Proxy servers are foundational to modern networking, acting as digital gatekeepers that manage how data travels between users and servers. Among them, forward proxies and reverse proxies stand out for their distinct roles.
A forward proxy is especially useful for organizations enforcing internet usage policies or individuals seeking anonymity online. On the flip side, a reverse proxy serves the server. It handles incoming traffic, distributes load across multiple backend servers, and adds layers of security and performance optimization.
Understanding the difference between these two is crucial for anyone working with web infrastructure, cybersecurity, or content delivery. Both enhance efficiency, but in opposite directions, i.e., forward proxies push requests out, reverse proxies pull them in. In this blog, we’ll explore how each works, its benefits, and real-world examples along with how miniOrange proxy solutions strengthen security and performance to help you grasp their impact on digital communication.
What are Proxy Servers?
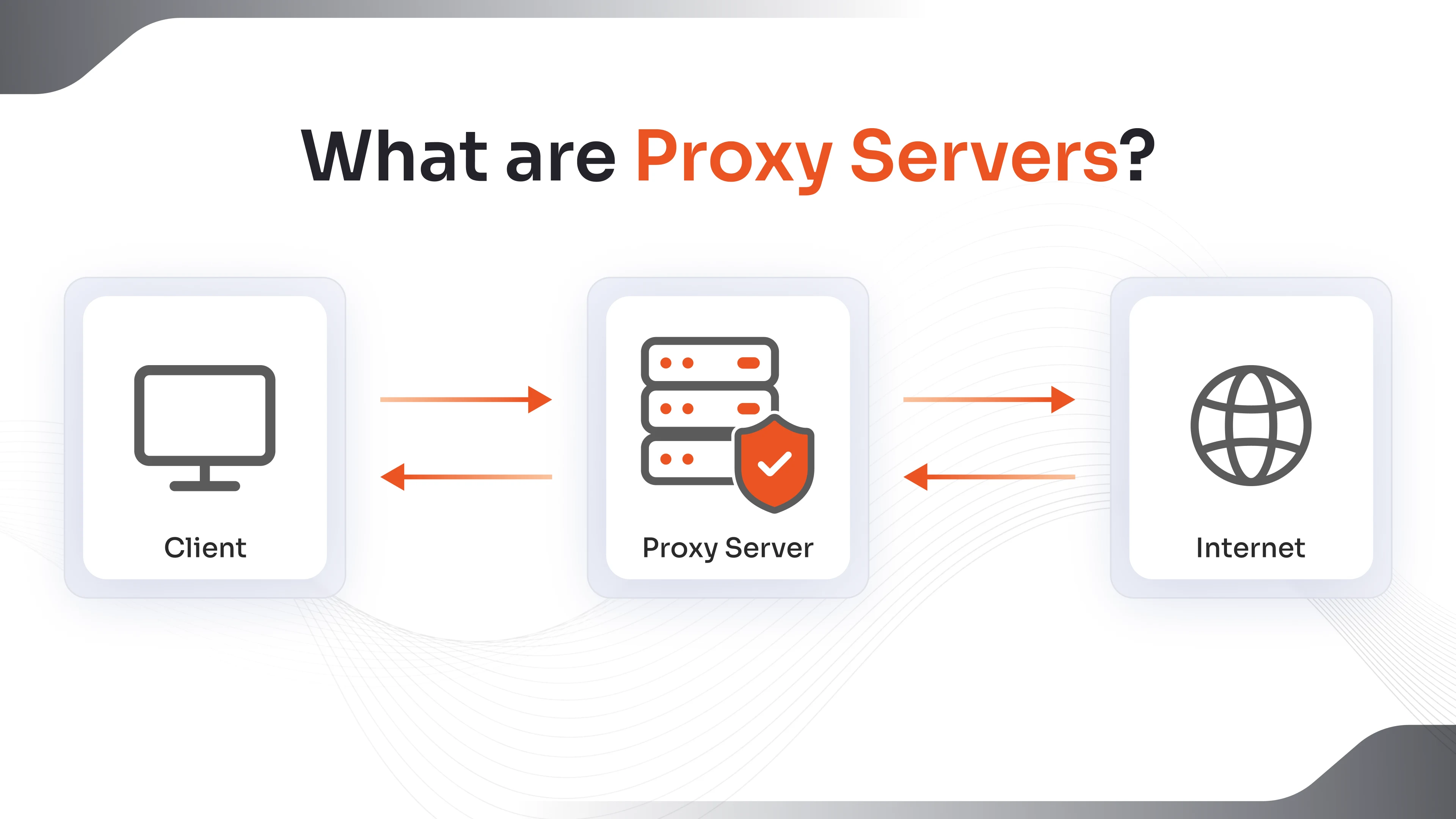
A proxy server acts as an intermediary between a client (such as a user's device) and the destination server (such as a website or application). Instead of connecting directly, the client sends its request to the proxy, which then forwards it to the destination. The response follows the same path back through the proxy.
