Invisible or hidden risks often corrupt organizations inside out. These are hard to detect and go unnoticed for a prolonged period.
Privilege Creep, one such hidden risk, is a silent security gap, where there is an accumulation of inessential access rights of employees over a period of time. This could pave the way for unauthorized access and breaches.
Key Takeaways
- Privilege creep increases attack surfaces and compliance risks.
- Often caused by poor deprovisioning, role switch, group membership, or unmanaged role changes.
- Regular reviews, PAM solutions, and Role-Based Access Control (RBAC) help detect it early.
- Temporary privilege access, a least privilege approach, and continuous monitoring are essential for preventing privilege creep.
What Is a Privilege Creep?
Privilege is a permission or an authority granted to employees to carry out tasks in an organization. These permissions could be temporary or permanent, based on role, department, or project. If these privileges aren’t protected and managed properly, then they can lead to grave cyberattacks.
One of the hidden risks that often leads to security attacks is privilege creep. It is a situation where employees or users accumulate permissions or access rights beyond what they actually need for their tasks or roles.
For example, an employee works on a temporary project and gains access to tools/systems. These access rights are not removed, resulting in an attack, insider threat, policy violations, or an operational risk.
Furthermore, there are two other related terms, permission creep and entitlement creep, which describe similar phenomena. Permission creep refers to the accumulation of unnecessary file or system access that is never revoked, while entitlement creep occurs when users retain outdated group memberships or entitlements, typically from prior roles or jobs.
The Principle of Least Privilege (PoLP) counters creep by granting users only the minimum access required for their tasks, with regular reviews to revoke excess. Implementing PoLP through identity governance tools prevents accumulation and aligns with standards like the National Institute of Standards and Technology (NIST).
What are the Security Risks and Business Impact of Privilege Creep?
Permission creep brings with it several cybersecurity risks and operational hindrances that organizations need to resolve as soon as possible. The security risks are as follows:
1. Unauthorized Access to Sensitive Data
Employees with access to sensitive data beyond their qualifications or after a project is wrapped up can prove to be dangerous. External threat entities that may have potentially hacked employees’ accounts or are planning to hack can easily gain unauthorized access to these sensitive resources.
2. Insider Threats
Employees, partners, users, or vendors themselves could be the reason for cybercriminal activity, whether intentionally or unintentionally.
Negligent employees can harm an organization by using personal PCs to log in to organizational systems or by clicking on suspicious links, which can lead to breaches and negatively impact the organization’s reputation.
Additionally, corrupt insiders can misuse their privileges to either sell, expose, or use company data for their own benefit.
3. Compliance Failures
Privilege creep directly results in violating the principle of least privilege, which breaks compliance regulations and standards, such as GDPR, HIPAA, or SOX. Organizations that fail to adhere to these standards end up facing legal actions like penalties, charges, or jail time.
4. Data Breaches
According to the 2024 IBM report, 40% of breaches involved data stored across multiple environments, and more than one-third of breaches involved shadow data (data stored in unmanaged data sources), highlighting the growing challenge with tracking and safeguarding data.
One of the reasons for severe data breaches could be privilege creep. It dramatically increases the likelihood and impact of data breaches because it creates a surplus of access that attackers or insiders can exploit.
When a single over-privileged account is compromised, it often becomes a direct path to sensitive data and critical systems.
5. Inefficiencies in System Management
Administrators face the daunting task of overseeing an intricate network of permissions, ensuring access rights remain properly assigned and up to date.
6. Expanded Attack Surface
Attack surfaces are all the entry points where threat entities can steal data or access a system. So, over time, employees collect extra permissions from role changes, temporary projects, or exceptions, and those permissions are rarely removed.
This accumulation means many users end up with far more access than their current duties require, quietly expanding the organization’s attack surface.
How Privilege Creep Happens in Organizations?
Privilege/Permission creep usually arises from unmanaged role changes, leftover temporary access, and inconsistent revocation processes. There are several other reasons behind this happening, which are listed below:
- A Switch in Roles or Departments: When users or employees switch roles and departments, but forget to disown previous access or hold on to the old permissions and privileges. Without a proper review or transfer of permissions, these employees may retain these privileges over a period of time.
- Temporary Permissions: There is a chance that temporary project or task-based permissions may not be revoked after their completion. Over time, these permissions pile up, offering more access to employees/users than necessary.
- Ineffective Deprovisioning Structure: Misalignments between HR and IT teams during the employee lifecycle (onboarding, role changes, offboarding) can often lead to lingering, unused, and dormant accounts. If not properly deactivated, these accounts may be exploited.
- Group Membership: Users may be added to groups with elevated permissions to access certain resources. Without periodic audits, individuals may rack up nested privileges, leading to insider or external threats.
