Is Single Sign-On (SSO) really secure? This question must have crossed your mind multiple times before opting for this technology.
According to a report published by the Cybersecurity and Infrastructure Security Agency (CISA), the recent cyber incidents related to SSO services (e.g., the Okta cyber incident; Bradbury [2023], Bracken [2023], Newman [2023]), the digital forensics and incident response experts recommend not locking cybersecurity tools under SSO.
The report further states that if sufficient expertise and dedicated resources are available, a more differentiated and closely monitored approach for cybersecurity tools may be warranted.
Nevertheless, cybersecurity analysts perceive the benefits provided by SSO capabilities to outweigh potential risks, even in the context of the most recent Okta cyber incident, as per the report by CISA.
But there are specific security risks associated with SSO.
We will talk about these risks and how to beat them. Before that, let’s understand the basics of SSO.
What is SSO in the First Place?
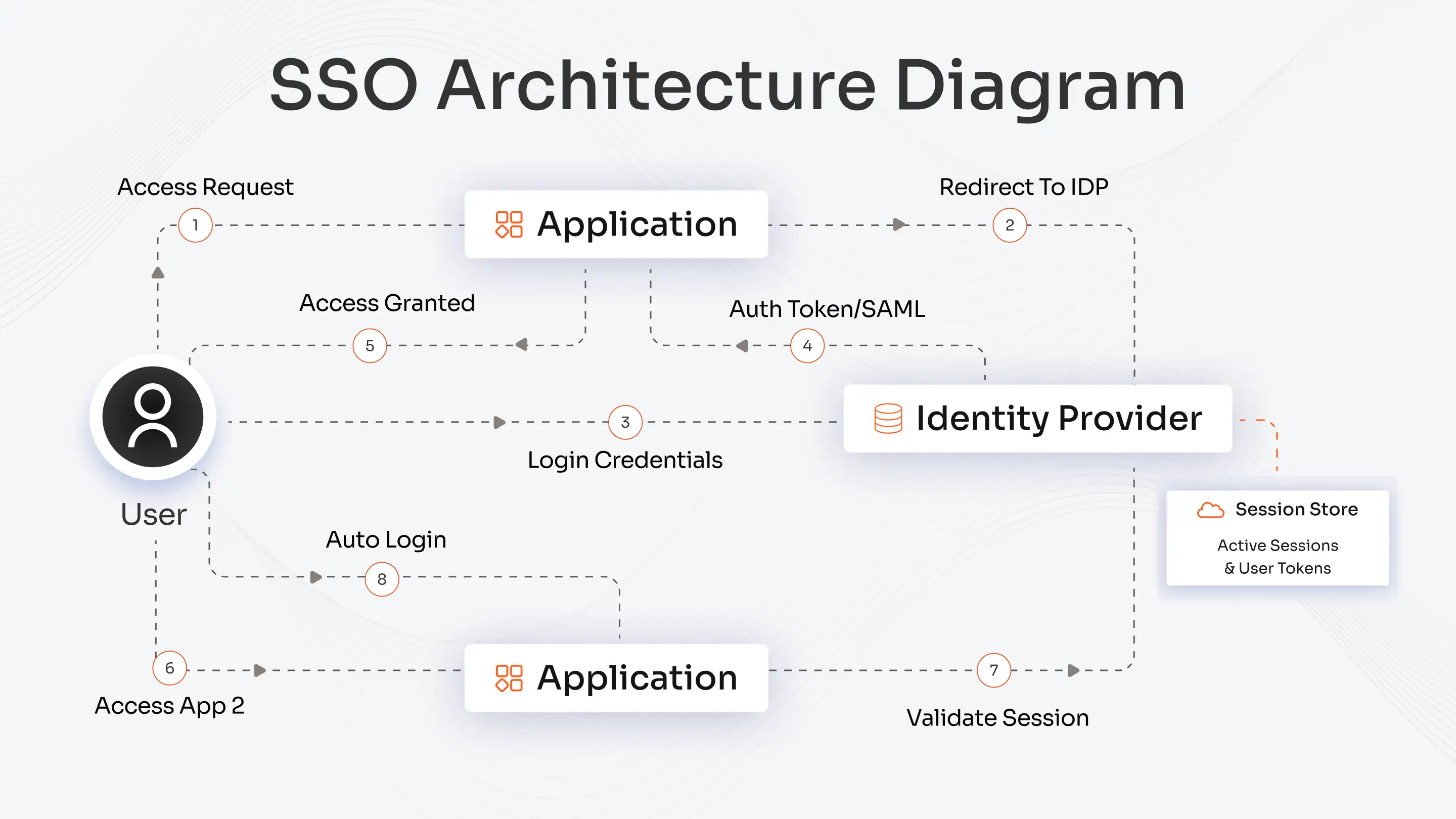
SSO is a cybersecurity technology that lets users log in once and access multiple apps without re-entering their credentials. It’s like having a VIP badge that opens every door in your office building.
