Need Help? We are right here!
Search Results:
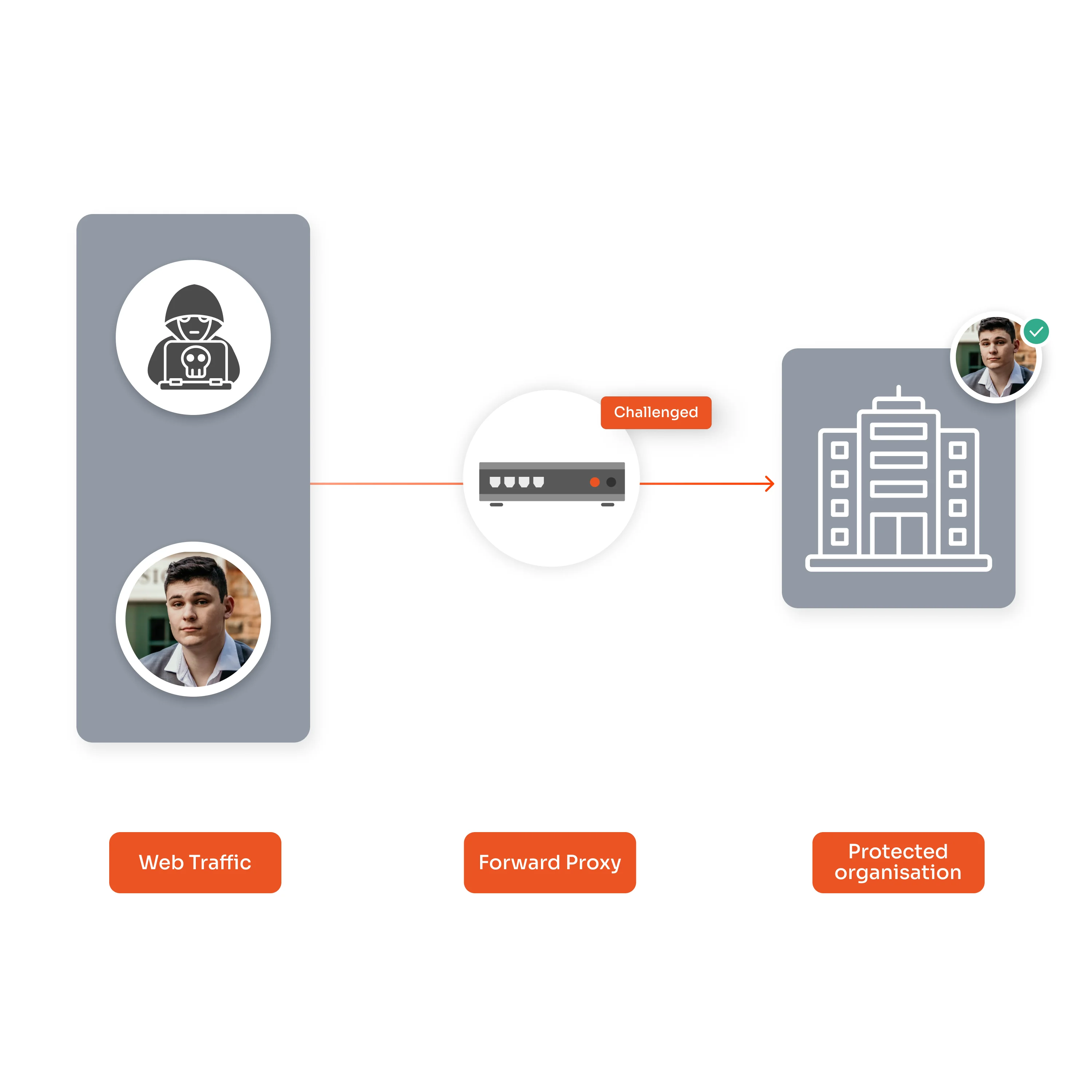
×A Forward Proxy solution acts like a middleman between the client devices and the internet, shielding users from accessing harmful sites and compromising enterprise resources.
