Cyber threats have evolved beyond simple data theft, targeting the very digital lifelines organizations rely on: their supply chain partners and third-party vendors. A supply chain attack is a type of cybersecurity attack where cybercriminals exploit vulnerabilities in an organization’s partners, providers, or dependencies to disrupt operations or access sensitive data.
Supply chain attacks have increased five times, which is around 431% between 2021 and 2023, showcasing a rising vulnerability in the interconnected business environment, according to the Cyber Roundup Report 2024. These attacks are dangerous because they can bypass strong internal defenses, affect thousands of businesses, and escalate rapidly, making “supply chain cyberattacks” a headline concern for companies worldwide.
What is a Supply Chain Attack?
A supply chain attack is an encroachment that exploits weaknesses within a company’s external or internal supply chain. They can be IT services, software providers, hardware, or critical business operations.
In the cybersecurity context, this means attackers don’t always go after companies directly; instead, they manipulate dependencies like service vendors or open-source libraries to invade even the safest organizations.
Apart from companies and dependencies, supply chain attacks are also used against the government, for example, the Stuxnet computer worm that was aimed at Iran’s nuclear facilities.
Multi-Factor Authentication (MFA) software emerges to be one of the leading solutions to tackle supply chain attacks via its authentication methods such as biometrics, push notifications, email/SMS-based OTP, Google/Microsoft Authenticator, and more.
How Supply Chain Attack Works?
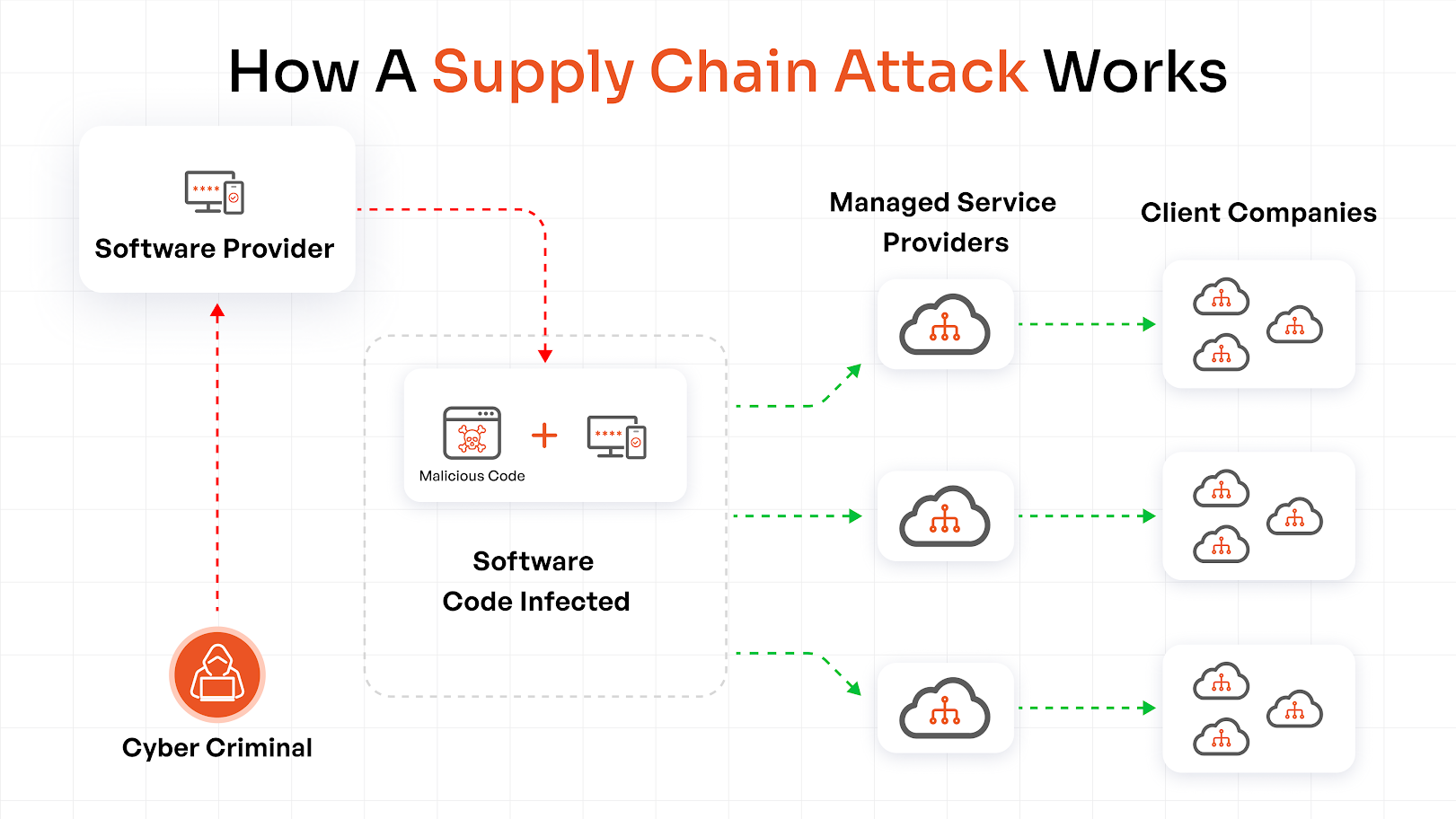
Organizations often leverage third-party vendors for their daily operations, such as human resource management, system maintenance, coding tools, etc.
These vendors have access to sensitive organizational data. So, by attacking the third-party vendors, organizations are crippled from the inside out.
Here’s a breakdown of what goes on during a supply chain attack:
- Spotting a Target: The hackers find out third-party vendors, along with the hardware, software, and services used by them. Usually, vendors with weak security patches are identified.
- Upstream Access: After a vulnerability is identified, the threat entities breach the system through upstream attacks such as credential theft, phishing, targeting developmental tools, etc.
- Malicious Injection: Once inside, attackers inject malicious code or a backdoor into open-source libraries that are used by developers, tamper with the software updates, and hamper the legitimate software/product.