If your organization uses varied apps such as Google Workspace, Salesforce, Slack, management tools, and more. These can be unlocked/accessed with the single sign-in function.
However, in certain cases SSO’s security can fluctuate and can result in serious problems for your organization. These could include identity theft, phishing attacks, password leakage, etc.
Is Single Sign-On Secure?
The answer is both ‘Yes’ and ‘No’.
SSO can be a very secure tool if it is implemented correctly and combined with the right security layers.
But what if you skip key precautionary measures, then you might be creating a massive security gap without realizing it.
Let’s explore why.
What are the Top Security Risks of SSO?
SSO is a convenient tool for users; however, it can create security risks for organizations if not implemented the right way and with the help from the right people.
SSO solutions provided by miniOrange, an Identity and Access Management (IAM) company, can help you to incorporate SSO the correct way, thereby amplifying your security levels.
Security Risks of SSO Include:
1. Compromised SSO Credentials = Full Access for Hackers
If a user is authenticated with single sign-on, then their authentication message is passed to every application the user would access. There is no further interaction with the SSO-initiated provider. So, it is possible for a hacker to intrude on the entire system by authenticating themselves.
Just by pretending to be a part of the organization, the hacker can cause catastrophic damage to the user’s account, gaining access to all the apps the user uses.
Solution: Don’t just rely on SSO for security. Rather, amplify your system’s safety by combining SSO with other solutions such as Multi-Factor Authentication (MFA) to avoid credential compromises.
2. SSO Token Hijacking
Session tokens are like backstage passes. Anyone can impersonate you midway through an event if they have a pass. SSO token hijacking is similar to this scenario.
In case it takes too long for a token to expire, then the cybercriminals can steal and use the token for themselves. This maximizes the risk of session hijacking.
Sometimes, revoking longer duration tokens can be difficult, especially if several systems have the authority to use them.
Solution: Try to limit the timeframe of user sessions to prevent token hijacking.
3. Phishing Attacks and Credential Theft
One password to rule them all = one password to phish. Attackers craft convincing methods and trick the users into revealing their credentials via phishing. This leads to unauthorized access to accounts, resulting in scams, frauds, and breaches.
Furthermore, attackers can design fake login pages that mimic legit SSO UX/UI to steal credentials.
Solution: Avoid clicking on links through illegitimate sources such as unknown email addresses, SMSs, WhatsApp messages, and more.
4. Inconsistent Security Policies Across Apps
SSO-integrated apps may have varying levels of security policies, creating substantial inconsistencies in the system, resulting in loopholes and vulnerabilities.
For example, some apps may have 2FA, while others may not. Some may support modern security protocols such as SAML, OAuth 2.0, and Kerberos, and many won’t be compatible with them.
Solution: Make sure that all your systems run on a single security application, backed by a rigid backup and support system.
5. The Offline Lockout Problem
SSO can stop working temporarily due to a myriad of reasons: no internet connection, SSO provider outage, or hardware or software failure. All connected apps and related activities stop working temporarily.
When SSO is down, transactions, security clearances, sensitive data transfers, and the reputation of the organization are at stake. This creates unnecessary downtime, hampering costs and productivity.
Solution: Ensure that your SSO solutions work with optimal uptime and don’t affect businesses.
With the miniOrange SSO solution, you can achieve frictionless SSO for all your apps. We also offer 24/7 support, which will help you to prevent glitches.
