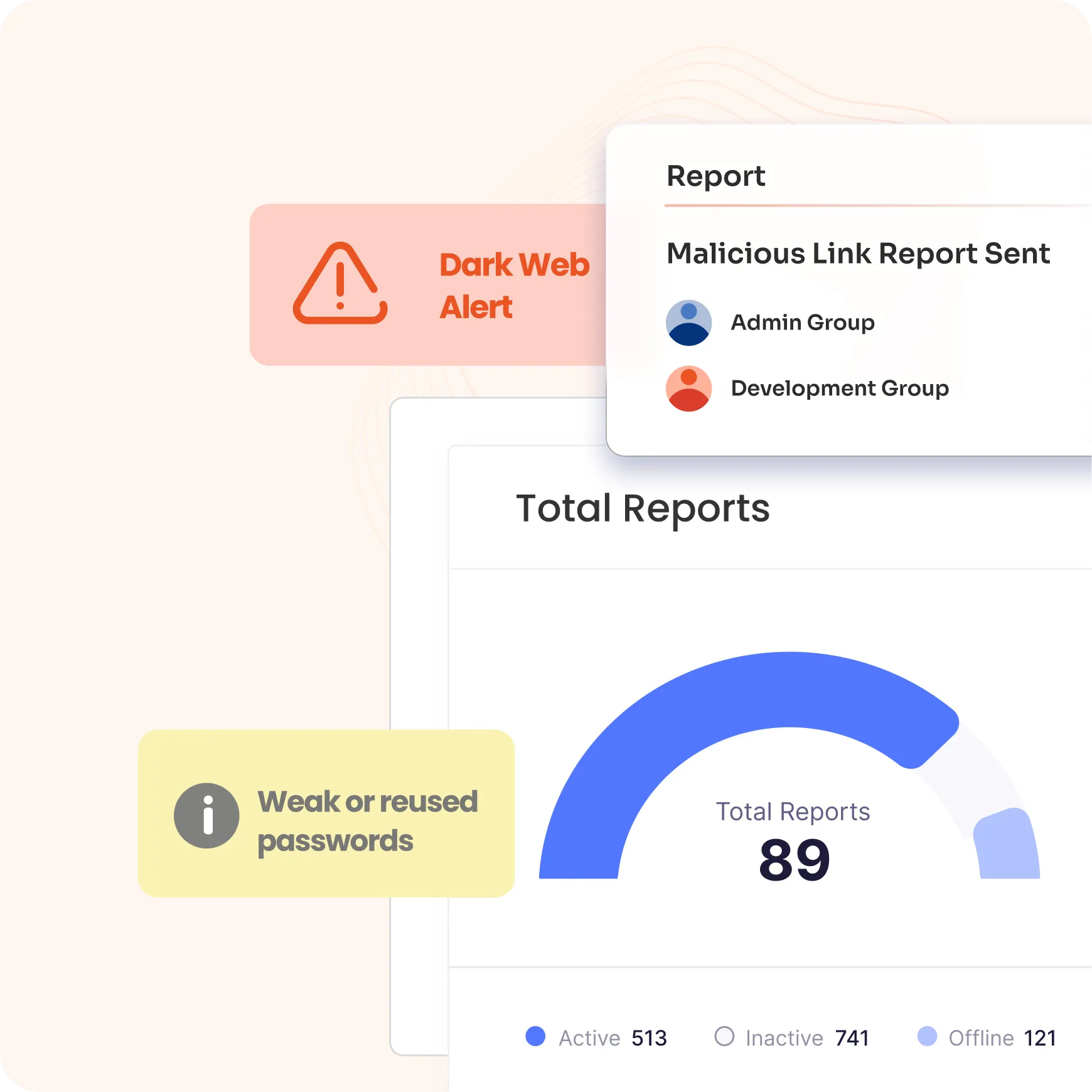
Leverage advanced analytics to monitor session activities and assign a risk score to each session and user task. Integrated with SIEM, this feature helps prioritize auditing efforts by identifying potentially risky behavior in real-time, enabling faster response to threats and enhanced security management.
Enable forensic investigations with session recording and replay capabilities while generating tailored reports. Built-in threat analytics enhance the detection of suspicious activities within privileged sessions, ensuring comprehensive security oversight and response.
Ensure only authorized users access critical assets, reducing data breach risks.
Identify potential vulnerabilities and weak practices to mitigate insider threats.
Align PAM practices with industry regulations to meet compliance requirements and avoid penalties.