- Downstream Delivery: The compromised software/product is delivered to the target organization via trusted sources. Since the malicious code is hidden within the trusted software, it often bypasses the security.
- Execution and Escalation: The tampered software is installed, and the malware is activated. Cybercriminals use this foothold to move laterally, extract data, gain higher access to the files, and deploy further attacks.
What are the Types of Supply Chain Attacks?

Here are “types of supply chain attacks” explained with real-world relevance:
1. Compromised Software Updates and Attacks
These attacks occur when malicious actors infiltrate the software update mechanism of a trusted vendor and inject harmful code into legitimate updates.
Organizations download and apply what appear to be routine patches, unwittingly allowing attackers into their own networks, potentially impacting thousands of downstream customers at once.
Attackers leverage the trust organizations have in updates from major software suppliers, making this tactic highly efficient and difficult to detect quickly.
2. Dependency Hijacking/Open-Source Dependencies
This attack involves exploiting open-source libraries or components by hijacking or introducing malicious versions into shared repositories. When developers unknowingly integrate these tainted dependencies into their products, attackers gain access to the broader application ecosystem.
Dependency confusion and typosquatting are common ploys, where bad actors publish malicious packages bearing names similar to legitimate ones, tricking automated build systems and developers alike.
3. Browser-Based Attack
In a browser-based attack, hackers exploit vulnerabilities in web browsers or inject malicious scripts (such as through cross-site scripting or compromised extensions) that execute when users visit certain websites.
These attacks can be delivered through supply chain vectors, like third-party scripts, plugins, or ad networks, and often result in theft of credentials or drive-by malware infections.
4. Hardware and Firmware Manipulation
Supply chain attackers may tamper with hardware devices or firmware, potentially during manufacturing or shipping, embedding backdoors or spyware before they ever reach the end user.
Once installed inside a target organization’s environment, this malicious hardware can bypass traditional endpoint security and maintain persistent access, sometimes undetected for years.
5. CI/CD Infrastructure Attacks
Modern software development relies on continuous integration and deployment (CI/CD) pipelines, which become lucrative targets for attackers.
