SIEM Integration
Use your favorite Security Information and Event Management (SIEM) solution to analyze security events generated from the miniOrange Identity platform. Capture, retain, and deliver security information and events to your SIEM app in near real time.
Use on-premises and cloud-based SIEM tools like Splunk, SumoLogic and FortiSIEM and more. You can control and protect the data feed with:
- Event filtering: You can filter the security events to collect in your SIEM by security configuration and security policy, which helps you focus on real threats.
- Data retention: The Collector stores security event data for 12 hours, enabling you to go back and capture missed events if necessary.
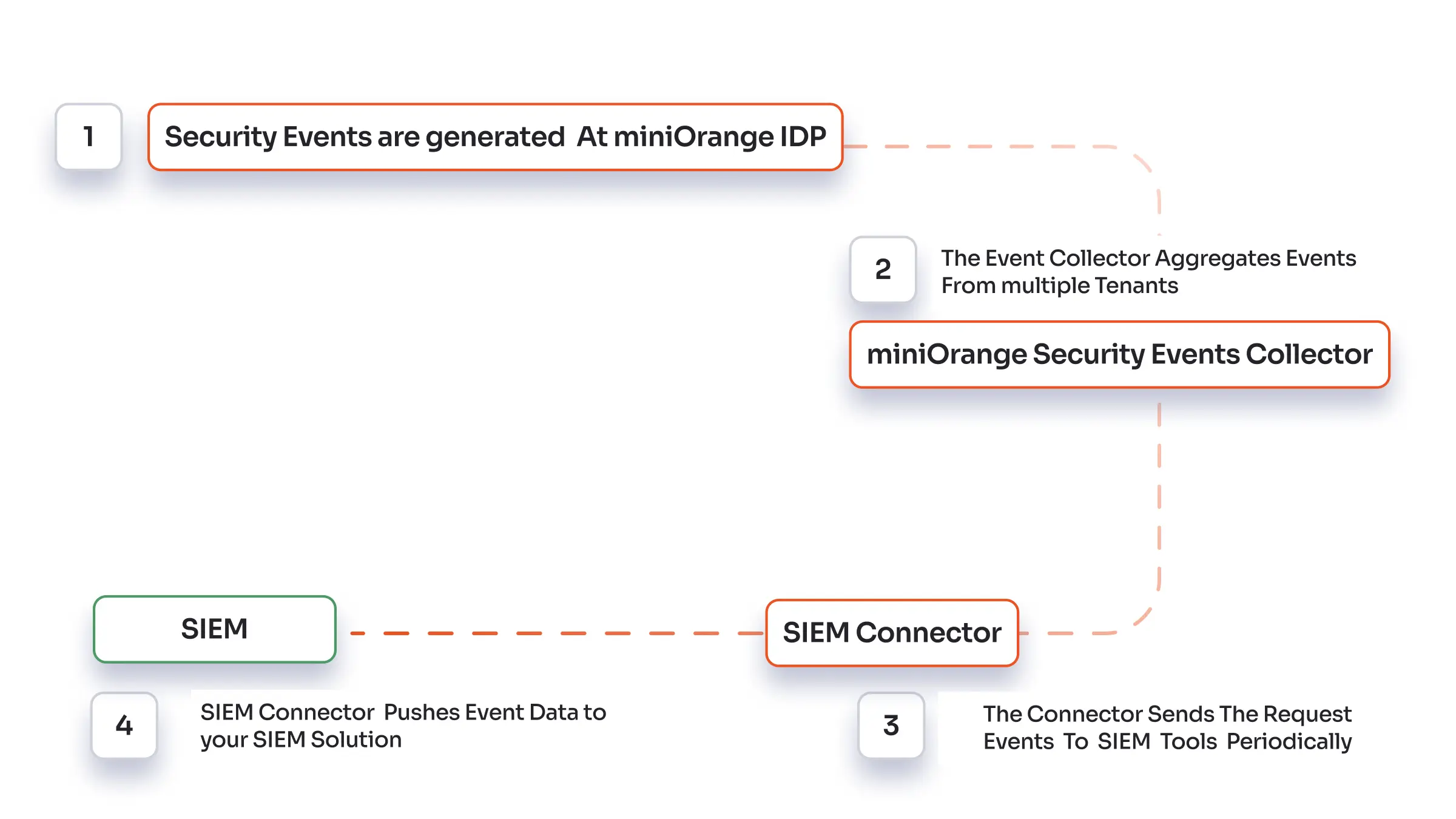
How SIEM Integration works?
SIEM systems are designed to collect log data from diverse sources, including devices and applications. This centralized aggregation of logs enables comprehensive analysis. Different types of SIEM forwarding we support:
- TCP Forwarding: miniOrange can forward the logs on a set of Host and Port using TCP protocol.
To ensure secure transmission of log messages, TLS encryption can be used, especially when forwarding via the Deep Security Manager.
- HTTP Forwarding: miniOrange can send event logs to your SIEM tool's ingestion API.
Which log formats do we support?
We currently support the JSON format.
JSON log event example
{
"audit": {
"logId": "79804b38-3c70-11f0-ab78-06260491ad45",
"customerId": 123456,
"actor": {
"identifier": "a@gmail.com",
"type": "END_USER",
"displayName": "a d",
"customerId": 123456
},
"target": {
"identifier": "a@gmail.com",
"type": "END_USER",
"displayName": "a d",
"customerId":123456
},
"eventType": "Update Users Phone or Email.",
"eventDescription": "User has updated Phone or Email.",
"status": "SUCCESS",
"displayMessage": "User has updated EMAIL.",
"clientIp": "127.127.127.127"
},
"customerId": 123456,
"auditKey": "Update Users Phone or Email.",
"auditValue": "User with username: a@gmail.com has updated EMAIL to: b@gmail.com.",
"xtraAttributes": "{}"
}
Follow the Step-by-Step Guide given below for SIEM Integration in Cloud & On-premise
1. SIEM Integration in Cloud
2. SIEM Integration in On-Premise
Prerequisites
We recommend changing the log level to error-level messages. When log levels are down to a minimum, the server generates large amounts of information in an active production environment. As an alternative, you can set the log level to ERROR and higher so that only important logs are logged. This ensures only important information is sent over to your SIEM tool.
You can even set up a specific log to log only ERROR and higher by modifying the log4j2.xml file. You can find log4j2.xml file here: <path to miniorange directory>\moas\WEB-INF\classes\log4j2.xml.
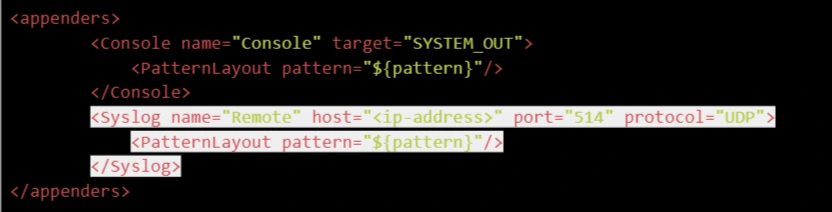
- Add an appender. The easiest way is to copy the one below.
<Syslog name="Remote" host="<ip-address>" port="514" protocol="UDP">
<PatternLayout pattern="${pattern}"/>
</Syslog>
Paste the appender in the appenders section as shown below. Make sure to replace <ip-address> with your SIEM IP Address.
 Add the following to any logger you may be interested in:
Add the following to any logger you may be interested in:
<appender-ref ref="Remote" />
For example:
<asyncLogger name="com.miniorange" level="debug">
<appender-ref ref="Remote" />
</asyncLogger>
Restart the server.