6. Shadow IT Sneaks In
Shadow IT refers to apps or systems used by the organization without the knowledge of the IT team.
Since shadow apps aren’t managed by the organization’s IT department, sensitive data accessed via unauthorized apps are outside the protection and monitoring of the IT team. This maximizes vulnerabilities, leading to breaches.
Solution: Avert using apps or systems that may compromise data integrity and security. The IT teams can check whether employees are accessing any apps that are outside the jurisdiction of the company.
7. Weak Adherence to Least Privilege
The Principle of Least Privilege (PoLP) works on the notion that users are granted access to apps, data, and systems that align with their work or intent. To obtain a high level of access, some additional permissions are required.
PoLP operates opposite to SSO; the former gives access to limited apps/resources, and the latter gives access to the entire system through just one set of credentials.
Solution: Access controls must be managed carefully so users cannot see more than they should. This helps in preventing the violation of the principle of least privilege.
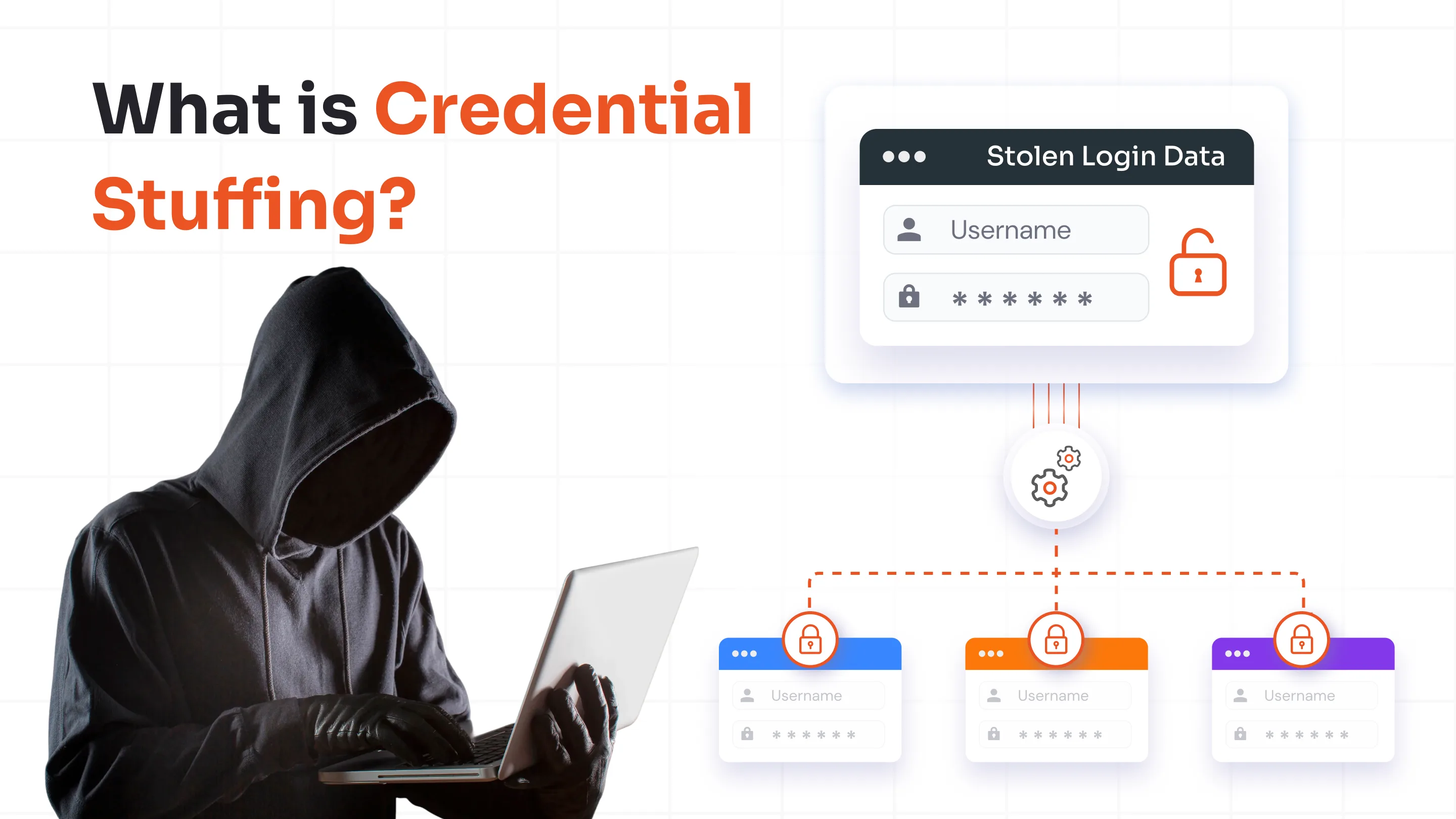
8. Credential Stuffing Becomes a Bigger Threat
If users reuse their SSO credentials on breached websites, hackers can use stolen credentials from those sites to attempt access to the primary SSO login.