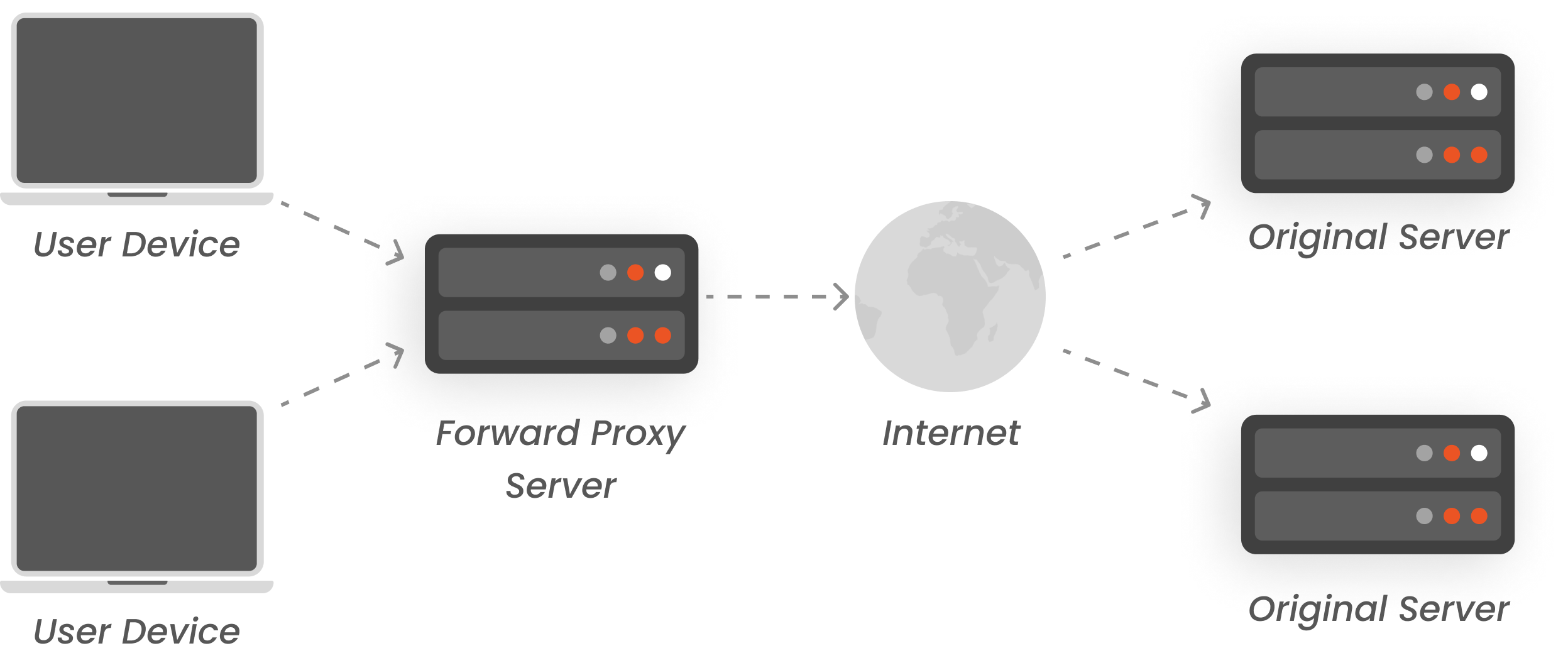







A Forward Proxy solution acts as an intermediary between an organization’s internal network and the World Wide Web, forwarding requests to websites and then returning the responses to the internal network. Forward proxies are optimized for controlling and monitoring outbound web requests, enforcing corporate policies, and detecting shadow IT and data exfiltration. These aspects are missing in traditional firewalls, giving proxy servers an edge. It also stores frequently accessed web pages to improve speed and save bandwidth, and hides the real IP address of users, keeping their browsing private.
User’s device sends a request to the proxy server instead of directly to the internet/site.
The proxy server receives the user’s request and acts as the gateway between the user and the target website.
Inspects the request based on security rules, filtering out requests to blocked/harmful sites, or applying policies like content restrictions.
Forwards the approved request to the website on behalf of the user, hiding the user’s real IP address.
The website sends its response back to the proxy server, which then relays the data safely back to the user's device.

Data risk increases when employees try to access their personal email accounts on company-issued devices. So, it is important to block personal email access (Gmail, Outlook, Hotmail, etc.) during business hours using the miniOrange Forward Proxy solution.
This solution acts as a buffer that analyzes the client request (user access request) and takes appropriate action as per the policies.
Forward proxy solution provides visibility into all outbound web traffic, enabling IT teams to detect and monitor shadow IT, also known as unsanctioned apps and devices used within the network.
By analyzing traffic patterns and application usage, the proxy identifies unauthorized cloud services and unknown software, helping organizations manage risks, enforce policies, and maintain control over their IT environment.
