Having some form of authentication enabled on your on-premise systems, devices, and networks is non-negotiable. Enabling single sign-on on your on-premise systems that lack federation calls for active measures like access gateway integration to experience IAM capabilities. Even lacking an MFA is a huge risk. It is crucial to integrate an access gateway with SSO, MFA, and IAM to gain complete security features through a comprehensive IAM suite.
In this article, we will discuss why unifying SSO, MFA, and IAM is critical for zero-trust, as now fragmented tools are becoming prominent, VPN access with more privileges than needed, and strict compliance. We’ll cover the core concepts, miniOrange Access Gateway’s integration and adaptive MFA, highlight use cases, and reveal the features that make deployment fast, scalable, and secure.
Why Integrate Access Gateway with SSO MFA and IAM?
In 2024, 99.9% of hacked accounts did not have multi-factor authentication turned on. Also, 72% of firms think that having distinct tools creates security blind spots.
Attackers prefer it when companies have to cope with security that isn't consistent across all apps and environments. VPN users who have too many permissions can go anywhere, and old systems are still at risk because of old access controls. At the same time, strict rules like HIPAA and GDPR punish people who get it wrong about who can see what, when, and how.
The Challenges Businesses Face Today
Disconnected security tools across apps and environments
It's impossible for teams to work together when they use different firewalls, VPNs, and identity silos. It's not just one tool dashboard that makes it hard to see risks; multiple tools need to be integrated.
Increased risk from over-permissioned VPN users
Blanket VPN access gives them more rights than they need. The whole network is in danger right away if someone hacks into such a user account.
Need for unified, identity-aware access to internal & legacy systems
Older apps lack traditional authentication connectors. Old logins obscure important information, which makes it easier for hackers to get in.
Regulatory compliance demands (HIPAA, GDPR, etc.)
Laws like HIPAA and GDPR necessitate controls and reporting that know who you are. Real-time access monitoring needs to keep up with how things are done manually.
You can enforce policy at all levels with miniOrange Access Gateway, whether it's on-premises or in the cloud. Single sign-on i.e., SSO, adaptive MFA, and centralized IAM make this possible. This full-stack, zero-trust solution makes sure that users only have to log in once, that their identity is checked in real time, and that they can only get to what they need when they need it.
Access Gateway Integration Components SSO MFA and IAM
Weak or stolen credentials are responsible for 80% of breaches. Layered identity measures stop the risk at the source. Here’s how each component plays a role:
Single Sign-On (SSO)
- SSO lets you log in to all your apps with one secure password.
- Gets rid of the need to reset passwords and get tired of them
- Makes authentication easier by centralizing it
Multi-Factor Authentication (MFA)
- MFA adds another step to verify your identity.
- Confirms the user's identity in more ways than just passwords
- Stops attacks that steal credentials and phishing
Identity and Access Management (IAM)
- IAM tells you who can get to what and when.
- Uses roles, groups, and policies to enforce least-privilege
- Keeps track of every access request for compliance and audit
Locking these three together gives you safety from login to logout without any trust issues.