- Lack of Regular Access Reviews: Missing quarterly/annual recertifications can lead to gathering of privileges over time.
- Shadow IT and Unauthorized Apps: Employees may use unauthorized tools or software that need elevated access, inadvertently providing themselves and others with unnecessary permissions.
- Shared Accounts: These types of accounts harness multiple users with varying needs, so monitoring and tracking these permissions can be difficult.
Once you understand the reason behind privilege creep, it can be quite easy to prevent and mitigate it.
How to Detect Privilege Creep Early?
Manually detecting privilege creep requires constant vigilance, detailed tracking, and regular audits.
To detect privilege creep early in organizations, it is essential to conduct manual access reviews for every employee, compare user permissions against defined role baselines, ensure Role-Based Access Controls (RBAC) are enforced, and identify users with unnecessary admin privileges so they can be aligned to the correct access levels.
Regular access audits are essential for maintaining security, but they are time-consuming and not always effective, as human error is always a possibility.
Modern IAM solutions, especially Privileged Access Management (PAM) tools, can significantly improve accuracy by monitoring privileged access rights in real time and highlighting anomalies as they occur.
How PAM Helps Avoid Privilege Creep?
Privileged Access Management (PAM) prevents privilege creep by enforcing strict controls over elevated permissions, ensuring users receive only necessary access without accumulation over time.
1. Regular Audits of Privileged Entitlements
PAM tools are designed to conduct periodic, automated audits of all privileged entitlements and accounts, detecting excessive or outdated permissions across systems, apps, and cloud environments.
These audits generate reports for review, enabling revocation of unnecessary permissions if needed, before they lead to a myriad of risks.
2. Just-in-Time and Time-Bound Privileges
The Just-in-Time (JIT) approach of PAM grants privileges on demand and only when required for particular tasks. It can also automatically revoke privileges after a certain duration, like days or hours, evading permanent retention.
The JIT model follows the Zero Trust principle, decreasing the window for misuse during role or project changes.
3. Continuous Monitoring of Activity
PAM constantly tracks privileged sessions, behaviors, and commands in real-time, flagging unwanted activities such as suspicious login patterns or accumulated data access.
Analytics and session recording help detect and remove privilege creep or entitlement creep situations before they escalate.
4. Secure Credential Vaulting
All privileged credentials are encrypted and stored in a centralized vault that is not accessible to the end users. This eliminates shared accounts and static passwords that give rise to creep.
Automatic checkout systems, rotation, and implementation of Multi-Factor Authentication (MFA) for vault access assure credentials are kept safe.
How to Prevent Privilege Creep in 2026?
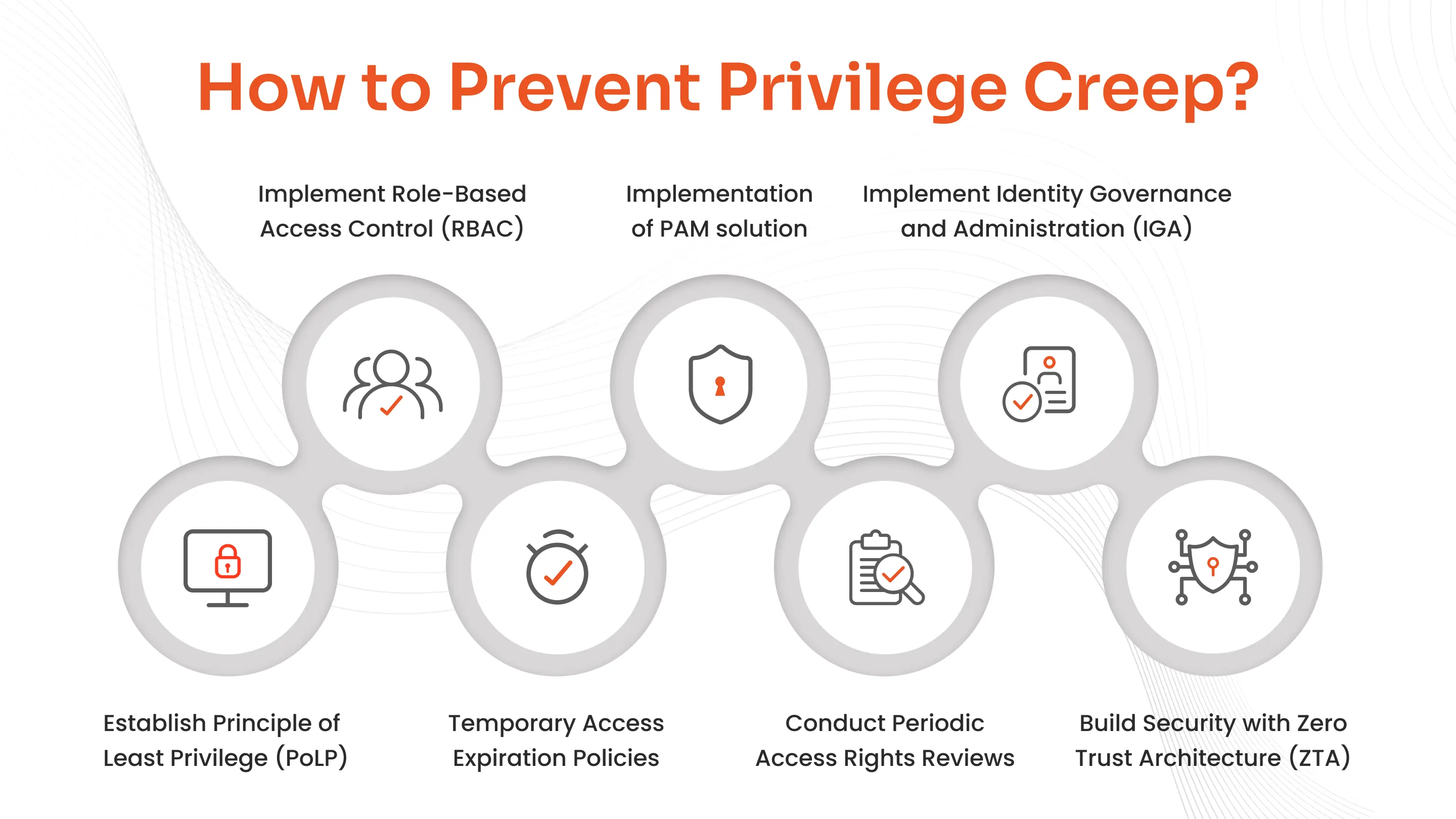
