In 2026, the stakes around identity security are higher than ever, and choosing the right multi-factor authentication (MFA) provider can directly influence how resilient your organization is against modern attacks. Cybercriminals are increasingly bypassing weak or legacy authentication using phishing, credential stuffing, and social engineering, which makes static passwords alone effectively obsolete.
Strong multi-factor authentication (MFA) significantly reduces the risk of account takeovers, safeguards remote access, and supports a Zero Trust security model across cloud, on-premises, and hybrid environments. At the same time, regulations and frameworks such as GDPR, NIST, PCI DSS, and HIPAA now expect robust authentication controls as a baseline, not an add-on.
To simplify this process, more than 30 leading MFA platforms were rigorously evaluated, with a strong emphasis on how well they handle adaptive MFA, support modern passwordless experiences, integrate across complex ecosystems, and scale in real-world deployments. This in-depth comparison focused on practical factors that matter to security and IT teams every day.
What Makes a Top MFA Provider in 2026?
Intelligent Threat Detection
Top MFA providers in 2026 leverage AI-powered threat detection to analyze user behavior, device posture, and contextual risks in real-time, automatically escalating authentication challenges during suspicious activity. This proactive defense stops advanced phishing and credential stuffing attacks before they succeed, ensuring robust protection without constant user intervention.
Frictionless Passwordless Authentication
Leading solutions prioritize passwordless methods like FIDO2 passkeys, biometrics, and hardware tokens, delivering high-security authentication solutions that feel effortless across desktops, mobiles, and IoT devices. This user-centric approach boosts adoption rates while aligning with the global shift away from passwords.
Broad Ecosystem Integrations
The best solutions integrate with most applications, including SaaS (Salesforce, Office 365), VPNs, legacy systems, and custom APIs via SAML, OIDC, and RADIUS. This coverage eliminates silos, enabling unified MFA across cloud, on-premise, and hybrid setups for enterprises of all sizes.
Transparent and Flexible Pricing
Leading vendors publish clear, predictable per-user or per-authentication pricing with minimal hidden add-ons, making it easier for organizations to forecast security spend. Tiered plans, volume discounts, and modular add-ons (such as advanced risk engines or passwordless options) allow businesses of different sizes to adopt MFA without overpaying for unused features.
Measurable Security and Business ROI
Strong MFA platforms demonstrate tangible ROI through reduced breach risk, fewer account takeovers, and lower helpdesk load from password resets. Many providers back this with case studies and analytics dashboards that quantify blocked attacks, authentication success rates, and user adoption, allowing CISOs to justify investments with data-driven outcomes.
Introduction to the Best Multi-factor Authentication Solutions
- miniOrange: Flexible MFA software with 6000+ app integrations, adaptive authentication, and unbeatable value for SMBs to enterprises seeking broad coverage without complexity.
- Microsoft Entra ID: Enterprise-grade MFA tightly integrated with the Microsoft ecosystem, conditional access, and strong passwordless options for hybrid environments.
- Okta MFA: Cloud-first adaptive MFA with rich policy controls and thousands of pre-built integrations for complex SaaS stacks.
- Cisco Duo: User-friendly push-based MFA with device health checks and strong Zero Trust access controls for mixed device fleets.
- Google Workspace MFA: Built-in MFA and passkeys for organizations standardized on Google services, balancing simplicity with strong security.
- Ping Identity: Federation-focused IAM and MFA platform ideal for large enterprises needing advanced SSO and hybrid deployment flexibility.
- RSA SecurID: Veteran token-based and modern MFA platform trusted by highly regulated industries that require stringent assurance levels.
- Thales SafeNet: Hardware-rooted MFA and token solutions combined with cloud services for organizations demanding high-assurance authentication.
- IBM Security Verify: Comprehensive IAM suite with built-in adaptive MFA for enterprises invested in the IBM security ecosystem.
- ManageEngine ADSelfService Plus: AD-centric MFA and self-service password tool tailored for Windows and VPN-heavy infrastructures.
- SecureAuth: Context-aware and adaptive MFA optimized for complex, hybrid, and legacy-heavy environments.