By compromising these automated build, test, and deployment environments, attackers can inject malicious code into code repositories or final software builds, spreading malware to any customers or partners who rely on the compromised systems.
Discover Man-in-the-Middle (MITM) Attack in Cybersecurity
6. JavaScript Attacks
Cybercriminals commonly use JavaScript to inject malicious code into web applications, either directly or through third-party services.
These scripts can skim sensitive data like payment information. By targeting popular plugins or ad networks, attackers can rapidly compromise thousands of sites and their visitors with a single campaign.
7. Third-Party Service Provider Breach
Organizations increasingly outsource critical operations, like payroll, IT support, or HVAC management, to specialized vendors.
Attackers target these providers; breaching a third-party indirectly allows attackers to pivot into the primary organization.
8. Watering Hole Attacks
In watering hole attacks, adversaries compromise websites or online resources frequently visited by specific groups, such as industry forums or development portals.
By infecting these trusted destinations, attackers ensure that when the intended targets visit, they’re silently delivered malware.
9. Complex Dependency Chains
Modern software ecosystems often feature deeply nested, interdependent libraries and modules.
When attackers compromise just a single low-level dependency, the threat can cascade through the entire chain, ultimately infecting every application or system that relies on it.
10. Magecart Attacks
Magecart refers to a group of cybercrime syndicates that specialize in injecting malicious JavaScript code into e-commerce checkout pages via compromised third-party plugins or software supply chain weaknesses.
These scripts skim credit card details directly from web forms, leading to massive financial losses and regulatory scrutiny for affected businesses.
11. Cryptojacking
In cryptojacking attacks, adversaries embed cryptocurrency mining scripts into software artifacts or web applications delivered through the supply chain.
Once activated, these scripts hijack processing power from thousands of compromised systems for illicit crypto mining.
12. Credential Theft and Island Hopping
Attackers frequently aim to steal login credentials, especially from third-party vendors or users with elevated privileges. They then use these keys to “island hop” across interconnected firms, moving laterally through supply chains to expand their reach and impact.
This multi-stage infiltration can make breaches harder to detect, as criminals obscure their tracks and exploit trusted relationships for maximum advantage.
Real-World Cases of Supply Chain Attacks
1. SolarWinds
In 2020, SolarWinds, a network management software company, was hacked, leading to a breach of various private companies and government agencies.
Around 18,000 businesses and customers were affected. The attack was traced back to an illegitimate software update that was added to SolarWinds’ Orion software.
2. Panasonic
In 2021, the Panasonic data breach was revealed, a supply chain cyberattack where data shared by the businesses as part of the supply chain was compromised due to a third party’s malicious access to Panasonic’s servers.
3. MOVEit
In 2023, MOVEit, a tool known for safely transferring confidential files, was a victim of a supply chain cyberattack. Around 620 organizations were gravely affected, these also included major companies such as British Airways and BBC.
This ransomware attack can be traced back to the Cl0p group and is a subtle reminder of the need for patching vulnerabilities quickly to mitigate attacks.
Why are Supply Chain Attacks So Dangerous?
Supply chain attacks have an outsized impact, potentially affecting thousands of businesses simultaneously through trusted vendor relationships.
Because these attacks exploit trust and often leverage privileged access, they’re notoriously hard to detect. As a result, the “supply chain attack in cybersecurity” now represents a top concern globally, especially when the weakest vendor or source can expose everyone.
How to Prevent Supply Chain Attacks?
Here are a few trusted approaches organizations can rely on to strengthen their defenses and minimize the risk of supply chain attacks effectively.
1. Execute Honeytokens
Placing decoy credentials or digital artifacts (“honeytokens”) within your environment helps identify intrusions at an early stage.
When an attacker interacts with these traps, it triggers monitoring systems, providing early warning of malicious activity that could otherwise go unnoticed.
2. Avail Privileged Access Management (PAM) Solutions
PAM product manages and monitors privileged accounts, ensuring that only authorized individuals have access to sensitive resources.