Since SSO grants access to multiple apps with a single set of credentials, if attackers succeed in compromising that SSO password via credential stuffing, they gain broad access across several systems.
Solution: Crafting unique passwords and using a combination of MFA and SSO. Also, monitoring login attempts for automated attacks.
9. Improper Redirects
If an app permits illegitimate input in the redirect URL, a hacker can create illegal URLs, resulting in phishing and other malicious attacks.
For example, redirecting to a site that tricks users into making a transaction or giving away confidential data.
Solution: Monitor suspicious looking URLs and avoid clicking on unknown links.
10. Cross-Site Scripting (XSS)
XSS is a critical threat because the hackers inject malicious scripts into the legitimated and trusted web apps that users access after authentication via SSO.
Solution: Apps connected to SSO must have strong content security policies, powerful input sanitization, and safe cookie flags.
Why Do Companies Still Use SSO?
Despite the risks, SSO has major upsides:
- Streamlined Login Experience: SSO lets users access multiple applications with only one set of credentials, decreasing the need for repeated login attempts.
- Fewer Password Resets = Lower IT Load: Because employees have fewer passwords to remember, password fatigue and the temptation to use weak or repeated passwords are lowered.
- More Control and Visibility into Logins: Centralized authentication allows IT admins to manage and monitor user access from a single platform.
The trick? You need to mitigate the risks smartly.
How Can You Make SSO More Secure?
With layered security strategy, and combining access controls at both the application and the identity level, single sign-on can be made more secure.
1. Turn on Multi-Factor Authentication (MFA)
SSO is a single entry point for login, making it a target for the hackers. But when SSO is combined with MFA, an additional defense system is put into place. This secures the system, reducing the risk of password usage and credential theft.
Some of the widely used MFA methods are One-Time Password (OTP), biometric scan, or authenticator app prompt to stop unauthorized access.
2. Use Role-Based and Least-Privileged Access
Single sign-on shouldn’t grant blanket access. With role-based access controls, every user receives only the bare minimum privileges necessary to get their jobs done. The PoLP limits possibilities of damage in case an account is compromised, preventing misuse.
3. Combine SSO with Privileged Access Management (PAM)
PAM adds guardrails around sensitive accounts such as admin logins or finance tools. Even with SSO, PAM can enforce:
- Just-in-time access
- Session monitoring
- Command-level restrictions
This is where true Zero Trust meets productivity.
4. Apply App-Level Security Policies
Make sure that all the applications in your SSO catalog adhere to your organization’s security requirements. You can enforce extra controls wherever possible, such as requiring app-based two-factor authentication (2FA) or limiting access from unknown devices.
5. Monitor for Phishing and Token Hijacking
Use security analytics tools or an Identity Provider (IdP) with anomaly detection to catch signs of abuse such as impossible travel logins or simultaneous access from different regions.
Final Thoughts: Should You Be Using SSO?
Absolutely, but with the right armor.
SSO can boost security and efficiency, but only when it’s paired with smart access policies, 2FA/MFA, and PAM controls.
It’s like upgrading from one lock on your front door to a smart, multi-layered security system that still gets you in quickly, just not recklessly.
Are you still managing 10+ passwords per user? Explore Customer SSO Solutions that combine convenience with airtight security. Your users will love it, and so will your security team.


Leave a Comment