- Silverfort: Agentless universal MFA extending protection to legacy systems, OT, and CLI with real-time risk-adaptive policies across hybrid environments
| Provider | Best for | Free / trial option |
|---|---|---|
| miniOrange | Flexible, cost-effective MFA across 6000+ apps for SMBs & enterprises | 30-day free trial |
| Microsoft Entra ID | Microsoft 365 and Azure-centric enterprises | 30-day trial |
| Okta MFA | Complex SaaS and multi-cloud environments | 30-day trial |
| Cisco Duo | Fast, user-friendly MFA rollout across mixed device fleets | Free tier + trials |
| Google Workspace MFA | Organizations standardized on Google services | Included + trial upgrades |
| Ping Identity | Large enterprises needing advanced SSO and federation | Trial/demo on request |
| RSA SecurID | Highly regulated and compliance-focused industries | POC / trial via sales |
| Thales SafeNet | High-assurance hardware token and cloud MFA deployments | Trial for cloud services |
| IBM Security Verify | Enterprises invested in IBM’s broader security ecosystem | 30-day trial |
| ManageEngine ADSelfService Plus | Windows and AD-heavy infrastructures | Free edition + trials |
| SecureAuth | Complex hybrid and legacy-heavy environments | Trial/demo on request |
| Silverfort | Agentless universal MFA for legacy, OT, and CLI systems | Trial/demo on request |
12 Best MFA Providers in 2026: Detailed Evaluation
1. miniOrange MFA Solution
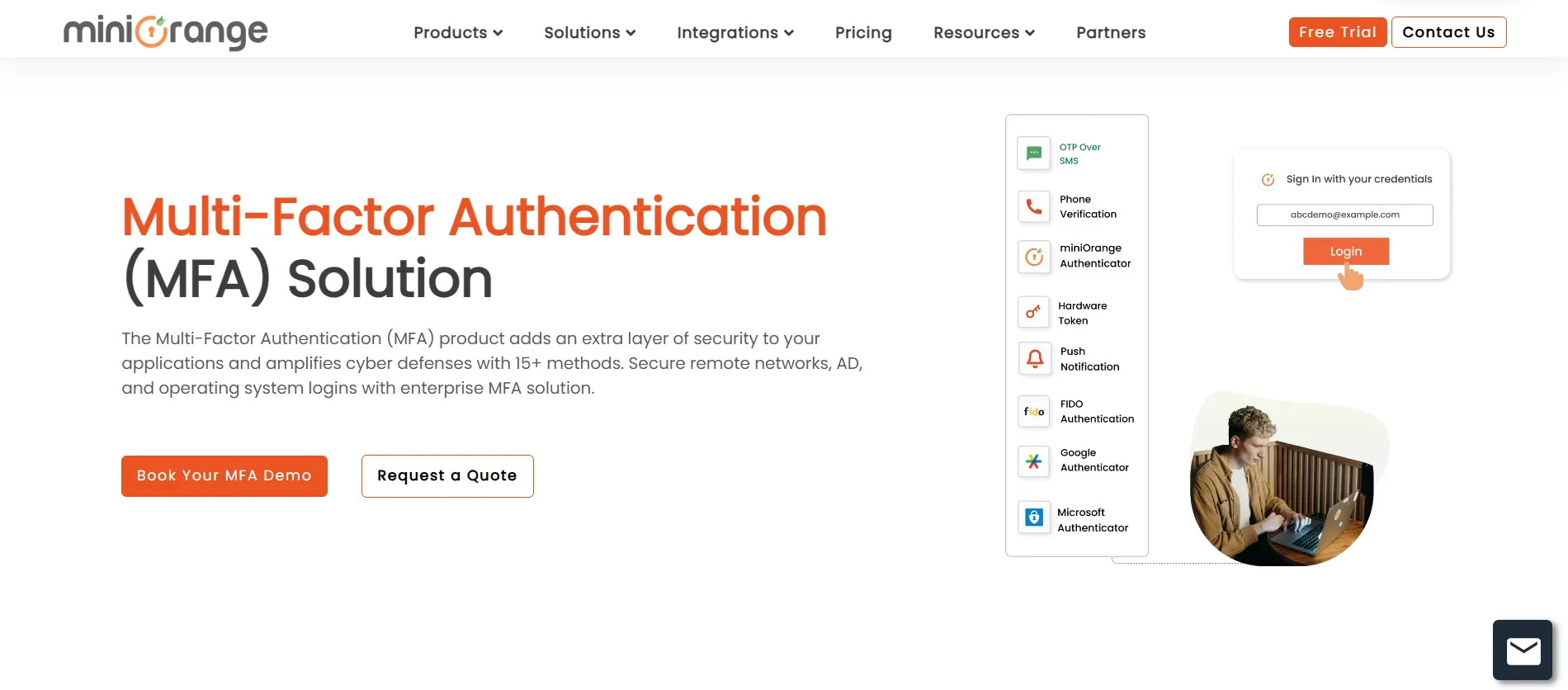
miniOrange stands out as a leading multi-factor authentication (MFA) provider and the primary choice for organizations that want a single MFA platform to secure every layer of their stack, from workforce to customers. It supports thousands of integrations across devices, including mobile, desktop, and even IoT endpoints, and works consistently across major operating systems like Windows, macOS, and Linux. This breadth extends to SaaS apps, on‑premise and legacy systems, VPNs, and business-critical platforms, allowing security teams to standardize on one solution instead of managing multiple disjointed tools.
The platform offers 15+ authentication methods, including OTP, push notifications, biometrics, and FIDO2-based passwordless options, which can be combined with risk-based authentication that evaluates risk signals such as device posture, location, and behavior. This helps deliver phishing-resistant security while keeping user friction low, and gives organizations the flexibility to design step-up journeys that match different assurance levels, compliance requirements, and user personas.