How Access Gateway Integrates with Single Sign-On (SSO)
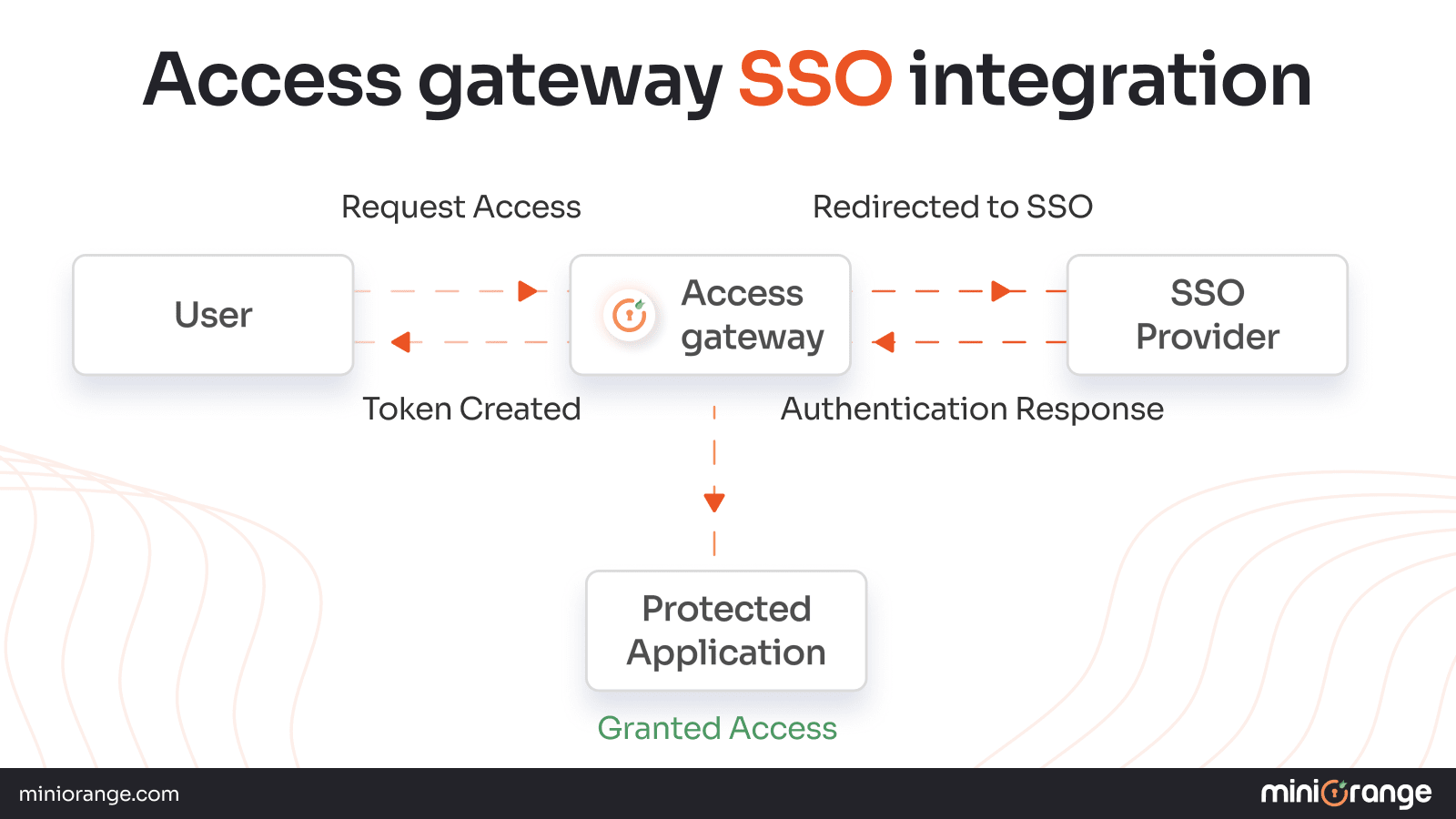
Authentication Flow for SSO using Access Gateway
1. User attempts to access a protected resource
2. Access Gateway checks the authentication status
3. If not authenticated, it redirects the user to the SSO provider
4. SSO provider authenticates user and returns token/assertion
5. Access gateway validates the token and creates a session
6. User is granted access to the protected application
Benefits of miniOrange SSO Integration for Legacy Apps
- The system enables SSO login through Identity Federation, which allows users to access centralized SSO while minimizing password distribution across multiple systems.
- The SSO portal enables central management of users and groups and their associated application permissions for simplified access control.
- The system allows users to create custom login pages for SSO which include social login functionality and password reset capabilities and optional security verification steps.
- The system supports SAML, OAuth, OpenID Connect, JWT and WS-Fed protocols to enable smooth connections between modern and legacy applications.
- The system provides advanced SSO administrative capabilities which allow users to establish roles and groups and implement policies and track login activities through a single administrative dashboard.