Now that we understand what privilege creep is, how it can harm your organization, and how it can be detected, we’ve put together practical steps to help you mitigate privilege creep in 2026 and beyond.
1. Establish Principle of Least Privilege (PoLP)
Adopt a system where users receive only the minimum access essential for their roles, regularly audited to strip excess. This foundational control blocks accumulation from the start, aligning with zero-trust mandates.
2. Implement Role-Based Access Control (RBAC)
Assign permissions via predefined roles tied to job functions, automating updates during promotions or transfers to avoid manual errors. RBAC minimizes ad-hoc grants that lead to creep, scaling efficiently in hybrid cloud setups.
3. Temporary Access Expiration Policies
Deploy Just-in-Time (JIT) provisioning for short-term needs, auto-revoking access after hours or days. This eliminates lingering project permissions, enforcing zero standing privileges.
4. Use a PAM Solution
The PAM solution from miniOrange is equipped with features such as JIT, credential vaulting, centralized access control, and session monitoring and recording. These help prevent the accumulation of unnecessary rights.
5. Conduct Periodic Access Rights Reviews
Schedule quarterly certifications where managers validate entitlements, using automated tools to flag orphans or over-provisioning. This proactive cleanup catches creeps early.
6. Implement Identity Governance and Administration (IGA)
IGA is a part of Identity and Access Management (IAM) that helps organizations meet compliance, manage access, and streamlines identity lifecycles (Joiners, Movers, Leavers). It prevents privilege creep through least privilege and provisioning/deprovisioning of user accounts.
7. Build Security with Zero Trust Architecture (ZTA)
ZTA verifies every access request regardless of origin, combining micro-segmentation and continuous authentication to render creep irrelevant.
Conclusion
Privilege creep is a threat to an organization because it not only gives rise to anomalies but also hampers operations. However, by actively addressing this issue, companies or businesses can safeguard their data while maintaining access management.
To prevent privilege creep for your organization and level up your security, take advantage of the miniOrange PAM product, which comes with competitive pricing options. We also offer a free 30-day trial period for you to check our core features.
FAQs
1. How do you detect privilege creep?
Run access audits to spot long-tenured excess rights, cross-department anomalies, or dormant accounts using IAM analytics.
2. What are the best practices to prevent privilege creep in 2026?
Implement RBAC, JIT policies, periodic reviews, IGA, PAM, and zero trust architecture for dynamic, minimal access control.
3. What are the risks of privilege creep?
It amplifies data breach potential via over-privileged accounts, enables insider threats, causes compliance violations like GDPR, and expands attack surfaces for lateral movement.
4. How does PAM prevent privilege creep?
PAM tools audit entitlements, enable just-in-time access, monitor activity, and vault credentials securely, automating revocation to halt sprawl.




Leave a Comment