Key Features
- 6000+ app integrations across SaaS, legacy, VPNs, Shopify, and custom APIs
- 15+ authentication methods: OTP, push, biometrics, FIDO2 passwordless, hardware tokens
- Adaptive MFA analyzes signals (device, location, time, IP reputation) to reduce high-risk access
- Multi-OS support (Windows/macOS/Linux desktop logins) and IoT endpoint protection
- 24/7 global support with free migrations and dedicated onboarding specialists
miniOrange MFA Pros
- Unmatched breadth eliminates the need for multiple MFA tools
- Intelligent policies balance security and user experience seamlessly
- Cost-effective scaling from SMB to enterprise with flexible licensing
miniOrange MFA Cons
- Initial setup requires planning for optimal policy tuning
- May require initial setup assistance
Pricing
- 30-day full-featured free trial
- Pricing starts from $2 per user per month
- Custom quotes available based on use cases
miniOrange Ratings & Reviews:
- G2: 4.6
2. Microsoft Entra ID
Microsoft Entra ID excels as an enterprise-grade MFA deeply embedded in Microsoft 365/Azure, with conditional access evaluating user risk, device compliance, and location. Integrates thousands of SaaS apps via App Gallery and hybrid AD Connect for on-prem. Ideal for Microsoft-invested orgs with passwordless Windows Hello and FIDO2.
Pros
- Provides native integration with Microsoft 365, Teams, and Azure for seamless rollout.
- Leverages Microsoft Defender for advanced threat intelligence and risk policies.
- Offers scalable hybrid AD Connect bridging on-premises to cloud environments.
Cons
- Policy configuration complexity overwhelms IT teams without dedicated identity expertise.
- Performs poorly for organizations outside the Microsoft ecosystem with limited non-Azure integrations.
Microsoft Ratings & Reviews:
- G2: 4.7
3. Okta MFA
Okta MFA delivers cloud-native, adaptive authentication via Workforce Identity Cloud, utilizing ThreatInsight across numerous SaaS integrations, including Salesforce. Supports Okta Verify push, FIDO2, biometrics with developer APIs for custom workflows. Ideal for multi-SaaS enterprises seeking to avoid on-premises lock-in.
Pros
- Covers a multitude of applications through an extensive app catalog and a universal directory.
- Provides developer-friendly APIs and SDKs for custom authentication workflows.
- Delivers proven scalability for global enterprises with high uptime SLAs.
