Need Help? We are right here!
Search Results:
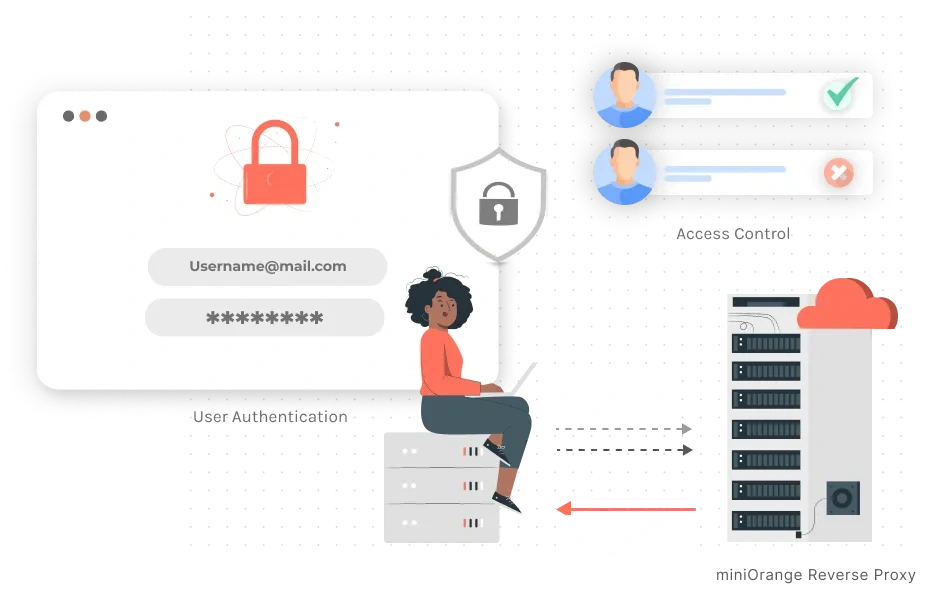
×Access Control is a security measure taken to secure cloud applications. Access control sets restrictions according to the roles assigned to the users. Role-based access control is used to set permissions according to the user roles and permissions assigned. Proxy servers can be used to prevent a group of unauthorized people from accessing particular websites. You can restrict priority access to only authorized users or give non-compliant visitor users partial access. Your resources can only be accessed by users who have logged in using your Identity Providers or Federated Identities.
The most typical scenario for Access Control is when the user is trying to protect PDF files from downloading. With the help of a reverse proxy, any unauthorized user will not even be able to read the contents of your PDF. Here’s how a reverse proxy works in protecting your PDF file contents:
1. User visits the site via the reverse proxy
2. User clicks on a PDF file to either download or views the content
3. Users will be redirected to a Login page where they’ll be prompted to enter their credentials. If the user is already logged in then reverse proxy will display one of the 3 outcomes mentioned below
4. These credentials will be sent back to the reverse proxy and then the website will display one of the 3 outcomes:
a. A custom error message set by the admin on a new page
b. An error 403 “Forbidden Page” will be displayed
c. If the user is authorized, PDF can be read and/or downloaded
Based on user roles, role-based access control (RBAC) can be set on the files, so that the user can just read the PDF or download it as well.

Blocking access to any website or URL which you don’t want your users to access.
Access Control can help to give your users confidence that they will be protected against any vulnerabilities or viruses.
Access Control will protect your website or cloud application from any third party user or vulnerability, preventing your cloud application or website from crashing.
Access Control can help in keeping your system clean and protected against long-term vulnerabilities or viruses.
Users can securely access the system outside the work environment.
Based on the roles users play in an organization, exclusive access to data and information on WordPress is granted and secured by properly monitoring the requests sent to the website’s IdP which are first intercepted by the miniOrange Reverse Proxy.
Based on the roles users play in an organization, exclusive access to the cloud applications will be granted by miniOrange Reverse Proxy using Access Control.
Prevent PDF files from being downloaded online by unauthorized users. Custom role-based access control ( RBAC ) can be set on the files with the help of a reverse proxy so that we can allow selected users to download the files and prevent data leaks.
Protect Videos from being downloaded online by unauthorized users by setting restricted mode. Along with video restriction, we can even set custom role-based access control (RBAC) on our other files with the help of a reverse proxy so that we can allow select users to download the protected files and prevent data leaks.
Protect Images/pictures from unauthorized access. This solution of reverse proxy server can be implemented for varying use cases for images of types and formats. You can modify user roles and access controls for specific data and avoid any leaks into public spaces.
Protect all your mp3 audio files, such as your audio recordings, voice recordings, etc. from being downloaded online by unauthorized users by setting restricted mode. Along with audio file restriction, we can even set custom role-based access control ( RBAC ) on audio files with the help of a reverse proxy server, so that we can allow select users to download the protected files and prevent data leaks.
A reverse proxy server is a special kind of proxy server. In contrast to a forward proxy server, which protects clients [...]
Role based access control (RBAC) means allowing access to users to a stack based on the set user roles and [...]
Ever felt concerned about the images that you added to your online folders, might be downloaded by users (who aren’t logged in) [...]
Google Workspace holds the entire collection of data that a company generates by storing [...]