- The system includes built-in security features and compliance tools which enforce MFA and IP-based rules and session controls to fulfill compliance needs and enhance access security.
miniOrange stands out because users want to store their credentials everywhere and compromise security but, we help you remember less passwords and do more with the time that you save logging in with our user friendly dashboard while increasing your security manyfolds.
Enabling MFA Through Access Gateway
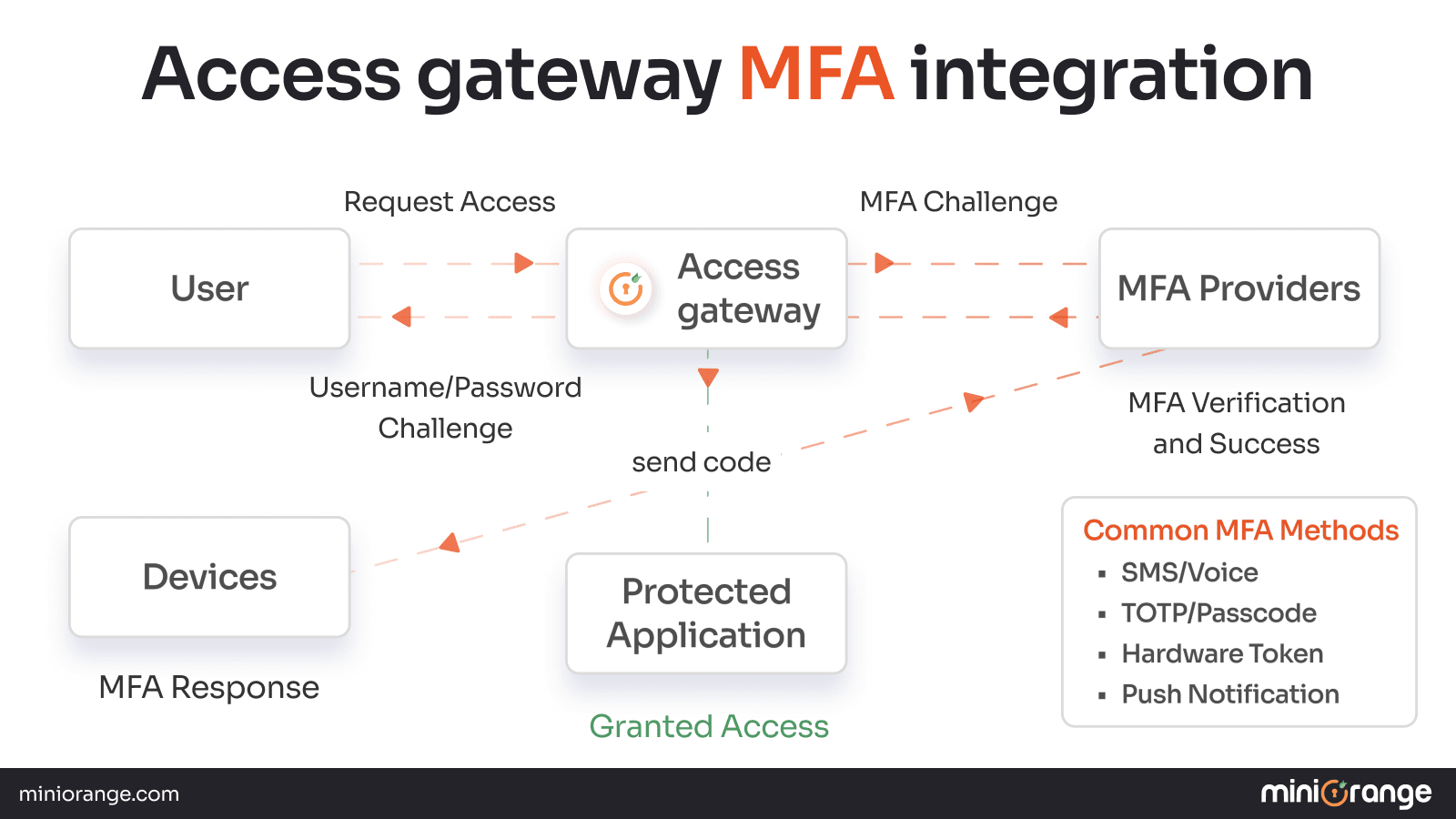
Authentication Flow for MFA with miniOrange Access Gateway
1. User requests access to a protected resource.
2. Access gateway presents a login form (i.e., the first factor)
3. User submits username/password credentials.
4. Gateway initiates MFA challenge with MFA provider.
5. MFA provider sends code/push notification to user device.
6. User providers second factor (code/approval).
7. Gateway verifies MFA response and grants access.
Various MFA methods supported by miniOrange
As per security standards and user convenience, you can implement different MFA methods as per your preference. Here are all the MFA methods miniOrange supports:
OTP and Link
Receive one-time codes via SMS, voice call, or email or tap an approval link sent to your SMS or email for instant authentication.
Authenticator TOTP
Scan a QR code with Google Authenticator, Microsoft Authenticator, or Authy to generate a 6-digit time-based passcode for authentication.
miniOrange Soft Token, Push Notification, and QR
Generate a 6–8 digit time-based token, approve or deny push notifications, or scan a QR code for instant, secure login with miniOrange Authenticator App. Also pattern grid authentication is possible.