Cons
- Requires steep pricing upgrades to access adaptive and risk-based features.
- Enforces mandatory annual commitments that deter smaller deployments.
Okta Ratings & Reviews:
- G2: 4.5
4. Cisco Duo
Cisco Duo prioritizes push-based MFA with device health checks for OS patches and encryption across VPNs, RDP, and cloud apps via RADIUS/SAML. Zero Trust focus enables rapid deployment for mixed devices without heavy training. IT teams love its simplicity and endpoint visibility.
Pros
- Enables lightning-fast deployments typically under 30 minutes for most environments.
- Features an intuitive mobile app that drives exceptionally high user adoption rates.
- Provides comprehensive device posture verification, including OS and security status.
Cons
- Requires paid add-ons to access advanced analytics and reporting features.
Cisco Duo Ratings & Reviews:
- G2: 4.5
5. Google Workspace MFA
Google Workspace MFA provides phishing-resistant prompts, security keys, and passkeys natively in Gmail/Drive with Admin console management. Automatic suspicious login blocking suits Google-centric teams seeking low-overhead protection without separate deployments.
Pros
- Incurs zero additional licensing cost beyond the existing Workspace subscription.
- Delivers a frictionless authentication experience optimized for Google ecosystem users.
- Includes built-in AI-powered phishing detection and suspicious login blocking.
Cons
- Limited exclusively to Google applications with minimal third-party coverage.
- Offers basic policy customization lacking enterprise-grade granularity.
Google Workspace Ratings & Reviews:
- G2: 4.6
6. Ping Identity
Ping Identity specializes in federation-heavy IAM with PingOne MFA, delivering advanced B2B/B2E SSO across SAML, OIDC, and WS-Fed standards for complex hybrid deployments. Adaptive policies leverage contextual risk signals to trigger push notifications, OTP, or FIDO2 challenges precisely when needed. Enterprises with extensive partner ecosystems and legacy federation requirements find Ping's platform uniquely capable of handling intricate identity flows without compromising standards compliance or deployment flexibility.
Pros
- Leads industry in B2B federation capabilities for partner ecosystems.
- Supports flexible cloud, hybrid, and on-premises deployment models.
- Maintains excellence in SAML, OIDC, and WS-Fed standards compliance.
Cons
- Presents a steep learning curve requiring specialized admin expertise.
- Proves overpriced and heavyweight for organizations needing only basic MFA.
Ping Identity Ratings & Reviews:
- G2: 4.4
7. RSA SecurID
RSA SecurID combines decades of token-based authentication reliability with modern cloud MFA capabilities, securing VPNs, VDI, and critical applications in finance and government sectors demanding FIPS-compliant assurance. Hardware and soft tokens integrate seamlessly with push notifications and biometrics, delivering comprehensive audit-grade reporting essential for stringent regulatory compliance and high-stakes access control scenarios.
Pros
- Earns battle-tested trust across heavily regulated financial and government sectors.
- Maintains a robust ecosystem supporting diverse hardware and software tokens.
- Provides comprehensive compliance reporting and documentation standards.
Cons
- Creates physical token distribution and logistics management burden.
- Trails cloud-native competitors in innovation speed and deployment agility.
RSA SecurID Ratings & Reviews:
- G2: 4.4
8. Thales SafeNet
Thales SafeNet anchors enterprise MFA in hardware security modules and FIPS 140-2 certified tokens, extending comprehensive protection to OT/SCADA systems and critical infrastructure alongside cloud services. Smart cards, USB tokens, and mobile authenticators secure air-gapped environments where cryptographic assurance remains paramount for defense contractors and utility providers prioritizing uncompromised security standards.
Pros
- Delivers enterprise-grade HSM-backed cryptographic security validation.
- Provides native compatibility with OT and industrial control systems.
- Features durable token lifecycles supporting long-term deployments.
Cons
- Hardware procurement processes significantly delay initial rollouts.
- Appears less agile compared to purely cloud-native MFA alternatives.
