Solutions
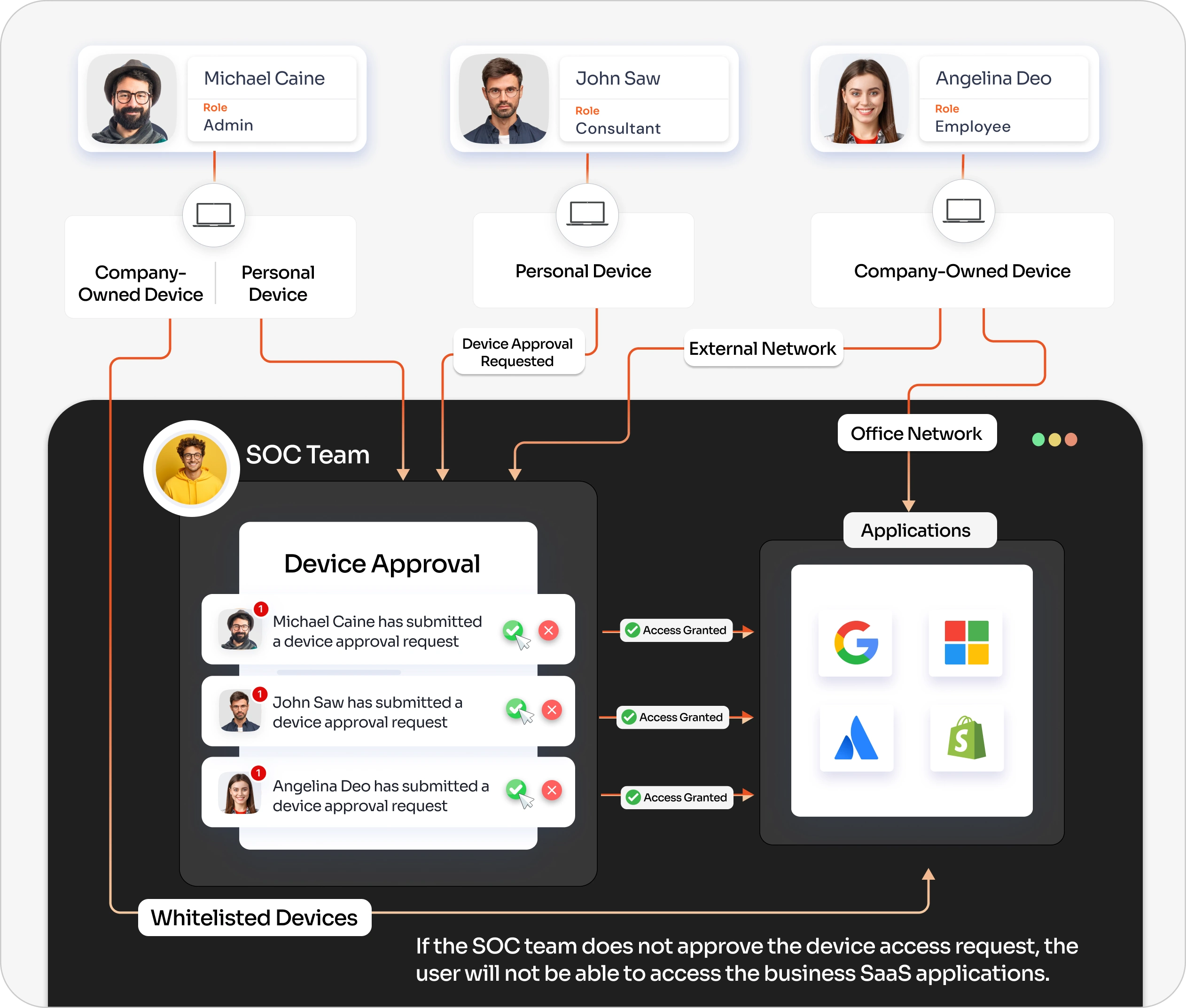
Cloud Access Security Broker (CASB) solution offers a device approval feature for access management. It helps identify, validate, and approve user devices before granting device access to business cloud applications. Here’s how:
CASB in Action
Approver Notification Email
IT admins or SOC team members receive an automatic email notification whenever a user requests access from a new device. Using CASB, they can instantly approve or deny the request based on the user role or device.
Out-of-Network MAC Validation
Configure a list of whitelisted network IPs (such as office networks). If users attempt access from outside these IPs, they are subjected to device approval checks. This prevents unauthorized access from untrusted or public networks.
Whitelisted MAC Address
Register the MAC addresses of trusted company-issued devices to bypass future approvals. Once a device is whitelisted, users can access the applications without undergoing MAC or network validations.