YubiKey and Display Hardware Token
Insert a YubiKey (or FIDO token) USB device to generate your MFA credential. Use a standalone display token (e.g., OTP c200) that shows a pre-coded OTP on its screen.
Security Questions
Answer personalized, knowledge-based questions as your second authentication factor.
Depending upon use cases such as remote location without any networks work well with authenticator apps MFA method. Another method implemented in restricted areas where phone, network and Yubikey access is prohibited is pattern grid. For most of the regular use cases, OTP and authenticator apps work well. For protecting critical data, YubiKey is preferred.
Identity Security with miniOrange Access Gateway:
- Adaptive MFA (risk-based): uses risk signals from the environment in real time to pick the best multi-factor checks.
- Step-up authentication: makes verification stronger on its own for sensitive actions or high-risk sessions.
- Configurable per-app and per-user: You can set up different rules for each app and user to log in.
Aligning with IAM for Full Access Governance
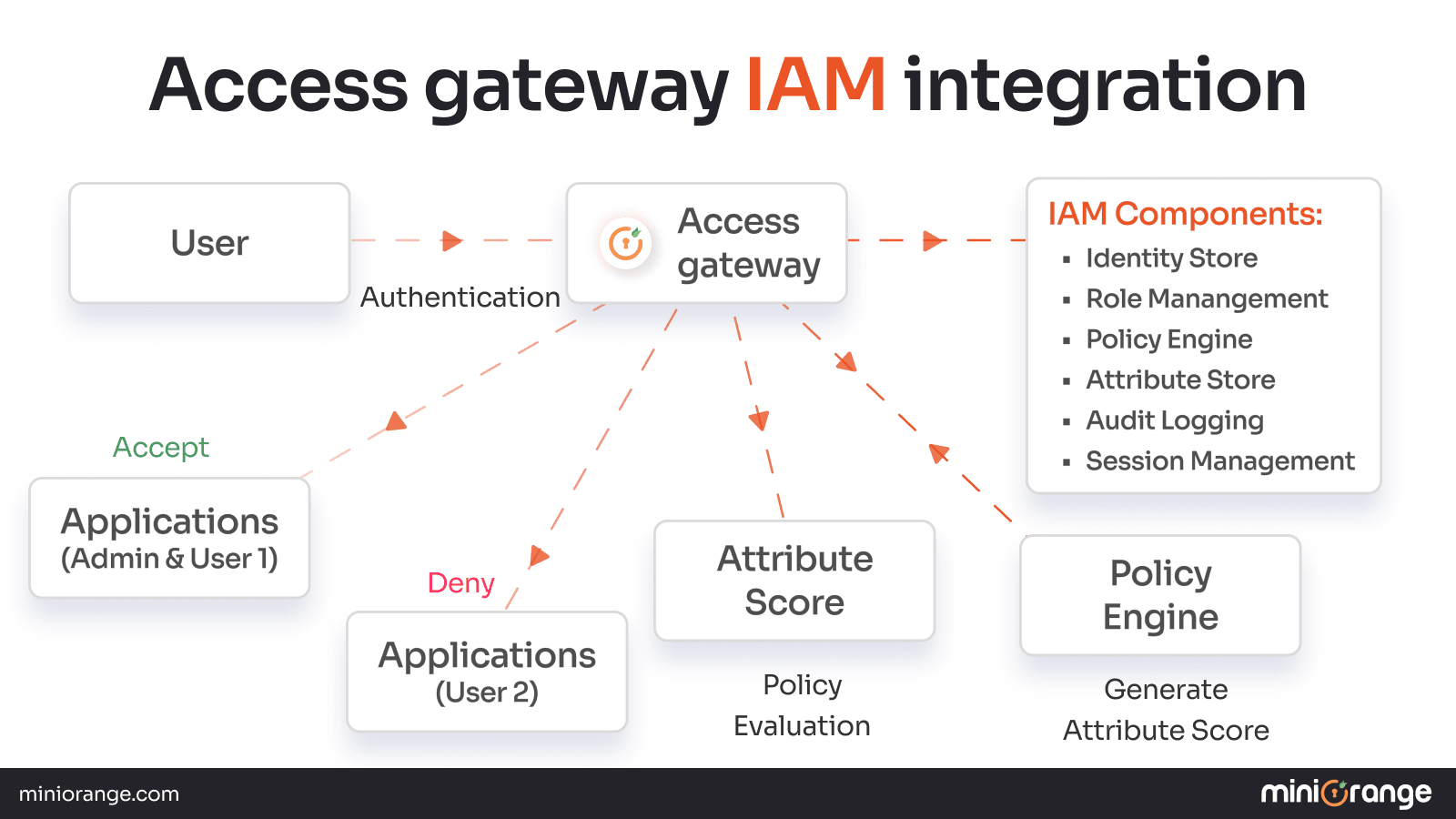
Authentication Flow for IAM with miniOrange Access Gateway
1. User authenticates with Access Gateway (username/password, SSO, etc.)
2. Gateway queries the IAM system to verify user identity.
3. IAM retrieves user roles, groups, and attributes from the directory.
4. The policy engine evaluates access rules based on the user context and resource.
5. IAM returns authorization decision (Allow/Deny) with permissions.
6. Gateway enforces decision: grants access to authorized apps, denies others.
7. All access attempts and decisions are logged for compliance and auditing.
miniOrange IAM capabilities
Identity Proofing
Verify if your users are truly who they claim to be with stringent verification processes. This significantly drops the risk of unauthorized access and unscrupulous activities.
Access Control with Zero Trust
Use advanced access control systems and a zero-trust framework to shield your sensitive data and minimize the attack surface.
Identity Federation and SSO
Allow users to access multiple applications with one identity and a single login using a single sign-on solution, improving productivity and simplifying the login process.
Data Security
Act as a shield, protecting your organization's data from unauthorized access and breaches by encrypting data and enforcing strict access rules in complex environments.
Identity Proofing and MFA
Verify user identity with rigorous checks and multiple forms of verification to reduce unauthorized access with identity proofing. Adaptive MFA adjusts security based on risk factors like location, device, and behavior, ensuring robust protection without hindering user convenience.
Reporting and Auditing
Get a detailed report and audit logs that offer insights into user behaviour, track access patterns, identify threats and vulnerabilities, and sustain compliance.
Regulatory Compliance
Maintain regulatory compliance with the help of stricter identity and access policies and meet data protection norms such as GDPR, HIPAA, or SOX to protect your systems.