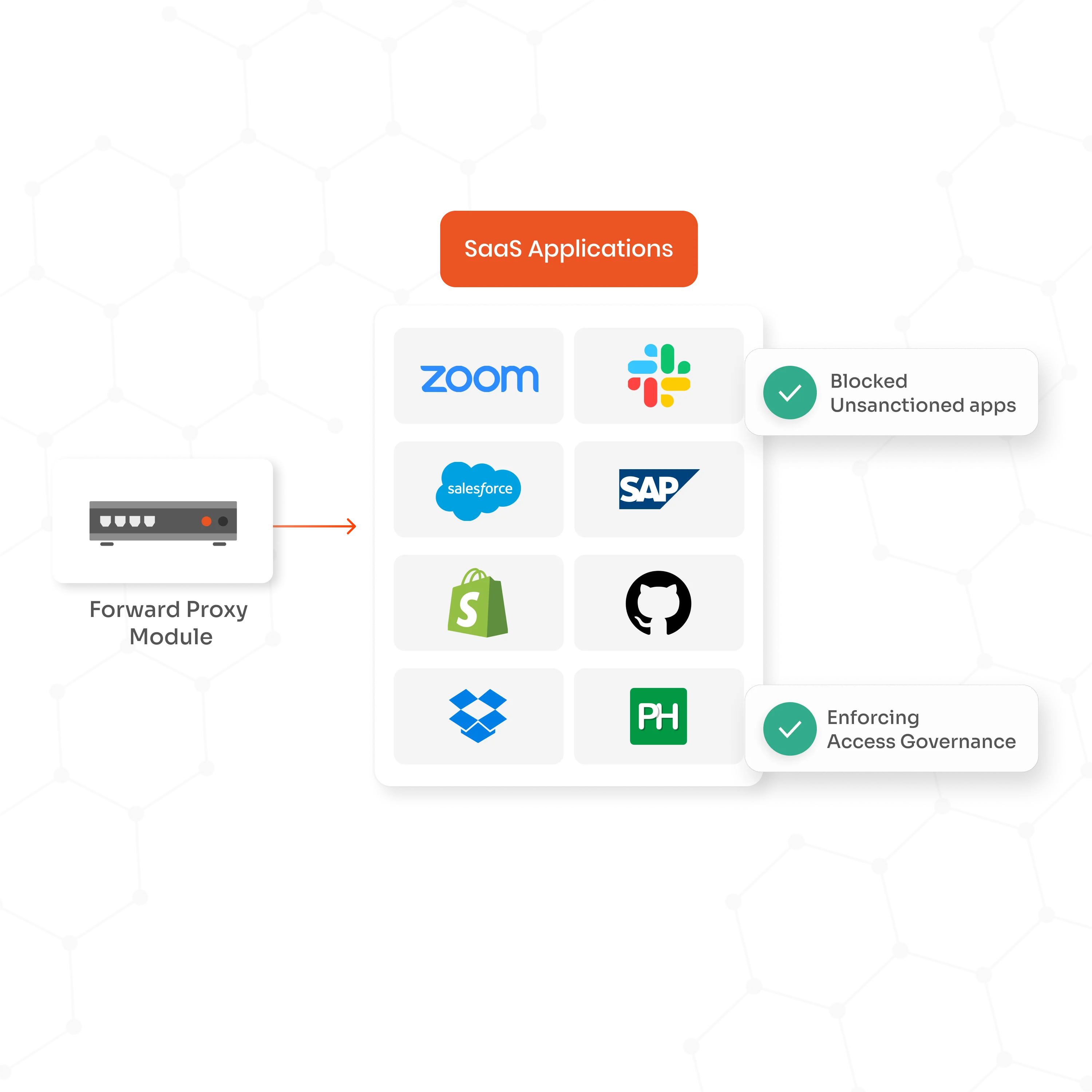
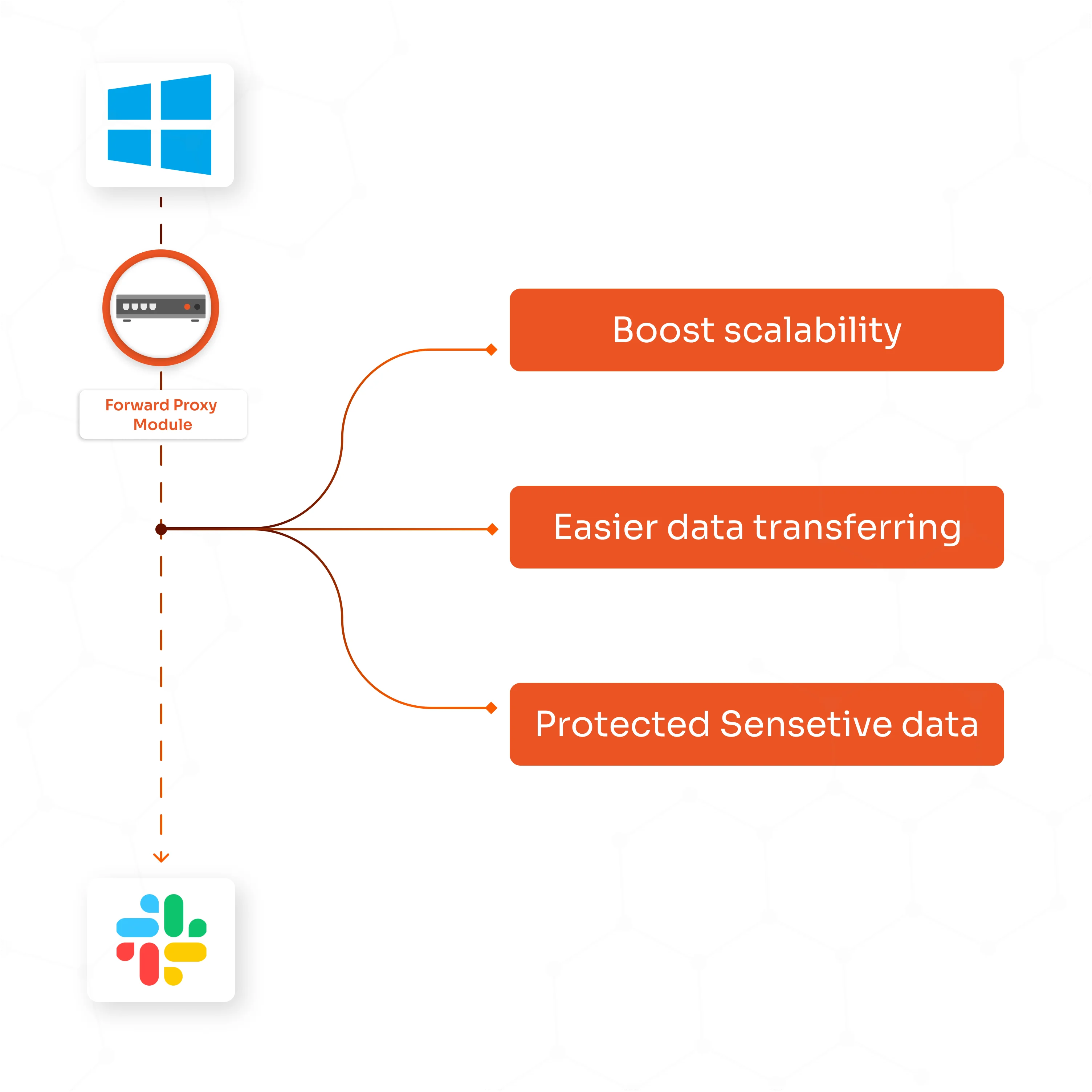
A forward proxy filters and inspects all web traffic, protecting sensitive corporate data from being leaked or exposed via unauthorized cloud storage or risky websites.
It blocks access to harmful sites and prevents malware by applying real-time threat detection, multi-factor authentication, and adaptive MFA.
A forward proxy maintains corporate privacy by masking internal network details and user identities from external websites.
By routing all web requests through the proxy, they hide IP addresses and unknown network structure, reducing attack surfaces and protecting valuable internal data from being mapped or exploited by cyber adversaries.





I can't speak highly enough regarding miniOrange, I am totally satisfied with the process and results in every regard.
5.0

Awesome tech service, Awesome product. Overall Awesome people. This solution is very simple and easy to implement
5.0
A CASB forward proxy operates as an intermediary sitting between users and the cloud services they want to access. It intercepts all outbound traffic to cloud applications, enforcing security.
Forward Proxy is widely used for adding Single Sign-On (SSO) for applications that do not support any standard SSO protocol like SAML, OAuth, or OpenID by default.
A forward proxy sits between the client devices and the internet, and is used for client anonymity, accessing geo-blocked or restricted content, content filtering, and reducing bandwidth via caching.Whereas a reverse proxy sits in front of the web servers and is used for load balancing, SSL offloading, content caching, protecting the backend servers, and preventing direct attacks on servers.
Unlike firewalls that filter data mainly at the network or transport layer (IP addresses and ports), a forward proxy solution inspects and relays requests at the application layer, allowing more granular control and the ability to filter specific web content and protocols (such as HTTP, HTTPS, FTP).