Proxy servers are used to:
- Enhance privacy by masking IP addresses
- Control and monitor internet usage
- Improve performance through caching
- Strengthen security by filtering traffic
There are two primary types: Forward Proxy and Reverse Proxy. Each of the two serves distinct purposes in network architecture.
What Is a Forward Proxy?
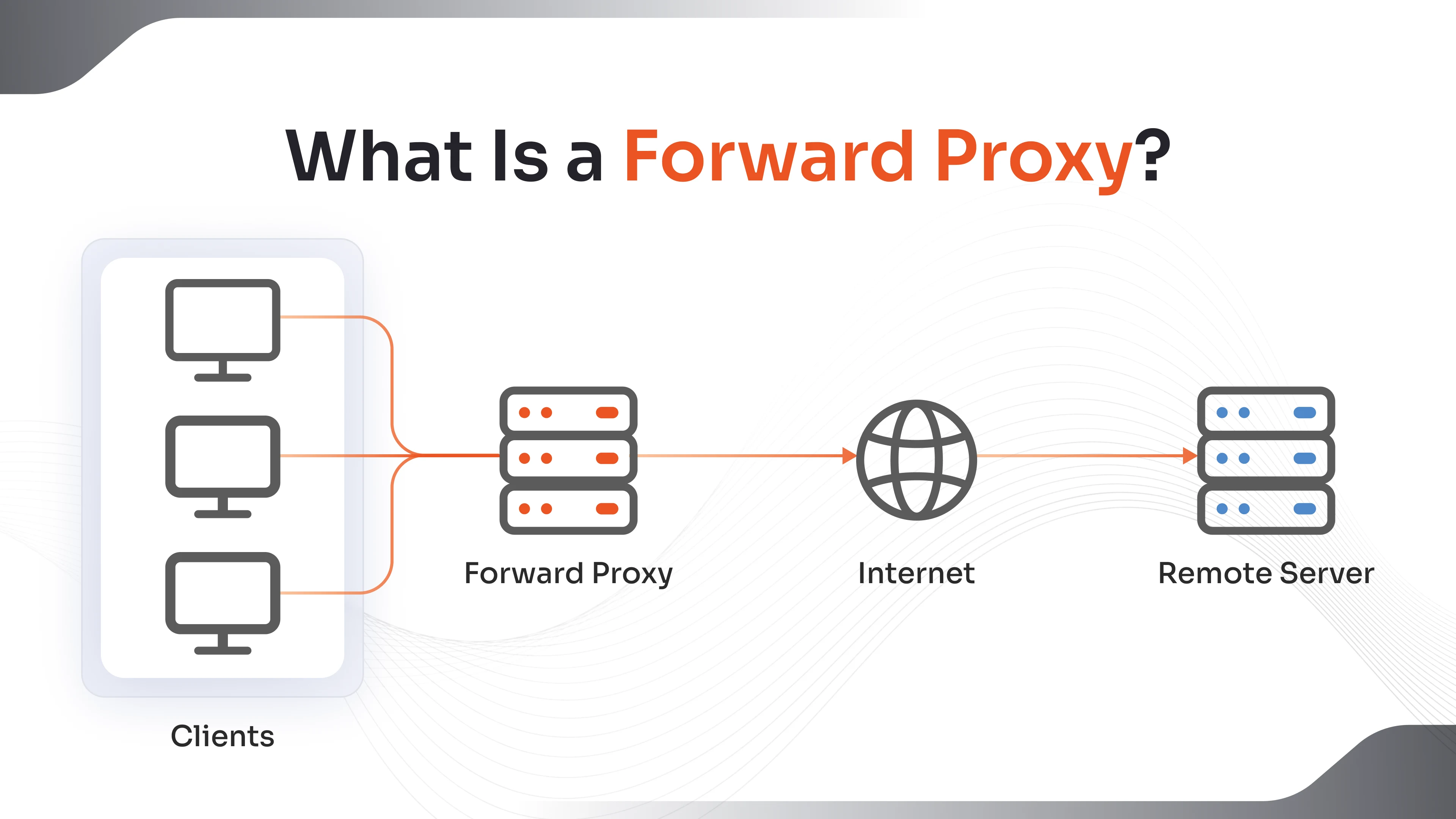
A forward proxy is a server that acts as an intermediary between a client (such as a user's computer or browser) and the internet. It forwards client requests to external servers, masking the client’s identity. The destination server only sees the proxy’s IP address, not the original requester. This setup is commonly used to enforce network policies, enhance privacy, and bypass content restrictions.