Thales SafeNet Ratings & Reviews:
- G2: 4.4
9. IBM Security Verify
IBM Security Verify integrates sophisticated adaptive MFA within comprehensive IAM capabilities, leveraging AI-driven risk analysis across mainframes, legacy systems, cloud applications, and APIs. OTP, biometrics, and FIDO2 authentication methods combine with advanced governance workflows, enabling IBM ecosystem enterprises to modernize identity infrastructure without disruptive rip-and-replace migrations.
Pros
- Offers native integration with mainframes and legacy IBM infrastructure.
- Features a sophisticated AI-powered risk assessment engine capabilities.
- Provides a complete governance, analytics, and compliance management suite.
Cons
- Creates heavy dependency on the existing IBM technology stack.
- Demands significant resources for deployment and ongoing maintenance.
IBM Security Ratings & Reviews:
- G2: 4.1
10. ManageEngine ADSelfService Plus
ManageEngine ADSelfService Plus delivers tightly integrated AD-centric MFA specifically designed for Windows logons, VPN access, and RDP sessions, bundled with self-service password reset functionality that dramatically reduces helpdesk tickets. Windows-focused SMBs and mid-market organizations with traditional infrastructures benefit most from its deep Active Directory affinity and immediate ROI through password management efficiencies.
Pros
- Provides deepest integration with Active Directory, VPNs, and RDP environments.
- Delivers immediate ROI through self-service password reset capabilities.
- Offers extremely budget-friendly pricing for Windows-centric deployments.
Cons
- Exhibits limited coverage for modern cloud and SaaS application ecosystems.
- Features a somewhat dated user interface that slows administrative tasks.
ManageEngine Ratings & Reviews:
- G2: 4.4
11. SecureAuth
SecureAuth specializes in context-aware adaptive MFA that analyzes behavioral biometrics, IP reputation, device fingerprinting, and environmental signals to dynamically adjust authentication requirements across complex hybrid environments. The platform protects custom applications, VPN gateways, mainframes, and legacy protocols through intelligent proxy integration, making it ideal for enterprises modernizing intricate IT estates without complete infrastructure overhauls.
Pros
- Features advanced behavioral biometrics and multi-signal risk analytics.
- Provides extensive support for legacy protocols and mainframe systems.
- Offers flexible custom risk scoring and policy configuration options.
Cons
- Typically requires professional consulting services for optimal implementation.
- Maintains a higher pricing threshold compared to basic MFA solutions.
SecureAuth Ratings & Reviews:
- G2: 4.4
12. Silverfort
Silverfort delivers completely agentless universal MFA by proxying protection across RDP, SSH, SMB file shares, and OT protocols without requiring endpoint modifications or application changes. Network-based deployment enables real-time risk-adaptive policies for service accounts, CLI access, and legacy systems that traditional MFA cannot reach, making it essential for hybrid enterprises protecting unmodernizable infrastructure alongside modern applications.
Pros
- Enables completely agentless deployment, requiring no endpoint modifications.
- Provides protocol-agnostic protection across diverse legacy environments.
- Delivers real-time threat detection and blocking capabilities.
Cons
- Involves complex network architecture deployment requirements.
- Functions as a complement to, rather than a replacement for, application MFA.
Silverfort Ratings & Reviews:
- G2: 4.8
How to Choose the Right MFA Provider?
You've explored the top MFA solutions on the market, but what key factors should guide your final decision? Our expert Ayushi Dewani, MFA Team Lead, breaks it down with essential considerations for selecting the right MFA platform.
"Technology is changing rapidly, reshaping how businesses operate and collaborate, yet MFA and authentication strategies remain the foundation for securing identities and access."
— Ayushi Dewani , MFA Team Lead
Step 1: Map Your Needs
Inventory applications, user types, and compliance across hybrid, cloud, and legacy environments. SMBs prioritize cost and simplicity, while enterprises require federation, adaptive policies, and IoT coverage. Document VPN, desktop, and SaaS gaps, user scale, and deployment preferences, then match your risk profile to each vendor's integration breadth and capabilities.
Step 2: Test Proof-of-Concepts
Deploy two or three shortlisted vendors in parallel proofs-of-concept over two to four weeks across VPN, SSO, and desktop logins. Measure deployment time, user adoption rates, false positives, and IT overhead. Prioritize solutions that deliver seamless day-to-day performance, minimal disruption, and strong security without generating excessive helpdesk tickets.