By requiring strong authentication and auditing actions, PAM sharply reduces the risk that compromised credentials can be misused in a supply chain attack.
3. Implement Zero Trust Architecture (ZTA)
A Zero Trust approach means no implicit trust is given to users, devices, or software; every access request is dynamically authenticated and authorized based on identity, context, and risk level.
ZTA limits lateral movement, continuously verifies permissions, and helps contain breaches, even if an attacker enters through a compromised vendor or update.
4. Integrate Malware Prevention Tools
Advanced malware detection and prevention should be integrated into endpoints, networks, and code repositories.
Continually updated anti-malware solutions can block malicious payloads from entering via software updates, third-party integrations, or compromised dependencies.
5. Spot Shadow IT
Regularly scan your environment to detect unauthorized use of third-party tools, cloud apps, or unmanaged software (“Shadow IT”).
Monitoring and controlling these hidden assets reduces the risk of unsanctioned software becoming a backdoor for attackers.
Stay informed through What are DDoS Attacks
6. Conduct Third-Party Risk Assessment
Assess the security practices of all potential and existing vendors. Review their cyber hygiene, evaluate their incident history, and require evidence of controls before granting access to your ecosystem. Ongoing assessment ensures vendors meet evolving security standards.
7. Minimize Access to Sensitive Data
Apply the principle of least privilege so staff, partners, and vendors only get access to the exact data necessary for their roles.
Limiting exposure reduces the blast radius if a credential is compromised or a third-party vendor is breached.
8. Monitor Vendor Network for Vulnerabilities
Actively scan vendors’ systems for known vulnerabilities and require timely remediation. Continuous monitoring increases visibility across your extended digital ecosystem and helps address emerging risks promptly.
9. Detect and Avert Zero-Day Exploits
Implement threat-detection solutions capable of identifying unusual activity indicative of zero-day exploits—attacks that leverage previously unknown vulnerabilities. Proactive anomaly detection and behavioral analytics are essential for stopping these stealthy attacks early.
10. Detect Vulnerabilities and Allow Patching
Establish automated scanning and patch management processes to rapidly identify and fix vulnerabilities in both your own and third-party systems.