Benefits of Forward Proxy
- Client anonymity: Hides the user's IP address to maintain privacy and prevent tracking
- Access control: Allows or blocks emails, specific websites or content based on organizational policies
- Content filtering: Filters out inappropriate or non-productive content in schools, offices, or public networks
- Caching: Stores frequently accessed data to reduce bandwidth usage and improve speed
- Geo-unblocking: Enables access to region-restricted services by masking geographic location
How Does A Forward Proxy Work?
- A user attempts to access a website
- The request is sent to the forward proxy server
- The proxy evaluates the request (e.g., filters, logs, or blocks it)
- If permitted, the proxy forwards the request to the destination server
- The server responds to the proxy
- The proxy relays the response back to the user
Example
A university uses a forward proxy to restrict access to social media sites on campus. When students try to visit Facebook, the proxy intercepts and blocks the request. However, requests to academic resources are allowed and may be cached for faster access.
What Is a Reverse Proxy?
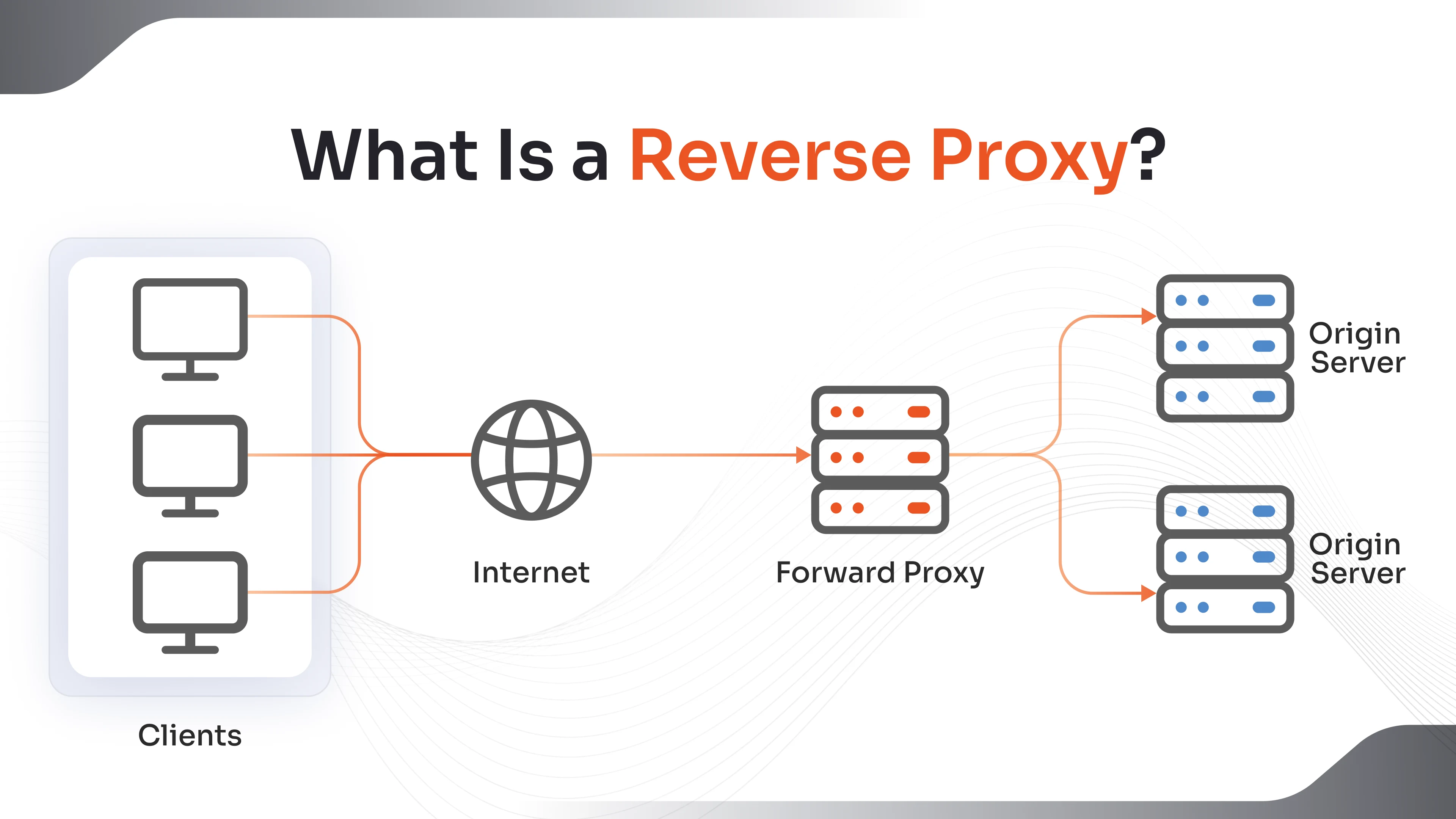
A reverse proxy is a server that sits in front of one or more backend servers and handles incoming requests from clients on behalf of those servers. Unlike a forward proxy, which serves the client, a reverse proxy serves the server. It routes requests to the appropriate backend server, manages traffic, and often performs additional functions like encryption, caching, and security filtering.
Benefits of Reverse Proxy
- Load balancing: Distributes incoming traffic across multiple servers to prevent overload and ensure high availability
- SSL termination: Manages encryption and decryption of HTTPS traffic, reducing the load on backend servers
- Caching: Stores static content to improve response times and reduce server strain
- Security: Hides backend server details and IP addresses, reducing exposure to threats
- DDoS protection: Filters out malicious traffic and mitigates denial-of-service attacks
How Does A Reverse Proxy Work?
- A user sends a request to a public-facing domain
- The request reaches the reverse proxy server
- The proxy selects the appropriate backend server based on load or content type
- The backend server processes the request and sends the response to the proxy
- The proxy forwards the response to the user