Step 3: Verify Compliance Certifications
Confirm alignment with GDPR, PCI-DSS, HIPAA, and any sector-specific regulations. Ask for SOC 2 Type II, ISO 27001, and recent penetration test summaries, along with detailed audit logging capabilities. Exclude vendors that cannot provide clear, current third-party assurances of their security posture and regulatory readiness.
Step 4: Compare the Total Cost of Ownership
Calculate the three-year total cost of ownership, including licenses, support, implementation, migrations, and training. Account for minimum user commitments, add-ons for adaptive authentication, and potential overage or scaling fees. Focus on transparent per-user pricing and demonstrable ROI through reduced breaches, fewer account takeovers, and lower password-related support volumes.
Step 5: Prioritize Support Quality
Evaluate support responsiveness, onboarding assistance, and migration help during the proof-of-concept. Favor vendors offering 24/7 support, clear SLAs, knowledgeable engineers, and proactive success management. Check independent reviews for real-world feedback, and treat long-term reliability and partnership strength as more important than short-lived promotional discounts.
MFA Trends to Look for in 2026
Passwordless Dominance
Passwordless authentication dominates 2026 as enterprises replace passwords with FIDO2 passkeys, biometrics, and certificates. Over 70% target full adoption following NIST guidelines. Browser and platform support matures, delivering phishing-resistant security without user friction across mobile, desktop, and web environments.
AI Anomaly Detection
AI-powered anomaly detection becomes standard in adaptive MFA solutions. Machine learning monitors behavioral patterns, device signals, and network context to preempt credential stuffing and session hijacking. Models achieve 99.9% accuracy in distinguishing legitimate access from sophisticated threats without manual policy adjustments.
Unified IAM Platforms
Unified Identity and Access Management consolidates workforce, customer, and service account authentication under a single platform. Consistent Zero Trust policies apply across B2E, B2B, and B2C scenarios, eliminating silos, reducing licensing sprawl, and simplifying compliance reporting for global enterprises.
Agentless Legacy Protection
Agentless MFA extends protection to RDP, SSH, SMB, and OT protocols through network proxies. Legacy systems, service accounts, and CLI access gain real-time risk policies without endpoint modifications, addressing coverage gaps in hybrid environments with unmodernizable infrastructure.
Quantum-Resistant Crypto
Quantum-resistant cryptography preparations accelerate as vendors certify post-quantum algorithms. Decentralized identity pilots gain traction for privacy-preserving customer authentication. Organizations prioritize future-proof standards protecting against emerging computational threats while maintaining backward compatibility.
Ready to Securely Begin 2026?
The top 12 MFA providers showcase specialized strengths addressing diverse enterprise needs. miniOrange leads with 15+ authentication methods, 6000+ integrations across devices, OS, and applications at competitive pricing. Silverfort excels in agentless legacy protection while Microsoft Entra ID dominates Microsoft ecosystems.
Organizations should prioritize adaptive intelligence, passwordless readiness, broad coverage, and total cost alignment when selecting solutions. miniOrange delivers versatile protection for SMBs scaling to enterprises with 24/7 support and free migrations.
FAQs
Why should enterprises prioritize MFA in 2026?
MFA significantly reduces account takeover risk, supports Zero Trust strategies, and helps meet regulations like GDPR and PCI DSS at a time when phishing and credential attacks continue to rise globally across sectors of all sizes.
What factors matter most when choosing an MFA provider?
Key factors are integration breadth, adaptive and passwordless capabilities, usability, compliance readiness, and three-year total cost of ownership, together with reliable support and a proven roadmap for future security enhancements.
How does adaptive MFA work?
Real-time analysis of IP address, device type, geographic location, login time, and user behavior patterns dynamically adjusts authentication strength, balancing security with minimal user friction across all access scenarios.
Most cost-effective enterprise MFA?
miniOrange plan starts at 1.50 USD/user/month with a 30-day free trial. Volume prices may vary at scale while maintaining 6,000+ integrations and adaptive capabilities.





Leave a Comment