Prompt patching is crucial to close security gaps before attackers can exploit them, especially in complex supply chain environments.
Supply Chain Attacks vs. Other Cyberattacks
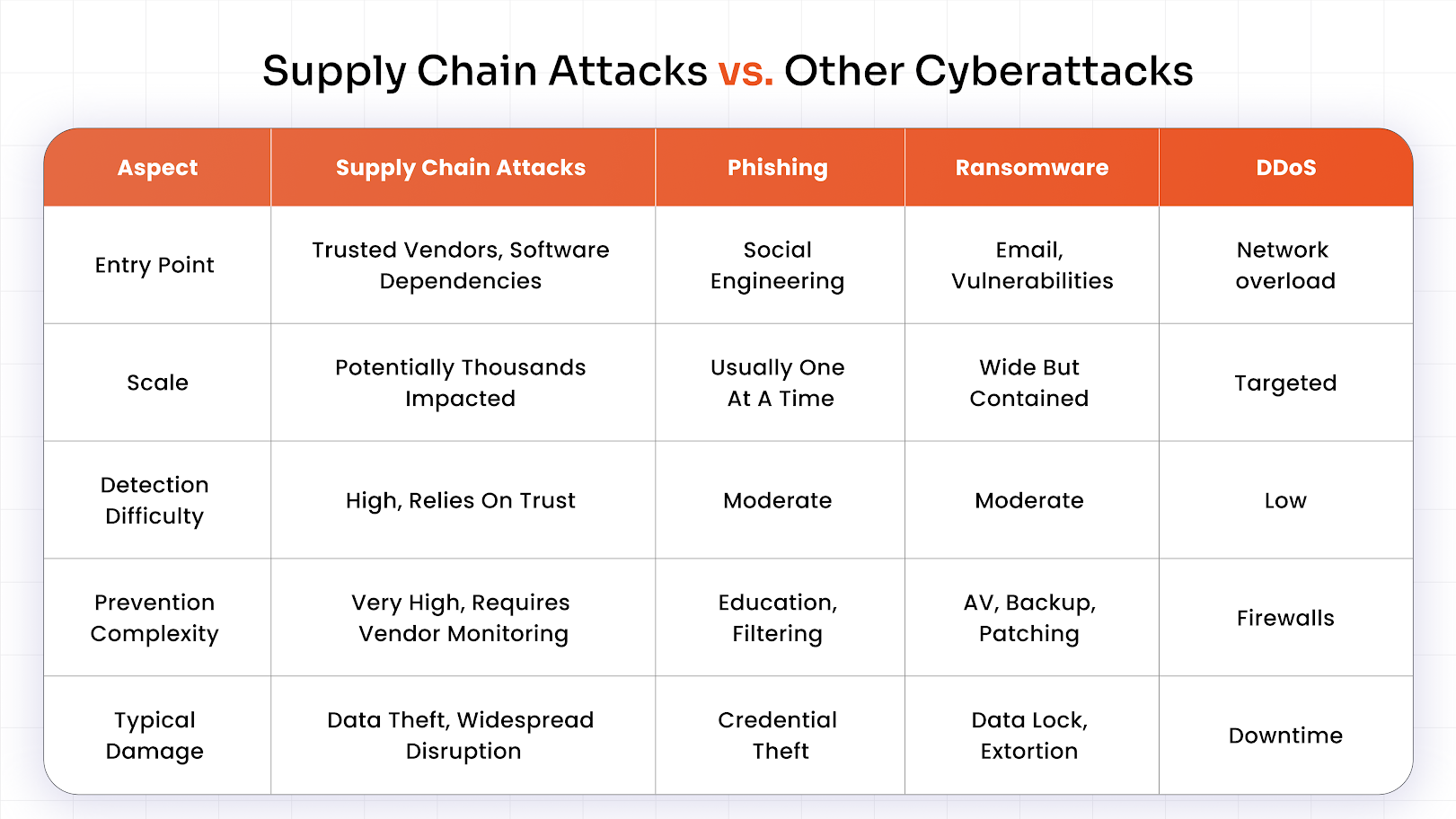
Supply chain attacks are harder to prevent because they exploit deeply trusted connections and dependencies.
Future Outlook: The Growing Risk of Supply Chain Attacks
The explosive growth of remote work and cloud adoption means supply chains—and their digital dependencies are expanding rapidly, enhancing risk.
Open-source supply chain risks are rising as thousands of organizations rely on freely available modules, sometimes abandoned and unvetted.
The future defense will hinge on Zero Trust principles and adaptive MFA solutions, which tighten access even in distributed environments.
See how push notifications simplify authentication
Why Choose miniOrange for Supply Chain Security?
miniOrange delivers comprehensive defense solutions, seamlessly integrating IAM, SSO, MFA, and privileged access management.
With adaptive risk detection, deep vendor management, and industry-leading authentication tools, miniOrange helps organizations strengthen supply chain resilience and preempt attacks before they escalate.
Conclusion
Supply chain attacks represent an existential threat to digital-first business models, but the right mix of proactive defense, authentication solutions, intelligent monitoring, and robust vendor controls can blunt the impact.
Make miniOrange your partner against invisible enemies by exploring a free IAM trial, reviewing competitive pricing, or reaching out for tailored solutions. Schedule a call with us today.
FAQs
What is meant by a supply chain attack?
A supply chain attack targets a company’s vendors, partners, or software dependencies to infiltrate or disrupt business systems.
What is the most common entry point for a supply chain attack?
Compromised software updates, third-party service providers, and open-source dependency hijacking are the most frequent entry points.
How do software supply chain attacks happen?
Attackers poison legitimate workflows, such as trusted updates, code repositories, or package managers, resulting in covert malware delivery.
What are examples of real-world supply chain hacks?
SolarWinds, NotPetya (via MeDoc), the Target breach (via HVAC vendor), and Magecart’s e-commerce exploits illustrate major supply chain hacks.



Leave a Comment