Example
An e-commerce platform uses a reverse proxy to manage traffic across multiple web servers. When a customer browses products, the reverse proxy routes the request to the server that is least busy. It may also cache product images and descriptions to serve them faster. If a server fails, the proxy redirects traffic to an alternative server, ensuring uninterrupted service.
Forward Proxy vs Reverse Proxy: Key Differences
| Aspect | Forward Proxy | Reverse Proxy |
|---|---|---|
| Primary Role | Acts on behalf of the client | Acts on behalf of the server |
| Client Visibility | Hides the identity and IP address of the client | Hides the identity and structure of backend servers |
| Traffic Direction | Handles outbound requests from clients to external servers | Handles inbound requests from external clients to internal servers |
| Management and Control | Monitors and controls user access to the internet | Manages and filters incoming traffic to protect backend systems |
| Authentication | Authenticates users before allowing internet access | Authenticates external users before granting access to internal apps |
| Protocol Support | Supports HTTP, HTTPS, FTP, SOCKS, etc. | Primarily HTTP/HTTPS, with WebSocket, gRPC, and TCP in advanced setups |
| Performance Optimization | Caches external content to reduce bandwidth and latency | Offloads SSL, compresses responses, and caches static assets for faster delivery |
| Security Role | Blocks access to malicious sites and scans outbound traffic | Acts as a shield against attacks like DDoS, XSS, and SQL injection |
| Deployment Use Case | Used in corporate networks, schools, and public Wi-Fi setups | Used in cloud platforms, high-traffic websites, and SaaS environments |
Specific Use Cases of Forward Proxy and Reverse Proxy
Forward Proxy Use Cases
Online Anonymity
Forward proxies conceal the user's IP address, helping protect their identity while browsing. They allow access to geo-restricted or censored websites by routing traffic through alternate locations. This is especially useful for individuals in surveillance-heavy or restricted regions.
Access Control and Monitoring
Organizations use forward proxies to filter outbound traffic and enforce browsing policies. They enable detailed tracking of user activity for compliance and internal audits. This setup is common in schools, enterprises, and public networks.