Integrated Access Gateway for Securing Your Industry
According to Bloomberg, 48% of companies continue to rely on on-premise ERP systems such as Oracle E-Business Suite rather than moving entirely to the cloud in a hybrid environment.
miniOrange provides easy integration with various technologies for applications that don’t yet support a standard protocol. This means with the miniOrange access gateway, you can protect your legacy applications for businesses of all sizes and industries. Here is how we help you protect your legacy apps:
- Retail and E-commerce: The majority of retail and e-commerce businesses maintain their inventory tracking, price management , and sales monitoring through Oracle EBS systems.
- Supply Chain: The supply chain management system of EBS serves discrete and process manufacturers for production planning and quality control, and barcode integration.
- Finance: The main financial operations of EBS serve the banking and financial services sector for risk management and compliance tasks.
- Healthcare: The healthcare and life sciences sector maintains EBS systems for research activities and procurement , and governmental reporting purposes.
- Utilities: The EBS system enables asset management and project cost tracking , and maintenance planning for the Utilities and Energy (Oil and Gas) sector.
- Government: The government, along with universities, employs EBS to monitor their budgets and handle employee management and grant administration.
- Telecommunications: The EBS system enables worldwide supply chain management and customer billing and service delivery operations for telecommunications and high-tech industries.
How Does miniOrange Stand Out?
miniOrange brings the power of security with SSO, MFA, and IAM in legacy apps with an access gateway in an easy-to-use, intuitive platform without any code changes or hassle.
- Access Gateway, SSO, MFA, and IAM all in one location: Everything you need for easy identity and access management is in one spot.
- Log in for applications that don't use SAML or OIDC based on the header: You may safely add old and custom apps without having to change any code.
- Works on the cloud, on-premises, or in a mix of the two: When you deploy the same way in every environment, users have a smooth experience.
- Quick setup and lots of help: You may be up and running in just a few days with pre-built connectors and step-by-step instructions.
- More than 25,000 companies trust it: Proven to keep identities safe in businesses all around the world.
miniOrange Access Gateway enables you to protect access to on-premises web applications that don’t support federation by extending miniOrange’s authentication and single sign-on capabilities to legacy systems. It’s deployed as a reverse-proxy virtual appliance behind your firewall, integrating with existing apps through HTTP headers, Kerberos tokens, and URL-based authentication. By routing all browser traffic
through the gateway, miniOrange enforces authorization policies, injects necessary headers or tokens, and secures external access without relying on traditional VPNs. Finding the differences between an access gateway and a VPN is important.
miniOrange delivers quick deployment solutions for better security for your business environments, built on cloud, on-premise, and hybrid, no matter where you are located in the world.
How to Build Comprehensive Security Controls with miniOrange?
Security for legacy systems has been a pressing question in identity and access management for a long time. To design complete security controls, miniOrange provides you with ways that help you achieve SSO, MFA, IAM, provisioning, deprovisioning, and PAM with the help of an access gateway.
No matter what your app language or framework is, the miniOrange access gateway accommodates everything. miniOrange access gateway accepts applications running on PHP, Java, JavaScript, Python, Dart, and Kotlin on any environment, like on-premise, cloud, and hybrid.
Here is an action plan with miniOrange:
- Use miniOrange as your only Identity Provider and store all of your user directories in one location.
- Use miniOrange connectors and Access Gateway to enable SSO for both cloud-based and legacy apps that don’t support any standard protocol.
- Use a variety of elements, such as TOTP, push, FIDO2, and SMS, to make MFA risk-based and adaptive.
- Create complex conditional access rules that take into account the person, the app's sensitivity, the network, and the device.
- Automate provisioning, deprovisioning, and RBAC with SCIM, JIT, and password resets that users can do themselves.
- Use MFA and Access Gateway protocol translation to protect legacy and on-premises systems.
- Check logs in real time, integrate to your SIEM, and undertake frequent reviews of who has access.
See how miniOrange Access Gateway can bring more security for your legacy applications. Book a Free Demo to view it in action.




Leave a Comment