Threat Containment
Forward proxies help prevent compromised devices from reaching malicious domains. They act as a barrier to outbound threats, reducing the risk of data exfiltration. This containment strategy is a key part of layered cybersecurity defenses.
Geo-Testing and Localization
Teams use forward proxies to simulate user access from different countries or regions. This allows validation of localized content, pricing, and user experience. It’s an essential tool for global QA and marketing operations.
Web Scraping and Automation
Forward proxies support large-scale data collection by rotating IP addresses to avoid detection. They are widely used in SEO monitoring, market research, and competitive intelligence. Automation tools rely on them to maintain access without triggering anti-bot defenses.
Reverse Proxy Use Cases
Load Balancing
Reverse proxies distribute incoming traffic across multiple backend servers to prevent overload. This ensures high availability and consistent performance during peak usage. It’s a foundational component of scalable web infrastructure.
Security and Obfuscation
By hiding internal server details, reverse proxies protect backend systems from direct exposure. They filter malicious requests and enforce access policies at the network edge. This adds a critical layer of defense against external threats.
Content Optimization
Reverse proxies cache frequently accessed content to reduce latency and server load. They compress data for faster delivery and handle SSL termination to offload encryption tasks. These optimizations improve user experience and backend efficiency.
Microservices and API Gateway
In distributed architectures, reverse proxies route requests to the correct microservices or APIs. They manage authentication, rate limiting, and logging across services. This centralized control simplifies operations and enhances security.
Flexible Deployment
Reverse proxies enable A/B testing and gradual rollouts by directing traffic to different application versions. They support legacy system integration through URL rewriting and protocol translation. This flexibility allows seamless updates and modernization.
Access Management Done Right with miniOrange
miniOrange offers a comprehensive IAM solution that secures users across cloud, on-premise, and hybrid environments. It provides centralized control over authentication, authorization, and user provisioning, enabling seamless access to thousands of applications while maintaining strict compliance with standards like GDPR, HIPAA, and ISO 270012.
At the heart of miniOrange’s IAM platform is adaptive multi-factor authentication (MFA). Adaptive MFA evaluates contextual signals such as IP address, device type, location, and time of access. This is to dynamically adjust authentication requirements. For example, a login attempt from a trusted device within a corporate network may require only a password, while an attempt from an unknown location might trigger biometric verification or a one-time passcode.
Together, IAM, multi-factor authentication, and proxy technologies form a layered defense strategy, ensuring that only the right users access the right resources under the right conditions. miniOrange doesn’t just manage access, it intelligently adapts to risk, scales with your infrastructure, and simplifies compliance across the board.
Conclusion
Understanding the distinction between forward and reverse proxies isn’t just about knowing where they sit in the network. It’s about recognizing how they shape control, visibility, and security in digital ecosystems. To effortlessly evaluate which proxy is most suitable for your network, get a free trial or schedule a demo to understand more about the proxies.
In a world where data flows constantly between users and services, proxies are no longer optional; they’re strategic. Whether you're building a resilient enterprise architecture, securing cloud-native apps, or simply trying to balance user experience with compliance, the right proxy setup can be the difference between reactive defense and proactive control.
FAQs
Is a proxy the same as a firewall or VPN?
No, a proxy is not the same as a firewall or VPN. A proxy acts as an intermediary server between users and the internet, mainly for masking IP addresses and controlling access. A firewall monitors, filters, and blocks network traffic based on security rules. A VPN creates an encrypted tunnel for data, ensuring privacy and security over public networks.
What is the difference between a proxy and a forward proxy?
A forward proxy sits between internal users and the public internet, forwarding requests from users to external servers and masking their IP addresses. In contrast, a regular proxy term may refer to forward or reverse proxies, but a forward proxy specifically serves outbound connections for internal clients.
Can forward and reverse proxies be used together?
Yes, organizations can use forward and reverse proxies together. Forward proxies are used for controlling outbound requests and protecting user privacy, while reverse proxies manage inbound requests to web servers, enhance performance, and protect internal resources from external threats.
When should an organization use a forward proxy?
Organizations should use a forward proxy when they need to:
- Control and monitor employee internet usage
- Enforce access policies and security rules
- Hide internal network IP addresses
- Cache frequently-requested content to improve performance
- Bypass geo-restrictions or enforce browsing restrictions for users



Leave a Comment